windows RDP remote code execution vulnerability reproduce _CVE-2019-0708
I. Overview of vulnerability
May 14, 2019 the official Microsoft release security patches, fixes a remote code execution vulnerability windows remote desktop services, the vulnerability affects certain older versions of Windows. This vulnerability is a pre-authentication and without user interaction, which means that the vulnerability can be exploited over a network worm ways. Exploited this vulnerability could spread any malware from an infected computer to other computers vulnerable.
Second, the flaw affects versions
Windows 7
Windows server 2008 R2
Windows server 2008
Windows 2003
Windows xp
Note: Windows 8 and windows10 version, and later affected by this vulnerability
Third, the vulnerability environment to build
Target: windows 7 IP: 192.168.10.171
Attacker: kali system, another Win7 (python3 installation environment, the installation module impacket)
Conditions: The target machine to open the 3389 port, turn off the firewall
Fourth, the vulnerability reproduction
1, 3389 target port, turn off the firewall (or 3389 release ports in the firewall policy)
2, using the corresponding msf module verifies if there are loopholes
2.1, the upgrade version msf
apt-get update
apt-get install metasploit-framework
Note: do not upgrade msf, use msf v4 load third-party version of the script, will complain, probably just because cve-2019-0708 scripts only compatible with the latest version of msf (msf v5)
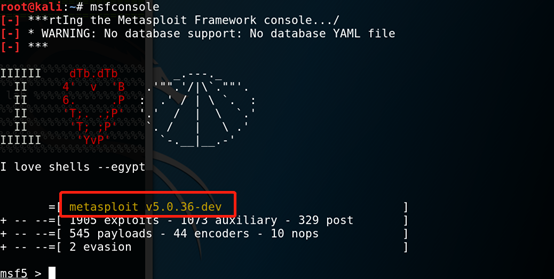
2.2, start msf, you can see the current version msf
2.3, search cve-2019-0708 Scripts

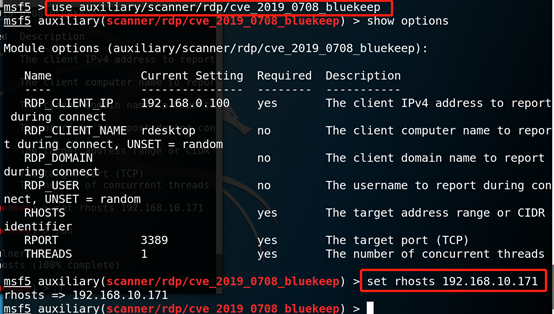
2.4, using a script, set the parameters
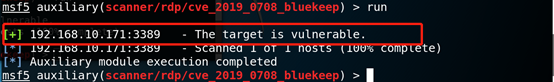
2.5, began to attack, the target figure below illustrates a vulnerability
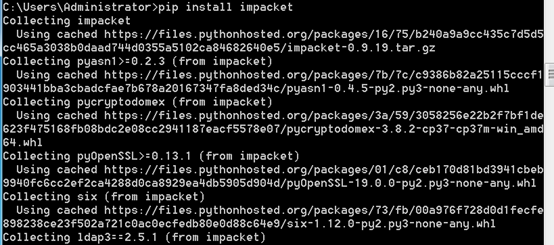
3, win7 attack installation python3.6, module mounting impacket
4, download POC, and then run the POC
POC Download: https://github.com/n1xbyte/CVE-2019-0708
5, after the POC run, the target machine blue screen
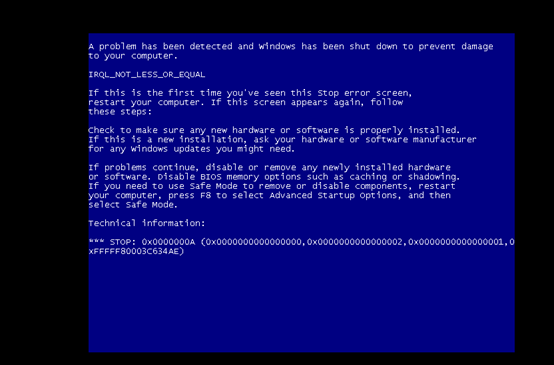
6、下载补丁,安装补丁,补丁下载地址: https://portal.msrc.microsoft.com/zh-cn/security-guidance/advisory/CVE-2019-0708
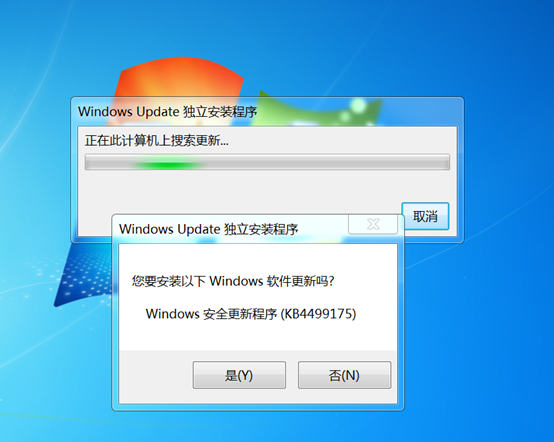
7、安装完补丁之后,需要重启电脑,补丁才能生效,再次验证目标机,下图可以看到目标不存在漏洞了 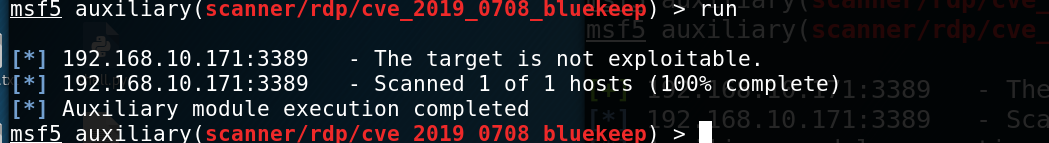
五、漏洞防御
1、 关闭远程桌面、开启防火墙
2、 更新系统