Public and private key
Application and development block chain technology, digital encryption technology is the key. Once the encryption was cracked, data security block chain will be challenged, not tamper resistance block chain will no longer exist. Into the encryption algorithm and a symmetric encryption algorithm asymmetric encryption algorithm, the main block chain applied an asymmetric encryption algorithm.
Asymmetric encryption means to meet security requirements and ownership verification requirements integrated encryption block chain. Asymmetric encryption is generally used in two asymmetric cryptographic encryption and decryption processes, the public and private keys are called. Asymmetric key pair has two characteristics:
First, after a key with which the encrypted information, only the other corresponding key to unlock.
Second, the public key can be exposed to other people, the private key is kept confidential, other people can not figure out the corresponding private key by the public key.
The main application of the asymmetric key cryptosystem there are two, namely, public key encryption and public-key authentication. Public key encryption and public key authentication process is not the same as, respectively, a brief introduction below.
Public key encryption
Encryption is a data encryption so that even if unauthorized users access to information encrypted and can not get the correct data content, data encryption can protect data against eavesdropping attack. The focus is data security.
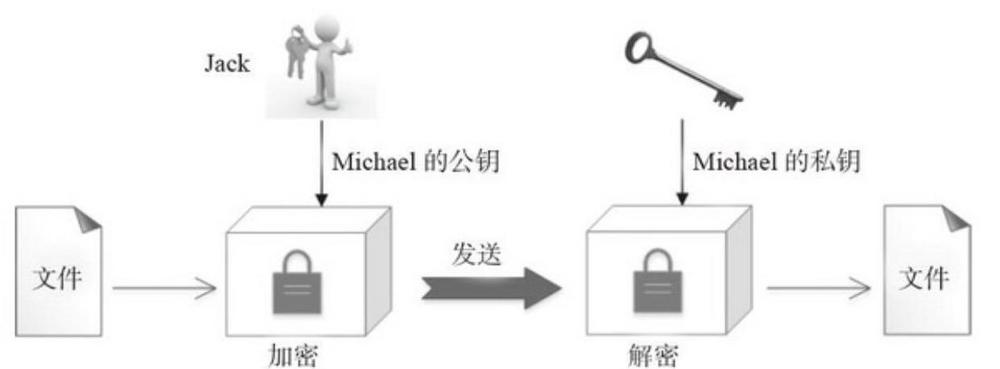
To make it easier for the reader to understand what is public key encryption, first look at a simple example. If two users and Michael Jack, Jack wants to send a text to the public key cryptography Michael, Michael and a pair of public and private keys, then the encryption and decryption process is as follows:
Michael sends his public key to Jack.
Michael Jack will use the public key to encrypt text, the result is sent encrypted to Michael. 3. Michael sent his message with his private key to decrypt Jack. The whole process as shown in FIG.
Public key authentication
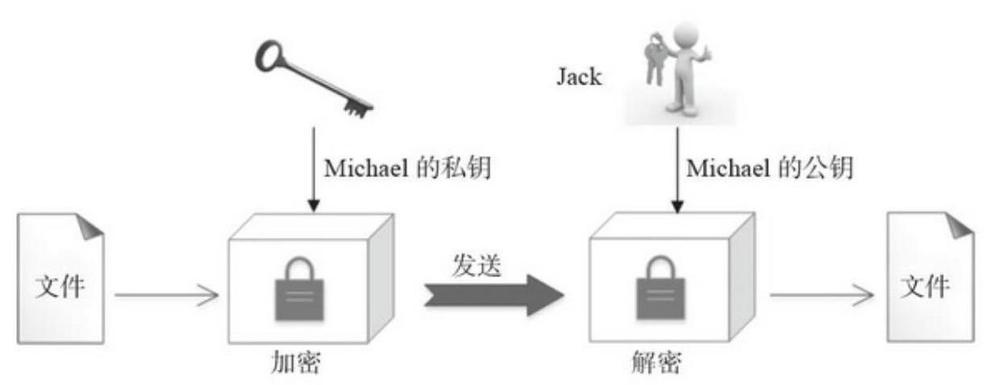
Authentication and encryption, is mainly used to identify the user's authenticity. Here we only able to identify a user's private key is correct, you can identify the user's authenticity. Cited a simple example, Michael let Jack know they are real Michael, not other people's fake, the entire authentication process is as follows:
Michael uses his private key to sign the document, sent to Jack.
