Tool introduction
BurpSuite
BurpSuite is an integrated platform (written in Java) for "attacking" web applications and includes many tools. Burp Suite has designed many interfaces for these tools to speed up the process of attacking applications. All tools share a single request and can handle corresponding HTTP messages, persistence, authentication, proxies, logging, and alerting.
BurpSuite is easy to understand, easy to use, and supports plug-in expansion. It is an essential tool for system security engineers. It is widely used in China and has complete documentation and tutorials. You can find a variety of learning videos on bilibili.
Reference for using bp in combination with web penetration range: https://blog.csdn.net/liaomin416100569/article/details/128200652?spm=1001.2014.3001.5501
Burp green installation-free jdk version
Baidu network disk: Link: https://pan.baidu.com/s/1y7KuzSg_SKmtEP4OTRycwg?pwd=52pj Extraction code: 52pj
Night God Simulator
Yeshen Android emulator, a new generation of artifacts for playing mobile games on computers, Yeshen Android emulator is a PC-side desktop software with a mobile phone-like interface visual design, using kernel technology (based on Android7.0 [3] version kernel pin Run deep development on a computer), with leading running speed and stable performance among similar simulators.
The Yeshen Android emulator is a software that allows mobile applications to run on a computer. It was launched by the Yeshen team in June 2015.
Yeshen simulator is also an essential tool for web packet capture and crawling. With the popularity of WeChat mini-programs, the cost of application decompilation is getting higher and higher. At the same time, programs are beginning to favor the separation of front and back ends. Set up proxy capture through mobile phone simulators. The demand for data access is getting higher and higher.
Compared with the official simulator, the Yeshen simulator is easy to install and has strong scalability.
