Hackers are a mysterious group in the Internet era. They always have the feeling of being a big BOSS that controls the overall situation. Many people are also curious about this group, especially their income . Are hackers who walk on blades really profitable?

First of all, hackers are divided into black hats and white hats, and their incomes will be different.
White hat hackers are "formal hackers" who mainly fix vulnerabilities. They are usually network security practitioners. These people have stable and above-average incomes, ranging from ten thousand to tens of thousands.
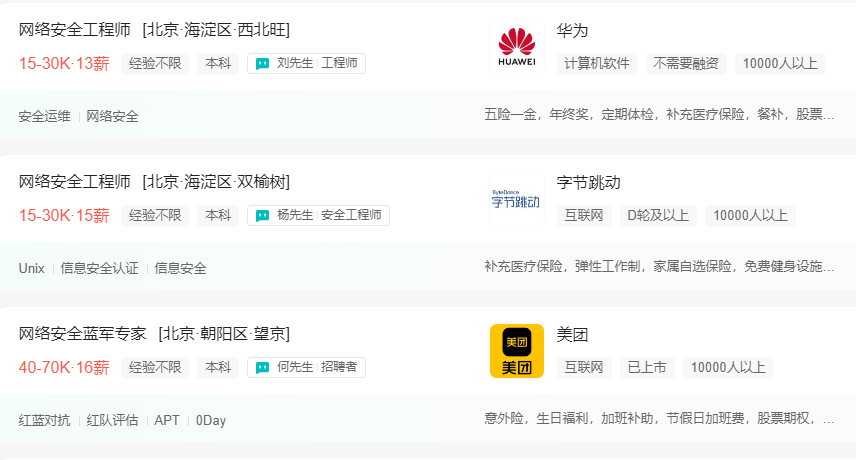
Black hat hackers are similar to the "Demon Cult" and mainly attack vulnerabilities. Amateurs account for about 80% of these people . Their low level means unstable income. Many people can't even get 10,000 yuan .
But there are also a small number of black hats whose annual income can reach more than one million . These top black hats are complete cyber assassins with superior skills and operate on the edge of the law. If the assassination is successful, they will be well rewarded, but if they fail, you will be lucky...
By now you can see that it is not easy to be a simple hacker, so many hackers are now turning to network security. Compared with hackers who stick to the "attack" method, network security requires both offense and defense. After all, this is in line with the development of the times . A skill that is recognized by society and is truly valuable.
So if I want to learn network security, what are the core technologies I need to master ? Regardless of white hat or black hat, learning technology is the last word. In addition, from the perspective of personal horizontal and vertical core competency improvement, how to earn technical dividends faster ?
How to learn hacking & network security
As long as you like my article today, my private network security learning materials will be shared with you for free. Come and see what is available.
1. Learning roadmap
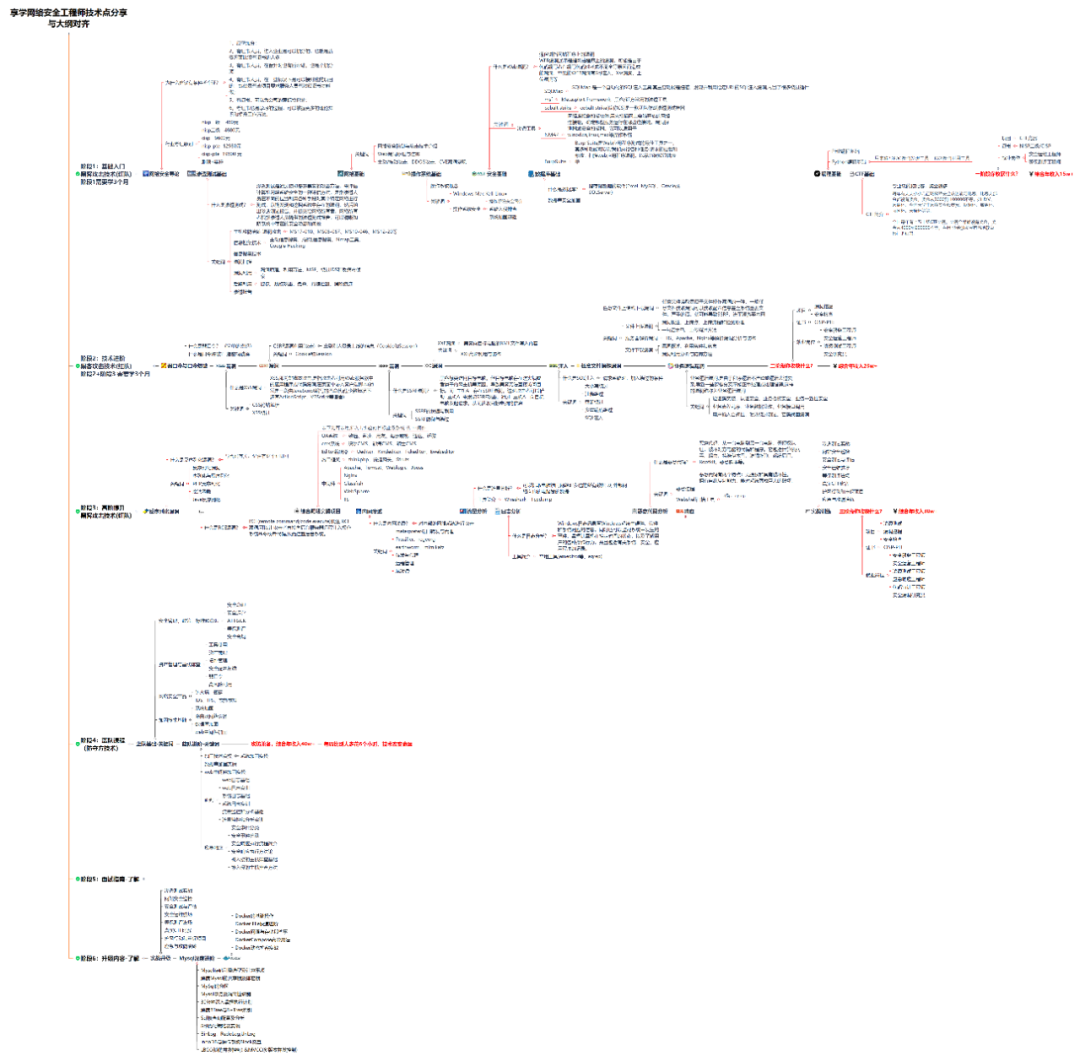
There are a lot of things to learn about attack and defense. I have written down the specific things you need to learn in the road map above. If you can complete them, you will have no problem getting a job or taking on a private job.
2. Video tutorial
