 Copyright: Attribution, allow others to create paper-based, and must distribute paper (based on the original license agreement with the same license Creative Commons )
Copyright: Attribution, allow others to create paper-based, and must distribute paper (based on the original license agreement with the same license Creative Commons )
 ,
,
Foreword
in mysql function for escaped have addslashes, mysql_real_escape_string, mysql_escape_string, etc., there is a situation magic_quote_gpc, but high version of PHP will remove this feature.
First, wide and byte injected HTML page code is irrelevant, I have seen
<meta charset=utf8>
Try to give up, this is a misunderstanding, SQL injection is not XSS. Although the causes of their encoded similar, but different locations of the attacks.
Many online material said program uses byte wide processing program, but do not indicate what specifically refers to the program. This article will introduce the principle of specific vulnerabilities occur with simple use. Here we define the language used is PHP5.4, database MYSQL5.6.
Some of the concepts involved
Character, character set and character sequence
Character (character) is the basic unit composed of the character set (character set) of. Assigning a number of characters (encoding) to determine the character position in the character set.
Character sequence (collation) refers to a comparison between the rules of the same character set characters.
UTF8
Since the ASCII character represented only 128, and therefore regulate the online world is to use UNICODE coding, but using UNICODE characters with ASCII representation is not efficient. Thus there has been an intermediate character set format, is called universal transformation format and UTF (Universal Transformation Format).
Byte wide
GB2312, GBK, GB18030, BIG5, Shift_JIS such as these are often said byte wide, in fact, only two bytes. Byte wide potential safety problem is eating ASCII characters (one byte) phenomenon.
MYSQL character set conversion process
-
MySQL Server upon receiving the request data requests from the character_set_client to the character_set_connection;
-
Internal operations before the request for data from the internal operation character_set_connection character set that determines as follows:
• use of each data field CHARACTER SET set value;
• If these values do not exist, DEFAULT CHARACTER SET is set value (MySQL extended, non-standard SQL) using corresponding data table;
• If these values do not exist, DEFAULT CHARACTER SET is a set value corresponding to the use of the database;
• If these values do not exist, character_set_server set value is used.
The operation result is converted from the character set of internal operations character_set_results.
Key: width position of PHP is Byte injection occurs when sending a request to the character set used MYSQL character_set_client encoding a set value.
PHP test code:
<!DOCTYPE html>
<meta charset="gbk"><!--仅用于基础的显示,换成utf8也行就是不好看-->
<?php
error_reporting(0);
$conn = mysql_connect('127.0.0.1','root','');
mysql_select_db('mysql',$conn);
mysql_query("set names gbk"); //不安全的编码设置方式
$res = mysql_query("show variables like 'character%';"); //显示当前数据库设置的各项字符集
while($row = mysql_fetch_array($res)){
var_dump($row);
}
$user = addslashes($_GET['sql']); //mysql_real_escape_string() magic_quote_gpc=On addslashes() mysql_escape_string()功能类似
$sql = "SELECT host,user,password FROM user WHERE user='{$user}'";
echo $sql.'</br>';
if($res = mysql_query($sql)){
while($row = mysql_fetch_array($res)){
var_dump($row);
}
}
else{
echo "Error".mysql_error()."<br/>";
}
?>
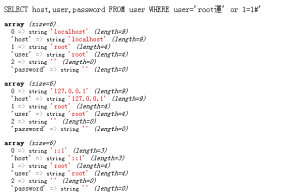
http://localhost/xl.php?sql=root%df%27%20or%201=1%23
It can be implemented successfully!
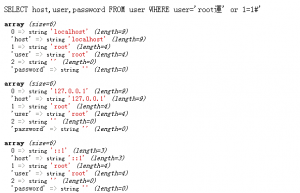
URL decoding sql = rootß 'or 1 = 1 #
Resolution process:
$_GET[‘sql’] 经过 addslashes编码之后带入了‘\’
1、root%df%5C%27%20or%201=1%23
2、带入mysql处理时使用了gbk字符集
%df%5c -> 運 成功的吃掉了%5c
%27 -> ‘ 单引号成功闭合
Execute the sql statement inserted.
How to eat:
GBK encoding, its encoding range is 0x8140 ~ 0xFEFE (not including xx7F), encountered% df (ascii (223))> ascii automatic splicing% 5c (128), the so eat '\', and 27%, 20% less than the character ascii (128) would retain.
supplement:
It is compatible GB2312 GBK, its high range 0xA1 0xF7, low range 0xA1 0xFE (0x5C not within the range), and therefore can not eat encoding% 5c.
Other wide-character set is the same process of analysis, to eat% 5c, only contained in the low normal 0x5c on the line.
Security filtering
The code above uses mysql_query ( "set names gbk") to set the encoding is actually recommended mysql_set_charset ( "gbk") in mysql; function to set the encoding, these two functions substantially similar functions, the only difference the latter modifies objects mysql mysql-> charset character set of attributes.
At the same time supporting the filter function is mysql_real_escape_string (). The above code lists several filtering function, the difference between them is the mysql_real_escape_string () will be treated in accordance with the incoming string object mysql mysql-> charset properties, it can be filtered according to the current character set.
Specific differences can refer to: http://www.laruence.com/2010/04/12/1396.html
Similarly available
Above can be obtained by a byte wide implantation is due to the transfer encoded form, that having a transfer function of the coding function has become causes of vulnerability.
Transcoding function
mb_convert_encoding()
iconv()
With the following iconv () to demonstrate, modify the above code:
<!DOCTYPE html>
<meta charset="gbk">
<?php
error_reporting(0);
$conn = mysql_connect('127.0.0.1','root','');
mysql_select_db('mysql',$conn);
mysql_set_charset("utf8"); //推荐的安全编码
$user = mysql_real_escape_string(($_GET['sql'])); //推荐的过滤函数
$user = iconv('GBK', 'UTF-8',$user);
$sql = "SELECT host,user,password FROM user WHERE user='{$user}'";
echo $sql.'</br>';
$res = mysql_query($sql);
while($row = mysql_fetch_array($res)){
var_dump($row);
}
?>

http://localhost/xl.php?sql=root%e5%27or%201=1%23
The same process can be executed successfully, code resolution is still above.
Summarize the causes of vulnerability:
Code a
1, using a character set unsafe function and the filter function.
2, when the flaw occurs PHP mysql request using a value character_set_client transcoding.
Code two
1, using the recommended settings function and filter function.
2, parsing errors in iconv () when the transcoding function, GBK UTF8 steering eaten "\"
3, PHP secure transcoding request mysql.
In addition:
When changing encoding direction user);
By visiting http:? //Localhost/xl.php sql = root% e9% 8c% a6 can be brought into a \, and then comment out single quotes.
Two injection parameters need to cope with this case.
E.g:'
http://localhost/xl.php?sql=root%e9%8c%a6¶=%20or%201=1%23
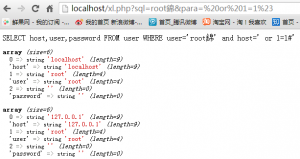
to sum up:
Byte injection Wide nothing to do with coding HTML page.
Mysql recommended encoding filter function mysql_real_escape_string (), mysql_set_charset ().
Encoding function will also cause rotation byte wide injection, even if the security setup function.