Linux network
understanding of the network
Problems in network transmission:
- Find the host we need to transfer
- Solve the problem of long-distance data transmission loss
- How to carry out data forwarding and path selection issues
If there is a problem, there is a solution;
We put problems of the same nature together and come up with solutions
The solution is designed as a layered structure, with high cohesion within the layers and low coupling between layers.
The layered structure is conducive to reducing later maintenance costs, and only errors on a certain layer need to be processed.
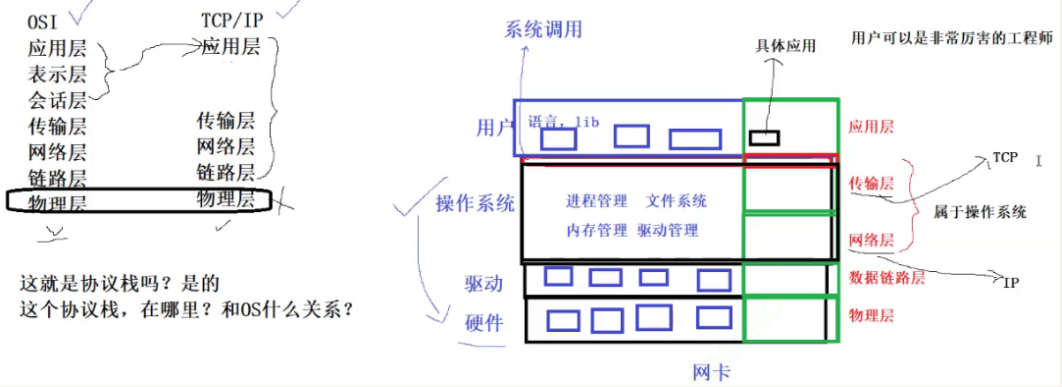
In Linux, everything belongs to files, and network card resources are also divided into files and managed in the form of files.
Both the transport layer and the network layer belong to the operating system layer.
There are many types of operating systems, but there can only be one type of network (because the TCP/IP protocol must be the same).
OSI seven-layer model
- Application layer
An interface between network services and end users. Various application protocols include: HTTP (Hypertext Transfer Protocol) FTP (Text Transfer Protocol) TFTP (Simple File Transfer Protocol) SMTP (Simple Mail Transfer Protocol) SNMP (Simple Network Management Protocol
) DNS (Domain Name System) TELNET (Remote Terminal Protocol)
HTTPS (Hypertext Transfer Security Protocol) POP3 (Post Office Protocol Version 3) DHCP (Dynamic Host Configuration Protocol)
- presentation layer
Data representation, security, compression. (It has been merged into the application layer in the five-layer model) The syntax and semantics of information and their relationships, such as encryption and decryption, conversion and translation, compression and decompression
formats, JPEG, ASCll, EBCDIC, encryption formats, etc. [2] such as LPP (lightweight level representation protocol)
- session layer
Create, manage, and terminate sessions. (It has been merged into the application layer in the five-layer model) The establishment and management of sessions between users on different machines
corresponds to the host process, which refers to the ongoing session security protocols between the local host and the remote host: SSL (Secure Socket Layer Protocol), TLS (Transport Layer Security)
- transport layer
Define the protocol port number for transmitting data, as well as flow control and error checking.
Accept the data from the upper layer, cut the data when necessary, and hand the data to the network layer, and ensure that these data segments effectively reach the peer protocol: TCP UDP. Once the data packet leaves the network card, it enters the network transport layer
.
