Apache access control
effect
1. control access to the site resources
2. Add the access authorization for a particular Web site directories
Common access control
1. The client address restrictions
2. User licensing restrictions
Client-based access control address
1. Require CI access control, according to the order limit
2 can be used to <Location>, <Directory>, <Files>, the <Limit> configuration section
Require common syntax of configuration items
Require all granted
Require all denied
Require local
Require [not] host <主机名或域名列表>
Require [not] ip <IP地址或网段列表>
使用not禁止访问时要将其置于<RequireAll> </RequireAll>容器中并在容器中指定相应的限制策略Example demonstrates
Apache restrict access to the client's address
1. first check the client's IP address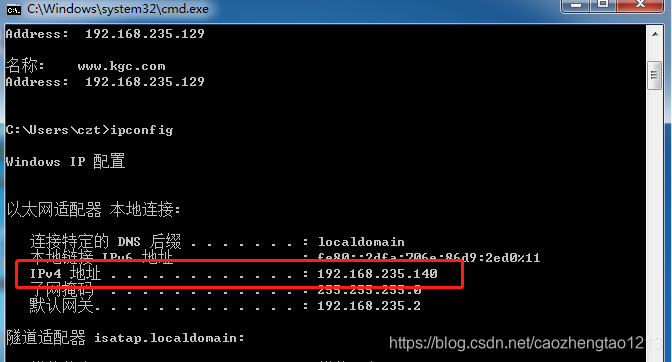
2. Configure httpd Extended Profiles
[root@localhost ~]# cd /etc/httpd/conf/extra //扩展配置文件目录
[root@localhost extra]# ls
vhost.conf
[root@localhost extra]# vim vhost.conf //编辑虚拟主机配文件
<VirtualHost 192.168.235.129:80>
DocumentRoot "/var/www/html/accp/"
ServerName www.accp.com
ErrorLog "logs/www.accp.com.error_log"
CustomLog "logs/www.accp.com.access_1og" common
<Directory "/var/www/html/">
<RequireAll> //容器起始标签
Require not ip 192.168.235.140 //禁止IP为192.168.235.140的主机访问
Require all granted
</RequireAll> //容器结束标签
</Directory>
</VirtualHost>
[root@localhost extra]# systemctl restart httpd //重启服务
[root@localhost ~]# systemctl restart named
[root@localhost ~]# systemctl stop firewalld.service
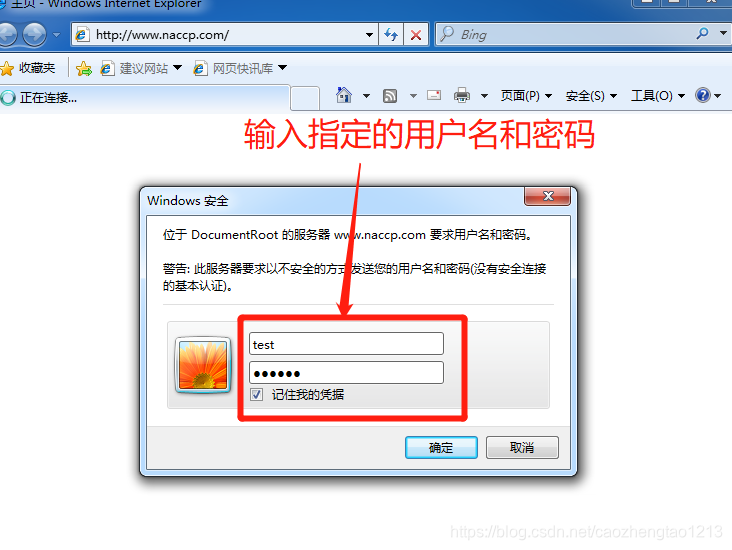
