原文题目《VoltageIDS: Low-Level CommunicationCharacteristics for AutomotiveIntrusion Detection System》
The continuous expansion of in-vehicle computer functions is intended to improve the safety and comfort of drivers. However, this also increases the possibility of being attacked. Today's methods to deal with these attacks have certain flaws, and most of these methods All require changes to the CAN protocol to function. This article focuses on protecting the in-vehicle network and proposes a relatively new in-vehicle intrusion detection system called VoltageIDS . This system makes full use of the characteristics of CAN signals as its fingerprint, and it does not require changes to the existing system structure, and its effectiveness has been proven through real cars. It is also the first automotive intrusion detection system capable of distinguishing between bugs and bus-off attacks .
Table of contents
Existing attack patterns on in-vehicle CAN networks
VoltageIDS knowledge background
1. Signal detection and preprocessing
4. Progressive/incremental learning
Simulating camouflage attacks on real vehicles
Article introduction
There are many electronic control units (ECUs) in cars, which are driving computers. You can probably find 50-100 ECUs in more luxurious cars. Each one is assigned a specific function to be performed, and because they each perform The functions will be divided into groups of in-vehicle network subnets, and messages sent between these ECUs will pass through the CAN protocol system that can provide stable communication. However, the CAN protocol lacks the function of message source identification, which makes the vehicle vulnerable to attacks. With the development of automotive functions, the number of access points to the CAN network in the vehicle is also increasing, making it easier for attackers to invade. The intrusion detection system IDS proposed in this article, called VoltageIDS, does not require changes to the existing driving system to work.
The starting point of this article is to distinguish legitimate or illegal ECUs based on their electrical characteristics. Even if they send the same message, it is difficult for an attacker to imitate the inherent electrical characteristics of the ECU. Therefore, the contribution of this article is:
- Analyze the shortcomings of existing IDS.
- The proposed VoltageIDS can be put on the road directly after the in-car system is installed, without the need to make changes to the in-car network.
- VoltageIDS was verified on a CAN bus prototype, a real vehicle, and a moving vehicle. This was the first time that many proposed IDSs were tried on the road. The results proved that masquerade attacks or bus shutdown attacks can be detected with a low error rate.
- Addresses the issue that device characteristics may change due to environmental factors, such as time and temperature.
- The ability to identify bus-off attacks, which was recently proposed, and VoltageIDS is the first system to be considered.
Related work
Existing attack patterns on in-vehicle CAN networks
In addition to the direct physical connection to a laptop that can cause attacks, indirect ways of invading the CAN network in the car include:
- Inject attack messages into the car's multimedia system
- Intrusion through the automotive aftermarket telematics control unit TCU (connected to the CAN network through the OBD-Ⅱ standard port)
- Vulnerability through telematics devices connected to cellular networks
Existing car IDS
Because most messages on the CAN network are sent periodically , this is also a feature that many IDSs can fully exploit to detect intrusions. The messages injected by the attacker will obviously speed up the message frequency. This is the car based on message frequency. ids . But later, more sophisticated attackers emerged that could simulate the message sending frequency of the CAN network in the car. After the limitations of automotive IDS based on message frequency were discovered, an intrusion detection model based on behavioral characteristics was proposed. ECUs connected to the CAN network have unique behavioral characteristics. If the CAN insulation and the identified ECU cannot be paired, it will It is believed that the ECU was damaged and invaded.
Some researchers used the characteristics of the clock offset of messages sent by the ECU to identify the ECU, but this was later proven to be imitable by attackers. The use of the electrical characteristics of CAN sent by the ECU to identify the ECU has also been studied by many scholars, but there are limitations, because there are multiple arbitration decision-making processes from different sending ECUs on the CAN network at the same time, and the real situation of the car on the road must also be considered. , it is not suitable to use the extended frame format, nor is it suitable to make hardware modifications to the existing ECU.
VoltageIDS knowledge background
signal inconsistency
The detection system method proposed in this article comes from the observation of two different ECUs sending the same message. On the physical layer, these two preferences will still be inconsistent, even if the two ECUs are products made by the same manufacturer. . This phenomenon may also be partly due to their different cable lengths and the increased wiring resistance as the cable length increases .
CAN protocol
- Differential signaling/encoding: CAN uses differential signaling, which makes it noise-immune and error-tolerant. The current in each line is the same and in opposite directions to produce a field cancellation effect to reduce noise. Balanced differential signaling reduces noise coupling and allows high signal rates over twisted pair cables, which enhance CAN's high noise immunity. One twisted pair is CANH and the other is CANL. The deviation of the two wires in the recessive 1 state is 3.5v, and the deviation in the dominant 0 state is 1.5v.
