Table of contents
Real-time editing of strategies
Online addition and deletion of black and white list rules
Non-sense verification provides management functions for risk control strategies, including adding, deleting, editing, importing, exporting, viewing trend charts, viewing versions, and flexibly configuring the policy list and taking effect in real time. At the same time, it supports different processing of whitelists, graylists, and blacklists, allowing managers to add, delete, edit, and export lists. In addition, Dingxiang's non-inductive verification can also monitor various components, including server node applications, interface calls, middleware status, etc., to help users better manage and operate.
![]()
Real-time editing of strategies
The policy management module provides users with management functions for all current policies, including adding, deleting, editing, importing, exporting, viewing trend charts, and viewing versions. Strategy refers to setting different verification methods and thresholds according to different scenarios and risk levels to achieve optimal risk control effects. Users can flexibly configure policies according to their business needs and take effect in real time.
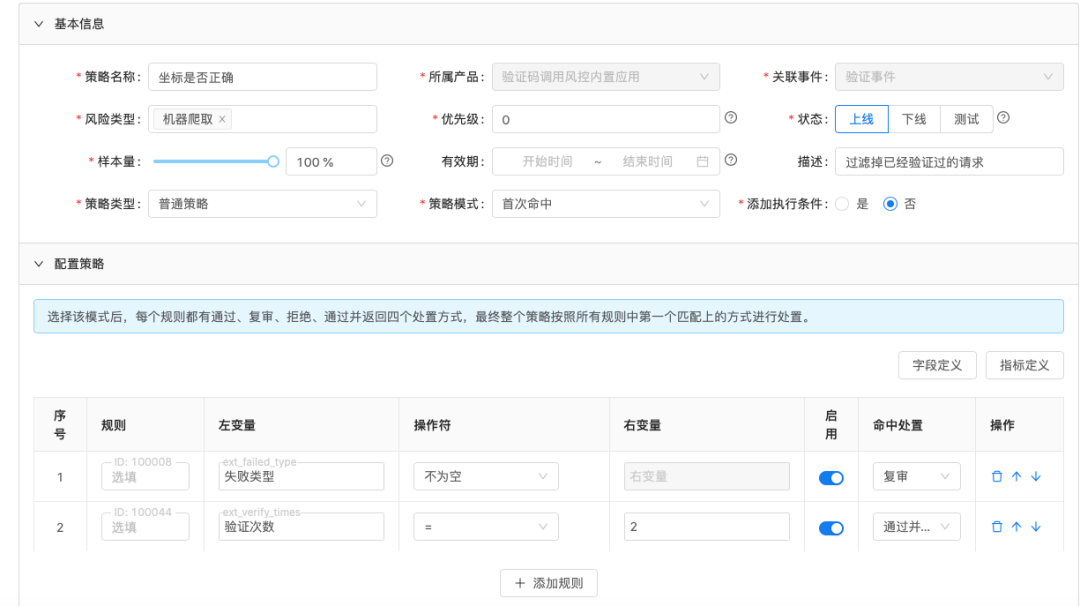
Under the "Add Policy" window, you need to fill in the necessary policy fields and configure the specific rules within the policy, which will take effect after passing the review. If you want to edit, delete, or export a policy, you can operate it in the relevant window respectively.
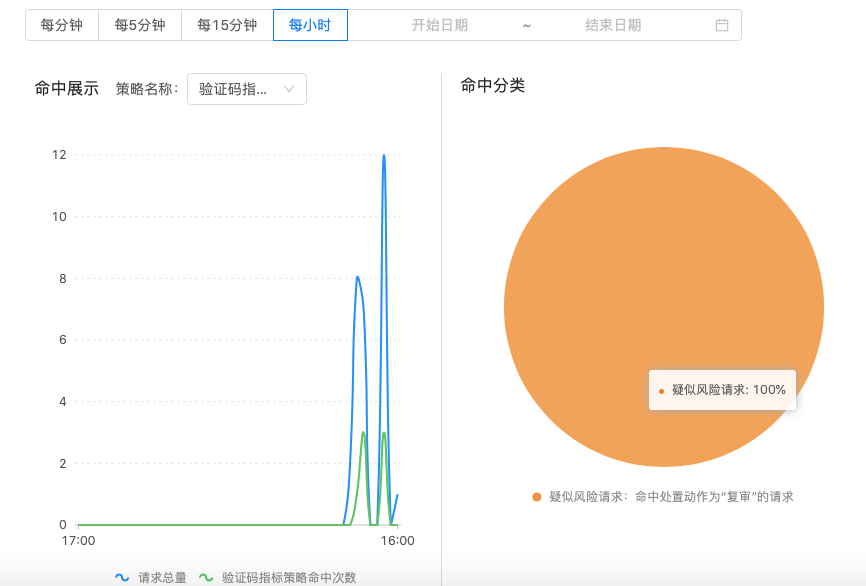
At the same time, under the "Trend Chart" window, you can view the trend details and check the version number of the relevant strategy according to your own needs.
