Cacls and ICacls
https://www.cnblogs.com/Aley/p/11089538.html
Need Study
Explanation:
Cacls: Displays or modifies access control list (ACL)
ICACLS: Displays or modifies specified on the discretionary access control list (Dacl) file and specify Dacl directory file to be stored.
Summary: Displays or modifies access control permissions
Related Terms:
A DACL ( Discretionary Access Control List) , which pointed out the permit and deny access to a user or group of users Control List, when a process needs to access secure object access, the system will check the DACL to determine the process. If an object is not DACL, the description of any people on this subject can have full access.
A the SACL (Acess the System Control List) , which indicates the set of access method on the object (such as: read, Xie, running, etc.) a list of access control for details
DACL and SACL constitute the entire Access Control List Access Control List , referred to as the ACL, ACL in each of us is called ACE (Acess Control Entry)
The above is a brief description of relevant terms DACL, SACL, ACL, ACE or the like.
Cacls using the format:
Cacls filename [/ T] [/ E]the User D [...]]
filename - to display the access control list (hereinafter referred to as ACL); /
T-- ACL change the current directory and all subdirectories of the specified file;
/ E - edit ACL instead of replacing;
/ C-- continues to deny access when an error occurs;
/ G the user: perm-- gives the specified user access rights. Perm can be R (read), W (write), C (change, write), F (complete control);
/ R user-- revoke access specified user (with only / E used together);
/ P User: perm-- alternative access specified user;
/ D user-- Deny specified user access
Example: the Windows system as an example
1. View the catalog and ACL
in E: \> Enter "Cacls file name" command prompt, and then it will list the Windows system user group and user access control permissions on the file name of the directory project. If you want to see CCE directory of all file access control permissions, enter "Cacls filename \?.?" Command.
2. And modify the directory ACL: file (filename) user (user name)
to set user access rights: We often have to modify the directory and file permissions, use Cacls command is very easy to do. To give the machine the following user user has full control over the file directory and all subdirectories under the E disk. At the command prompt, the dialog box "Cacls file / t / e / c / g user: f" command.
Alternatively access: replaces the native full control of the user as read only user. At the command prompt, the dialog box "Cacls file / t / e / c / p user: r" command.
Revoke access: To revoke local user full control of the user directory is also very easy to run at the command prompt "Cacls file / t / e / c / r user" can.
Deny user access: To deny users access to user file directory and all subdirectories, run "Cacls file / t / e / c / d user" can be.
Calcs command a virus call the following example:
Virus process: c: \ documents andsettings \ administrator \ local settings \ temp \ tp5.tmp
Behavior: Create a new process
Goal: c: \ windows \ system32 \ cacls.exe
Command line: cacls.exeC: \ WINDOWS \ system32 \ cmd.exe / e / t / g everyone: F
Meaning is to give everyone a user group (owner) cmd.exe full control
ICacls using the format: (The following parameters shown in the table)
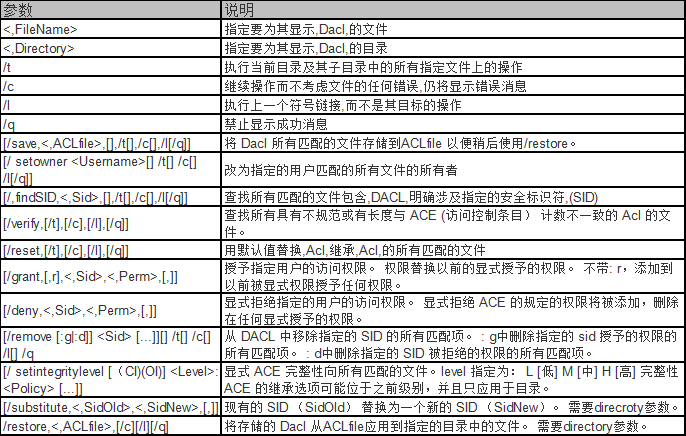
ICacls file name / save Tofile [/ T] [ / C] [/ L] [/ Q]: matches the name of the file DACL stored tofile so with future / restore used together.
