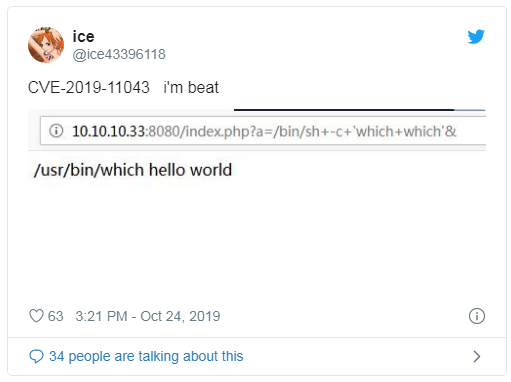
ZDNet According to foreign media reports , PHP 7.x in recent fix a remote code execution vulnerability being malicious use, and will result in the attacker's control server. Number CVE-2019-11043 vulnerabilities allow an attacker to send a specially crafted through to the target server URL, you can execute commands on a vulnerable server. The PoC exploit code that has also been posted on GitHub .
Once the vulnerable targets, the attacker will be able to by appending the URL '? A =' to send a specially crafted request to a vulnerable Web server
Only the affected server NGINX
Fortunately, not all of the PHP Web server are affected. According to reports, only enabled PHP-FPM of NGINX server vulnerable to attack. PHP-FPM Representative FastCGI Process Manager, having some additional features PHP FastCGI alternative implementations. It is not a standard component of nginx, but some Web hosting providers will continue as part of the standard PHP hosting environment.
Web hosting providers Nextcloud is one example of the company on October 24 issued to its customers a security warning , urging customers to update to the latest version of PHP 7.3.11 and 7.2.24 , which includes fixes for vulnerabilities CVE-2019-11043 . In addition, many other hosting provider also suspected nginx + PHP-FPM combination of running vulnerable.
But there are some sites due to technical limitations and can not be updated PHP, or can not switch from PHP-FPM to another CGI processor.
Suggested fix
- The PHP 7.1.X update to 7.1.33 https://github.com/php/php-src/releases/tag/php-7.1.33
- The PHP 7.2.X update to 7.2.24 The https://github.com/php/php-src/releases/tag/php-7.2.24
- The PHP 7.3.X update to 7.3.11 https://github.com/php/php-src/releases/tag/php-7.3.11
Detailed analysis of the vulnerability could view https://paper.seebug.org/1063/ .