- Network layer
Carry out logical address addressing to realize path selection between different networks. Control the operation of the subnet, such as logical addressing, packet transmission, and routing protocols: ICMP (Internet Control Message Protocol)
IGMP (Group Management Protocol) IP (IPV4 IPV6) (Internet Protocol) Security protocols, routing protocols (vrrp virtual routing redundancy)
- data link layer
Establish logical connections, perform hardware address addressing, error checking [3] and other functions. (Protocol defined by underlying network)
Combining bits into bytes and then into frames, using MAC address to access media, errors detected but not corrected. Physical addressing, while converting the original bit stream into logical transmission lines
Address Resolution Protocol: ARP, PARP (Reverse Address Translation Protocol)
- physical layer
Establish, maintain, and disconnect physical connections. (The protocol is defined by the underlying network) The original bit stream on the mechanical, electronic, and timing interface communication channel transmits the TCP/IP
hierarchical model structure. The protocol between the application layers calls the transport layer (Transport layer) and the network layer (Network Layer) step by step. And the physical data link layer (Physical Data Link) can realize application communication interconnection at the application layer.
TCP/IP five-layer (or four-layer) model
- Physical layer: Responsible for the transmission method of optical/electrical signals. For example, the common network cables (twisted pairs) of Ethernet, the coaxial cables used by early Ethernet (now mainly used for cable TV), optical fibers, and the current wifi wireless network The use of electromagnetic waves and so on all belong to the concept of the physical layer. The capabilities of the physical layer determine the maximum transmission rate, transmission distance, anti-interference, etc. The hub (Hub) works at the physical layer.
- Data link layer: Responsible for the transmission and identification of data frames between devices. For example, the driver of the network card device, frame synchronization (that is, what signal is detected from the network line is counted as the beginning of a new frame), conflict detection (if a conflict is detected Automatic retransmission), data error checking, etc. There are standards such as Ethernet, Token Ring, and Wireless LAN. The switch (Switch) works at the data link layer.
- Network layer: Responsible for address management and routing. For example, in the IP protocol, a host is identified by its IP address, and the data transmission line (routing) between two hosts is planned through the routing table. Router ) works at the network layer.