Directory icacls [/ `substitute 'SidOld SidNew [...]] / Restore tofile: DACL is applied to the stored files in the directory.
ICacls file name / reset [/ T] [/ G] [/ L] [/ Q]: change the owner of all matching names, this option does not force change all identities, using takeown.exe utility for this purpose.
ICacls file name / findsid Sid [/ T] [ / C] [/ L] [/ Q]: Find all matching names ACL explicitly contain the SID.
ICacls all files find its ACL irregular or inconsistent with ACE length count: File name / verify [/ T] [/ C] [/ L] [/ Q]
ICacls filename / reset [/ T] [/ C] [/ L] [/ Q]: to use the default inherits all matching documents replace the ACL ACL
ICACLS 文件名 [/grant[:r] Sid:perm[...]]
[/deny Sid:perm [...]]
[/remove[:g|:d]] Sid[...]] [/T] [/C] [/L]
[/setintegritylevel Level:policy[...]]
/ Grant [: r] Sid: perm grants the specified user access rights. If you use the: r,
These permissions will replace all previously granted explicit permissions.
If you do not use: r, these permissions will be added to all previously granted explicit permissions.
/ deny Sid: perm explicitly deny user access to specified.
Permissions will add the listed explicitly denied ACE,
and remove all the same rights explicitly granted permission in.
/ remove [: [g | d ]] Sid delete all occurrences of the ACL SID. Use
: g, will remove all permissions for that SID. Use
: d, will refuse to delete all permissions for that SID.
/ setintegritylevel [(CI) (OI )] The integrity level ACE explicitly added to all
matching files. To specify the level of one of the following levels:
L [OW]
M [edium]
H [IgH]
inheritance option integrity ACE may take precedence level, but applies only to
the directory.
/ Inheritance: E | d | r
E - enable inheritance
d - disable inheritance and copy ACE
r - remove all inherited ACE
Note: Sid may be in digital format or friendly name format. If a given digital format, then add a * at the beginning of the SID.
/ T indicates to do this in the name of the specified directory on all matching files / directories.
/ C indicates that this operation will continue on all file errors. An error message will be displayed.
/ L indicates that this operation is performed on the symbolic link itself rather than its objectives.
/ Q indicates the icacls should be prohibited success message is displayed.
ACE canonical order ICACLS reserved items:
explicitly denied
explicitly granted
denied inherited
inherited grant
Note:
In parenthesis to specific permissions comma-separated list:

perm is a permission mask, you can specify one of two formats:
simple rights Sequence:
F - full access
M - modify permissions
RX - read and execute permissions
R - read-only access
W - Write-only permissions
inheritance rights can take precedence over every formats, but only applies to
the directory:
(OI) - objects inherit
(CI) - container inherit
(IO) - inherit only
(NP) - does not propagate inheritance
Example:
c icacls: \ Windows \ * / AclFile the Save / T
- the c: \ windows and all files in subdirectories
save ACL to AclFile.
c icacls: \ windows \ / Restore AclFile
- will restore the c: \ windows within existing under its subdirectories AclFile
ACL of all files
File icacls / Grant Administrator: (D, WDAC)
- will grant a user deletes a file and write the DAC pipe
administrator privileges
File icacls / Grant * S-1-1-0: (D, the WDAC)
- will be granted to the user by the sid S-1-1-0 definition files deleted
except for DAC and write permissions
1, forcing all documents and files in the current directory folder, change the owner of subfolders under the administrators group (administrators) command:
takeown /f * /a /r /d y
2, all the d: \ directory under the file documents, subfolders NTFS permissions to modify only the administrators group (administrators) complete control (to delete all the existing NTFS permissions):
cacls d:\documents\*.* /T /G administrators:F
3, in the original d: \ files in documents directory, add NTFS permissions on a subfolder of the Administrators group (administrators) Full Control permissions (does not delete all the existing NTFS permissions):
cacls d:\documents\*.* /T /E /G administrators:F
4 to cancel the Administrators group (administrators) Full Control permissions (does not delete all the existing NTFS permissions):
cacls \\ Server \ Documents \% username % \ My Documents / t / e / r "mddq \ domain admins"
cacls \\ Server \ Documents \% username % \ Desktop / t / e / r "mddq \ domain admins"
Explanation:
Cacls: Displays or modifies access control list (ACL)
ICACLS: Displays or modifies specified on the discretionary access control list (Dacl) file and specify Dacl directory file to be stored.
