
QQ 1274510382
Wechat JNZ_aming
Business Alliance QQ group 538250800
Technology trouble QQ group 599020441
Solution QQ group 152889761
Join us QQ group 649347320
Shared learning QQ group 674240731
Chronological technology aming
network security, deep learning, embedded, machine enhancement, biological intelligence, life science .
Ding Ding Ding: The product is online—>Follow the official-WeChat public
account —Jinan Ji Nian Information Technology Co., Ltd. People’s livelihood project: store franchise/entertainment dating/startup business circle/outsourcing part-time development-project release/
security project: situational awareness defense system /Intranet inspection system
Cloud service project: dynamic expansion of cloud host/domain name/elastic storage-database-cloud disk/API-AIeverthing
product consulting/service after-sales (same)
It's always shallow on paper, and I absolutely know that I have to do it! ! !
Looking for like-minded partners to start a business. . . Baotuan Didi aming contact information! !
#This article is the advertising system automatically serving ads
# If there is any infringement, deletion, please contact us quickly
Kernel caching is enabled by default in IIS to perform tasks related to caching in the request processing pipeline.
When the HTTP protocol stack (HTTP.sys) incorrectly parses the HTTP request, it will cause the IIS remote code execution vulnerability.
Through experiments, learn about the
IIS architecture, HTTP protocol stack and how it works, and HTTP protocol stack vulnerabilities, and
master the MS15-034 vulnerability exploitation methods and vulnerability principles.
Web security
Information security practitioners
Computer foundation, computer network
Preliminary knowledge
Vulnerability information
Vulnerability Number: CVE-2015-1635
Vulnerability description: The
IIS remote code execution vulnerability exists in the HTTP protocol stack (HTTP.sys).
This vulnerability can be caused when HTTP.sys incorrectly parses HTTP requests.
Microsoft's announcement on vulnerabilities: https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2015/ms15-034
Affected version: Windows Server 2008 R2/Server 2012/Server 2012 R2 and Windows 7/8/8.1
installed with Microsoft
IIS 6.0 or higher
are all affected by this vulnerability.
IIS architecture

After installing IIS (Internet Information Service) on the system,
There is a service called World Wide Web Publishing Service (WWW Service).
When the client sends an HTTP request to the system, the
WWW service will start or select the worker process w3wp.exe based on the load balancing strategy
to process the HTTP request and send an appropriate HTTP response.
The w3wp.exe process uses HTTP.sys to complete many tasks related to HTTP protocol processing,
including HTTP protocol analysis, response content assembly and content caching.
HTTP.sys receives HTTP requests and sends HTTP responses through TCPIP.sys.
HTTP protocol stack and how it works
The IIS Web server uses the HTTP listener as a part of the Windows network subsystem,
which is implemented by the kernel mode device driver of the HTTP protocol stack (HTTP.sys). The
HTTP protocol stack parses HTTP requests and provides responses to the client.
HTTP.sys provides the following services in IIS 6.0: routing HTTP requests to the correct request queue; caching responses in kernel mode; performing all text-based logging for WWW services; implementing quality of service functions, including connection restriction, connection timeout, Queue length limit and width limit.
When creating a website, IIS will use HTTP.sys to register the website, and then HTTP.sys will receive all HTTP requests to the website. The function of HTTP.sys is similar to a forwarder. It sends the received web request to the request queue running the user mode process of the website or web application, and sends the response back to the client.
In addition to retrieving the stored response from its internal cache, HTTP.sys does not process the requests it receives. Therefore, application-specific code is not loaded into kernel mode, so errors in application-specific code will not affect the kernel or cause system failure.
HTTP protocol stack vulnerability
Kernel caching is enabled by default in IIS to perform tasks related to caching in the request processing pipeline.
Caching improves performance by storing processed information (such as web pages) in memory on the server.
Use the Range HTTP header to exploit this vulnerability.
This HTTP header allows the client to request specific content from the server as needed.
Usually the Range header contains the following values:
Range: bytes=124-5656, may also contain the following values: Range: bytes=0-
If the upper limit in the Range header does not exist,
it is assumed that the client is requesting complete data.
On the contrary, if the attacker specifies a high upper limit and sends an HTTP request with a special Range value, it
will cause the Range variable to overflow on the server.
The upper limit of the Range header is 0xFFFFFFFFFFFFFFFFFF,
which is the largest 64-bit unsigned integer.
The attacker sends an HTTP request with this value, which will cause an integer overflow, and the
server will respond as'the requested range cannot be met', which means that the client requires a part of the file to exceed the end of the file on the server.
Successful exploitation of an attack can also lead to a denial of service.
IIS server security related experiments
IIS6.0 write permission vulnerability exploit: https://www.hetianlab.com/expc.do?ec=ECID172.19.104.182015102217203100001
IIS6.0 remote code execution 0day vulnerability analysis and exploitation: https://www.hetianlab.com/expc.do?ec=ECID9d6c0ca797abec2017032915142000001 (CVE-2017-7269)
IIS analysis vulnerability used in fckEditor upload attack: https://www.hetianlab.com/expc.do?ec=ECID172.19.104.182015102217243800001
Experiment purpose
To understand the IIS architecture,
HTTP protocol stack and how it works, and HTTP protocol stack vulnerabilities through experiments , and
master the vulnerability exploitation methods and vulnerabilities principles of MS15-034.
Experimental environment
Client: Windows Server 2008 R2, IP: 10.1.1.134
Attack:Kali,IP:10.1.1.100
Vulnerability exploitation tool download address: http://tools.hetianlab.com/tools/CVE-2015-1635.zip
Task description: vulnerability detection.
We know that this is an integer overflow vulnerability located in HTTP.sys.
Sending an HTTP request in the following format to the IIS server can trigger the detection of the vulnerability:
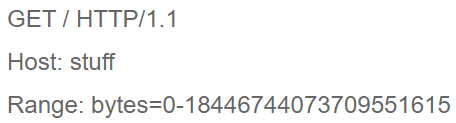

