Threat intelligence refers to the collection, analysis and interpretation of information related to potential threats in the field of information security and security defense in order to pre-discover and assess potential threats that may cause damage to organizational assets. It is a multi-dimensional and comprehensive approach. It helps organizations understand factors that may pose threats to their security through the collection, analysis, and judgment of information. This approach not only focuses on the technical level, but also includes social, psychological, political and other dimensions to better deal with the ever-changing and complex threat environment. It is designed to provide analysts with critical information to help them implement preventive measures and emergency response strategies to reduce the risk and impact of threat response implementation.
Preface
As the cyber attack confrontation environment becomes increasingly severe, cyber threat intelligence gradually plays an indispensable role in attack behavior analysis. The importance of cyber threat intelligence mainly lies in its ability to help organizations understand the ever-changing threats they face, provide data-driven defense strategies, reduce potential risks and losses, and provide support for establishing a stronger information security system.
This article focuses on threat intelligence countermeasures from the perspective of C2 infrastructure. In the article, the author will discuss the attack and defense ideas in the threat intelligence analysis process. From the advanced attack and defense process, look at the threat intelligence analysis ideas from the perspective of the attacker, and briefly analyze the problems that exist in the intelligence research and hunting process. During the work process, the author found that it is very necessary to view threat intelligence from an attack perspective. We need to think about possible laxities in threat intelligence from the attacker's perspective. When an attack occurs, is the researcher's analysis based on his or her own understanding of the attack or on objective intelligence? I believe readers will think about this through this article. Since the concept of threat intelligence confrontation is relatively broad and covers many different subdivisions, due to space limitations, this article will only explain the direction of C2 infrastructure confrontation.
This article is only the author's personal opinion. If there is any inaccuracy, please correct me.
Threat intelligence research and judgment ideas from the attacker’s perspective
When seeing suspected attacks, we should first think about whether the threat intelligence we see is completely real? When analyzing security incidents, threat intelligence should be used as an auxiliary basis for judgment, but it should not be the decisive factor. The first criterion for analysts to judge security incidents is "behavior" , and the concept of behavior is also reflected in cyberspace mapping. However, there are interoperability and ambiguity between the two. In the process of threat intelligence traffic side hunting, behavior mainly refers to what the subject did, focusing on the communication process, while in mapping, it is the unique characteristics of the individual, with the purpose of ultimately forming a fingerprint. However, the characteristics of the subject can also be used as one of the focus information of threat intelligence to correlate the assets and facilities of an organization.
Behavior : Different groups may show basic unique characteristics. When we can grasp this characteristic, then we can identify all individuals in this group as much as possible, and these behavioral characteristics are displayed in cyberspace mapping. is the banner feature in each port protocol of this device.
Behavior can be understood as features here, and how to extract these features for more accurate matching has undoubtedly become one of the most important links.
In order to form the facility assets of an APT organization, we should extract the "behavior" displayed by these facilities to construct a fingerprint that can point to the organization's assets. Therefore, we then need to introduce some more "accurate" , "specific" , "Immutable"** individual characteristics can decisively point to the asset range of a certain person or group. It must not only accurately distinguish the target assets, but also be specific and cannot be easily modified.
Here I believe that when threat intelligence targets the assets of a certain organization or a special C2 facility, analysts can perform preliminary asset filtering by making relevant fingerprints, and then further verify the associated assets, and finally synchronize them into the threat intelligence , and threat intelligence hunting, it is better to be incomplete than to be inaccurate and mislead analysts who face subsequent attacks.
For threat hunting of malicious samples, we locate the sample side, analyze the communication situation on the traffic side, and synchronize it to the threat intelligence side. This is reflected in the process of comprehensive research and judgment on C2 on the intelligence side and marking malicious behaviors. Traffic plays a vital role in this process. In the current offensive and defensive confrontation process, weaponized engineers have been very sophisticated in generating samples. Various white + black emerge in an endless stream, so communication behavior is undoubtedly required. The thing to pay more attention to, to sum up in one sentence, is not to look at its appearance, but to look at what is going on with it.
C2 facility communication characteristics:
-
Return address
-
Communication content
-
special channel
-
Communication frequency
-
duration
-
.....
