The root user in Linux is a super administrator, who can brute force the password for the root user, which is very unsafe. In work, we generally prohibit the root user from directly logging in remotely, and open one or more ordinary users, only allowing ordinary users to log in. If necessary With the root user, you can switch to root with su or sudo to execute commands with root privileges.
1. Root cannot log in remotely, but all users can switch root
First open the configuration file:
vim /etc/ssh/sshd_config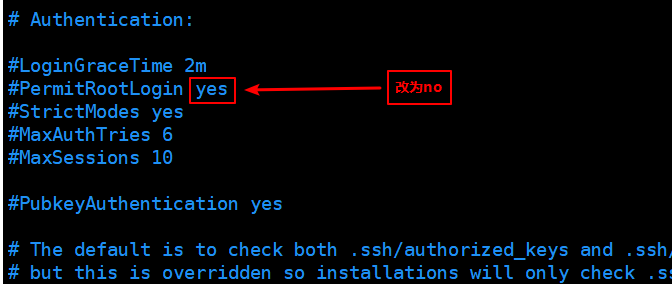
This line means that the root user is allowed to log in, so we change it to no, and the root user is not allowed to log in directly.
After saving and exiting the configuration file, restart the sshd service:
systemctl restart sshd.serviceAfter re-establishing the connection, we found that the root user can no longer log in. We can only log in through ordinary users and then switch.
2. Root cannot log in remotely, but only specific users can switch root
Generally, ordinary users can log in as root by executing the "su -" command. In order to strengthen the security of the system, it is necessary to establish an administrator group, only allow users in this group to execute the "su -" command to log in as root, and allow users in other groups to enter the correct password even if they execute "su -". It is also not possible to log in as root. Under Unix and Linux, this group is usually named " wheel ".
1. Add a user and add this user to the wheel group
adduser admin
passwd admin
usermod -G wheel admin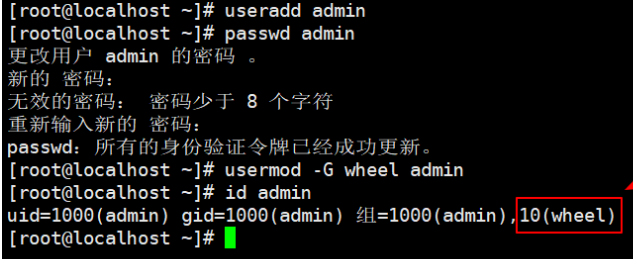
2. Modify /etc/pam.d/su
auth required pam_wheel.so use_uid 去掉这行注释 3 Modify /etc/login.defs
vim /etc/login.defsAdd a line at the end of the file
SU_WHEEL_ONLY yes3. Add a user with the same permissions as root
- adduser admin
- passwd admin (change the password, the password must follow the password complexity)
Modify the /etc/sudoers file, find the following line, and add a line under root, as follows:
vim /etc/sudoers## Allow root to run any commands anywhere
root ALL=(ALL) ALL
admin ALL=(ALL) ALL 这个文件只读是一种保护机制,如果你使用vi编辑器的话,只要保存时使用:wq!就可以保存了。 或者使用visudo命令来进入sudoers文件的编辑,就可以正常保存Fourth, ssh restricts IP and user login
1. Configure sshd restrictions
Add the ip or network segment that allows ssh login in /etc/hosts.allow
sshd:192.168.1.2:allow #表示一个ip
sshd:192.168.1.0/24:allow #表示一段ipAdd an IP that does not allow ssh login in /etc/hosts.deny
sshd:ALL #ALL表示除了上面允许的,其他的ip 都拒绝登陆ssh2. Use iptables firewall restrictions
iptables -A INPUT -p tcp -s 192.168.1.2 --destination-port 22 -j ACCEPT
iptables -A INPUT -p tcp --destination-port 22 -j DROP
————————————————
Copyright statement: This article is the original article of CSDN blogger "Yiliang Cool", following the CC 4.0 BY-SA copyright agreement, please attach the original source link and this statement.
Original link: https://blog.csdn.net/annita2019/article/details/106233955/