--- --- restore content begins
The following finishing from Transient-Steady Effect Attack on Block Ciphers 2015
This article presents a new attack: Attack temporary steady effect
temporary state effect: output combinational circuit before jumping to the correct value will remain a temporary value
Pros: attack and other faults, do not require a lot of encryption to build a statistical model, less the number of encryption that is required to stage attacks
Attack achieved: injection clock glitches, to give temporary steady value, i.e. comprising fault information outputting secret key
Target circuit: two non shield cartridge and an AES circuit s s shield box, FPGA implemented
Results: For the S-box cryptography unmasked once the secret key can be obtained a byte
for shielding the cartridge s 20 byte encrypted secret key may be obtained
1. Background
Side channel attacks made 1
now has a method (information leakage type) many side-channel attack the cryptographic circuit:
Power Analysis 2,3
Template. 4
collide 5,6
Mutual Information. 7
fault attack, the DFA is known wherein 8 compares, based on fault model correct ciphertext to recover from an error and output the output ciphertext secret key
2010 fault sensitivity analysis presented FSA 9, this method has critical dependency data path s cassette-based AES, but the encryption requires multiple cracks
2011 FSA and collision attack in combination, have to break the AES circuit shield 10, the disadvantage is to increase the number of encryption
2012 proposed clockwise collision fault sensitivity analysis CC-FSA, AES circuit for shielding
they pointed out that if the two inputs are identical, the first secondary time will be shorter, since almost no combining circuit flip
2012 FRA attack immediately made clock width, cartridge serial break the shielding s AES,
but the above two methods have a common disadvantage:
1. confusing clock frequency
2. appropriate clock width detecting inefficient
3. encryption too many times
The contribution of this article
A new fault attack method: a temporary state attack TSE attack
Target circuit is usually calculated in the first cycle, and a clock glitches injected to create a second very short period. Calculate the normal output of the first clock cycle of data in accordance with a short path length in the first cycle and the data path. Error output of the second cycle is calculated according to data of the short path length of the first cycle and the data path of the second cycle. By a combination of the output of two successive clock cycles, we can recover the information data short path
(path where the short secret key)
2. Preparation
AES10 encryption round, round cartridge requires 16 s. When power is restricted area, the serial algorithm to achieve better.
For example:
In each encryption round, with four cartridge 4 cycles 13-14 s
much lower power consumption methods have been proposed to achieve 15-16
Shield conventional countermeasures against power analysis. Sensitive intermediate mask values so that the value of the randomization, and minimizing power consumption and the dependency between the data. AES algorithm S-box is the only non-linear operation, as a method based on column field, many masking schemes have been proposed [17].
Shielded and unshielded s Box:
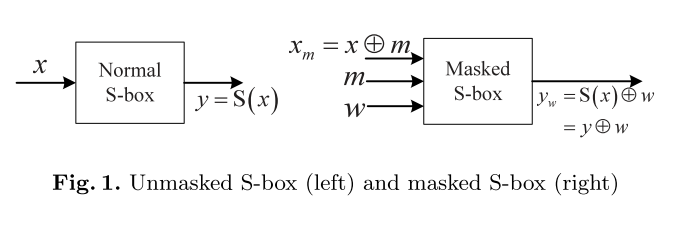
Li et al proposed CC-FSA attacks. In 2012 [11]. If the input is not changed in two successive clock periods, the second period almost no signal inversion. This is called a clockwise collision , the establishment of the second clock cycle time will be very short. They let the goal to work in the first period, and insert a clock glitch to produce a very short second clock cycle. If the output is correct, clockwise collision will be detected.
3. temporary state effect attacks
Data combining circuit path length is not the same
example, we can assume that a signal path shorter than the path delay of the delay signal b. After arriving a, b before reaching the output, the output will show an illegal value. When the signal propagation delay between the two differences is sufficiently long, the output will remain at an invalid value. This is known as the transient stabilizing effect. Transient Stability effect may lead to data related to power consumption, and indirectly disclose confidential information [18-22]. However, in this paper, we show that the value of the temporary effect caused by the transient stability can be captured and can be used to directly recover the secret key.
Temporary effect on the steady state, steady state effects of proposed temporary attack:
target circuit is usually calculated in the first cycle, and a clock glitches injected to create a second very short period. Calculate the normal output of the first clock cycle of data in accordance with a short path length in the first cycle and the data path. Error output of the second cycle is calculated according to data of the short path length of the first cycle and the data path of the second cycle. By a combination of the output of two successive clock cycles, we can recover the information data of the short path.
