I. Introduction:
1. This is a path to persevere. If you are enthusiastic for three minutes, you can give up and move on.
2. Practice more and think more, don't know anything without leaving the tutorial. It is best to complete the technical development independently after reading the tutorial.
3. Sometimes when we search Google or Baidu, we often fail to meet a kind-hearted master who will give you answers without chatting.
4. If you encounter something you really don’t understand, you can put it aside for now and solve it later.
1. Learn the basics:
First, you can learn the basics by studying on your own or taking a cybersecurity course. Understand basic concepts such as computer networks, operating systems, programming languages, and network protocols. Learn network security terms and concepts such as authentication, access control, encryption, and more.
2. Explore cybersecurity tools:
Be familiar with commonly used cybersecurity tools and techniques. For example, learn to use Wireshark to analyze network traffic, use Nmap for vulnerability scanning, use Metasploit for penetration testing, etc. Practice using these tools and learn how they work and how to use them.
3. Understand common attack types:
Learn various common types of network attacks, such as denial of service attacks, malware (viruses, worms, Trojans) attacks, social engineering, etc. Understand the methods and techniques used by attackers, and how to defend and respond to these attacks.
2. Learning route
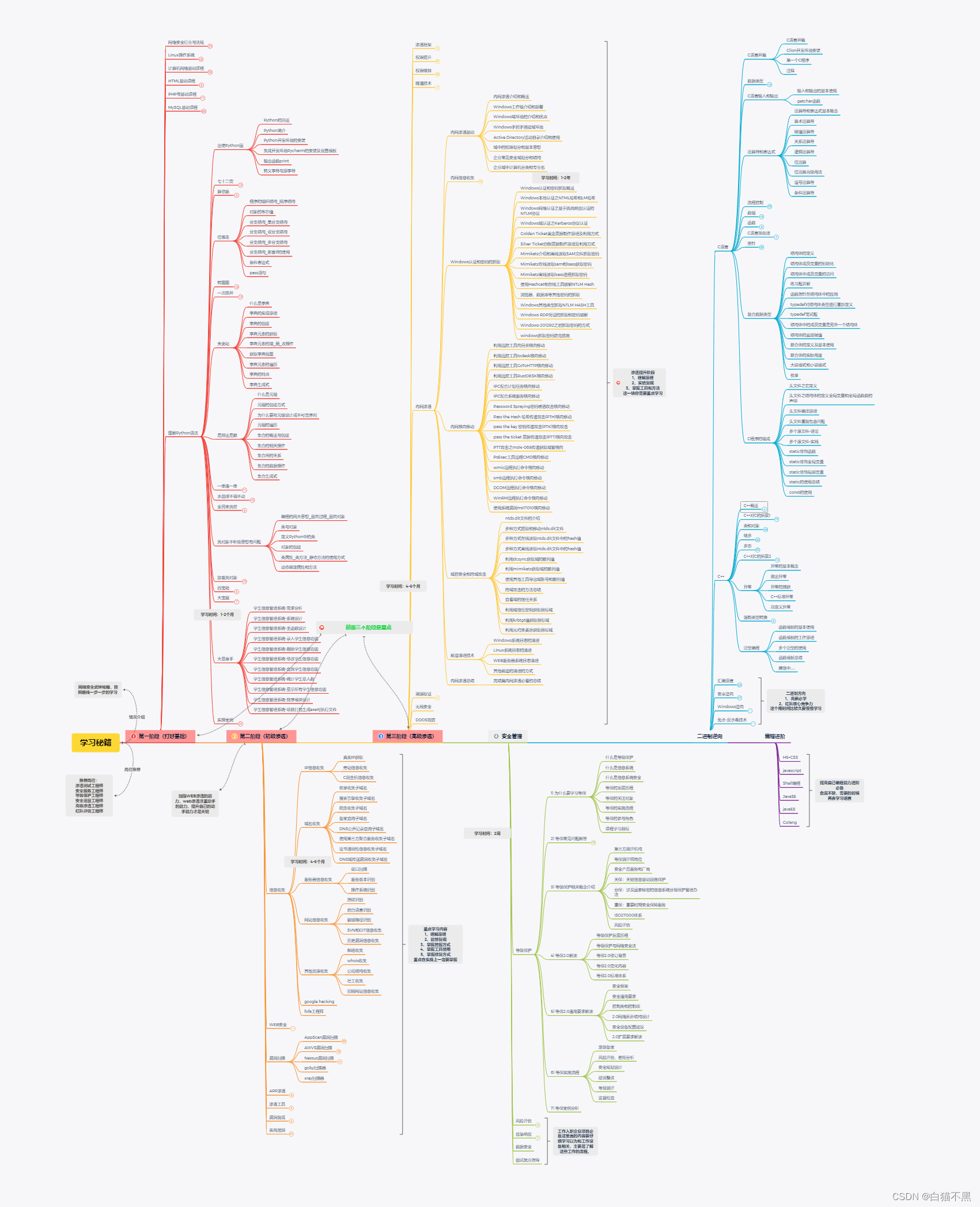
The picture is too big and a bit blurry! ! If you need the pdf version of the learning route, you can follow the blogger to get it automatically! ! !
