Shell commands to switch root users, manage configuration files, and check hardware
Like other UNIX-based systems, Linux can be used by multiple people at the same time. The multi-user feature allows multiple people to have accounts on a single Linux system and protect their data from being destroyed by others.
If you want to complete most management tasks, you need to log in as the root user (also known as the super user), or temporarily obtain root privileges (usually using the sudo command). Ordinary users without root permissions cannot change or even view certain configuration information of the Linux system in some cases. In particular, security features such as passwords are particularly protected.
This article will also introduce how to monitor devices in Linux systems.
Switch root user
Two methods
As a system administrator of a Linux system, you usually log in to the system as a normal user account and want to request administrative rights when needed. You can choose to use two different methods to achieve this goal: the su command and the sudo command.
su command (switch user) : The su (switch user) command is a common method for temporarily switching to the identity of another user, usually root, to gain full system administration rights. When using the su command, the administrator needs to enter the password of the target user (usually root) to authenticate. Once successfully switched to the target user, the administrator will have all the permissions of that user and can perform various system commands and configuration changes. One feature of the su command is that after switching to the target user identity, the administrator will remain under that user until manually exiting or logging off. This means that care needs to be taken to avoid unnecessary privileged operations.
sudo Command (Execute Command as Privileged Mode) : The sudo (Execute Command as Privileged Mode) command provides a more flexible and secure way to gain administrative rights when needed without having to completely switch to the root user. When using the sudo command, the administrator needs to enter their own password (not the target user's password) to authenticate themselves. Administrators can use sudo to run specific commands when needed without having to remain privileged for long periods of time. This helps reduce potential security risks because the administrator can only gain privileges when necessary and return to normal user status immediately after the command is executed. In addition, the sudoers file allows system administrators to precisely control which users or user groups can use sudo and which commands can be run, thereby improving security and manageability.
Detailed introduction to su command
suCommand (short for Switch User) is a command used to switch user identities in Linux systems. It is typically used to switch to another user, usually root, in order to perform tasks that require privileged access. The following is sua detailed introduction to the command:
Basic syntax :
su [选项] [用户]
- Options:
-(hyphen) is used to completely emulate the target user's environment, including environment variables and working directory. - User: The target user to switch to. If no user is specified, it usually defaults to the root user.
Usage permissions :
- Typically, only system administrators (or users with sudo privileges) can use
sucommands to switch to the identity of root or another user. - By default, ordinary users can
suswitch to the root user, but they need to know the root user's password.
Switch to the root user : Use suthe command to switch to the root user. The administrator needs to enter the root user's password. For example:
su

Switch to other users : Administrators can also use sucommands to switch to other users, and need to specify the user name of the target user. For example, switch to user "john":
su john
Fully emulate user environment : Use -the option to emulate the target user's complete environment, including the user's working directory and environment variables. This is useful for performing tasks related to the user's environment. For example, switch to the root user and simulate its environment:
su -
Exit a su session : To exit sua session, you can use exitthe command or Ctrl+Dkey combination. This will return you to the previous user identity.
Detailed introduction to sudo command
sudo(short for superuser do) is a command used in Linux and Unix systems to execute commands in a privileged manner. It allows authorized users to execute commands run with root privileges or other specific user rights without completely switching to the identity of a privileged user. The following is sudoa detailed introduction to the command:
Basic syntax :sudo [选项] [命令]
- Options:
-uUsed to specify which user to run the command as, usually the root user. - Command: The command to be executed in privileged mode and its parameters.
Usage permissions :
- Only users or groups listed in the sudoers file have permission to use
sudocommands. - The sudoers file is usually located in
/etc/sudoers, and can only be edited by a privileged user, such as root.
Executing a command : To execute a command in privileged mode, the user needs to prepend the command sudoand then enter their password to authenticate. For example, to list directory contents with root privileges:
sudo ls /root
Switch user execution : Use -uoptions to specify that a command should be executed as a specific user. For example, to edit a file as user "john":
sudo -u john nano /path/to/file
Privilege elevation persistence : Once a user enters a password, the password does not need to be verified again for a period of time (default is 5 minutes). This means that within that time window, a user can run multiple privileged commands in succession without having to repeatedly enter their password.
sudoers file configuration : The sudoers file contains rules for which users can use sudo and which commands can be run. The sudoers file can be visudoedited using the command, which checks for syntax errors to avoid corrupting the file.
