With the rapid development of emerging IT technologies such as "cloud migration", enterprise digital transformation has made the network environment of IT business more complex and diverse, and the security protection of enterprise digital resources is facing unprecedented pressure and threats. The zero-trust security architecture abandons the traditional "boundary"-based security model and establishes an identity-centered security access framework based on the security situational awareness of access context. It monitors data, applications, and services in accordance with the enterprise's unified security policy. Implement dynamic, risk-adaptive access control for digital resources.
Situation Awareness (SA) refers to “the perception and understanding of the various components in the target environment within a certain time and space range, and the prediction of their future changes.” The initial research results in this field came from the US military command For related projects on control systems, Endsley described situational awareness as an information processing chain containing a three-layer model, which in turn includes three parts: perception of environmental components, understanding of the current situation, and prediction of the future situation.
Bass introduced situational awareness into network security research in 1999, proposed the concept of Cyberspace Situational Awareness (CSA), and divided network situation into security situation, topology situation and transmission situation according to application fields. In view of the limitations of cloud environment network security situation prediction in terms of accuracy and real-time performance, Shen et al. proposed a cloud environment network security situation analysis method based on gray neural network, and constructed corresponding situation awareness indicators through classification and fusion technology. .
From the perspective of application methods and purposes, network security situational awareness assesses the security situation of the network by collecting, refining, and integrating various security information, and provides security analysts with decision-making basis for risk management. However, specific to the implementation method of security assessment, due to the complexity of network systems, network security measurement is still an academic problem recognized by domestic and foreign academic circles, including network security measurement models and methods, automated collection of security data, perception measurement, and quantitative assessment. and other issues have not yet been well resolved.
In terms of zero trust security, zero trust research is currently developing relatively rapidly in terms of system architecture standardization and solution implementation. The National Institute of Standards and Technology (NIST), the U.S. Department of Defense, and the Cloud Security Alliance have all provided corresponding zero-trust architecture reference models from their respective perspectives. Literature [9] uses DS evidence theory to transform various "uncertainties" of access subjects into "certain" security states, forming trust data that can be used by zero-trust security assessment engines.
In order to provide a reliable and reasonable security situation assessment method for zero trust solutions, this article first analyzes and sorts out the concepts of network situation awareness, continuous monitoring and trust assessment, studies and determines the connotation of zero trust access security situation assessment, and then studies and proposes A zero-trust secure access architecture was developed, and the key technologies and functions of zero-trust access security situation assessment were discussed based on this architecture. Finally, through an scalable security indicator system and a scientific quantitative assessment algorithm, contextual security assessment was provided for user access and strengthened Zero Trust’s “continuous assessment” capability enables zero trust’s dynamic fine-grained access control and provides a reference for researchers in the zero trust security field.
1 The connotation of security situation assessment
This section analyzes the development of technical theories in the fields of risk assessment and continuous monitoring, discusses the similarities and differences between them, and then analyzes the connotation, goals and significance of zero trust situation assessment.
1.1 Continuous monitoring of information security
Information Security Continuous Monitoring (ISCM) is a concept proposed by NIST in accordance with the Federal Information Security Management Act of 2002. It aims to continuously monitor and evaluate the information security of enterprise networks and provide information support for security management decisions. NIST reports SP 800-37, SP 800-53 and SP 800-137 summarize and define ISCM from different levels. Among them, SP 800-137 proposes the steps to establish, implement and maintain a continuous monitoring project, including six links: defining strategy, establishing project, implementing project, analysis/reporting, response processing, and review/update, as shown in Figure 1.
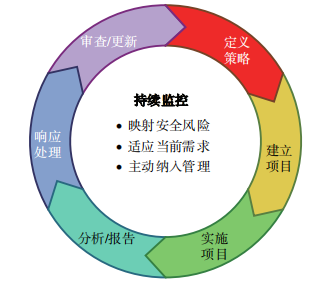
Figure 1 Implementation process and steps of ISCM project
ISCM conducts full-process status monitoring of the operation of federal systems from the perspective of risk management, providing situational awareness and decision-making support for enterprise network security management, including network asset management, security monitoring feedback analysis, and optimization of mitigation measures.