- Transport layer: Responsible for data transmission between two hosts. Such as Transmission Control Protocol (TCP), which can ensure that data is sent reliably from the source host to the target host.
- Application layer: Responsible for communication between applications, such as Simple Email Transfer (SMTP), File Transfer Protocol (FTP), and Network Remote Access Protocol (Telnet)
Basic process of network transmission
Transmission process in the same LAN
Transmission processes in different LANs
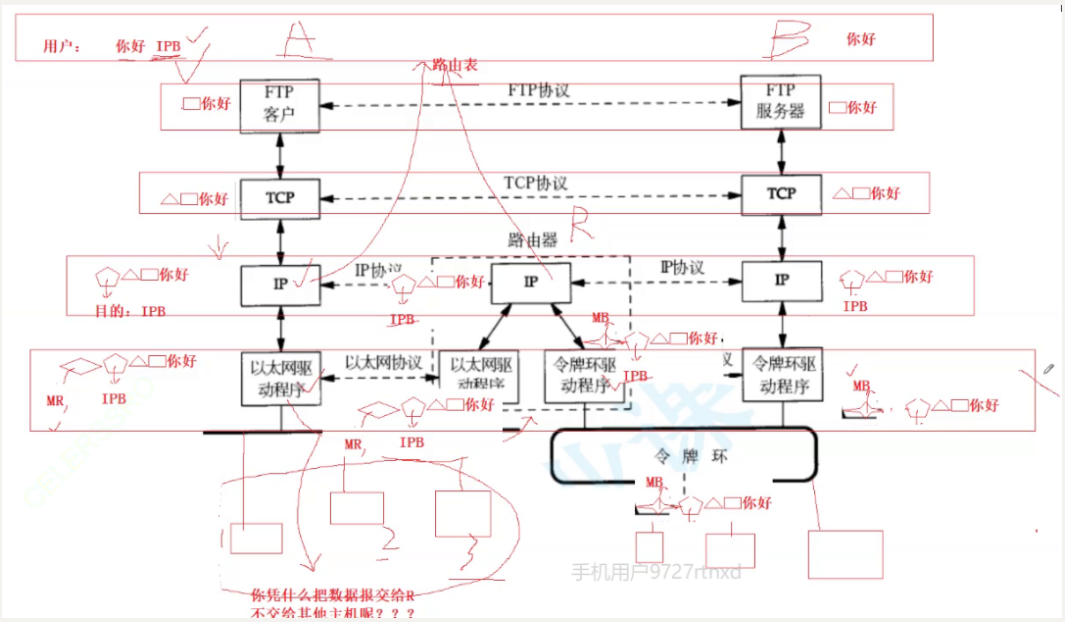
Routers work at the network (IP) layer
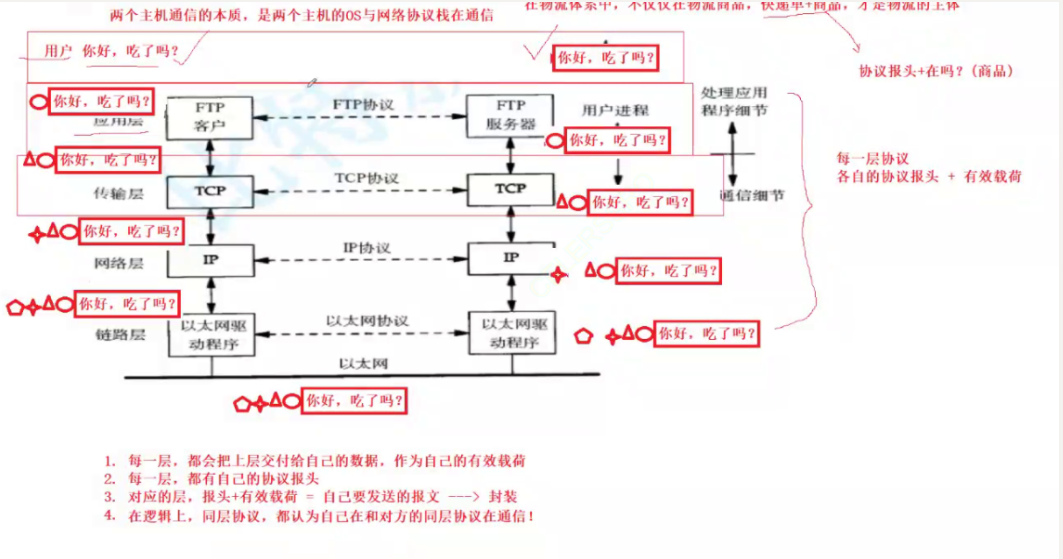
Packet encapsulation and demultiplexing
When application layer data is sent to the network through the protocol stack, each layer of the protocol must add a data header (header), which is called encapsulation.
When the data packet reaches the destination host and is unpacked, the corresponding header will be eliminated for each layer of protocol, which is called demultiplexing.
The difference between MAC address and IP address
During the data transmission process, there are two sets of addresses, namely MAC and IP.
The addresses of the starting point and the ending point (destination host) where the IP address exists.
The MAC address stores the transit address:
During the original distance transmission, we need to pass through many transfer stations (routers). Our MAC address stores the address of the next transfer station we need to go to.
Know IP addresses
There are two versions of the IP protocol, IPv4 and IPv6. In our entire course, whenever the IP protocol is mentioned, unless otherwise specified, it refers to IPv4 by default.
- IP address is the address used to identify different hosts in the network in the IP protocol;
- For IPv4, the IP address is a 4-byte, 32-bit integer;
- We usually also use "dotted decimal" strings to represent IP addresses, such as 192.168.0.1; each number separated by dots represents a byte, the range is 0 - 255, such as 192.192.0.0;
IPv6 is 16 bits, 128 bytes;
Know the MAC address
MAC addresses are used to identify connected nodes in the data link layer;
- The length is 48 bits and 6 bytes. It is generally represented by a hexadecimal number plus a colon (for example: 08:00:27:03:fb:19)
- The network card is determined when it leaves the factory and cannot be modified. The mac address is usually unique (the mac address in the virtual machine is not the real mac address, but
- There may be conflicts; some network cards also support users to configure mac addresses)