Official document: https://www.yeshen.com/Other
alternatives to similar simulators:
- MuMu simulator, an simulator produced by NetEase, is more refreshing than Yeshen simulator, https://mumu.163.com/.
- Xiaoyao simulator, produced by Baidu https://www.xyaz.cn/.
- Lightning simulator: https://www.ldmnq.com/
WeChat mini program packet capture
This content is for learning purposes only. The article is referenced from the official website: Configuring an Android device to work with Burp Suite Professional
.
Set up proxy server
Open burpsuite and create a temporary project (this is mainly for demonstration, you can also save it to disk). Open
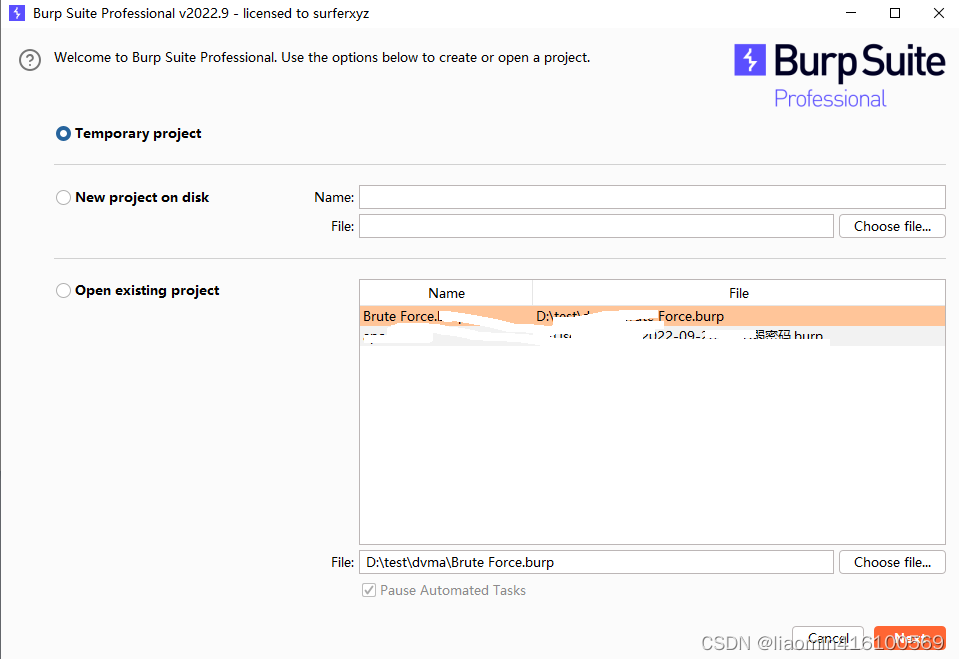
burpsuite, open the tab: proxy-options, add a proxy listener, set the port that needs to be proxy, a four-digit number is enough, bind to Address: Select the IP address of your host's physical network card (open cmd, view ipconfig)
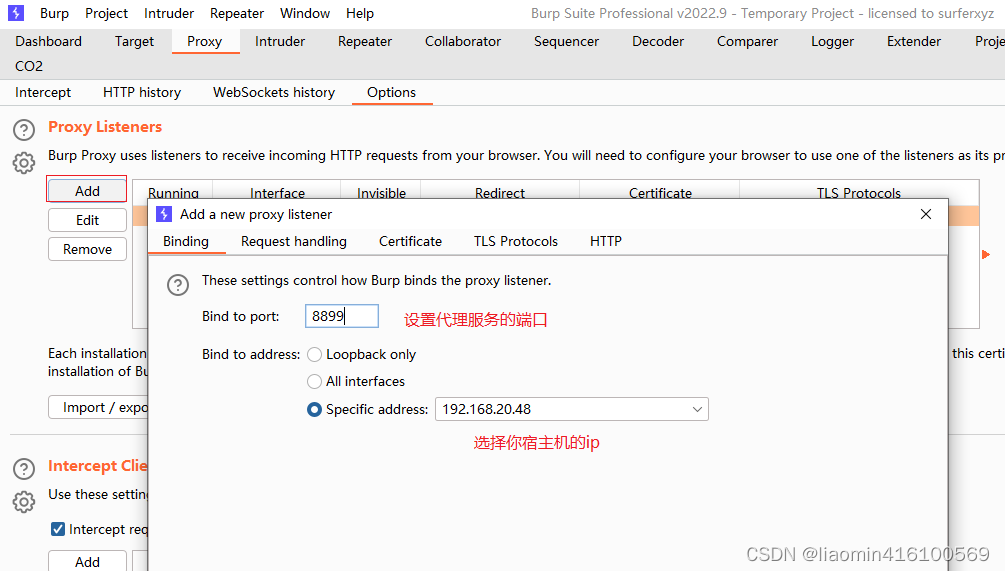
