3 weeks of HW finally over, HW action in both red and blue did her best to carry out anti-*** *** the ultimate battle of. As a blue square staff, not only to see the wonderful performance of traditional defense technology in the HW is, but also feel a great role to play in defense technology initiative in HW, in my opinion most typical honeypot, and red by staff strayed honeypot, the blue side personnel to capture and identity of the portrait, then we have to talk about why the honeypot so diao.
From passive defense to active defense
has been threatened by passive defense is known for feature-based signature database to find an exact match for suspicious behavior and characteristics of the target program library one by one than to achieve abnormal behavior monitoring and blocking these feature library is built on the basis of the above has occurred, which is a very good explanation of why a passive defense "after the fact" behavior. A typical firewall technology, *** testing. But for unknown *** as 0day, depends on the characteristics of library matching the defense is unable to respond effectively, in order to deal with this *** unequal pattern of active defense technology appeared, the typical technique has Cyberspace mimicry defense, etc. .
The introduction of active defense strategy
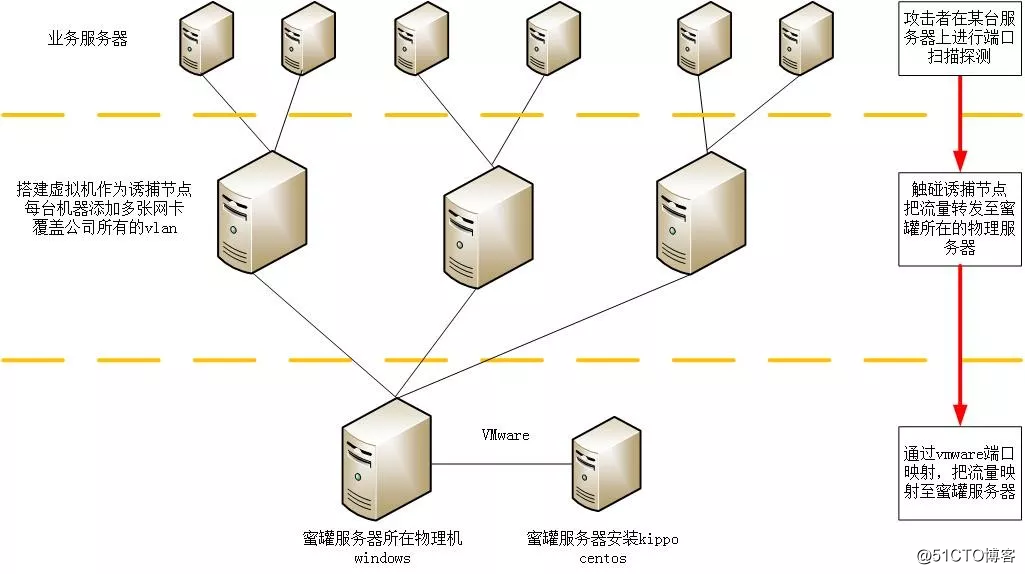
with the further increase *** technology, more and more ways to get around the traditional passive defense technology to launch *** on the target system, the traditional passive defense technology has also introduced a proactive defense strategy, such as the major manufacturers introduced intelligent firewall, Cisco's next-generation firewall, firewall Hillstone intelligence, artificial intelligence technology into the firewall to proactively identify malicious behavior. In addition, there are new technologies such as active defense sandbox, honeypot appeared in succession, further to make up *** asymmetric situation. Such technology is mainly to solve the "known unknown threat", for example, by building a honeypot camouflage business initiative to lure *** who, in order to capture behavior. During the HW, there will be disguised as a honeypot clothing ××× network mapping out who lure *** *** *** who charmed to increase the time by capturing ***'s IP for closure the cost can also be traceable to *** who, but honeypot technology is still unable to cope with 0day.
Sandbox technology
sandbox technology from software fault isolation techniques (software-based fault isolation, SFI ). The main idea is to isolate SFI. Sandbox provided by a virtualization technology to construct a separator operating environment, and is a program which runs substantially computing resources abstraction by the target program for detection analysis, accurate discovery process malicious code, etc., and thus to protect the host the goal of. As Moan architecture using kvm, the pavilion uses a docker.
Since the sandbox having barrier properties, malicious programs will not affect the system outside the sandbox isolation, but also has a function sandbox detection assay to analyze whether a program is a malicious program. But there are risks, sandbox only monitor common operating system application program interfaces, makes some malicious code can easily be circumvented so *** environment outside the host. It provides a virtualized operating environment based sandbox virtual machine is not credible resources to ensure the original features while providing appropriate security for the host will not be affected. Be detected based on the virtual machine sandbox virtualization and malicious behavior detection both techniques, malicious behavior detection method uses signature detection and behavior detection, signature detection to detect 0day powerless, behavior detection can detect 0day, However, high false alarm rate.
Honeypot
honeypot technology originated in the 1990s, lured by deploying it to simulate a real network system by *** ***, *** and then detect behavior in the default environment, analysis, *** *** way to restore those, methods, processes, etc., and to obtain information for the protection of the real system. Malicious code detection and widely used sample capture, detection and *** *** feature extraction, network *** forensics, botnets tracing.
It is called honeypot honeypot, because the beginning is to design tailored *** who include a large number of system vulnerabilities, is a trap for trapping *** who, in essence, a kind of person *** a spoofing, only honeypot is constantly being scanned, *** even compromised when to reflect the value of the honeypot. Honeypot actually does not contain any sensitive data. So to speak, to access the honeypot, are suspicious behavior, it can be identified as ***, in order to take the next action.