1.2 Continuous adaptive risk and trust assessment
In June 2017, Gartner proposed the security concept of Continuous Adaptive Risk and Trust Assessment (CARTA), which integrates threat intelligence, behavior analysis, big data, artificial intelligence, situation assessment and other technologies to build a An adaptive security protection framework is developed to provide security assessment and control capabilities covering business access processes to deal with the growing digital asset security risks in enterprise IT networks, as shown in Figure 2.
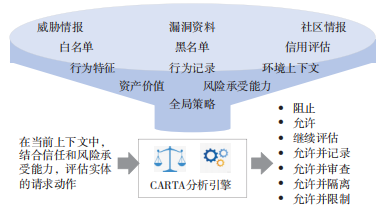
Figure 2 Continuous adaptive risk and trust assessment
The core concepts of the CARTA security protection framework include risk, trust, adaptability, and continuity. Among them, risk refers to the judgment and identification of network security risks (such as attacks, vulnerabilities, violations, anomalies, etc.); trust refers to access control based on trusted identity assessment; adaptation refers to the dynamic adaptation of security controls to risk changes. Capability; continuity refers to the continuity and periodicity of the risk and trust assessment process in time.
CARTA's risk and trust assessment is a dynamic weighing process that can use various security data to continuously evaluate access behavior, Application Programming Interface (API) calls, network activities, etc., and dynamically make security decisions. Including allowing/blocking access, or some action between allowing and blocking (such as continuing to evaluate, allowing but read-only, allowing and recording, etc.). The International Telecommunications Union Telecommunication Standardization Sector (ITU-T) defined a continuous protection framework for the service access process in the literature [14], and also adopted a similar non-binary decision-making result form.
1.3 Zero Trust Access Security Situation Assessment
In NIST's zero-trust architecture, policy components such as Policy Decision Point (PDP) and Policy Enforcement Point (PEP) work together to enforce user access based on contextual attributes such as access time and environmental attributes. Dynamic permission control, as shown in Figure 3.
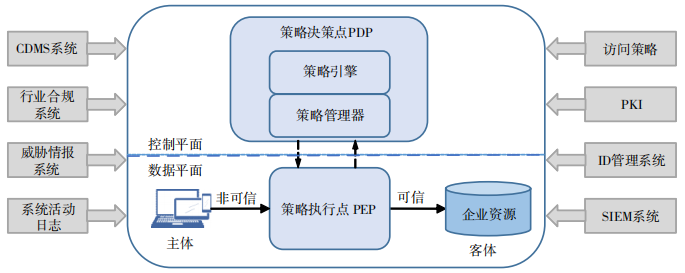
Figure 3 NIST’s Zero Trust Architecture Reference Model
Under the zero-trust security concept, the security status of all enterprise IT assets is included in the monitoring scope to provide dynamic and adaptive security protection for various resources. In order to ensure the correct implementation of dynamic security policies in a zero-trust system, enterprises need to collect the real-time status of IT assets (such as terminal devices, security components, and network services) as much as possible in order to assess the security posture of the network.
ISCM, CARTA, and NIST zero trust architectures all believe that risk and trust are constantly changing. Enterprise security protection needs to continuously monitor security risks in the network and be able to dynamically adapt to the current security context by adjusting user access behavior. Maximize protection of corporate assets. In addition, CARTA also embodies the characteristics of risk-based strategic decision-making. The decision conclusion is no longer a simple "allow/deny". There should also be an intermediate conclusion in between to adapt to different security risks.
It can be seen that in order to achieve continuous protection of applications, services, and data, the zero-trust architecture needs to continuously monitor and access all related entities around the user access process, and analyze changes in situations that affect access security, so as to monitor the user's access behavior, System security protection measures are controlled and deployed in a timely and effective manner. Therefore, zero trust security posture assessment requires the following capabilities and characteristics.
(1) Continuous and effective situation monitoring. Ensure that under the zero trust principle, periodic data collection and analysis of security data on all access-related entities is performed to obtain real-time security situation data.
(2) Reasonable and diverse safety indicators. Closely following the application requirements of zero trust security situation analysis, sort out and screen effective security indicators from complex and diverse multi-source security data, and establish a scientific and reasonable security indicator system and quantitative evaluation algorithm for situation analysis.
(3) Timely and accurate results reporting. Situation assessment results should be submitted to the strategic decision center in a timely and accurate manner and should comply with the decision center's data processing requirements to simplify their use.