In my opinion, the detection of communication content is always a difficult point. It is impossible to know the encrypted communication data after encrypted communication traffic. Traffic detection technologies such as rule matching and load restoration detection used in traditional plaintext detection cannot detect the information content transmitted by the encrypted session. detection. C3, which uses the legitimate functions of popular applications to disguise communications between infected endpoints and C2 servers, makes threat tracking more difficult. Products on the market that detect encrypted traffic are basically helpless when facing higher versions of the TLS protocol. The communication frequency is the heartbeat packet, which can be bypassed by performing heartbeat silence + offset. This is also a basic operation. As a result, as attackers may begin to exploit more covert C2 channels in future encounters, intelligence teams should accelerate analysis of endpoint machine data to quickly detect threats throughout the kill chain.
For self-signed samples, code signature fingerprints are undoubtedly a good idea.
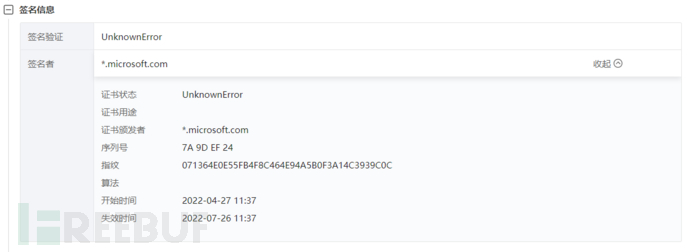
I think that based on code fingerprints, some self-signed certificate samples can be correlated. I have learned about Weibu's OneSec before, so is it possible to correlate the relationship between malicious samples transmitted in the organization? The fingerprint of his signature should be that all the programs signed with this certificate are the same. Attackers usually give white + black signatures to the programs. The premise for corresponding multiple samples is that they are all signed by this certificate. **If the Agent has been deployed on the terminal device, the signature fingerprints of the associated terminal suspicious programs will be compared, and based on the detection intelligence of the cloud sandbox, malicious programs with the same code signature will be identified as a detection basis. I think this idea should be feasible if applied in the context of organizational structure. **Of course, the specific feasibility still needs to be considered by professionals. In theory, all devices based on agent-side deployment as the basis for protection should be able to learn from it.
Organizations should always pay attention to their own risk exposure, be driven by intelligence, and pay attention to public opinion (code leaks, contact information, data leaks, supply chain risks) . The later impact of some data leakage incidents may directly lead to security incidents in relevant organizations. With the development of an organization's business, cloud-based business, mobile office needs, and expansion of partners and branches, security risks will gradually increase, so it is necessary to pay more attention to recent security intelligence. From the attacker's perspective, infiltration will not be initiated from the safest location. Instead, it will observe Internet assets and public opinions related to the target as a special bridge to move to the target organization. It should be noted that the barrel principle is to start from the most secure position of the defense system. Break through weak points.
To sum up, in the process of threat intelligence hunting, misses and discovered intelligence are always the most important. When the attack has become a fact, further intelligence hunting analysis can only reduce the loss of the organization to a certain extent. The threat intelligence analysis team should pay more attention to ongoing attacks and attacks that have already occurred , and on this basis, discover incidents that are about to attack, promptly push attack events to high-risk industries based on intelligence, conduct timely investigation, and report security incidents Reduce risks by taking preventive measures in advance and effective disposal afterwards.
Strategy and Implementation to Counter C2 Threat Intelligence
Command and control servers, also known as C&C or C2, are used by attackers to maintain communications with compromised systems within a target network. The terms "command" and "control" are often used loosely, and malicious cyberattacks have been on the rise over the past decade. One of the most damaging attacks, often performed via DNS, is accomplished via C&C, which is defined as a technique used by threat actors to communicate with infected devices over a network.