![]()
Online addition and deletion of black and white list rules
The list management module provides users with management functions for all current lists, including adding, deleting, editing, and exporting. List refers to classifying users into whitelists, graylists and blacklists based on their verification results to facilitate different processing. Users can flexibly configure the list according to their own business rules, and it will take effect in real time.
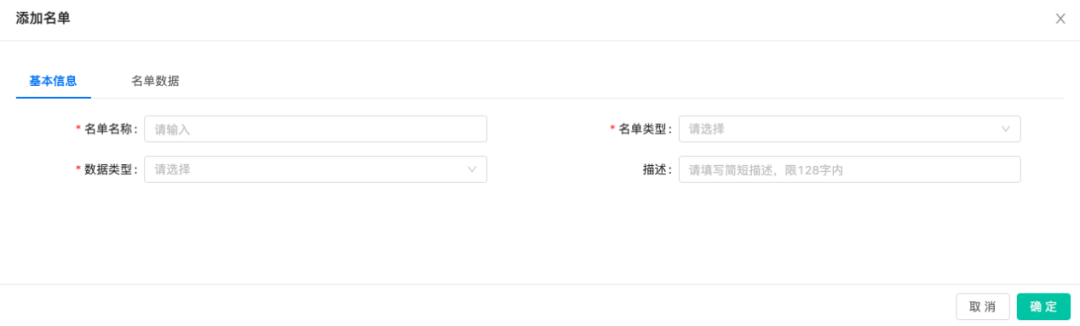
Under the "List Management" window, fill in the basic information and detailed list data. You can also edit, delete or export the list online. It will take effect after review.
![]()
Monitor each module
The verification monitoring module mainly includes viewing verification details, viewing verification statistics, and viewing verification alarms. Through this module, administrators can understand the process and results of each verification, as well as the overall situation and trends of verification. Users can also set verification alarm rules to receive timely notifications when verification is abnormal or fails.
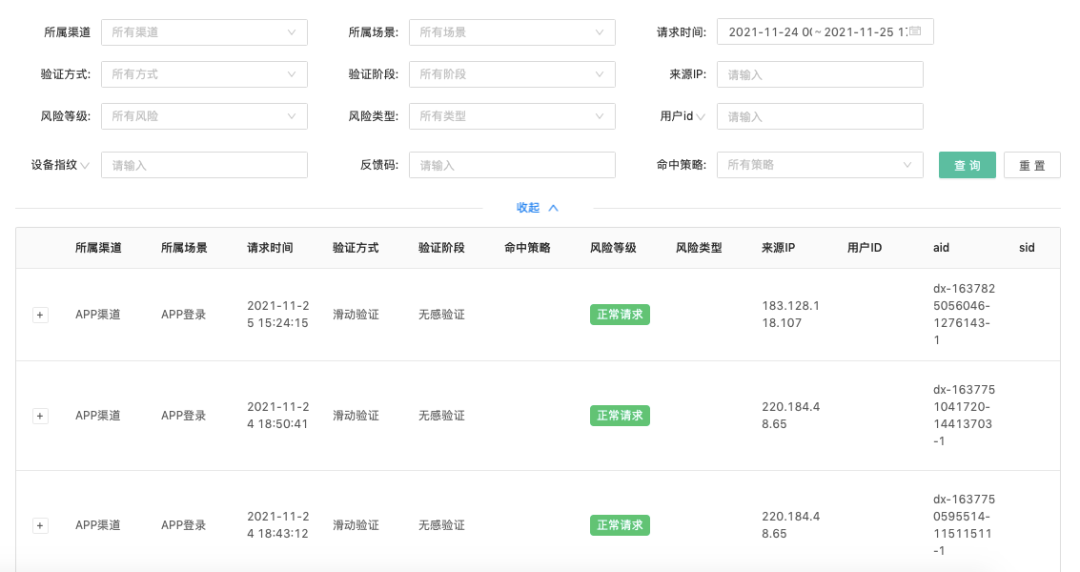
Verification monitoring: The system will record the relevant verification requests when verifying the code, and the administrator can intuitively see recent request information. This can help administrators analyze the success rate of verification, failure reasons, anomalies, etc., thereby optimizing verification strategies and improving verification efficiency.