Although there are many learning resources on the Internet, they are basically incomplete. This is an Internet security video tutorial I recorded myself. I have accompanying video explanations for every knowledge point in the roadmap above.
The content covers the study of network security laws, network security operations and other security assessments, penetration testing basics, detailed explanations of vulnerabilities, basic computer knowledge, etc. They are all must-know learning contents for getting started with network security.
(They are all packaged into one piece and cannot be expanded one by one. There are more than 300 episodes in total)
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
3. Technical documents and e-books
I also compiled the technical documents myself, including my experience and technical points in participating in large-scale network security operations, CTF, and digging SRC vulnerabilities. There are more than 200 e-books. Due to the sensitivity of the content, I will not display them one by one.
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
4. Toolkit, interview questions and source code
"If you want to do your job well, you must first sharpen your tools." I have summarized dozens of the most popular hacking tools for everyone. The scope of coverage mainly focuses on information collection, Android hacking tools, automation tools, phishing, etc. Interested students should not miss it.
There is also the case source code and corresponding toolkit mentioned in my video, which you can take away if needed.
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
Finally, here are the interview questions about network security that I have compiled over the past few years. If you are looking for a job in network security, they will definitely help you a lot.
These questions are often encountered when interviewing Sangfor, Qi Anxin, Tencent or other major companies. If you have good questions or good insights, please share them.
Reference analysis: Sangfor official website, Qi’anxin official website, Freebuf, csdn, etc.
Content features: Clear organization and graphical representation to make it easier to understand.
Summary of content: Including intranet, operating system, protocol, penetration testing, security service, vulnerability, injection, XSS, CSRF, SSRF, file upload, file download, file inclusion, XXE, logical vulnerability, tools, SQLmap, NMAP, BP, MSF…
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.