In some cases, a customer can not or do not want direct access to another object, then you need to find an intermediary to help complete a task, this is the intermediary proxy object. For example, do not necessarily go to the train station to buy train tickets to buy, you can go through the 12306 website or ticket outlets to buy. Another example is to find a girlfriend, looking for a nanny, find a job and so can find an intermediary to complete.
First, the definition
For some reason you need an object to provide a proxy to control access to the object. In this case, the object does not fit or can not access a direct reference to the target object, a proxy object as an intermediary between the access and target objects.
Second, the structure and mode of realization
1. Structure Model
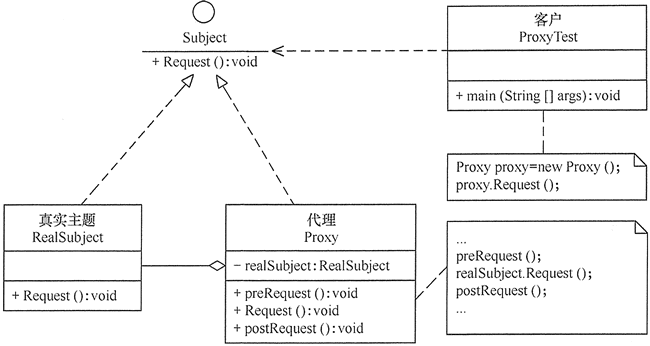
The main role of proxy mode is as follows:
- Abstract topics (Subject) categories: real business methods and themes proxy object achieved by the interface or abstract class declaration.
- Real theme (Real Subject) category: abstract achieve specific business topics, real object is represented by a proxy object, the object is to be the ultimate reference.
- Proxy (Proxy) class: provides the same interface with the real theme, the interior contains a reference to the real subject, it can access, control, or extend the functionality of the real theme.
2. Mode of realization
Scene Three application, mode
- Remote Agent, this approach is usually to hide the fact that the target object exists in different address spaces, to facilitate client access. For example, when users apply some network disk space, creates a virtual hard disk in the user's file system, users access the virtual hard disk is actually access the network disk space.
- Alerts, this approach is typically used when you want to create audience much overhead. For example, downloading a large image takes a long time for some short period of time to calculate more complex and can not be completed, then you can start with a virtual agent to replace real objects small proportion, eliminate the user the feeling of a slow server.
- Security agent, this approach typically used to control different types of customers access to the real object.
- Intelligent guidance is mainly used when calling the target object, a proxy attach some additional processing functions. Calculating a real object, for example increased, the number of reference function, so that when the object is not referenced, it can be automatically released.
- Lazy loading, refer to in order to improve system performance, delayed loading of the target. For example, the Hibernate on the existence and properties associated delay loading delay loading table.
Advantages and disadvantages of four modes
The main advantage of proxy mode are:
- Proxy mode to play a mediating role and protect the role of the target object between the client and the target object;
- Proxy object can extend the function of the target object;
- Client proxy mode capable of separating the target object, the coupling degree is reduced to some extent;
The main disadvantages are:
- Between the client and the target object is a proxy object to increase, will cause the slow request processing;
- Increases the complexity of the system;
Extended V. proxy mode
In proxy mode described earlier, the proxy class contains a reference to the real subject, there are two shortcomings of this approach:
- The real subject of correspondence with the agent theme, the theme should be increased to increase the real agent.
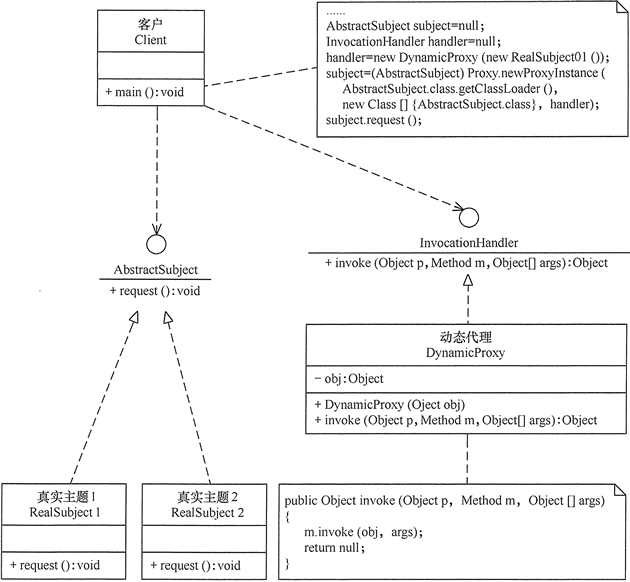
- Design agency before the real theme must already exist, less flexible. Dynamic proxy mode can solve the above problem, such as the Spring the AOP, the structure shown in Figure 4.