- CAN frame format: CAN networks are configured to accommodate two frame formats, standard frames (supporting 11-bit identifiers) and extended frames (supporting 29-bit identifiers). The CAN standard identifies four frame types: data frame, remote frame, error frame and overload frame . All trues begin with a start-of-frame bit indicating the start of frame transmission. The VoltageIDS system in this article covers the verification of frame types and can also verify the newly proposed bus shutdown attack . The standard frame consists of four parts: identifier, data length code DLC, data, and cycle check code CRC. The data part occupies up to 8 bits, and the identifier bit is the identifier of the sender, which represents its priority and meaning. Different ECUs are generally set not to use the same identifier. An ECU can have multiple identifiers, and different identifiers correspond to different functions.
- Arbitration: When multiple ECUs try to transmit CAN messages at the same time, the CAN network will provide a lossless arbitration decision process to determine the priority between such colliding messages. The arbitration decision process requires all ECUs to synchronously sample every bit of the identifier field on the CAN bus network. If the ECU transmitting a dominant 0 bit collides with an ECU transmitting a recessive 1 bit, the dominant bit ECU can take priority. Arbitration ends only within the identifier field; transmission of fields outside the identifier field is considered an error. The VoltageIDS in this article
Bus-Off Attack
Bus shutdown attack: This is a newly proposed attack. As mentioned above, according to the CAN standard, simultaneous transmission of bits in fields other than the identifier field is considered an error. When an ECU detects a dominant 1 state when trying to transmit a recessive 0 state, its transmission error counter TEC will increase, that is, the bit error will increase the number of the counter by 1. When the accumulation exceeds 255, it will enter the bus shutdown mode . , the ECU is forced to shut down. In this case, the attacker can use this error handling mechanism to conduct a DoS attack on the in-car CAN network. At this point it is difficult for the system to tell whether it is an error or an attack .
system model
ECU identification/car IDS
ECUs can send CAN messages related to their functions to the CAN network in the car. For example, the engine ECU can only transmit CAN messages related to the engine. The VoltageIDS in this article will analyze the electrical characteristics of the CAN message to identify which ECU sent it. After determining the characteristics of the message sent by which ECU, it also determines whether the ECU can transmit the CAN message. If the verification is invalid, it will be It is thought that the ECU is damaged.
An attacker can send seemingly valid CAN messages, but it is difficult to imitate the electrical characteristics. VoltageIDS analyzes the CAN electrical signals in the physical layer, not the CAN messages in the data layer, but it is difficult for an ECU destroyed by an attacker to generate Electrical signal, the attacker would also need to install an additional device to generate an electrical signal, but this is easily recognized by the driver and therefore is not considered.
attacker model
Regardless of the fact that the attacker can directly connect the device at the physical level to attack the in-car network (because it will be discovered by the driver), the attacker, that is, the hacker of the car network must be able to access the in-car CAN if he wants to cause chaos in the internal functions of the car. Network approach, they can use different types of ECUs as access channels:
- Pre-market ECUs: These ECUs are installed in the car when it is produced. For example, some telematics ECUs are connected to external cellular networks and can easily become targets of attacks.
- Post-market ECU: Some automotive applications plugged into the OBD-II port will connect the in-vehicle network to the external network and become the target of attackers.
Attack type
The detection ranges that VoltageIDS can cover include:
- Masquerade Attack: Manipulating an ECU that manages safety-critical functions and hiding the fact that it has been compromised allows an attacker to inject harmful information into the in-vehicle network.
- Bus-Off Attack: The attacker remotely sends fields other than the identification field for simultaneous bit transmission, which causes the target ECU to enter bus-off mode.
Methods of this article
VoltageIDS consists of three stages: 1. Signal detection and preprocessing; 2. Feature extraction; 3. Intrusion detection (also divided into camouflage attacks and bus shutdown attacks according to attack types).
1. Signal detection and preprocessing
Due to the presence of noise, the voltage of the two signal lines of the CAN protocol may be different from the ideal expected value. VoltageIDS reduces the amount of noise by measuring and examining the signal from the differential channel instead of a separate channel. The electronic CAN signal can be divided into dominant 0 state and recessive 1 state . The dominant 0 state is actively sent by the sender, and the recessive 1 state is the voltage passively returned by the resistor. Therefore, Voltage considers the dominant 0 state more. , that is, the dominant state , because it may contain more electrical characteristics about the sender.
And VoltageIDS focuses on the signal parts of states 1->0 and 0->1, which are regarded as positive slope and negative slope . IDS processes electronic CAN signals to obtain dominant states, positive slopes, and negative slopes.
2. Feature extraction
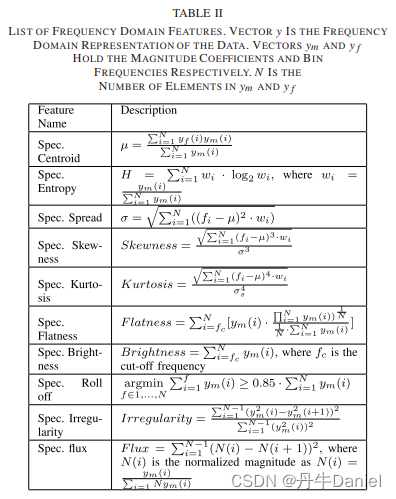
A total of 20 scalar features each from the dominant state, positive slope, and negative slope in the time/space domain were considered, as shown in the table below, for a total of 60 features. But this may also cause too much calculation, so the SFS algorithm is used to select available features. The selected features are all evaluated through evaluation functions to reduce the classification error rate MCE.