Summary: Displays or modifies access control permissions
Related Terms:
A DACL ( Discretionary Access Control List) , which pointed out the permit and deny access to a user or group of users Control List, when a process needs to access secure object access, the system will check the DACL to determine the process. If an object is not DACL, the description of any people on this subject can have full access.
A the SACL (Acess the System Control List) , which indicates the set of access method on the object (such as: read, Xie, running, etc.) a list of access control for details
DACL and SACL constitute the entire Access Control List Access Control List , referred to as the ACL, ACL in each of us is called ACE (Acess Control Entry)
The above is a brief description of relevant terms DACL, SACL, ACL, ACE or the like.
Cacls using the format:
Cacls filename [/ T] [/ E]the User D [...]]
filename - to display the access control list (hereinafter referred to as ACL); /
T-- ACL change the current directory and all subdirectories of the specified file;
/ E - edit ACL instead of replacing;
/ C-- continues to deny access when an error occurs;
/ G the user: perm-- gives the specified user access rights. Perm can be R (read), W (write), C (change, write), F (complete control);
/ R user-- revoke access specified user (with only / E used together);
/ P User: perm-- alternative access specified user;
/ D user-- Deny specified user access
Example: the Windows system as an example
1. View the catalog and ACL
in E: \> Enter "Cacls file name" command prompt, and then it will list the Windows system user group and user access control permissions on the file name of the directory project. If you want to see CCE directory of all file access control permissions, enter "Cacls filename \?.?" Command.
2. And modify the directory ACL: file (filename) user (user name)
to set user access rights: We often have to modify the directory and file permissions, use Cacls command is very easy to do. To give the machine the following user user has full control over the file directory and all subdirectories under the E disk. At the command prompt, the dialog box "Cacls file / t / e / c / g user: f" command.
Alternatively access: replaces the native full control of the user as read only user. At the command prompt, the dialog box "Cacls file / t / e / c / p user: r" command.
Revoke access: To revoke local user full control of the user directory is also very easy to run at the command prompt "Cacls file / t / e / c / r user" can.
Deny user access: To deny users access to user file directory and all subdirectories, run "Cacls file / t / e / c / d user" can be.
Calcs command a virus call the following example:
Virus process: c: \ documents andsettings \ administrator \ local settings \ temp \ tp5.tmp
Behavior: Create a new process
Goal: c: \ windows \ system32 \ cacls.exe
Command line: cacls.exeC: \ WINDOWS \ system32 \ cmd.exe / e / t / g everyone: F
Meaning is to give everyone a user group (owner) cmd.exe full control
ICacls using the format: (The following parameters shown in the table)

ICacls file name / save Tofile [/ T] [ / C] [/ L] [/ Q]: matches the name of the file DACL stored tofile so with future / restore used together.
Directory icacls [/ `substitute 'SidOld SidNew [...]] / Restore tofile: DACL is applied to the stored files in the directory.
ICacls file name / reset [/ T] [/ G] [/ L] [/ Q]: change the owner of all matching names, this option does not force change all identities, using takeown.exe utility for this purpose.
ICacls file name / findsid Sid [/ T] [ / C] [/ L] [/ Q]: Find all matching names ACL explicitly contain the SID.