2 Zero trust secure access architecture
Based on the zero-trust secure access principles proposed by NIST, this section proposes a secure access architecture based on zero-trust situation assessment, which continuously collects and analyzes context status information related to access requests, verifies the rationality of access requests, and protects the integrity of access sessions. Process security, as shown in Figure 4.
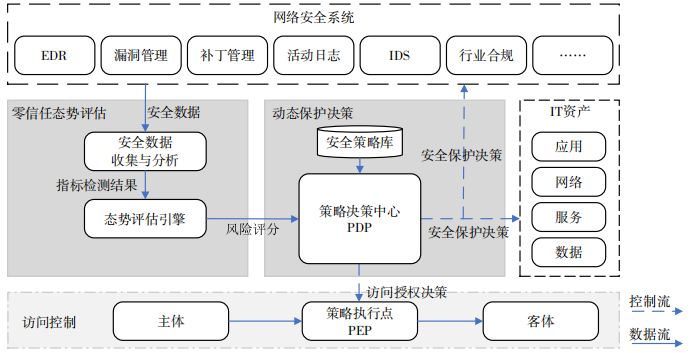
Figure 4 Security access architecture based on zero trust situation assessment
Security protection strategies are formulated by enterprise organizations based on business needs and according to the sensitivity level and tolerable risks of assets, including describing the protection level of object resources, the division of permissions of access subjects, and external conditions that affect policy decisions (such as user authentication methods, subject access location) etc.
PDP is the control center of the entire security access architecture, controlling user access according to security policies (such as attribute-based access control rules) to provide continuous security protection for enterprise resources. Decision instructions include two types: access authorization decisions and security protection decisions. The main differences are:
(1) The access authorization decision is an authorization decision generated by the PDP in real time after the PEP submits the user access request to the PDP. In order to ensure that user access requests can be processed quickly, it is generally required to generate decision-making instructions in real time, such as allow/deny and other access control instructions.
(2) Security protection decisions can be generated asynchronously or in a timely manner during the access session. PEP does not have to wait synchronously for the protection decision to arrive in real time. It only needs to ensure that when the protection decision is received, the instruction can be executed in time. Typical protection decisions are when the user trust score is too low, requiring the user to close the connection and perform patch repairs on the terminal.
PEP is responsible for executing the decision-making instructions issued by the policy center and protecting the confidentiality and authenticity of all access traffic. It should be noted that Figure 4 only shows examples of access control policy enforcement points.
Zero Trust Situation Assessment provides the policy decision center with quantitative security situation information, such as trust or risk scores, for use by the PDP when calculating authorization decisions.
3 Zero Trust Situation Assessment Method
Based on the requirements of situation assessment, contextual security and dynamic access control in the zero-trust architecture, this section studies the design and implementation of key technologies for zero-trust situation assessment, including security data collection and analysis, functional design of the situation assessment engine, and construction of the security indicator system. Methods and implementation of indicator quantification and fusion algorithms.
3.1 Safety data collection and analysis
Security Data Collection and Analyze (SDCA) is the data input component of situation assessment. Its functions mainly include continuously collecting security data, identifying network security status, and detecting security threats.
Sources of security data collection include but are not limited to user identity management, system activity logs, Endpoint Detection and Response (EDR), vulnerability/patch management, intrusion detection (Intrude Detection System, IDS), user behavior analysis and other systems . In addition, it also includes access-related metadata, such as user location, access time and other environmental factors.
Security data from different systems usually have different reporting forms, data formats and cycle frequencies. SDCA needs to sort out simple, effective and reasonable situation information from massive, multi-source security data in order to alleviate the problem of situation assessment engine. Functional and performance pressure.
3.2 Situation Assessment Engine
The Posture Assessment Engine (PAE) continuously receives the analysis and detection results of SDCA, standardizes and quantifies the security situation information from multi-source data and integrates indicators, and integrates relevant entities in the user access process (including users, terminals, networks, and environments). etc.) into the "trust level/access risk" (such as high, medium, low) of the access subject for use by the PDP.
PAE's situation assessment algorithm needs to reflect the trust assessment centered on the identity of the subject. After the subject passes the first identity authentication, it begins to continuously assess its access context (such as terminal security configuration, system vulnerabilities, behavioral characteristics, etc.) so that it can be used when the PDP needs can provide real-time information.