Application node monitoring: The system will record the health status of application nodes related to the service, and administrators can intuitively see the recent health status of application nodes. This can help administrators monitor the running status, load conditions, fault conditions, etc. of application nodes, so as to discover and deal with problems in a timely manner and ensure the stability and availability of services.
Server performance monitoring: The system will record server performance status, and administrators can intuitively see recent server performance status. This can help administrators monitor the server's resource usage, response time, throughput, etc., so as to reasonably allocate and adjust resources and improve service performance and efficiency.
Interface call monitoring: The system will record the interface call status, and the administrator can intuitively see the recent interface call status. This can help users monitor the number of calls, call sources, call results, etc. of the interface, thereby analyzing the usage and problems of the interface, and optimizing the design and implementation of the interface.
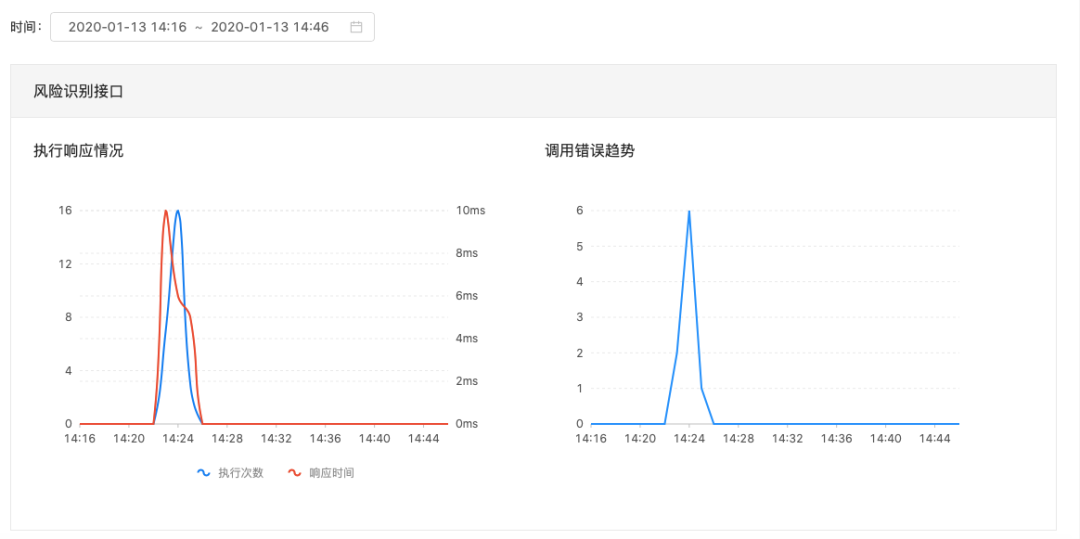
Middleware monitoring: The system will record the usage status of middleware, and administrators can intuitively see recent middleware status. This can help administrators monitor the type, version, configuration, connection, etc. of middleware, so as to manage and maintain middleware and ensure the normal operation and collaboration of middleware.
Dingxiang's senseless verification combines multiple technologies such as device fingerprints, behavioral characteristics, access frequency, and geographical location to effectively intercept malicious logins, batch registrations, block machine operations, and intercept abnormal users. Compared with traditional verification codes, users No more thinking or typing required, just swipe to verify. Users who have been intelligently identified as normal users no longer need to perform sliding operations within a certain period of time, which not only provides security for enterprises, but also allows users to pass without any awareness, greatly improving the user experience.