(Secret key where path is relatively short)
The basic idea
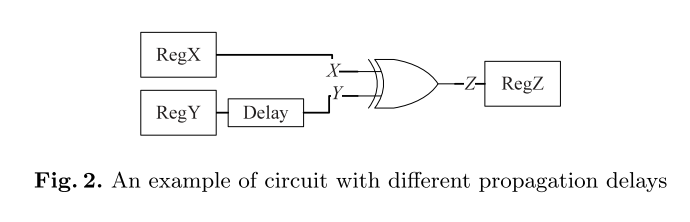
Delay X, Y signals are each T X- , T the Y , Z will be the output value of the capture register
assumed T X- $ / $ T << the Y
--- end --- restore content
The following finishing from Transient-Steady Effect Attack on Block Ciphers 2015
This article presents a new attack: Attack temporary steady effect
temporary state effect: output combinational circuit before jumping to the correct value will remain a temporary value
Pros: attack and other faults, do not require a lot of encryption to build a statistical model, less the number of encryption that is required to stage attacks
Attack achieved: injection clock glitches, to give temporary steady value, i.e. comprising fault information outputting secret key
Target circuit: two non shield cartridge and an AES circuit s s shield box, FPGA implemented
Results: For the S-box cryptography unmasked once the secret key can be obtained a byte
for shielding the cartridge s 20 byte encrypted secret key may be obtained
1. Background
Side channel attacks made 1
now has a method (information leakage type) many side-channel attack the cryptographic circuit:
Power Analysis 2,3
Template. 4
collide 5,6
Mutual Information. 7
fault attack, the DFA is known wherein 8 compares, based on fault model correct ciphertext to recover from an error and output the output ciphertext secret key
2010 fault sensitivity analysis presented FSA 9, this method has critical dependency data path s cassette-based AES, but the encryption requires multiple cracks
2011 FSA and collision attack in combination, have to break the AES circuit shield 10, the disadvantage is to increase the number of encryption
2012 proposed clockwise collision fault sensitivity analysis CC-FSA, AES circuit for shielding
they pointed out that if the two inputs are identical, the first secondary time will be shorter, since almost no combining circuit flip
2012 FRA attack immediately made clock width, cartridge serial break the shielding s AES,
but the above two methods have a common disadvantage:
1. confusing clock frequency
2. appropriate clock width detecting inefficient
3. encryption too many times
The contribution of this article
A new fault attack method: a temporary state attack TSE attack
Target circuit is usually calculated in the first cycle, and a clock glitches injected to create a second very short period. Calculate the normal output of the first clock cycle of data in accordance with a short path length in the first cycle and the data path. Error output of the second cycle is calculated according to data of the short path length of the first cycle and the data path of the second cycle. By a combination of the output of two successive clock cycles, we can recover the information data short path
(path where the short secret key)
2. Preparation
AES10 encryption round, round cartridge requires 16 s. When power is restricted area, the serial algorithm to achieve better.
For example:
In each encryption round, with four cartridge 4 cycles 13-14 s
much lower power consumption methods have been proposed to achieve 15-16
Shield conventional countermeasures against power analysis. Sensitive intermediate mask values so that the value of the randomization, and minimizing power consumption and the dependency between the data. AES algorithm S-box is the only non-linear operation, as a method based on column field, many masking schemes have been proposed [17].
Shielded and unshielded s Box:

Li et al proposed CC-FSA attacks. In 2012 [11]. If the input is not changed in two successive clock periods, the second period almost no signal inversion. This is called a clockwise collision , the establishment of the second clock cycle time will be very short. They let the goal to work in the first period, and insert a clock glitch to produce a very short second clock cycle. If the output is correct, clockwise collision will be detected.
3. temporary state effect attacks
Data combining circuit path length is not the same
example, we can assume that a signal path shorter than the path delay of the delay signal b. After arriving a, b before reaching the output, the output will show an illegal value. When the signal propagation delay between the two differences is sufficiently long, the output will remain at an invalid value. This is known as the transient stabilizing effect. Transient Stability effect may lead to data related to power consumption, and indirectly disclose confidential information [18-22]. However, in this paper, we show that the value of the temporary effect caused by the transient stability can be captured and can be used to directly recover the secret key.
Temporary effect on the steady state, steady state effects of proposed temporary attack:
target circuit is usually calculated in the first cycle, and a clock glitches injected to create a second very short period. Calculate the normal output of the first clock cycle of data in accordance with a short path length in the first cycle and the data path. Error output of the second cycle is calculated according to data of the short path length of the first cycle and the data path of the second cycle. By a combination of the output of two successive clock cycles, we can recover the information data of the short path.
(Secret key where path is relatively short)
The basic idea

Delay X, Y signals are each T X- , T the Y , Z will be the output value of the capture register
assumed T X- << T the Y