Exit the sudo session : After executing a privileged command, the user is automatically returned to his normal user identity. No need to manually exit sudothe session.
/etc/passwd file
/etc/passwdFile is one of the text files in Linux and Unix systems that stores user account information. It contains basic information about each user in the system, but does not include the user's password. The following is /etc/passwda detailed introduction to the file:
File Location : /etc/passwdFiles are usually located in the root directory of Linux and Unix systems.
File format : /etc/passwdThe format of a file is fields separated by colons (:). Each row represents a user account, and the meanings of the fields are as follows:
- Username: User's login name.
- Password field: In the past, this field stored the user's password hash, but now it is often replaced by
xor*and the actual password information is stored in/etc/shadowa file for added security. - User ID (UID): Each user has a unique numeric identifier that is used to identify the user internally within the system.
- Group ID (GID): Numeric identifier of the primary user group associated with the user.
- User description information (gecos): usually includes the user's full name, contact information, etc.
- 主目录:用户登录后的起始目录。
- 登录Shell:用户登录后默认使用的Shell。
例如,以下是/etc/passwd文件中的一行示例:
john:x:1001:1001:John Smith:/home/john:/bin/bash
密码信息的分离: 用户密码不再存储在/etc/passwd文件中,而是分离存储在/etc/shadow文件中。这是为了增加密码安全性,因为/etc/passwd文件通常对系统中的所有用户可读,而/etc/shadow文件只对root用户可读。