Kali machine executes the command curl url -H "Host:ip" -H "Range:bytes=0-18446744073709551615":

At this time, 18446744073709551615 converted to hexadecimal is 0xFFFFFFFFFFFFFFFF (16 F), which
is the largest integer that can be expressed by a 64-bit unsigned integer,
so the integer overflow must be related to this abnormal integer.
As shown above,
if the IIS server returns "requested range not satisfiable", then there is a vulnerability;
if it returns "the request has an invalid header name", then the vulnerability has been patched.
Download the script:
wget http://tools.hetianlab.com/tools/CVE-2015-1635.zip
unzip CVE-2015-1635.zip


Pay attention to modify the IP of the experimental machine:


Use POC for vulnerability detection:

Indicates that the target machine has a vulnerability.
Experimental step two
Task description: MS15-034 exploit attack: obtain memory data.
Kali machine opens msfconsole and searches for vulnerability related exploit modules:


Use the second module
ms15_034_http_sys_memory_dump to read server memory data:
HTTP protocol stack requests to process HTTP.SYS memory information disclosure.


Perform an attack:

Read server memory data successfully.

Experiment Step Three
Task description: MS15-034 exploit attack: denial of service attack.
Use the first module
ms15_034_ulonglongadd to carry out ddos attacks: HTTP protocol stack request processing denial of service

Configure the parameters and execute the attack:

Note: You can switch to the client before executing the attack, and feel the running state before and after the attack.



Successful performance of the client being attacked on the experimental machine:

Experiment Step Four
Vulnerability analysis: denial of service attack.
After sending the request to the HTTP Server,
w3wp.exe will process the HTTP request, and
TCPIP.sys will forward any HTTP protocol content to HTTP.sys.
If the request is within the HTTP range, the
function UlpParseRange() will be called to parse the request to obtain the start and end positions of the request range,
and calculate the length of the range.
When the start position is 0 and the end position is 0xFFFFFFFFFFFFFFFFFF, the
range length is equal to 0, the code does not check whether there is overflow, and does not take error handling measures;
When the start position is 284 and the end position is 0xFFFFFFFFFFFFFFFFFF, the
range length is equal to -284, and the hexadecimal value is 0xFFFFFFFFFFFFFFFEE4.
If it is interpreted as an unsigned integer, the value is very large.
After parsing the HTTP request, the function UlAdjustRangesToContentSize() will be called.
If the start position and length are'invalid'
(including the range start position is 0xFFFFFFFFFFFFFFFFFF, the range length is 0xFFFFFFFFFFFFFFFFFF, the
start position >= the requested web page length and the end position >= the requested web page length),
the function will adjust the range The starting position and length of the
If the same request is received continuously, the response to the request will be cached, and will be retrieved from the cache and sent to the requester.
This process will call the function UxpTpDirectTransmit() to calculate the length of the HTTP response packet.
After assembling the HTTP response package,
HTTP.sys will forward the packet information to the protocol stack driver for sending.
The function TcpSegmentTcbSend() of TCPIP.sys will traverse the contents of each part of the packet. There is an integer overflow in the function.
When the start position of the HTTP range request is 284 and the
end position is 18446744073709551615 (hexadecimal value is 0xFFFFFFFFFFFFFFFFFFFF), the
range exceeds the size of the requested web page file.
Because the HTTP response length is very large, when the loop runs multiple times and an integer overflow is triggered,
the virtual address will be used to construct a partial memory descriptor list. Because the range is not a sub-range of the source range, it will cause a blue screen of death.
Experimental step five
Vulnerability analysis: Get memory data.
Suppose that 3-18446744073709551615 is set to range1 and
1-600 is set to range2.
After the function UlpParseRange() parses the HTTP request,
the function UlAdjustRangesToContentSize() will be called.
At this time, range1 will trigger an integer overflow (3+0xFFFFFFFFFFFFFFFD>=0).
If the same operation is received continuously, the response to the request will be cached, retrieved from the cache and sent to the requester.
By using multiple scope requests,
there is a scope binding tag and scope information before each scope content.
After assembling the HTTP response package, HTTP.sys will forward the packet information under the protocol stack driver for sending.
The function TcpSegmentTcbSend() of TCPIP.sys will traverse each part of the data packet.
Using multi-range requests can increase the length of the HTTP response, thereby revealing more information.
If only a single range is used, the HTTP response length becomes too large or too small:
If the HTTP response length is too large, the system will cause a blue screen of death;
if the HTTP response length is too small, the buffer will not be overwritten after the target webpage content leaks information.
Therefore, the attacker will use multi-range requests to disclose more information.
Bug fixes
Disable enabling kernel caching in the output cache (disable IIS kernel caching):


Analysis and thinking
For more analysis, see: https://blogs.360.cn/post/cve_2015_6135_http_rce_analysis.html.
reference
1、https://technet.microsoft.com/en-us/library/cc739400(v=ws.10).aspx
2、https://www.trendmicro.com/en_us/research/15/d/iis-at-risk-the-http-protocol-stack-vulnerability.html?_ga=2.58551274.1902911539.1609211638-1589647619.1609211638