In zero-trust security access, the higher the trust level of the subject, the lower the access risk. Therefore, there is an inherent relationship between the trust level and access risk. The physical meaning of the situation assessment results depends on the indicator system used by the assessment engine. and quantitative algorithms, this article uses "access risk" to express the meaning of situation assessment results.
3.3 Safety indicator system
The security data collected by SDCA can be divided into five categories according to its associated entities, namely security content related to users, devices, applications, services and traffic respectively.
In order to simplify the process of zero trust security situation analysis, this article breaks down the indicators of the security status of different entities from three dimensions: user behavior security, terminal (application) security, and network environment security based on the Analytic Hierarchy Process (AHP). , forming a scalable zero-trust security posture assessment index system, as shown in Table 1.
Table 1 Zero Trust Security Situation Assessment Index System
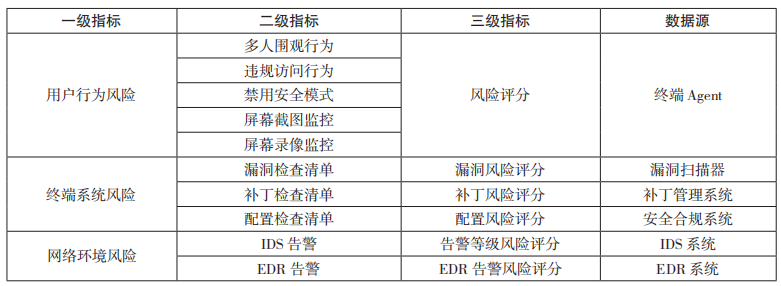
Zero trust security posture consists of three first-level indicators, including user behavior risk, terminal system risk and network environment risk. Among them, user behavior risk is broken down into five second-level indicators based on typical violations, such as multiple people watching and illegal access. .
Terminal system risk mainly evaluates the security factors of user access to terminals, such as software vulnerabilities, patch installation and security configuration items. Taking vulnerability risk assessment as an example, an enterprise develops a vulnerability inspection list in accordance with security policies and conducts vulnerability inspections on each terminal. Each vulnerability to be inspected in the list has a corresponding risk score (such as severity). After the vulnerability scanner completes the scan of the target terminal, it submits the scan results to the situation assessment engine, and its built-in quantitative assessment algorithm performs indicator fusion on the terminal security risk.
Network environment risk mainly analyzes and processes the situation information in network security alarms. For example, alarm events from IDS, EDR and other systems are associated with users or terminals to form corresponding risk scores. Because different external systems may have unique scoring mechanisms, the scoring conversion issue needs to be considered for the specific system.
The third-level indicator is the lowest level indicator and is represented by different types of risk scores (values).
3.4 Indicator quantification and fusion algorithm
This section focuses on the hierarchical evaluation index system proposed in Table 1, and solves the quantification problem of security indicators and the fusion problem of multi-dimensional and multi-layer indicators through the score-based index quantitative evaluation method and the multi-dimensional index fusion algorithm respectively.
3.4.1 Quantitative evaluation of indicators based on scoring
The security indicators proposed in this article include three types: user behavior risk, terminal security risk and network environment risk. Among them, terminal security risks mainly come from three types of software vulnerability issues: software defects, software security configuration, and software function abuse. Currently, there are standard vulnerability measurement and scoring methods for these three types of problems.
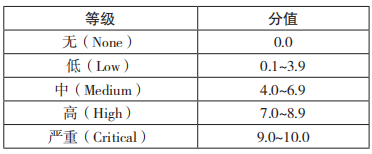
Common Vulnerability Scoring System (CVSS) provides a universal assessment method for the severity of software vulnerabilities and is mainly used in the field of vulnerability management and assessment. Common Misuse Scoring System (CMSS) In view of the difference between software vulnerabilities and misuse problems, the CVSS evaluation components and algorithms are adjusted to adapt to the characteristics of software function abuse defects. Common Configuration Scoring System (CCSS) mainly solves the vulnerability assessment problem of software security configuration. The above three algorithms all use the same theoretical basis and evaluation dimensions to evaluate the severity of software defects, and their quantitative results have consistent value ranges and grade divisions, as shown in Table 2.