访问权限: /etc/passwd文件通常对系统中的所有用户可读,因为它包含了用户账户的基本信息,但只有root用户才能编辑此文件。
/etc/passwd文件是Linux和Unix系统中存储用户基本信息的重要文件之一。它包含了用户的用户名、UID、GID、用户描述、主目录和登录Shell等信息,但密码信息已分离存储在/etc/shadow文件中,以提高安全性。
/etc/passwd文件里为什么有乱七八糟的用户?

/etc/passwd文件中包含了系统中所有用户的基本信息,包括系统用户和服务账户。这些用户不仅用于普通用户登录,还用于系统进程和服务的运行。以下是为什么/etc/passwd文件中包括系统用户的一些原因:
1. 系统进程和服务:许多系统进程和服务需要运行在特定的用户或用户组权限下,以增加安全性和隔离性。这些用户账户通常称为系统用户或服务账户,它们负责运行特定的服务,如Web服务器、数据库服务器、邮件服务器等。这些用户账户通常是系统自动创建的。
2. 权限控制:系统用户和服务账户通常受到严格的权限控制。它们的主要目的是运行系统进程和服务,而不是用于用户登录。因此,它们的Shell字段通常设置为/sbin/nologin或/usr/sbin/nologin,这样任何尝试登录到这些账户的操作都会被拒绝。
3. 隔离:将系统进程和服务运行在特定的用户账户下有助于隔离它们的操作。这样,如果某个服务出现漏洞,攻击者将受到限制,无法直接访问系统的关键部分。
一些常见的系统用户和服务账户,如root、bin、sys等,是系统默认创建的,用于运行系统进程和服务。它们的存在是为了确保系统的正常运行和安全性。
尽管这些系统用户不用于人工登录,但它们的存在对于系统的正常操作和管理是必不可少的。如果怀疑某个用户账户是否应该存在或需要删除,务必小心,因为删除系统关键用户可能会导致系统不稳定或不可用。一般情况下,只有有经验的系统管理员才应该对这些用户账户进行操作。
/etc/shadow文件
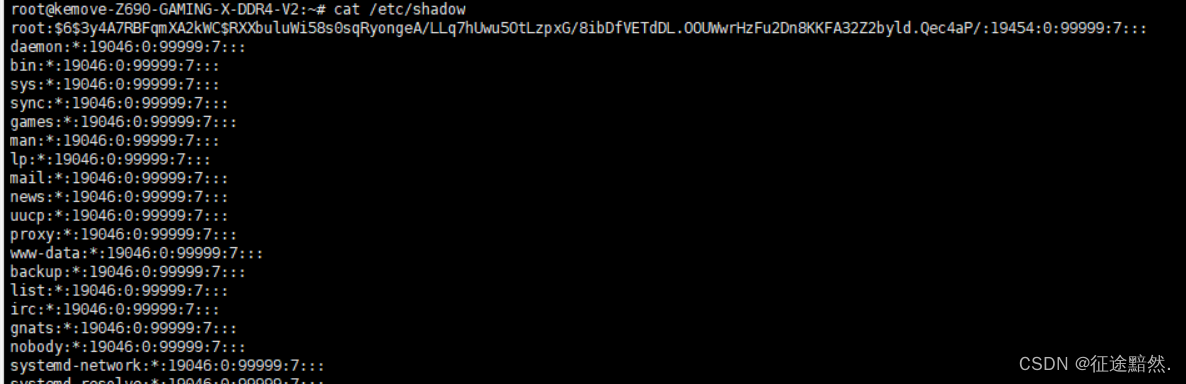
/etc/shadow 文件是Linux系统中用于存储用户密码哈希值和与密码策略相关的其他安全信息的文件。这个文件对于保护用户密码的安全性至关重要,因为它通常只能由具有足够权限的用户(通常是root用户)访问,普通用户不能直接读取或修改它。
/etc/shadow 文件的常见格式和字段:
每一行代表一个用户账户,字段之间用冒号(:)分隔。
- 用户名:用户的登录名。
- 密码哈希值:用户密码的哈希值。密码通常被哈希后存储,而不是以明文形式存储。
- 上次修改密码日期:表示密码最后一次更改的日期,通常是从1970年1月1日开始计算的天数。
- 密码最短有效期:指定密码必须保持不变的最短天数。
- 密码最长有效期:指定密码允许保持不变的最长天数。
- 密码警告期限:指定在密码即将到期前多少天发出警告通知用户更改密码。
- 密码失效期限:表示密码过期的日期,通常也是从1970年1月1日开始计算的天数。过期后,用户将无法使用该密码登录。
- 密码不活动期限:指定密码在用户不活动多少天后失效,即如果用户在此期限内未登录系统,则密码将失效。
- 账户失效日期:表示用户账户的失效日期,通常也是从1970年1月1日开始计算的天数。失效后,用户将无法登录。
