In addition to skills, tools are actually used more in operation and maintenance work. Useful tools can get twice the result with half the effort. Today Haodao will share with you several practical tools that can improve your operation and maintenance work. Let’s take a look and use them!
1. Check the bandwidth occupied by the process-Nethogs
Nethogs is a network traffic monitoring tool under the terminal that can visually display the bandwidth occupied by each process.
Download: http://sourceforge.net/projects/nethogs/files/nethogs/0.8/nethogs-0.8.0.tar.gz/download
[root@localhost ~]#yum -y install libpcap-devel ncurses-devel
[root@localhost ~]# tar zxvf nethogs-0.8.0.tar.gz
[root@localhost ~]# cd nethogs
[root@localhost nethogs]# make && make install
[root@localhost nethogs]# nethogs eth0

2. Hard disk read performance test-IOZone
IOZone is a Linux file system performance testing tool that can test the read and write performance of file systems in different operating systems.
Download: http://www.iozone.org/src/current/
[root@localhost current]# tar xvf iozone3_420.tar
[root@localhost ~]# cd iozone3_420/src/current/
[root@localhost current]# make linux
[root@localhost current]# ./iozone -a -n 512m -g 16g -i 0 -i 1 -i 5 -f /mnt/iozone -Rb ./iozone.xls
-a uses fully automatic mode
-n sets the minimum file size (Kbytes) for automatic mode.
-g sets the maximum file size in Kbytes that can be used in automatic mode.
-i is used to specify which test to run.
-f specifies the name of the test file and automatically deletes it after completion
-R generates Excel to standard output
-b specifies output to the specified file
3. Real-time monitoring of disk IO-IOTop
The IOTop command is a command specifically used to display hard disk IO. The interface style is similar to the top command.
[root@localhost ~]# yum -y install iotop
4. Network traffic monitoring-IPtraf
IPtraf is a simple network status analysis tool running under Linux.
[root@localhost ~]# yum -y install iptraf

5. Network traffic monitoring-IFTop
iftop is a real-time traffic monitoring tool similar to top under Linux. More intuitive than iptraf.
Download: http://www.ex-parrot.com/~pdw/iftop/
[root@localhost ~]# tar zxvf iftop-0.17.tar.gz
[root@localhost ~]# cd iftop-0.17 [root@localhost iftop-0.17]# ./configure
[root@localhost iftop-0.17]# make && make install
[root@localhost iftop-0.17]# iftop [root@localhost iftop-0.17]# iftop -i eth0 #指定监控网卡接口

-
TX: send traffic
-
RX: receive traffic
-
TOTAL: total traffic
-
Cumm: The total traffic from running iftop to the current time
-
peak: peak value of traffic
-
rates: represent the average traffic in the past 2s, 10s and 40s respectively.
6. Real-time process monitoring-HTop
HTop is an interactive process browser under Linux that can be used to replace the top command under Linux.
rpm -ivh http://pkgs.repoforge.org/rpmforge-release/rpmforge-release-0.5.2-2.el6.rf.x86_64.rpm (install third-party YUM source)
[root@localhost ~]# yum -y install htop
7. System resource monitoring-NMON
NMON is a monitoring and analysis tool widely used on AIX and various Linux operating systems.
Download: http://sourceforge.jp/projects/sfnet_nmon/releases/
[root@localhost ~]# chmod +x nmon_x86_64_rhel6
[root@localhost ~]# mv nmon_x86_64_rhel6 /usr/sbin/nmon
[root@localhost ~]# nmon