[root@localhost ~]# setenforce 03. Use the client test page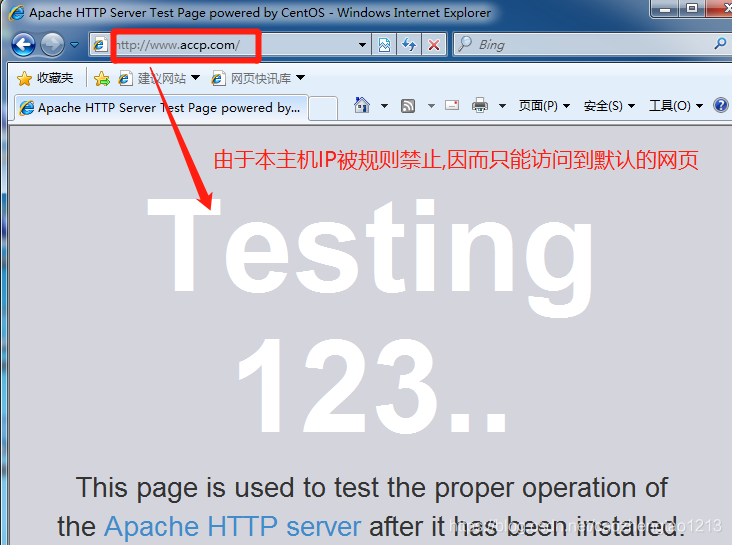
Users access the Apache licensing restrictions
1. Create a user authentication database
[root@localhost ~]# cd /etc/httpd/conf //进入httpd主配置文件
[root@localhost conf]# htpasswd -c /etc/httpd/conf/pwd test //创建用户加密文件,若文件存在则不需要加-c
New password: //输入自定义密码
Re-type new password: //确认密码输入
Adding password for user test
[root@localhost conf]# cat pwd //查看用户及密码加密
test:$apr1$VBfoRWHC$Feck.BITMYhaOlEKrc/1j.Configuring DNS
[root@localhost extra]# vim /etc/named.rfc1912.zones
zone "naccp.com" IN {
type master;
file "naccp.com.zone";
allow-update { none; };
};
[root@localhost extra]# cd /var/named
[root@localhost named]# cp -p accp.com.zone naccp.com.zone
[root@localhost named]# vim naccp.com.zone
$TTL 1D
@ IN SOA @ rname.invalid. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS @
A 127.0.0.1
www IN A 192.168.235.1423. Configure httpd Extended Profiles
[root@localhost conf]# cd /etc/httpd/conf/extra
[root@localhost extra]# vim vhost.conf
... //省略部分不做修改,追加以下内容
<VirtualHost 192.168.235.142:80>
Documentroot "/var/www/html/accp02/"
ServerName www.naccp.com
Errorlog "logs/www.accp02.com.error_log"
Customlog "logs/www.accp02.com.access_log" common
<Directory "/var/www/html/">
AuthName "DocumentRoot" //声明条目
AuthType Basic //基本验证类型
AuthUserFile /etc/httpd/conf/pwd //验证文件目录
Require valid-user //授权用户的验证
</Directory>
</VirtualHost>
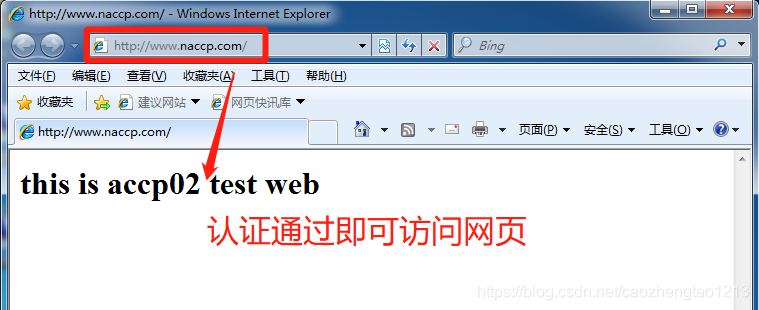
[root@localhost extra]# systemctl restart httpd //重启服务4 uses the client test page