Phase One: Security Basics
Cybersecurity Industry and RegulationsLinux operating system
computer network
HTML PHP Mysql Python basics to practical mastery
Phase Two: Information Collection
IP information collectionDomain name information collection
Server information collection
Web website information collection
Google hacking
Fofa network security mapping
Phase Three: Web Security
SQL injection vulnerabilityXSS
CSRF vulnerability
File upload vulnerability
File contains vulnerability
SSRF vulnerability
XXE vulnerability
Remote code execution vulnerability
Password brute force cracking and defense
Middleware parsing vulnerability
Deserialization vulnerability
Stage 4: Penetration Tools
MSF
Cobalt strike
Burp suite
Nessus Appscea AWVS
Goby XRay
Sqlmap
Nmap
Kali
The fifth stage: actual digging of holes
Vulnerability mining skillsSrc
Cnvd
Crowd testing project
Recurrence of popular CVE vulnerabilities
Shooting range actual combat
3. Recommendation of study materials
The learning framework has been sorted out, and now we are just missing information and resources. I have compiled the information and resource documents corresponding to all knowledge points here. If you don’t want to look for them one by one, you can refer to these materials!
1. Video tutorial (shareable)
2. Hacking tools & SRC technical documents & PDF books & web security, etc. (can be shared)
If you need learning materials and tutorials, you can follow the blogger to get them automatically! ! ! Anxious friends can get it through the official account at the bottom! ! !
Recommended book list:
Computer operating system:
【1】Coding: the language hidden behind computer software and hardware
【2】In-depth understanding of the operating system
【3】In-depth understanding of Windows operating system
【4】Linux kernel and implementation
Programming development category:
【1】 windows programming
【2】windwos core becomes
【3】Linux Programming
【4】Advanced transformation of unix environment
【5】IOS becomes
【6】The first line of code Android
【7】C programming language design
【8】C primer plus
【9】C and pointers
【10】C Expert Programming
【11】C Traps and Defects
【12】Assembly language (Wang Shuang)
【13】java core technology
【14】java programming ideas
【15】Python core programming
【16】Linuxshell script strategy
【17】Introduction to Algorithms
【18】Compilation principle
【19】Practical combat of compilation and decompilation technology
【20】How to clean your code
【21】Code encyclopedia
【22】Detailed explanation of TCP/IP
【23】Rootkit: Lurkers in the gray area of the system
【24】Hacker attack and defense technology guide
【25】Encryption and decryption
【26】C++ disassembly and reverse analysis technology revealed
【27】Web security testing
【28】White hat talks about web security
【29】Proficient in script hacking
【30】Web front-end hacking technology revealed
【31】Applications for programmers
【32】English Writing Handbook: Elements of Style
Conclusion
The network security industry is like a river and lake, where people of all colors gather. Compared with many well-known and upright people in European and American countries who have a solid foundation (understand encryption, know how to protect, can dig holes, and are good at engineering), our country's talents are more of a heretic (many white hats may be unconvinced), so in the future talent training and In terms of construction, it is necessary to adjust the structure and encourage more people to do "positive" "system construction" that combines "business" with "data" and "automation". Only in this way can we quench the thirst for talents and truly provide comprehensive services to society. The Internet provides security.