and access: http://192.168.20.48:8899. When this page appears, it indicates success.

Click the CA Certificate on the right to download a local backup of the root certificate.
Emulator settings network proxy
Open the Yeshen simulator and modify the WiFi proxy. The operation of the Yeshen simulator is the same as that on the mobile phone. Just use the mouse as a hand. Swipe down from the upper toolbar. Click the gear on the window that appears to enter the settings and slide to Wireless
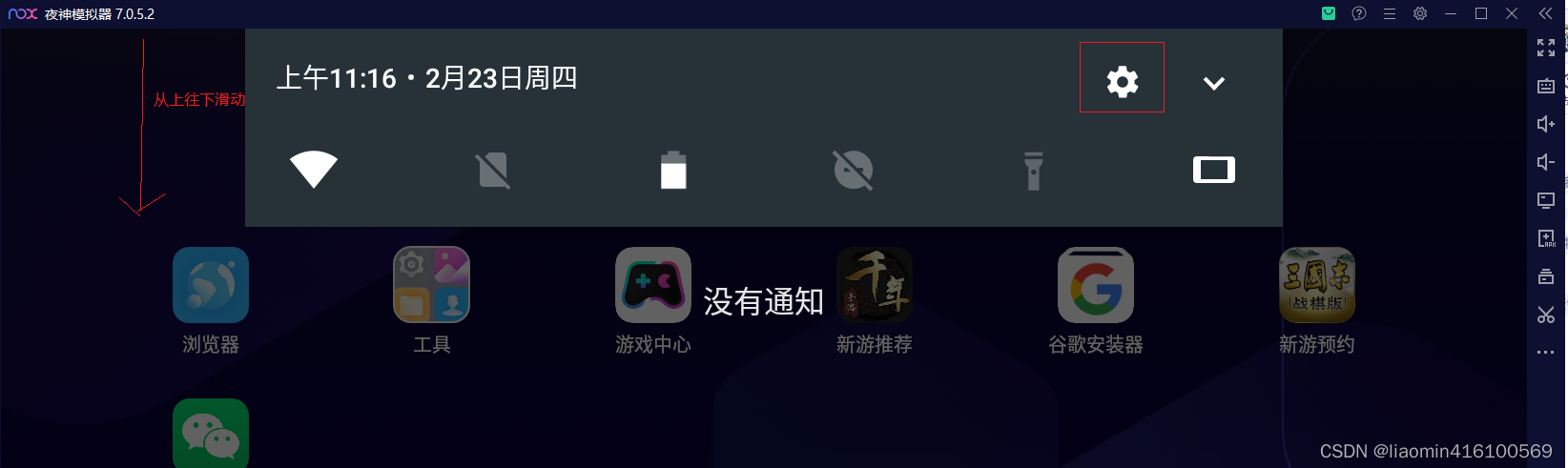
and Network-Wlan
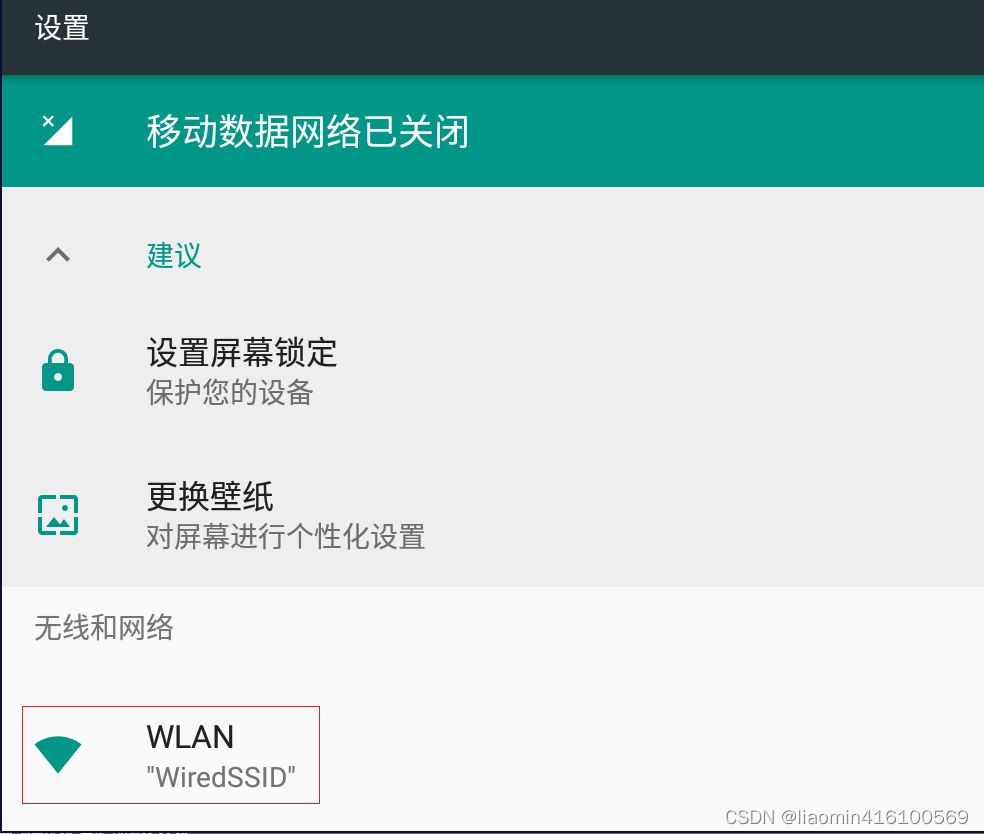
Click Wlan to enter, use the left button of the mouse to hold down WiredSSID to pop up the menu, select Modify Network
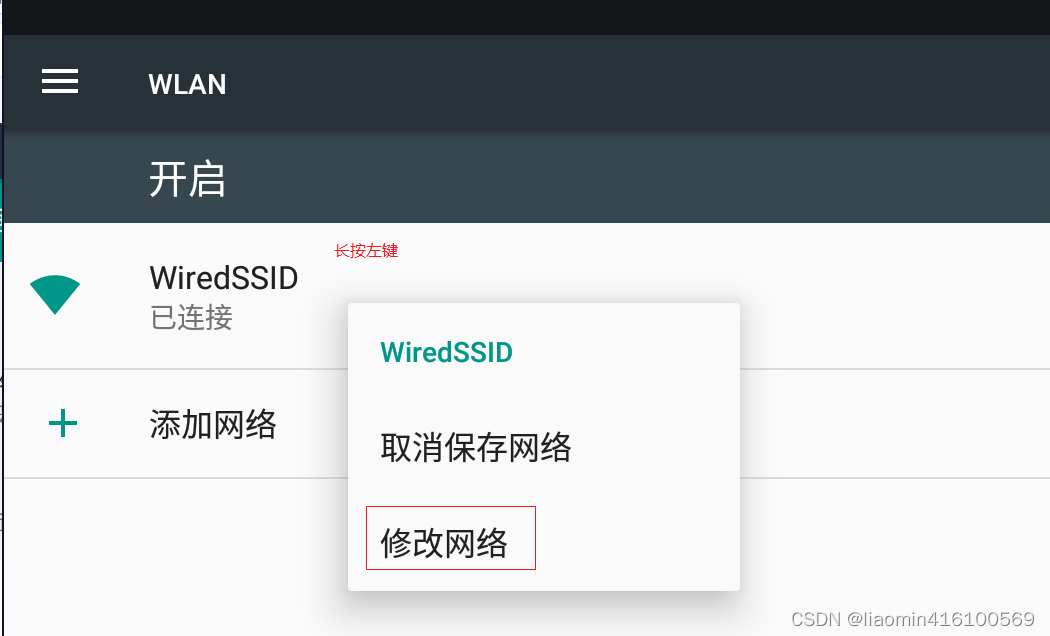
, click Advanced Options, choose manual proxy, and fill in the proxy server ip and port set in the previous bp.
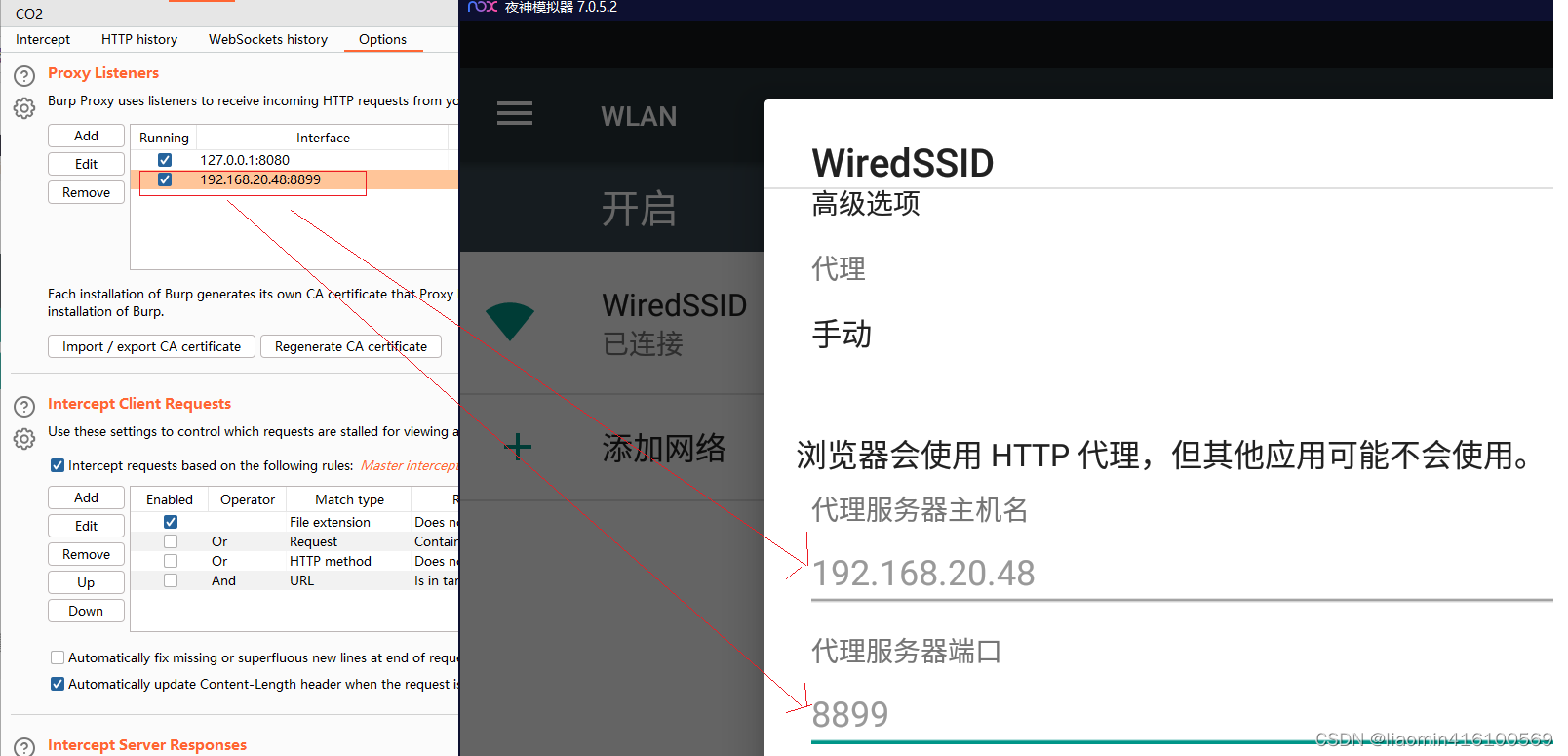
Install proxy root certificate
