0x00
whois information collection http://whois.chinaz.com/ ip query https://site.ip138.com/ ip locate https://www.opengps.cn
subdomain blasting https://phpinfo.me/domain/ port scanning namp, masscan the like
as well as directory scan sweep sword like tool not to mention
0x01
Middleware identification: apache, nginx, iis, weblogic
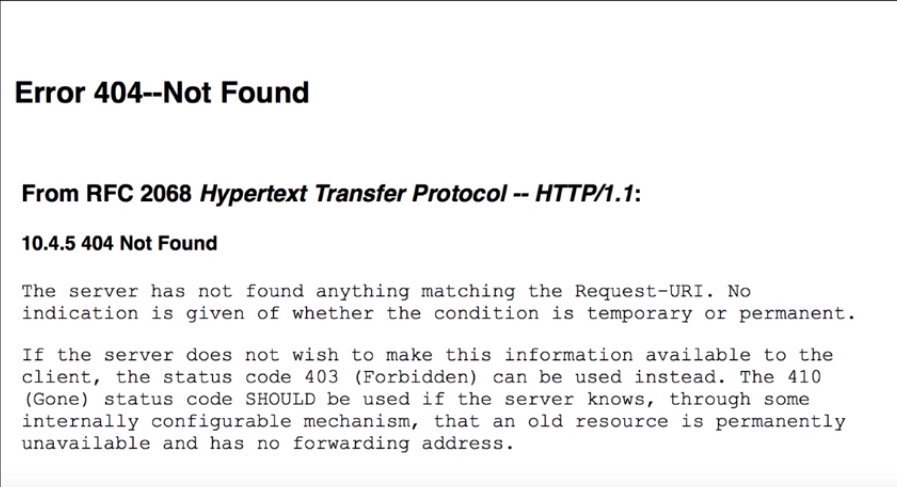
The error page identifier 404, different
apache:

iis:

nginx:

weblogic:
Web development language recognition: php, java, asp, etc.
-
-
According http header content judgment: X-Powered-By field, Server field, Cookies in SESSIONID
-
Using the browser plug: W3techs
0x02
cms recognition:! Wordpress, Drupal, Thinkphp, Discuz, Dedecms etc.
-
Check the footer or web page source code, copyrights and other information on whether there
-
Website Recognition
Online website http://whatweb.bugscaner.com/look/ http://www.yunsee.cn/finger.html
Local tool https://github.com/Ms0x0/Dayu
In fact, there are many real aspects of information gathering, it just said something ordinary common
There is a set of information-gathering tool: https://github.com/hannoch/scaner