- 保留字段:这些字段通常为空,保留供将来使用。
管理配置文件
/etc—该目录包含大部分基础Linux系统配置文件。
/etc/cron*——该组中的目录所包含的文件定义了crond 实用工具如何按照每天(cron.daily)、每小时(cron.hourly)、每月(cron.monthly)或每周(cron.weekly)计划运行程序。
etc/httpd——包含用来配置 Apache Web服务器行为(特别是 httpd守护进程)的各种文件(在Ubuntu和其他Linux系统上,使用的是/etc/apache 或/etclapache2).
/etc/mail—包含用来配置sendmail 邮件传输代理的文件。
/etc/ppp——包含几个用来设置点对点协议(PPP)的配置文件,以便可以让计算机拨号到Intermet(在拨号调制解调器非常流行时,PPP经常被使用)。
/etc/security——包含为计算机设置多种默认安全条件的文件(主要是定义如何完成身份验正)。这些文件是pam包(一种插入式身份验证模块)的一部分。
crontab——为运行与cron实用工具相关联的自动化任务和变量而设置时间(比如与cron相关联的SHELL和PATH)。
hostname—包含本地系统的主机名。
hosts——包含计算机上可用的IP地址和主机名(通常使用该文件保存LAN或者小型私人网络上的计算机名)。
passwd——存储本地系统中所有有效用户的账户信息。其外,还包括其他信息,比如主目录和默认Shell(但很少包括用户密码,通常用户密码保存在/etc/shadow文件中)。
rpc——定义远程过程调用名称和编号。
services——定义TCP/IP和UDP服务名及其端口分配。
shadow ——包含passwd文件所定义用户的加密密码(相对于直接在passwd文件中存储原始加密密码,这种方法更安全。passwd文件必须是公开可读,但shadow文件只能由root用户读取)。
shells——列举系统中可用的Shell命令行解释器(比如 bash、sh、csh等)及其位置。
sudoers——该文件设置了那些没有权限运行某些命令的用户通过使用sudo命令可以运行的命令。特别是使用该文件为所选择的用户提供root权限。
检查硬件命令
查看CPU
To view CPU information and performance statistics, you can use different commands:
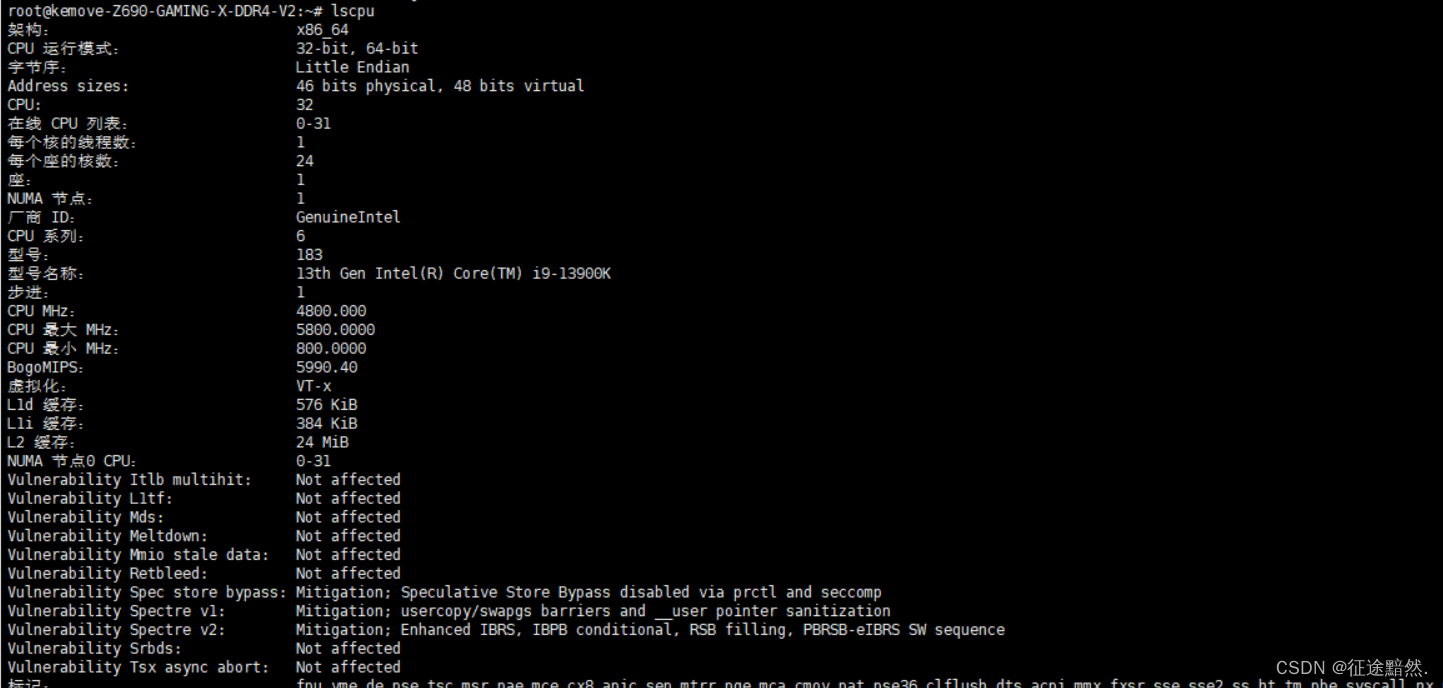
1. Use lscputhe command : lscpuThe command can display detailed information of the CPU, including CPU model, architecture, number of cores, number of threads, etc.
lscpu
2. Use cat /proc/cpuinfothe command : /proc/cpuinfoThe file contains information about the CPU. Use catthe command to view the contents of this file, as shown below: details for each core are displayed.