As the name suggests, command and control servers issue commands and control to infected systems (usually home users' Internet-connected computers, which then form an army of zombies, known as a botnet). These communications can be as simple as maintaining timing beacons or "heartbeats" so that operators running attacks can keep an inventory of the systems they have compromised in a target network, or use them for more malicious operations such as remote control or data transmission. leakage. Although command and control servers are used to control systems within the target organization, it is typically the compromised host that initiates the communication from within the network to the command and control server on the public Internet. 【Command-and-control servers: The puppet masters that govern malware】By Adam RiceJames Ringold, Westinghouse Electric Company
I hope that after reading this paragraph, readers can think about security prevention strategies from the attacker's perspective and understand new C2 facility protection methods. This paragraph will also explain the implementation theory of C2 infrastructure methods to combat threat intelligence. The picture below is a schematic diagram generated by micro-step Graph. Readers can read the text first and then look at the legend to enhance their understanding of relevant technical ideas to achieve better reading results.

[^Weibu Information]: Graph Overview
RedGuard is a derivative tool based on command and control (C2) front-end flow control technology, with a more lightweight design, efficient flow interaction, and reliable compatibility with Go programming language development. As network attacks continue to evolve, red and blue teams become more and more complex as exercises are conducted. RedGuard aims to provide the red team with a better C2 channel hiding solution, provide flow control for the C2 channel, and block "malicious" analysis traffic to better complete the entire attack task.
RedGuard is a C2 front-end traffic control tool that can avoid detection by Blue Team, AVS, EDR, and Cyberspace Search Engine.
Github download address
https://github.com/wikiZ/RedGuard
Forged TLS certificate
When deploying domain fronting to hide C2 traffic, the accelerated domain name does not have HTTPS certificate information by default. This is obviously a problem. Therefore, when configuring the domain name, you need to pay attention to configuring the certificate. This is also the way to determine whether the sample is domain fronting. Set the default basis for traffic.

[^Tencent Cloud]: Content distribution network certificate configuration
I believe that after seeing this, everyone will have questions, how to obtain the certificate configured **? If you use your own application certificate, it will not meet the concealment effect we expect to achieve. **You can use cloned certificates for configuration here. Taking Tencent Cloud as an example, it was found in the test that it will not verify the validity of the custom uploaded certificate. We can use the same certificate as the actual site of the accelerated domain name for forgery. Although the forged certificate cannot communicate under normal circumstances when replacing the default certificate of CS, when deployed on the cloud service provider CDN full-site acceleration and RedGuard, the validity will not be verified and C2 interactive traffic can be communicated normally.
The following is the address of existing projects on Github
https://github.com/virusdefender/copy-cert
Although the certificate on the front traffic side of the sample domain has been resolved, from the perspective of large network mapping, our C2 server is still exposed, and the real C2 server may still be detected and associated. At this time, we can use RedGuard Modify C2's pre-default certificate to achieve concealment.

[^Weibu Community Intelligence Information]: Digital Certificate
The above is the effect of the certificate forged by the C2 server. It can be seen that it is credible and unexpired in the Weibu community’s intelligence, and the main way to obtain the digital certificate is to extract it in the cloud sandbox during sample analysis and real-time It is updated, but it has obviously not been verified effectively. The status value only verifies the expiration time. The certificate trustworthiness verification should only be judged based on whether it can communicate normally.
It should be noted that Weibu Intelligence does not label the SNI and HOST addresses requested by the sample with certificate information. This is actually out of consideration to prevent false positives. **I think this is correct. As an auxiliary researcher, An important basis for analysis, threat intelligence is better not to be complete, but also to avoid misdirection and misjudgment in subsequent analysis. **If the certificate configured to accelerate the whole site is to forge communication traffic, then configuring the pre-response certificate of RedGuard C2 is to forge the behavioral characteristics of the real C2 server deployed on the public network to achieve anti-mapping effect. This is very necessary.
