Network status view netstat [options]
Netstat is a command line tool used to display network status information in Linux systems. It can display network connections, routing tables, connection data statistics and other information.
use
Options
-a: Show all options, including listening and unlistening ports.
-t: Only display tcp related options.
-u: Only display udp related options.
-n: Refuse to display aliases and convert addresses into numbers.
-l: Only list sockets that are listening.
-p: Display the name of the program that establishes related links.
-r: Display routing information and routing table.
-e: Display extended information, such as user, etc.
-s: Statistics based on each protocol.
-c [number of seconds]: Execute the netstat command every fixed time.
Can be used with grep and pipe symbols at the same time to filter results
Example


firewall management firewall
what is firewall
Firewall is a tool for managing network firewalls. It provides control over functions such as network packet filtering and Network Address Translation (NAT). The firewall determines how to process network data packets entering and leaving the system by configuring rules to protect the security of the system.
The main functions of firewall include:
- Packet filtering: Firewall can filter data packets entering and leaving the system according to rules to control network access. Filtering can be performed based on source IP address, destination IP address, port number and other conditions.
- Network Address Translation (NAT): Firewall can convert internal private IP addresses to public IP addresses to achieve access to the external network. NAT can be used to implement shared Internet access, port forwarding and other functions.
- Zone management: Firewall supports defining different security zones (zones), and each zone can have different security levels and rules. Interfaces can be assigned to different areas based on the type of network connection (such as wired, wireless, VPN, etc.), and corresponding firewall rules can be configured for each area.
- Service management: Firewall can manage network services and allow or deny access to specific services. Rules can be configured to allow or deny specific protocols, port numbers, and service names.
- Logging: Firewall can record network access logs to facilitate monitoring and auditing of network traffic. Rules can be configured to log specific network activity or unusual traffic.
Download firewall
yum install -y firewalld
sudo apt-get install firewalld
firewall use
Turn on/off/turn on startup/turn off startup/check status
systemctl start/stop/enable/disable/status firewalld
Management fire protection
systemctl status firewalld View firewall status
firewall-cmd --permanent --add-port=3306/tcp Permanently (--permanent) add (--add-port) 3306 port tcp protocol (3306/tcp)
firewall-cmd --reload reload so that the changes will take effect
firewall-cmd --permanent --remove-port=3306/tcp Permanently (--permanent) remove (--remove-port) 3306 port tcp protocol (3306/tcp)
firewall-cmd --zone=public --query-port=3306/tcp View port 3306, the protocol is tcp, and the security zone is public.
firewall-cmd --list-ports View all open ports
firewall-cmd --zone=public --list-ports View all open ports in the security zone that are public
Example

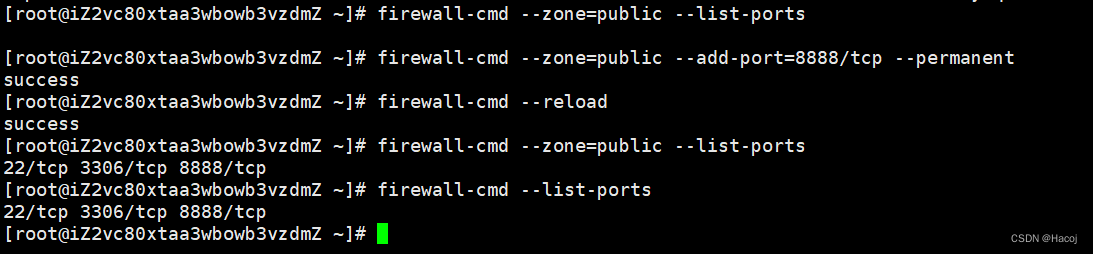
Additional understanding
Several common zones in Linux firewall:
public : This is the default zone and is used for network security settings in most cases. It contains all configured network interfaces and uses firewall rules to restrict packets entering and leaving the network.
home : This zone provides stricter network security settings and is typically used in home or small business network environments. It can define more specific firewall rules to restrict external access to the internal network.
dmz : DMZ (Demilitarized Zone) is a isolation zone usually used to isolate internal networks from external networks. In a firewall, DMZ zones provide a secure way to allow external access to certain services or ports while keeping the rest of the internal network isolated.
work : This zone provides network security settings suitable for the work environment. It can define rules to restrict external access to specific services or applications within the internal network.
external : This zone is used to protect external network interfaces, usually when connecting to the Internet. It can define more stringent firewall rules to restrict external access to the internal network.
internal : This zone is used to protect internal network interfaces, usually used to connect other devices or computers in the internal network. It can define appropriate firewall rules to restrict external access to the internal network.
firewall-cmd --list-all-zones can view all zones
Generally just use public