1, system security assessment of password There are three main methods:
(1) unconditional security
of this evaluation method to consider is assumed that the attacker has unlimited computing resources, but still can not decipher the password system.
(2) computing security
of this method is the use of the best way to calculate the break it needed computing resources far beyond the level of the attacker, you can define the password system is safe.
(3) can prove the safety of
this approach is to password security system comes down to a certain depth study of mathematical problems (such as a large integer factorization, discrete logarithm calculation, etc.), it proved difficult to solve mathematical problems. The problem with this approach is that it only explanation assess the security of the password method associated with a difficult problem, there is no absolute proof that the security problem itself, and give proof of their equivalence.
2, the actual security
For practical applications cryptographic system, due to the presence of at least one deciphering method, i.e., brute-force attack, and therefore can not meet the unconditional security, only provides security calculated. Password system to achieve real security, we must meet the following criteria:
(1) to decipher the actual computation of the cryptographic system (including the calculation of time or cost) is huge, so that in fact can not be achieved.
(2) the calculation time required for deciphering the code system of encrypted information over a useful life cycle. For example, fighting the war launched attack combat command only needs to be kept confidential before the battle started; important news messages before publicly reported the need for confidentiality of time is often only a few hours.
(3) to decipher the password system costs more than the value of the information itself is encrypted.
If a password system can meet one of the above criteria it can be considered to meet the actual security.
3, provable security
3.1 may prove three elements of security system
In provable security system, there are three elements: security model , security definitions and difficult issues .
Security model is divided into rival security objectives and capabilities . Security target describes the security model to achieve what degree of security, for example, indistinguishability for encryption algorithm (Indistinguishablity referred IND), for the non-existence of the forged signature algorithm (Existable Unforgeble referred to as the EU) and so on.
Wherein indistinguishability (IND) also called semantically secure (the Semantic scurity) , as defined below. Even if a ciphertext obtained adversary can not get any information corresponding plaintext, even if the information 1bit. Which is a formal representation: known m0, m1 and Cb = Enc (pk, mb) , or where m0 m1 m0 is an arbitrary one, i.e., Cb is m0, m1, wherein one of the ciphertext, the adversary can not effectively Analyzing the encryption process in the end b is 0 or 1.
3.2 Security Definitions
Characterization capabilities rival, there are four main, chosen-plaintext attack (Chosen Plaintext Attacke referred to as the CPA), chosen ciphertext attack (Chosen Ciphertext Attack referred to the CCA), but ciphertext attack (Ciphertext-Only Attack), a known plaintext attack (Known Plaintext Attack). Characterization common front two rival ability, chosen-plaintext attack (CPA) refers to a rival can be chosen-plaintext and the corresponding ciphertext . Chosen ciphertext attack (CCA) refers to the adversary can not only get chosen plaintext ciphertext, can choose a limited number of ciphertext to obtain a corresponding plaintext . CCA ability adversary stronger than CPA description.
Here are some common security definitions.
CPA security. We have chosen-plaintext attack (CPA) described as a game in order to facilitate better understanding. First of all make it clear that the aim of the game is to break the system of choice indistinguishable under the premise of plaintext attacks (Indistinguishablity) , so the following referred to this game as a CPA-IND . Furthermore, we should define the role of two rival challenger C and A. Challenger (challenger) making the task of the referee, presided over the game and the behavior of rival feedback. Adversary name suggests, is to attack the current system, but also for the game is the use of chosen plaintext attack method of attack. Description of the game are as follows:
A. Initialization: Create IND-CPA Challenger C system, and transmits the public key to the adversary A.
B. A selected adversary two identical plaintext length m0, m1 to a challenger C. C challenger randomly selected B ∈ {0,1}, and mb applied chronograph as cb , and then transmits the ciphertext to the adversary A cb .
C. adversary A guess step of encrypting the plaintext challenger is C or m0 m1, and outputs the guess result, the output denoted as b '. If b '= b, then the adversary success.