Extract the certificate serial number: 55e6acaed1f8a430f9a938c5, perform HEX encoding to get the TLS certificate fingerprint:26585094245224241434632730821
| IP | Port | Protocol | Service | Country | City | Title | Time |
|---|---|---|---|---|---|---|---|
| 103.211.xx.90 | 443 | https | Apache httpd | China | Suzhou | Baidu Pictures-Discover the colorful world | 2023-08-28 |
| 223.113.xx.207 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
| 223.112.xx.48 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
| 223.113.xx.40 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
| 223.113.xx.31 | 443 | https | JSP3 | China | 405 Not Allowed | 2023-08-28 | |
| 223.113.xx.206 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
Search Result Amount: 2291
Through cyberspace mapping, 2291 independent IPs were discovered, and verification was conducted to confirm that they were all TLS certificates owned by Baidu. It is difficult to judge whether it is malicious communication based on the communication traffic alone, and the above is for the domain front + C2 front traffic facility. The TLS certificate was forged, successfully interfering with space mapping and threat intelligence, causing wrong information association, making the attacker's traffic characteristics more realistic, and achieving the purpose of forging normal communication traffic.

[^RedGuard]: RG assets using default certificate
Even if there is no covert forwarding processing before the C2 traffic front-end facility, it is still best to change the certificate for RedGuard. By default, the fingerprint library formed by fingerprint recognition of any common component currently commonly used in cyberspace surveying and mapping uses the behavior of the default configuration characteristics of the common component for identification. In these customization processes, different groups may behave differently . The same unique characteristics. Of course, the formation of fingerprints requires a certain understanding of the target components, so as to extract the default characteristics of the target and form an associated fingerprint. Here, the behavioral characteristics expressed by RG certificates are used to conduct network space mapping, which is associated with a large number of RG nodes deployed on the public network.
It is not surprising that the author can extract this fingerprint, but it is still recommended that RedGuard users modify the default certificate information and become a professional Hacker:)
Hijack site response
I believe many readers will be more interested in the hijacking response. The general principle is that when the client initiates a request to the real C2 server, since it does not comply with the inbound rules, the C2 server will obtain the specified normal site and return its response information, so From the effect request side, it seems that the service is interacting with this IP, but in fact, the intermediate C2 server is used as a proxy server to interact with the normal site, so it is difficult to detect abnormalities. If it meets the inbound request, the traffic request will be forwarded to the real C2 service listening port for interaction. The real listening port has been filtered by the cloud firewall and only allows local access. It cannot be directly accessed from the outside. Therefore, judging from the external port opening situation, only the HTTP/S port is open, and in a sense, this is indeed the online port of C2.
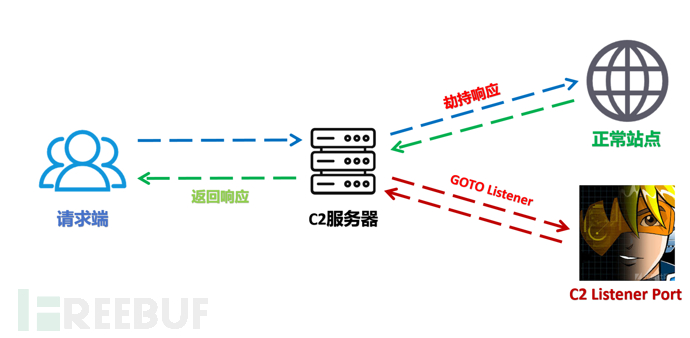
[^Traffic diagram]: C2 server traffic interaction process
In the cyberspace mapping data, the IP's HTTP/S open port response code is 200, not a 302 jump, which is more authentic.
The HTTPS certificate has the same effect as the forged certificate mentioned above and is the fingerprint of the real certificate.
I believe that many red teams will extensively use concealment methods such as cloud functions/domain prefixes during the project process. However, in today's offensive and defensive confrontation game, the above two concealment methods have a fatal problem. It means that we can directly connect to the C2 service, and the result of this is undoubtedly that when we get the cloud function address or the interactive IP/HOST of the domain front, we can directly access the C2 listening service and prove that it is an attack facility.
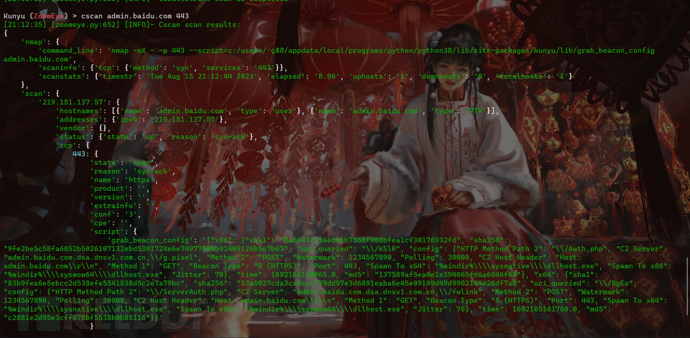
Since the traffic can directly reach C2, you might as well think about whether the security device can perform CS scanning on the traffic that does not match the SNI and HOST to identify whether it is malicious traffic. The same is true for cloud functions or sandbox environments, except for the sample side. There can be more analysis processes at the traffic level.