Table 2 Vulnerability level classification of CVSS/CMSS/CCSS
On this basis, this article comprehensively considers the impact of various index factors on confidentiality, integrity and availability in user behavior risks and network environment risks, and maps the corresponding risk measurement calculations to CVSS, CMSS and CCSS algorithms in order to make the entire security The quantitative measurement of the indicator system has a unified evaluation perspective and dimension, as shown in Table 3.
Table 3 Quantitative evaluation algorithm of security indicators
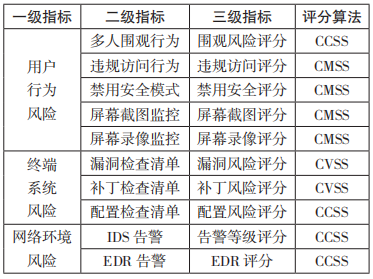
The indicator quantitative evaluation algorithm mainly solves the risk scoring problem of a single indicator. For example, if there are multiple people watching on the user terminal, according to the CCSS scoring algorithm, the "onlooker risk score" can be given as 4.6 points, or the terminal has CVE-2022- 30138 vulnerability has a severity score of 7.8.
3.4.2 Multi-dimensional indicator fusion algorithm
Comprehensive calculations of multiple indicators usually require the use of appropriate fusion algorithms. Sometimes the indicators established by the evaluation system may come from different observation dimensions (such as system vulnerabilities and user behaviors). When fusing these incomparable indicators, the scientific rationality of the fusion algorithm needs to be considered.
In the quantitative evaluation method used in this article, the quantitative scores of the underlying indicators come from or refer to the CVSS algorithm. Such algorithms adopt the same perspective and are unified in the definition of final results and risk levels, providing a basis for designing scientific and reasonable The indicator fusion algorithm lays the foundation.
The following takes the indicator fusion of terminal security risks as an example to illustrate the calculation method of comprehensive indicators in the situation assessment engine of this article.

In the formula: ![]() is the overall risk indicator of the vulnerability on the terminal; i is the check item in the vulnerability checklist; v(i) is the check result of vulnerability i (that is, exists or does not exist). Each vulnerability on the checklist has a corresponding CVSS score (representing the severity of the vulnerability). Therefore, from the calculation method, it can be seen that
is the overall risk indicator of the vulnerability on the terminal; i is the check item in the vulnerability checklist; v(i) is the check result of vulnerability i (that is, exists or does not exist). Each vulnerability on the checklist has a corresponding CVSS score (representing the severity of the vulnerability). Therefore, from the calculation method, it can be seen that ![]() the essence is the average severity of the vulnerabilities on the terminal (based on the checklist), so it can be used to characterize the terminal. The degree of security risk associated with the vulnerability.
the essence is the average severity of the vulnerabilities on the terminal (based on the checklist), so it can be used to characterize the terminal. The degree of security risk associated with the vulnerability.
Similarly, it ![]() is the degree of security risk caused by the terminal not installing patches as required, and it is
is the degree of security risk caused by the terminal not installing patches as required, and it is ![]() the degree of security risk caused by the terminal software not being safely configured as required.
the degree of security risk caused by the terminal software not being safely configured as required. ![]() is the overall security risk value of the user terminal, represented by
is the overall security risk value of the user terminal, represented by ![]()
, which is derived from the fusion of 3 indicators, ![]() and , respectively, are the weighted fusion weights of these three types of indicators.
and , respectively, are the weighted fusion weights of these three types of indicators.![]()
![]()
![]()
The fusion algorithm is characterized by simple calculation and easy implementation, and the checklist-style inspection method makes the security assessment index system easier to expand. In terms of the rationality of the fusion algorithm, many methods use the number of violations or the number of system vulnerabilities as indicators to measure the degree of security risks. For example, they mistakenly believe that the security risk of N violations is N times more serious than a single violation. This algorithm replaces unreasonable counting indicators by appropriately using binary indicators, and finally calculates the vulnerability's contribution to the overall evaluation result by calculating the proportion of the score of the vulnerability (i.e., the vulnerability that exists on the terminal) to the total list risk score. The inspection results reflected in the master list are reasonable to a certain extent.
When different enterprises evaluate terminal security when implementing zero trust access, they can adjust
![]()
![]() weighting values to accommodate differences in vulnerability, patch management, and compliance configuration requirements.
weighting values to accommodate differences in vulnerability, patch management, and compliance configuration requirements.