3.1 Disguise attack
VoltageIDS detects disguise attacks by constructing a multi-classifier, and the number of classes is equal to the number of ECUs in the in-vehicle network. So it is a supervised learning with two steps: training and testing. In the training stage, features and corresponding CAN message IDs are used to label the training. During the testing phase, the extracted features of a new CAN message are judged.
3.2 Bus shutdown attack
The previous multi-classifier can only identify those ECUs that have been trained based on their electrical characteristics. For bus shutdown attacks where multiple messages are transmitted simultaneously, the electrical characteristics may be mixed, but will only be classified by the model into one ECU. , so VoltageIDS can only classify this signal as unknown first .
The new detection method to be adopted in this paper requires the identification of new or unknown data that has not been used to train the classifier. VoltageIDS uses a simple threshold-based method to detect position signals as an extension of the basic model, using a SVM with RBF technique applied to a single classifier . For mixed signals, a single classifier can be created, which considers the possibility that all signals come from the same ECU, and gives a score to indicate how closely it matches a legitimate ECU. A signal smaller than a specified threshold is considered a position signal.
4. Progressive/incremental learning
Voltage signals are very sensitive to environmental factors, such as temperature and time, which may affect them. VoltageIDS is also not very effective under temperature changes, so VoltageIDS has been improved based on the incremental learning method. The input data continuously updates the existing classifier, which is dynamic supervised learning . A method was chosen to enhance the robustness of the SVM classifier, which is descending learning to exclude old data from the classifier.
method evaluation
Evaluate the effectiveness of VoltageIDS on CAN bus prototypes and real cars.
Experimental setup
- CAN bus prototype: CAN bus network with 12 CAN nodes (ECU), operating at a common CAN network speed in practice, that is , a bit rate of 500kbps. The CAN shielding plate removes most of the resistors, leaving only two.
- Real vehicles: Two real cars were selected for evaluation
- Electronic CAN signal collection: Use an oscilloscope to collect CAN electronic signals from CAN bus prototypes and real vehicles. The oscilloscope is connected to CAN_H and CAN_L, and after obtaining the analog signal, it is decoded into CAN information through the NRZ encoding rule.
- Classification algorithm: SVM and BDT (support vector machine and decision tree) are used in matlab. The linear function is used as the SVM kernel. There are 30 decision trees in BDT. More than 150 sets of data were collected. Randomly select data for training and other data for testing.
- Performance indicators: Use precision, recall, and F-score as evaluation indicators. High precision and high recall represent low FPR false positive rate and low FNR false negative rate. If the FPR is too high, the alarm will be called frequently and the driver will feel uncomfortable. The F-score represents the harmonic mean of precision and recall .
training set size
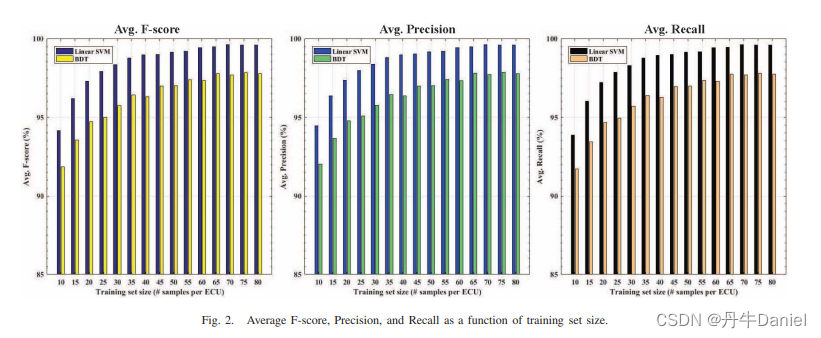
Only the signals generated on the CAN bus prototype were considered, and 100 inputs on each ECU were selected for testing. Fig.2. shows the average F-score, precision and recall. It can be seen that as the training set size increases, the score also increases.
Feature extraction
Feature extraction is to select a subset of relevant features for model construction in order to simplify the model, shorten training time and reduce overfitting to improve generalization. Project the original feature space into a low-dimensional space like principal component analysis. However, selecting the most likely feature combinations does not necessarily achieve the best results, and sometimes overfitting can occur.
Simulating camouflage attacks on real vehicles
The diagnostic CAN subnet-DCAN on the real vehicle was selected to test the model effect under camouflage attack, and it was found that the F score result was not very good. The possible reason is that VoltageIDS cannot distinguish CAN messages with different CAN IDs sent by the same ECU. As an alternative, it is considered that each ECU has a specific ID used for diagnostic protocols. It is better to use an alternative scheme than to use a normal CAN ID. Taking into account temperature changes, the results are also acceptable.
Bus shutdown attack detection and the impact of temperature changes will be updated later...