Traffic control technology
▪ Traffic Manipulation Technique
▪ penetration testing often encountered in a network environment with limited access
▪ use covert means to evade security measures and check source tracking
▪ proof seemingly strict access control weaknesses still exist
▪ non-trusted network for secure data transmission in the
implementation process ▪ slightly burned part of the concept of brain
▪ redirection (Redirection)
- IP, Port
▪ tunnel (Tunneling)
- for secure communication in an untrusted network environment
- usually establish a communication tunnel using a variety of encryption technologies
- point (IP2IP), end ( Port2Port) tunnel
- the VPN: PPTP, L2TP, the IPSec, the SSL VPN
▪ encapsulated (encapsulation)
- commonly used in conjunction with the tunnel, a protocol using a protocol encapsulation (the RPC O HTTP, the VoIP)
- using a gateway device to implement different types of networks interoperability
Redirection
▪ rinetd
- Installation: APT-GET install rinetd
- Configuration: etc / rinetd.conf
▪ BINDADD bindport connectadd The ConnectPort
- run: rinetd
▪ scenarios
- redirect web traffic breakthrough Internet restrictions
- Remote Desktop Redirection
- NC redirect get shell
- is not compatible with other secondary connection FTP protocol
▪ install a firewall monowall

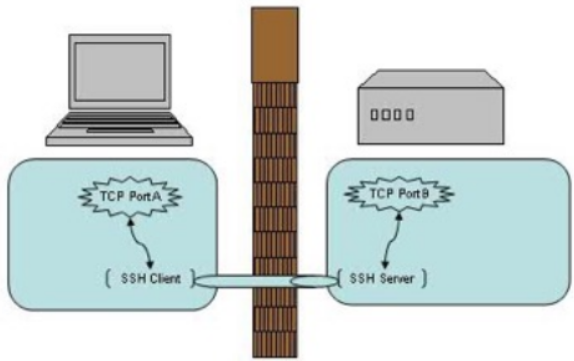
SSH tunnel
▪ SSH supports two-way communication tunnel
- the other communication TCP port forwarding through SSH link
- using SSH as a transport layer protocol, automatic encryption and decryption of traffic
- Limit break through the firewall access rules that can be used over the wall
▪ SSH local port forwarding
- the effect is similar to rinetd
- the local port and a remote server to establish tunnel
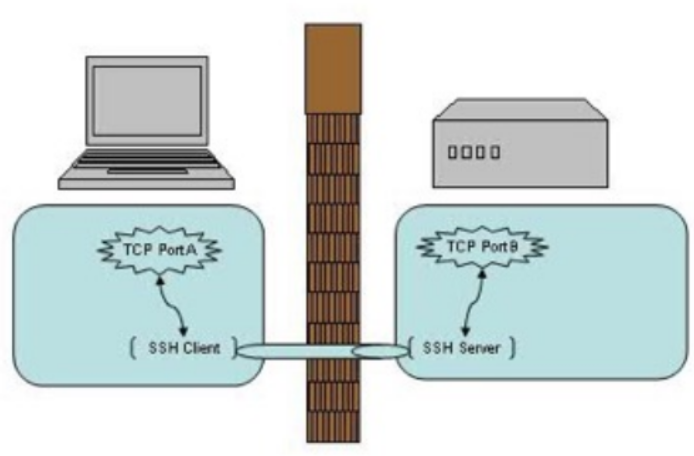
▪ Establish two-way secure tunnel
- the other communication TCP port forwarding through SSH link
- using SSH as a transport layer protocol, automatic encryption and decryption of traffic
- Limit break through the firewall access rules that can be used over the wall
▪ local port forwarding
- Local investigation listen to port, access to the remote host specified port forwarding
▪ remote port forwarding
- remote listening ports, access to the local host to forward the specified port
▪ dynamic tunneling protocol