A similar method can be used for higher-level indicator fusion. By integrating user behavior indicators, terminal security indicators and network security indicators, complex evaluation targets can be decomposed into unified indicator measurement dimensions, and the same measurement scale can be used to evaluate different indicators. The security situation of various dimensions is quantified, forming a scientific and reasonable indicator system structure.
4 Analysis of evaluation methods
As an emerging network security concept, zero trust needs to focus on the overall security status of the system in industry practice and enterprise security construction, collect key indicators and risk factors in real time, and apply the evaluation results to the implementation of dynamic security strategies to provide Provides the basis for access control decisions.
Traditional situation assessment is mainly divided into two types: qualitative analysis and quantitative analysis. The former is mainly based on the experience and knowledge of experts and can provide in-depth insights, but the evaluation results are more obviously affected by subjective factors; the latter uses data and indicators to quantify the security status of the system, which is helpful for quantitative comparison of the security status of different systems, but A large amount of data needs to be collected and analyzed, and there is a lack of unified standards and basis for safety quantification. The results may be inaccurate due to data reasons.
Compared with traditional situation assessment methods, this solution has the following characteristics.
4.1 Multi-dimensional hierarchical index system
Given the complexity of security assessments, constructing an effective comprehensive security metric for a "system of systems" can be very difficult. Generally, security needs to be described and evaluated from multiple levels such as confidentiality, integrity and availability. Zero trust posture assessment needs to consider the overall security of the access-related context (including users, terminals, devices, networks, applications, etc.). To ensure that rich decision-making information is provided for dynamic access authorization. The indicator system proposed in this article takes into account the basic elements related to access security and is scalable, easy to observe, and interpretable. It can be used as a reference indicator system in the practice of zero trust situation assessment.
4.2 Objective and reasonable quantitative methods
During the safety assessment process, the evaluator's subjective factors can lead to serious distortion of the assessment results. For example, when using a 5-point scale to evaluate something, different people may regard the 5-point scale as 5 levels with equal or unequal intervals, or even produce a curve-like score based on their personal understanding of the mathematical distribution of the results. Hierarchy.
This article maps assessment algorithms such as CVSS to zero trust security situation assessment, and provides risk measurement calculations for each indicator factor in user behavior risks and network environment risks, so that the quantitative measurement of the entire security indicator system has a unified assessment perspective and dimension. This makes the comprehensive indicators obtained by fusion calculation more effective and reasonable.
4.3 Agile and efficient evaluation process
The purpose of zero trust situation assessment determines the need to use a more agile and efficient assessment method to continuously analyze access risks when users access applications and provide a decision-making basis for access control. Therefore, it is necessary to collect and analyze the security situation of the access environment quickly and in real time to ensure a good user experience.
In this application scenario, the situation assessment method designed in this article transforms the risk assessment traditionally conducted by security expert organizations into automated situation assessment, laying the foundation for zero-trust access control, automated security operations, and security orchestration.
5 Conclusion
This article studies the zero trust security situation assessment technology, introduces the typical technical framework of network security situation assessment, continuous monitoring and other concepts, combs and analyzes the connotation, purpose and significance of the situation assessment under the zero trust architecture, and then proposes a zero trust Security access architecture, and through this architecture, technologies such as security content collection and analysis, assessment engine function design, indicator system construction, quantitative assessment, and fusion algorithms for situation assessment are discussed.
The following is a summary of the development trends of zero trust situation assessment and the problems that may be faced:
(1) Zero trust application scenarios have gradually expanded from traditional office applications to 5G, industrial Internet, Internet of Things and other fields. With the ubiquity of network computing, how to establish a scientific and reasonable zero-trust security situation assessment index system for different network architectures is an important issue in the future.
(2) Big data analysis technologies such as artificial intelligence and machine learning have become important methods for situational awareness. How to apply these technologies in zero-trust situational assessment to improve assessment efficiency and accuracy will be one of the key directions of zero-trust situational assessment technology research. .
(3) The core goal of zero trust security posture assessment is to provide a decision-making basis for the security protection of enterprise resources. How to use posture assessment to strengthen security protection automation capabilities, realize the automated orchestration of security functions such as access control, user authentication, and password technology, and promote the organization's The security process is also an issue to be considered in the future zero trust security system.