8. Monitor multiple logs-MultiTail
MultiTail is software that opens multiple windows on the console to monitor multiple log documents at the same time, similar to the tail command.
rpm -ivh http://pkgs.repoforge.org/rpmforge-release/rpmforge-release-0.5.2-2.el6.rf.x86_64.rpm (install third-party YUM source)
[root@localhost ~]# yum -y install multitail
[root@localhost ~]# multitail -e "fail" /var/log/secure #筛选关键字进行监控
[root@localhost ~]# multitail -l "ping baidu.com" #监控后面的命令-l将要执行的命令
[root@localhost ~]# multitail -i /var/log/messages -i /var/log/secure #-i指定一个文件名
9. SSH brute force cracking protection-Fail2ban
Fail2ban can monitor your system logs and then match the error messages in the logs with regular expression matching to perform corresponding blocking actions. Generally, firewall blocking is called.
Download: http://www.fail2ban.org/wiki/index.php/Downloads
[root@localhost ~]# cd fail2ban-0.8.11
[root@localhost fail2ban-0.8.11]# python setup.py install
[root@localhost fail2ban-0.8.11]# cd files/
[root@localhost files]# cp ./redhat-initd /etc/init.d/fail2ban
[root@localhost files]# service fail2ban start
[root@localhost files]# chkconfig --add fail2ban
[root@localhost files]# chkconfig fail2ban on
Note: You need to configure iptables to make it practical. If you restart iptables, you must also restart fail2ban, because the principle of fail2ban is to call iptables to block external attacks in real time.
[root@localhost ~]# grep -v "^#" /etc/fail2ban/jail.conf | grep -v "^$" [DEFAULT]
ignoreip = 127.0.0.1/8#忽略本机IP
bantime = 600 #符合规则后封锁时间
findtime = 600 #在多长时间内符合规则执行封锁如600秒达到3次则执行
maxretry = 3 #最大尝试次数
backend = auto #日志修改检测日志gamin、polling和auto这三种
usedns = warn [ssh-iptables]
enabled = true#默认是禁用
false filter = sshd action = iptables[name=SSH, port=ssh, protocol=tcp] # sendmail-whois[name=SSH,dest=收件人邮箱, sender=发件人邮箱, sendername="Fail2Ban"] logpath = /var/log/sshd.log #响应的错误日志一般在/var/log/secure maxretry = 5 #尝试错误次数覆盖全局中的maxretry
Note: All application protection is turned off by default and needs to be turned on manually. The fail2ban.conf file is log information, and the jail.conf file is protected specific service and action configuration information.
[root@localhost ~]# touch /var/log/sshd.log
[root@localhost ~]# service fail2ban restart
[root@localhost ~]# fail2ban-client status #查看监控已经开启 Status |- Number of jail: 1 `- Jail list: ssh-iptables
[root@localhost ~]# iptables -L #iptables过滤表有fail2ban一条规则 fail2ban-SSH tcp -- anywhere anywhere tcp dpt:ssh
10. Connection session terminal persistence-Tmux
Tmux is an excellent terminal reuse software similar to GNU Screen, which is more comprehensive, flexible and efficient than Screen. In order to ensure that disconnection when connecting to SSH does not affect the task operation.
rpm -ivh http://pkgs.repoforge.org/rpmforge-release/rpmforge-release-0.5.2-2.el6.rf.x86_64.rpm (install third-party YUM source)
11. The page displays disk space usage-Agedu
Download: http://www.chiark.greenend.org.uk/~sgtatham/agedu/
[root@localhost ~]# tar zxvf agedu-r9723.tar.gz
[root@localhost ~]# cd agedu-r9723
[root@localhost ~]# ./configure
[root@localhost ~]# make && make install
[root@localhost ~]# agedu -s / #-s扫描
[root@localhost ~]# agedu -w --address 192.168.0.10:80 #-w输入一个网页链接
[root@localhost ~]# agedu -w --address 192.168.0.108080 --auth none #--auth关闭认证如果不加端口号会生成一个随机的用浏览器访问

