July 16, 2019, Rancher Labs released a new version 2.2.5 Rancher, this version fixes a security vulnerability CVE-2019-13209 recently discovered, the official support Kubernetes 1.14, for the latest Kubernetes 1.15 also provides experimental support, In addition also brought a series of functions and optimization.
Currently, Rancher's Latest and Stable version information is as follows:
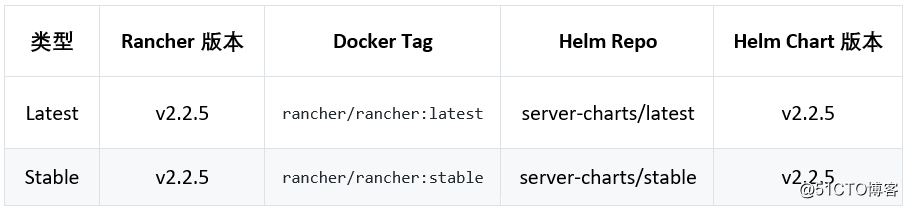
Fix CVE: CVE-2019-13209
Rancher 2.2.5 fixes a security vulnerability CVE-2019-13209 newly discovered. The problem was first discovered by Workiva of Matt Belisle and Alex Stevenson and reports, including the affected Rancher version v2.0.0-v2.0.15, v2.1.0-v2.1.10, v2.2.0-v2.2.4. Rancher v1.6 unaffected.
The vulnerability is called "cross-site Websocket hijacking ***." *** can be accessed by Rancher managed by the cluster's role *** / permissions. *** It requires the person to log on to the server Rancher, then visit hosted by a third-party developer sites. Once completed, developers can take advantage of the rights and identity of persons *** execute commands on Kubernetes API. More details can be viewed description:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-13209
Rancher 2.2.5 release in the same period, Rancher Labs also released the official Rancher v2.1.11 and v2.0.16, both versions also provide a fix for this vulnerability, available have not been upgraded to Rancher 2.2.x users.
Function and Optimization
Officially supported version Kubernetes 1.14
Add experimental support for Kubernetes 1.15 version
In Kubernetes 1.14 and above clusters, support CoreDNS provider as the default dns
In the UI-date information for the public certificate Rancher cluster configuration, and an alarm before the certificate expires 30 days
For Rancher directly configure a cluster, support for custom CA snapshot configuration, thereby S3 snapshot service will be trusted inside the signed certificate
Added support for Kubernetes v1.13 for EKS cluster
Bug fixes
The following are the major version fixes bug. You can reference the milestone Rancher for a complete list:
https://github.com/rancher/rancher/milestone/168
Fixed problem Rancher v2.2.4 upgrade to project members is not displayed in the user interface [20825]
Fix Computer Configuration node driver may be due to "run SSH command error" error and the reason for failure [20753]
Fixed an issue Minio configured as a backup destination overtime Etcd Snapshot [19496]
Fixed and HTTPS_PROXY provided HTTP_PROXY rancher-server environment variables to allow the container it contacts the public network, not the use of a functional configuration Rancher node driving node [20709]
Rancher configuration may cause problems in the cluster etcd repair damaged when deleting etcd members [19696]
Fixed an issue where the application update process helm overtime [20289]
Fixed crash Rancher once every 5 minutes sever problem in the configuration settings in the snapshot etcd [20964]
Fix the program if there is an error in the Catalog of the response, and the response is saved, the user can not fix the problem Catalog application [21027]
Fixed Rancher's Azure Cloud configure a cluster configuration problems when running multiple subscriptions can not have Service Principal [21124]
Ordinary users can not fix the list of multi-cluster applications revision issue [20919]
Fixed an issue where non-compliance with http_proxy alarm parameters [20926]
If you would like more information associated with each of the above issue, please Rancher GitHub issue to issue number input interface to query:
https://github.com/rancher/rancher/issues
Download and Upgrade
You can Rancher GitHub page to read the full Rancher 2.2.5 Release Note, download the latest version, or to learn more about the upgrade rollback considerations.
GitHub link:
https://github.com/rancher/rancher/releases