ICacls all files find its ACL irregular or inconsistent with ACE length count: File name / verify [/ T] [/ C] [/ L] [/ Q]
ICacls filename / reset [/ T] [/ C] [/ L] [/ Q]: to use the default inherits all matching documents replace the ACL ACL
ICACLS 文件名 [/grant[:r] Sid:perm[...]]
[/deny Sid:perm [...]]
[/remove[:g|:d]] Sid[...]] [/T] [/C] [/L]
[/setintegritylevel Level:policy[...]]
/ Grant [: r] Sid: perm grants the specified user access rights. If you use the: r,
These permissions will replace all previously granted explicit permissions.
If you do not use: r, these permissions will be added to all previously granted explicit permissions.
/ deny Sid: perm explicitly deny user access to specified.
Permissions will add the listed explicitly denied ACE,
and remove all the same rights explicitly granted permission in.
/ remove [: [g | d ]] Sid delete all occurrences of the ACL SID. Use
: g, will remove all permissions for that SID. Use
: d, will refuse to delete all permissions for that SID.
/ setintegritylevel [(CI) (OI )] The integrity level ACE explicitly added to all
matching files. To specify the level of one of the following levels:
L [OW]
M [edium]
H [IgH]
inheritance option integrity ACE may take precedence level, but applies only to
the directory.
/ Inheritance: E | d | r
E - enable inheritance
d - disable inheritance and copy ACE
r - remove all inherited ACE
Note: Sid may be in digital format or friendly name format. If a given digital format, then add a * at the beginning of the SID.
/ T indicates to do this in the name of the specified directory on all matching files / directories.
/ C indicates that this operation will continue on all file errors. An error message will be displayed.
/ L indicates that this operation is performed on the symbolic link itself rather than its objectives.
/ Q indicates the icacls should be prohibited success message is displayed.
ACE canonical order ICACLS reserved items:
explicitly denied
explicitly granted
denied inherited
inherited grant
Note:
In parenthesis to specific permissions comma-separated list:

perm is a permission mask, you can specify one of two formats:
simple rights Sequence:
F - full access
M - modify permissions
RX - read and execute permissions
R - read-only access
W - Write-only permissions
inheritance rights can take precedence over every formats, but only applies to
the directory:
(OI) - objects inherit
(CI) - container inherit
(IO) - inherit only
(NP) - does not propagate inheritance
Example:
c icacls: \ Windows \ * / AclFile the Save / T
- the c: \ windows and all files in subdirectories
save ACL to AclFile.
c icacls: \ windows \ / Restore AclFile
- will restore the c: \ windows within existing under its subdirectories AclFile
ACL of all files
File icacls / Grant Administrator: (D, WDAC)
- will grant a user deletes a file and write the DAC pipe
administrator privileges
File icacls / Grant * S-1-1-0: (D, the WDAC)
- will be granted to the user by the sid S-1-1-0 definition files deleted
except for DAC and write permissions
1, forcing all documents and files in the current directory folder, change the owner of subfolders under the administrators group (administrators) command:
takeown /f * /a /r /d y
2, all the d: \ directory under the file documents, subfolders NTFS permissions to modify only the administrators group (administrators) complete control (to delete all the existing NTFS permissions):
cacls d:\documents\*.* /T /G administrators:F
3, in the original d: \ files in documents directory, add NTFS permissions on a subfolder of the Administrators group (administrators) Full Control permissions (does not delete all the existing NTFS permissions):
cacls d:\documents\*.* /T /E /G administrators:F
4 to cancel the Administrators group (administrators) Full Control permissions (does not delete all the existing NTFS permissions):
cacls \\ Server \ Documents \% username % \ My Documents / t / e / r "mddq \ domain admins"
cacls \\ Server \ Documents \% username % \ Desktop / t / e / r "mddq \ domain admins"