Adversary advantage can be defined as the following functions:
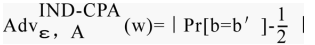
Where w is the length of an encryption key scheme. Because random guessing there is a probability of 1/2 to win the game IND-CPA. and so
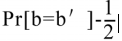
After the adversary is trying to get the advantage. If for any polynomial time adversary A, there is a negligible advantage of [sigma], such that
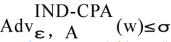
Then call this encryption algorithm indistinguishability under chosen-plaintext attack, otherwise known as IND-CPA security.
3.3 difficult problem
With security models and security definitions, generally use the statute to difficult problems to security proof. Cryptography has difficulties commonly used discrete logarithm problem (discrete logarithm problem, referred to as DLP), CDH problem (Computational Diffie-Hellman), DDH problem (Decisional Diffie-Hellman) and BDH problem (Bilinear Diffie-Hellman).
3.4 provable security theory
With the previous model describes the safety, security definitions, difficult issues, with the front license describes the security model, security definitions, difficult issues, provable security system is also feasible. Provable security is a method of using the "Statute", the methodologies attack cryptographic algorithms or security protocol on the Statute of the attack to a difficult problem. First, determine the encryption system security objectives, such as security objectives signature scheme is not be forged signatures (Existable Unforgeble), safety goals are indistinguishable encryption system of information (Indistinguishablity). Then determine the ability of rivals to build a security model based on security definitions.
Statute is a conceptual complexity theory, the problem to a problem P1 P2 refers statute, resolution algorithm known problems P1 and M1, we can construct another algorithm M2, M2 M1 as a subroutine may be used to solve the problem P2.
Methods used in the statute on security proof security cryptographic algorithms or protocols, for example, adversary of the Statute of the cryptographic algorithms or security protocol (P1) can be some difficult issues have been studied in depth (P2). That is, if the adversary can mount an effective attack on the algorithm or protocol, you can use an algorithm to build a rival to break the difficult problem, however, is a difficult problem that has been proven not compromised, so there is a conflict. According to reductio ad absurdum, the adversary can break the algorithm or protocol assumption does not hold, QED.
In general, in order to prove the safety of Scheme 1, we can Scenario 1 Scenario 2 to the statute, that is, if the adversary can break scheme 1 A, then B is also an adversary can attack Option 2, and Option 2 has been shown to be safe or a problem.
The proof is described by a thinking game. First, create a scenario Challenger 2, B represents a rival in Scheme 2, Scheme 1, A represents the adversary. B To break scheme 2, using as a subroutine to attack A in Scheme 1. A B wants to use, you need to train A, so B A simulation of a challenger.
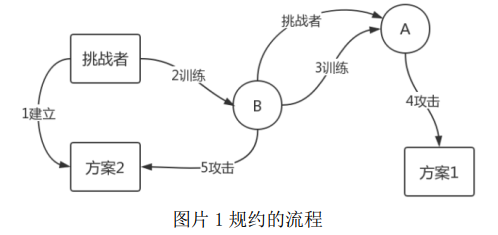
For example, if you want to prove the security of encryption algorithm, then Option 1 is a specific encryption algorithm. The goal is assumed that the security information indistinguishability (Indistinguishablity), the ability of the adversary A is chosen-plaintext attack, i.e. CPA. A simulated adversary challenger adversary B performs IND-CPA and A game. In the course of the game, B in order to achieve the purpose of using their own A. If A and B are unable to judge their own or with the challenger playing games, then B is called simulation complete.
For other encryption algorithm or encryption protocol, we must first determine the security objectives it wants to achieve, for example, can not be forged signature scheme, and then determine the ability of rivals to build a security model based on security definitions, then the encryption algorithm or encryption attack of the Statute of the agreement on difficult issues has been proven. This is provable security.
Conclusion: provable security theory is the theory of cryptography and computational complexity theory of a perfect combination, the cornerstone of modern cryptography. In the past 30 years - the biggest breakthrough in modern cryptography is the cryptographic system based on computational complexity theory, which makes cryptography from an art developed into a rigorous discipline.
https://blog.csdn.net/wangtingyao1990/article/details/79475842?utm_source=blogxgwz5
"Talking about modern cryptography and provable security theory" - Liu Yan Pei