cat /proc/cpuinfo
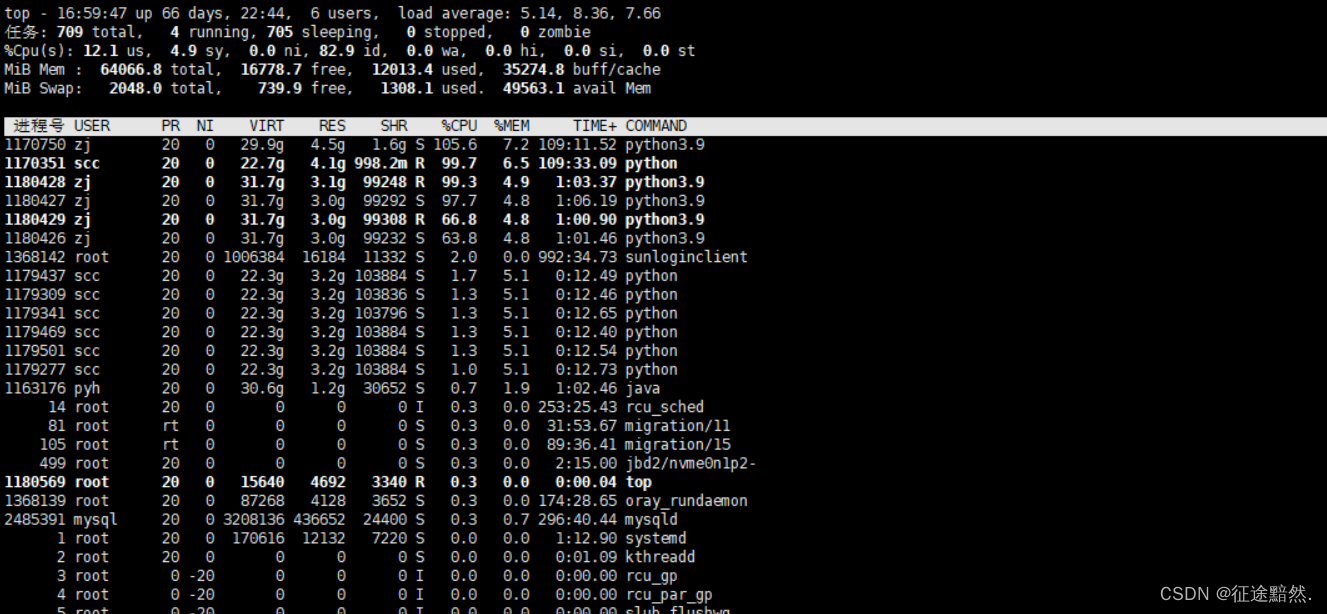
3. Use topthe command : topThe command is a real-time system performance monitoring tool that can view the system's CPU utilization and other performance indicators in the terminal. Run the following command to start top:
top
To exit top, press qthe key.
View GPU
To view the GPU (Graphics Processing Unit) information in the system, you can use the following methods:
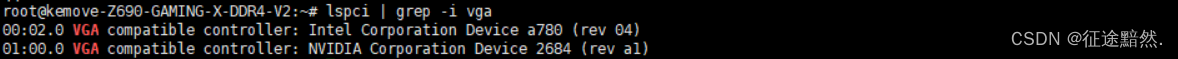
1. Use lspcithe command : lspciThe command is used to list the PCI devices on the system, including the GPU. Run the following command in the terminal to view GPU information:
lspci | grep -i vga
Displays information related to graphics devices (GPUs), including manufacturer, model, and PCI identifier.
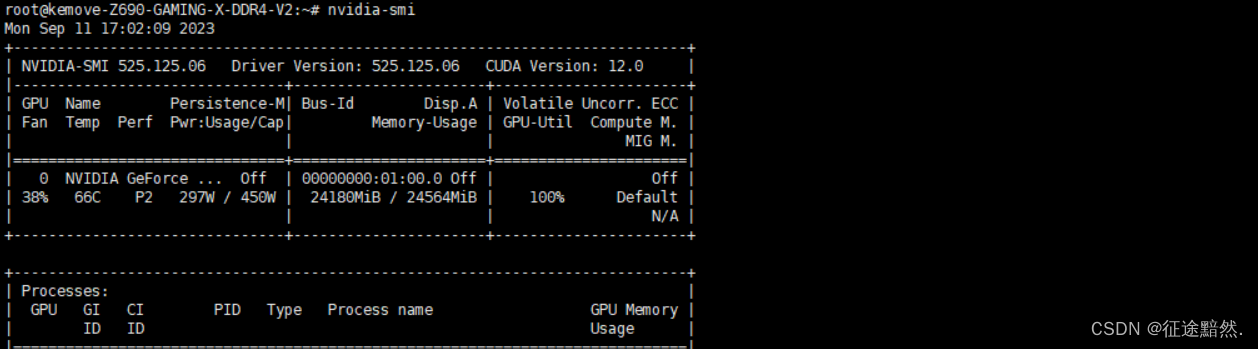
2. Use nvidia-smithe command (only for NVIDIA GPU) : If you are using an NVIDIA graphics card, use nvidia-smithe command to view GPU information and performance statistics. Run the following command in the terminal:
nvidia-smi
Displays detailed information related to NVIDIA GPUs, including GPU model, driver version, GPU utilization and temperature, etc.