After the hijacking response, direct access to the HTTP service allows normal website interaction, but Cscan cannot scan out the sample information because the traffic cannot reach the real C2 listener. Normal C2 can only be performed when the characteristics of traffic initiation are met. Interaction, but there is a problem. The C2 scanning script needs to comply with the inbound rules, which puts the coding ability of the blue team analysts to a certain test. The currently public scanning script is in the form of Nmap.
Here are some tips. In addition to domain prefixing, you can also try to register some highly reputable domain names. Some organizations may neglect to register certain domain names. In this case, you can register and use the hidden WHOIS information service as an interactive domain name to increase credibility. higher.
PS I’m sure you can buy it back, I’m sure it’s useless for me to keep it >_<
Identify cloud sandbox fingerprints
JA3 provides a more highly identifiable fingerprint for the encrypted communication between the client and the server. It uses the TLS fingerprint to identify the TLS negotiation between the malicious client and the server, thereby achieving the effect of correlating the malicious client. This fingerprint uses MD5 encryption and is easy to generate on any platform. It is currently widely used in threat intelligence. For example, it can be seen in the sample analysis reports of some sandboxes to prove the correlation between different samples.
If we can grasp the JA3(S) of the C2 server and the malicious client, even if the traffic is encrypted and the IP address or domain name of the C2 server is not known, we can still identify the TLS negotiation between the malicious client and the server through TLS fingerprinting. I believe everyone can think of it after seeing this. This is also a measure to deal with traffic forwarding and concealment methods such as domain fronting, reverse proxy, and cloud functions. The sandbox is used to perform TLS negotiation and generate communication between sample identification and C2. JA3(S) fingerprint is a technical means used in threat intelligence to assist traceability.
This technology was announced last year. When testing the micro-step sandbox environment, it was found that although the number of exit IPs requesting interaction is not large, it is not accurate to identify the sandbox by IP, and this is a feature that is easily changed. However, its JA3 fingerprint is unique under the same system environment. Subsequent feedback was received that the sandbox has completed fingerprint randomization, but recent tests have revealed that it is still not fully implemented. We still hope to face up to the problem of fingerprints on the traffic side.
Currently the main JA3 fingerprints are:
-
55826aa9288246f7fcafab38353ba734
From the perspective of the cloud sandbox, JA3(S) fingerprints are generated by monitoring the traffic interaction between the sample and the C2 server to identify the malicious client for correlation. We think in reverse, and as the C2 front-end traffic control facility, we can also Perform this operation to obtain the JA3 fingerprint requested by the client, and obtain these JA3 fingerprints through debugging different sandbox environments to form a fingerprint library to form a basic interception strategy.
It is assumed that during the staged Trojan interaction process, the loader will first pull the shellcode of the remote address. Then when the traffic recognizes that the request matches the cloud sandbox characteristics of the JA3 fingerprint library, it will intercept subsequent requests. If the shellcode cannot be obtained and the entire loading process cannot be completed, the sandbox will naturally not be able to fully analyze it. If the environment is a stageless Trojan, then the sandbox analysis will also not be able to be finally online on the C2 server. I believe everyone will have a lot of long-timed-out sandbox records hanging on C2 after sleeping. Of course, ideally we Different sandbox environments can be identified, which mainly depends on the reliability of the fingerprint database.