Michael Jack use the public key to decrypt the file, if the decryption is successful, the proof of Michael's private key is correct, and thus completes the authentication of Michael's. In order to verify the signature.
From the above two examples, the sender's public key encryption is first encrypted with the public, then the private key to decrypt the recipient, and the sender public key authentication is used to encrypt the private key, then the public key to decrypt the recipient To verify.
digital signature
In a distributed network of chain blocks, the conduct and communication between nodes to achieve trust, need to rely on a digital signature, digital signature related to public, private and wallets and other tools, it has two effects:
First, it proves that the message really is complicated by the sender signature by the information out.
Second, to determine the integrity of the message.
Digital signature technology is summary information encrypted with the sender's private key, transmitted to the recipient along with the original. Only the recipient of the sender's public key can decrypt the encrypted summary information, and then produce a summary of the information received with the original HASH function, comparative summary information and decryption. If so, then the information received is complete and has not been modified in transit, or explanatory information has been modified. Therefore, the digital signature can verify the integrity of the information.
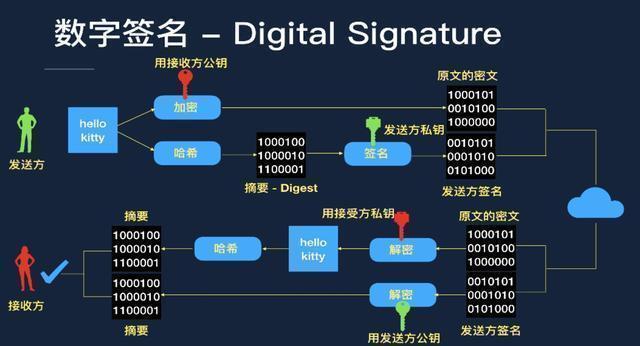
We use an example to illustrate, look at the FIGS., The sender of the message hello kitty double treatment:
1 is carried out by the recipient public key encryption ciphertext.
Why recipient's public key to encrypt? Because only the recipient's private key can unlock the recipient's public key plus too close, to ensure that only the recipient can decrypt.
2. hello kitty obtained hash digest, followed after the sender signed the private key, the signature sent to the recipient with the derived cipher text and the digital signature.
Why use the sender's private key signature? Because this way, in order for the recipient to confirm this information is sent to the sender. Only the sender's public key to unlock the signature of the sender.
Similarly recipient received information (cipher text and the digital signature) the following process steps:
1. own private key to unlock the ciphertext to obtain hello kitty.
2. hello kitty get a hash digest.
3. unlock the sender signature by the sender's public key to obtain a summary.
4. Summary of decrypting the ciphertext decrypts the digital signature and summary of comparison, if the same summary, acknowledgment information may be issued to the sender, and the integrity of the information.
to sum up
Digital signature is a certification tool that can be easily identified, because it just solving a mathematical problem on a computer to verify the nature of its process. Therefore, the blink of an eye you can complete the certification process, do not like people than writing or as time-consuming to seal laborious.
By digitally signed our main achievement:
1, before being received by the identity of the sender public key authentication of the sender
2, by way of signature private key, others can not forge the signature information
3, the sender also can not deny the signature of the information by the private key signature
4, the digital Abstract technology to ensure data integrity
5, the hash function also ensures that the data is not available any tampering
TA and obviously did not meet, but in the world of bits, digital signatures, but allows you to see words such as face.