Through the above analysis, the introduction of honeypot has three abilities:
伪装,通过模拟各种含有漏洞的应用系统来引诱***者***以减少对实际系统的威胁。
数据诱捕,***者如果攻入蜜罐,那么可以通过蜜罐日志记录来还原***者从进入到离开蜜罐期内的所有活动过程及其他信息。
威胁数据分析,对***者的数据进行分析,还原***者的***手法,并对此进行溯源等。
但同时,蜜罐也具有局限性,他只有***者***时才能发挥它自身的作用,如果***者没有触发蜜罐,那么蜜罐将毫无意义,所以现在我们更要关注如何让***者能有效的触碰到蜜罐,然后利用相关技术对此展开溯源。同样,如果***者识别了该蜜罐,并且成功进入,利用相关逃逸0day对蜜罐展开***(蜜罐记录不到),那么蜜罐将会被当成跳板机对其他真实业务展开***,危害巨大。
蜜罐分类
蜜罐可以分为三类,低交互式蜜罐,中交互式蜜罐,高交互式蜜罐。
低交互式蜜罐:通常是指与操作系统交互程度较低的蜜罐系统,仅开放一些简单的服务或端口,用来检测扫描和连接,这种容易被识别。
中交互式蜜罐:介于低交互式和高交互式之间,能够模拟操作系统更多的服务,让***者看起来更像一个真实的业务,从而对它发动***,这样蜜罐就能获取到更多有价值的信息。
高交互式:指的是与操作系统交互很高的蜜罐,它会提供一个更真实的环境,这样更容易吸引***者,有利于掌握新的***手法和类型,但同样也会存在隐患,会对真实网络造成***。
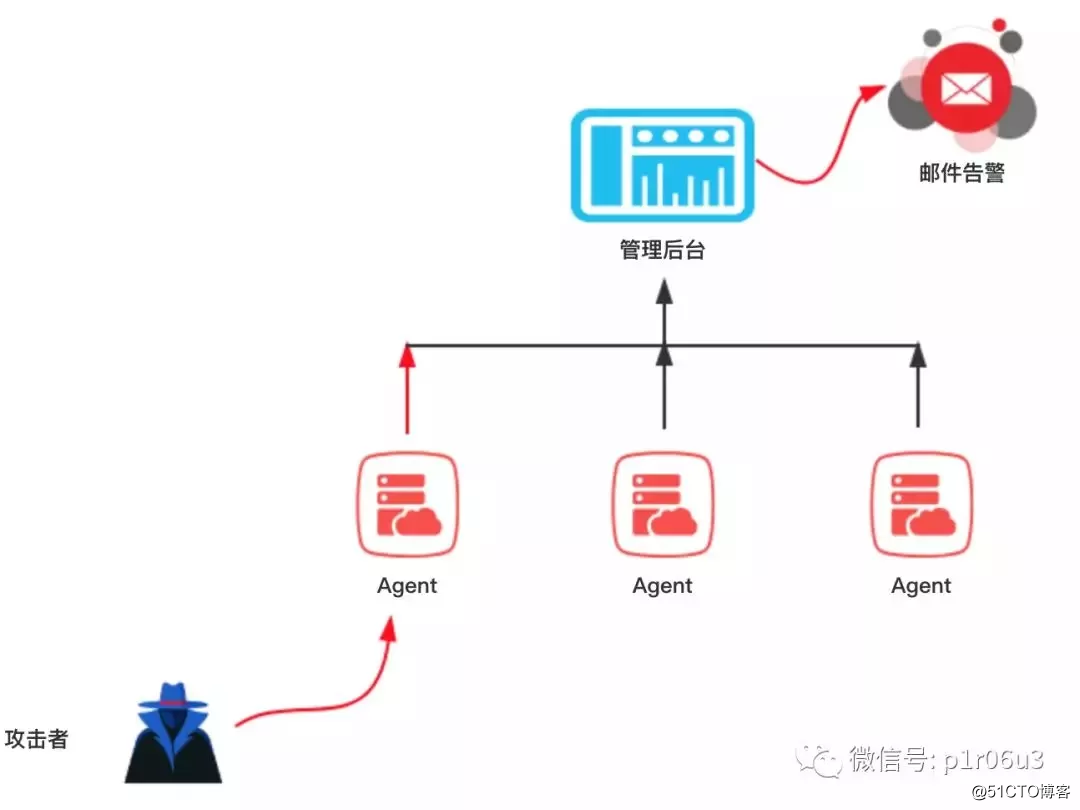
在这次HW中,相当大一部分蜜罐都部署在内网当中,部署在外网的蜜罐只有极少数,部署在外网的蜜罐可以检测到的东西就多了,尤其绑定域名后,把***者迷惑的分不清东西南北。某厂商的蜜罐可以说在HW中大放光彩,只要***者对该蜜罐进行访问,在很大程度上就能够获取你的社交账号ID,然后根据指纹信息还原***者身份画像,这点我相信很多红方没有料到,从而被社工的很惨。至于用了什么技术我就不写了,怕见不到第二天的太阳。蜜罐不仅能检测***者的***手法,也能够检测到僵尸网络,比如说这次HW中,有很多肉鸡利用weblogic的漏洞自动对外网发起***,然后植入***病毒等。公网蜜罐可以很好的检测这种行为,进而进行信息收集或追踪。
For interested honeypot related technologies, open source honeypot friendship recommend three tools: devaluation opencanary team members from the pirogue, supports 16 protocols, 24 kinds *** Feature Recognition: pirogue, public number: pirogue officially open source honeypot - easy to use - supports 16 protocols honeyd: http: //www.honeyd.orghttps: //github.com/desaster/kippo end the grateful knowledge insight pirogue, 12306 brother, in order to write such a hard-won article.