During the test, I found that after adding the JA3 fingerprint of the ZoomEye GO language request library to the fingerprint library, I monitored the RG request traffic. Most of the requests triggered the basic interception of the JA3 fingerprint library features. Here I guessed that the underlying language of the surveying and mapping product It is a partial scanning task implemented in GO language. Through a link, the scanning logic composed of different underlying languages finally completes the entire scanning task. This also explains why the scanning of some surveying and mapping products triggers the JA3 fingerprint interception of the GO language request library. feature. The principle of identification rules is the same as that of cloud sandbox fingerprints. They both take advantage of the uniqueness of the request client environment and request library. Different from the PC side, the request environment of these products basically cannot be changed at will, which also leads to Now that we can grasp the traffic side fingerprint and intercept it , can we think about whether the security device can use the JA3 fingerprint that actively detects the traffic as the basis for interception? Of course, when business traffic is large, there may be certain false alarms. Here we only propose theoretically implementable product requirements.
PS readers can also upload their own samples to the sandbox to obtain and verify their JA3 fingerprints and add them to the fingerprint database. It should be noted that it is meaningless if the sandbox only changes the JA3 fingerprints and not the above fingerprints. What really needs to be solved is each time The fingerprints are not the same during sandbox dynamic analysis, and their changes need to be as non-repetitive as possible. If the repetition rate is high, they will still be used as fingerprints.
Custom sample fingerprint
Here is a practical scenario. When an attacker wants different listeners to correspond to independent samples, and when a certain sample is captured or wants its key to "fail", he can specify whether the sample traffic is allowed to be released to C2. In this case, Custom sample fingerprints are available. This function is based on customizing the HTTP Header field of the Malleable Profile as the sample fingerprint " sample Salt value " to provide unique identification for the same C2 listener/Header Host. **In addition, the Trojan sample fingerprint generated in combination with other relevant request fields can be used to detect the survivability of custom samples.
According to the attacker's task requirements, the Trojan sample fingerprint identification function can perform "offline operations" for samples that are expected to be invalid , to better avoid the sample connectivity correlation of malicious research and judgment traffic and the phased sample PAYLOAD attack load acquisition and analysis, giving the attacker more information. Personalized concealment measures. For different C2 listeners, you can configure aliases for different Malleable Profiles and customize the field names and values of related headers as the sample Salt value, which can be used as a unique identifier to distinguish between different samples. The following code is for convenience of explanation, but in actual attack and defense scenarios, we can give more realistic HTTP request packet fields as a basis for judgment.
http-get "listen2" {
set uri "/image.gif";
client {
header "Accept-Finger" "866e5289337ab033f89bc57c5274c7ca"; //用户自定义字段名及值
metadata {
print
}
}
}
HTTP traffic

As shown in the figure, we use the above sample Salt value and Host field as the basis for fingerprint generation. Here we know:
-
Salt值:866e5289337ab033f89bc57c5274c7ca
-
Host field value: redguard.com
According to splicing the above values and using 32-bit lowercase MD5 hash, the sample fingerprint is:
redguard.com866e5289337ab033f89bc57c5274c7ca //拼接后待哈希字符串
d56da55231dfd8e9a4f3ad2e464f49e4 //Sample FingerPrint
The above sample fingerprint is currently known. Now we set the custom Header field and sample fingerprint in the RedGuard configuration file for malicious traffic interception. **It is worth noting that the Header fields and values here can be customized to be more realistic. In order to better display the effect, Accept-Finger and Hash of long fields are used as examples. **We can expand multiple sample fingerprints. The FieldName and FieldFinger fields between different fingerprints are separated by commas. The FieldName field needs to be consistent with the Header field name configured in the Malleable Profile. This is also an important basis for obtaining the Salt value carried in the request packet.
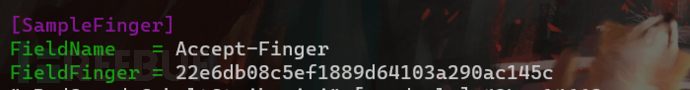
Because the RG configuration file is a hot configuration, we do not need to restart and stop the RG to intercept samples that we hope will become invalid. When we want the sample to be valid again, we only need to delete the relevant sample fingerprints in the RG configuration file. Can achieve.