12. Security scanning tool-NMap
NMap is a network connection scanning and sniffing toolkit under Linux used to scan open network connections of computers on the Internet.
Download: http://nmap.org/download.html
[root@localhost ~]# tar jxvf nmap-6.40.tar.bz2
[root@localhost nmap-6.40]# ./configure
[root@localhost nmap-6.40]# make && make install
[root@localhost ~]# nmap 192.168.0.10 #获取基本信息
[root@localhost ~]# nmap -O 192.168.0.10 #获取系统版本信息
[root@localhost ~]# nmap -A 192.168.0.10 #获取系统综合信息
[root@localhost ~]# nmap 192.168.0.0/24 #获取一个网段工作设备基本信息
-sSTCP scan
-sV system version detection
13. Web stress test-Httperf
Httperf is more powerful than ab and can test the maximum service volume that a web service can carry and discover potential problems; such as memory usage and stability. The biggest advantage: You can specify rules for stress testing and simulate the real environment.
Download: http://code.google.com/p/httperf/downloads/list
[root@localhost ~]# tar zxvf httperf-0.9.0.tar.gz
[root@localhost ~]# cd httperf-0.9.0
[root@localhost httperf-0.9.0]# ./configure
[root@localhost httperf-0.9.0]# make && make install
[root@localhost ~]# httperf --hog --server=192.168.0.202 --uri=/index.html --num-conns=10000 --wsess=10,10,0.1
Parameter Description:
-
--hog: Let httperf generate as many connections as possible. httperf will generate access connections regularly according to the hardware configuration;
-
--num-conns: Number of connections, a total of 10,000 requests are initiated;
-
—wsess: Simulation of the time pattern when a user opens a web page. The first 10 indicates that 10 session connections are generated, the second 10 indicates that each session connection makes 10 requests, and 0.1 indicates the interval/s between each session connection request.
` How to learn hacking & network security
As long as you like my article today, my private network security learning materials will be shared with you for free. Come and see what is available.
1. Learning roadmap
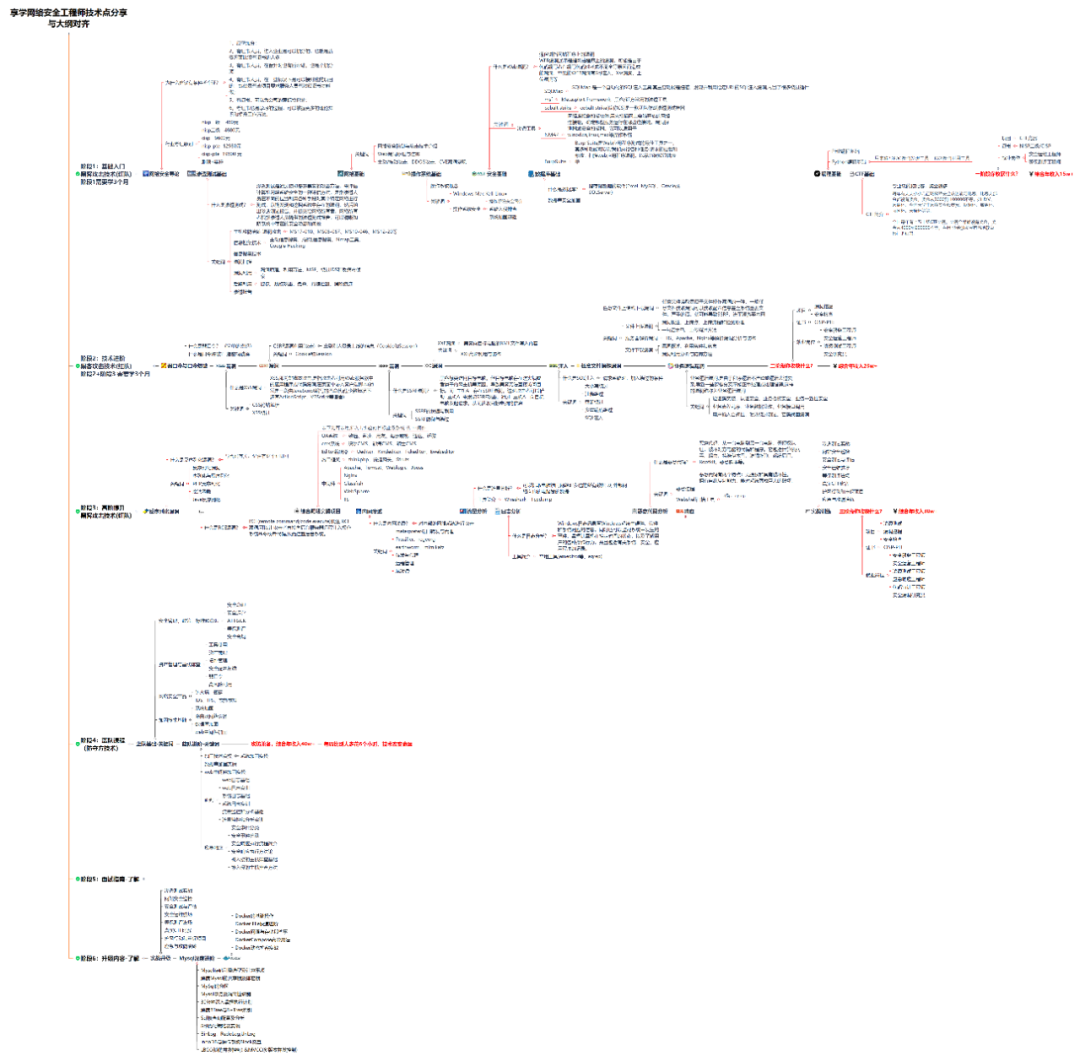
There are a lot of things to learn about attack and defense. I have written down the specific things you need to learn in the road map above. If you can complete them, you will have no problem getting a job or taking on a private job.
2. Video tutorial
Although there are many learning resources on the Internet, they are basically incomplete. This is an Internet security video tutorial I recorded myself. I have accompanying video explanations for every knowledge point in the roadmap above.
The content covers the study of network security laws, network security operations and other security assessments, penetration testing basics, detailed explanations of vulnerabilities, basic computer knowledge, etc. They are all must-know learning contents for getting started with network security.
(They are all packaged into one piece and cannot be expanded one by one. There are more than 300 episodes in total)
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
3. Technical documents and e-books
I also compiled the technical documents myself, including my experience and technical points in participating in large-scale network security operations, CTF, and digging SRC vulnerabilities. There are more than 200 e-books. Due to the sensitivity of the content, I will not display them one by one.
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
4. Toolkit, interview questions and source code
"If you want to do your job well, you must first sharpen your tools." I have summarized dozens of the most popular hacking tools for everyone. The scope of coverage mainly focuses on information collection, Android hacking tools, automation tools, phishing, etc. Interested students should not miss it.
There is also the case source code and corresponding toolkit mentioned in my video, which you can take away if needed.
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
Finally, here are the interview questions about network security that I have compiled over the past few years. If you are looking for a job in network security, they will definitely help you a lot.
These questions are often encountered when interviewing Sangfor, Qi Anxin, Tencent or other major companies. If you have good questions or good insights, please share them.
Reference analysis: Sangfor official website, Qi’anxin official website, Freebuf, csdn, etc.
Content features: Clear organization and graphical representation to make it easier to understand.
Summary of content: Including intranet, operating system, protocol, penetration testing, security service, vulnerability, injection, XSS, CSRF, SSRF, file upload, file download, file inclusion, XXE, logical vulnerability, tools, SQLmap, NMAP, BP, MSF…
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.