Honeypot malicious trapping
The principle of honeypot malicious trapping mainly relies on the hijacking response or redirection function of RG traffic guidance, which directs analysts who study the C2 facility to the address of the honeypot sandbox. In the state of hijacking response, RG will send inbound messages that do not meet the requirements. The regular request traffic is directed to the honeypot assets . When encountering some more powerful honeypots (such as those that capture the operator's mobile phone number), the client will initiate a request based on the response of the target site and be hijacked by jsonp to obtain relevant information.
Just imagine, when analysts directly access the C2 online port, they will be directed to honeypot assets. The result will undoubtedly be disruptive to analysts, and analysts will be maliciously directed to request honeypot assets, and the honeypot monitoring terminal will capture The relevant information of the blue team analysts can be used to trace the source of the error. If the analysis of the goal from the beginning is wrong, how can we get good results? This will undoubtedly cause serious internal friction to the defensive team.
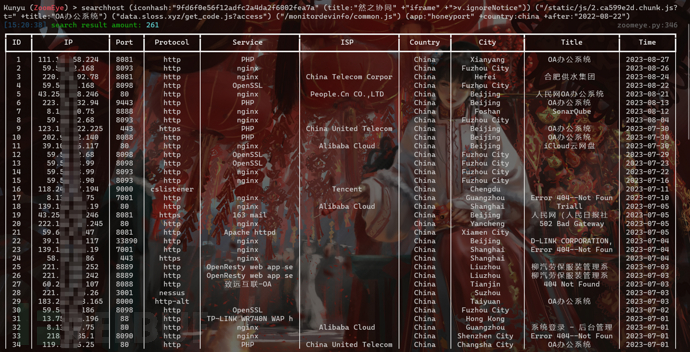
Here is a set of ZoomEye fingerprints associated with honeypot assets:
(iconhash:"9fd6f0e56f12adfc2a4da2f6002fea7a" (title:"然之协同" +"iframe" +">v.ignoreNotice")) ("/static/js/2.ca599e2d.chunk.js?t=" +title:"OA办公系统") ("data.sloss.xyz/get_code.js?access") ("/monitordevinfo/common.js") (app:"honeyport" +country:china +after:"2022-08-22")
The way to achieve this effect is very simple, just change the relevant key values of the RG configuration file.
# RedGuard interception action: redirect / reset / proxy (Hijack HTTP Response)
drop_action = proxy
# URL to redirect to
Redirect = https://market.baidu.com
PS I believe everyone knows how to configure it without explaining it:)
This method is a kind of clever trick, and it is more reflected in the idea. If it is further utilized, the honeypot capture function can be deployed in the C2 front-end traffic control facility and then interactive traffic guidance is performed. The effect is the same as that of traditional honeycomb. Jars can also obtain the client's browser cache data. However, I personally feel that in the public version, it may not be meaningful to apply it to the current stage of offensive and defensive confrontation. It is meaningless for the attacker to capture the social information of the blue team analysts and then trace the source. Of course, if you take a step back and think about it, this may make the analysis of C2 samples more dangerous. When a black and gray attacker can obtain the virtual identity of the analyst, it will still be more dangerous if the virtual identity can be converted into real identity. Therefore, I believe that future research and analysis should be more cautious and alert.
postscript
We have reached a relatively relaxed stage again, which is also my favorite part of writing articles. I haven’t written an article for a year, and I haven’t paid attention to the security direction, huh. . There may be some deviations from the situation. I have just completed my fourth year of HW experience, and a friend said something that impressed me deeply, "It feels like HW to us is just participating in a lively event that has little to do with us ." Hahahaha, it feels very appropriate. . Looking back on my own safety experience, I still feel that my learning is relatively complex. Is it because I am broad-minded and make reservations, and I am accumulating more than I am learning? My later plans may not focus on technology. To be honest, I have never been a person who likes to pursue technology, so after I graduate, I may work in a job that is oriented towards interacting with people and technology, rather than focusing on security. Research. I position myself as a person who is good at understanding + association + innovation. Maybe to put it bluntly, I am a person who is good at summarizing and innovating. Therefore, I always like to be exposed to emerging things, because this can always inspire me and discover something different . s things. 2023 is a new beginning, and the wind is still on the way.
Finally, I wish you all that your wishes will come true and your dreams will come true!