Visit the proxy server and download the root certificate from CA Certificate in the upper right corner: http://192.168.20.48:8899

Convert the downloaded der into pem format
- You can use the online version,
http://web.chacuo.net/netsslcer2pem - You can also use openssl (https://slproweb.com/products/Win32OpenSSL.html download and install) to convert
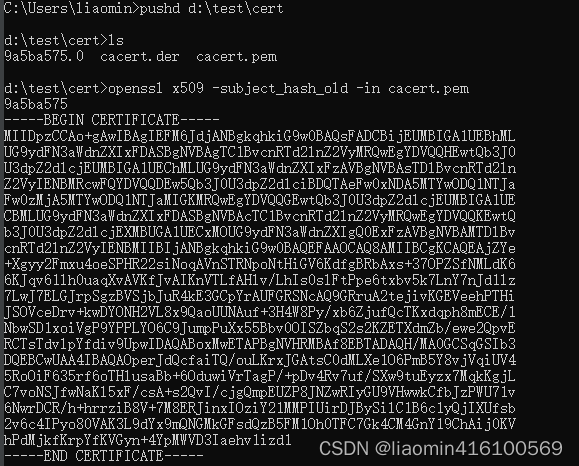
openssl x509 -inform der -in cacert.der -out cacert.pem
Because the name of the certificate stored inside the android emulator must be stored in the hash value of pem.0, you need to know its hash value. The hash value of the
root certificate generated by burpsuite is 9a5ba575, so you can directly rename cacert.pem to: 9a5ba575. 0Of
course, you can also use openssl to confirm
openssl x509 -subject_hash_old -in cacert.pem
Open the emulator and turn on developer mode
Open Settings - About Tablet, find the version number, click the version number five times, the system will prompt a countdown, enter developer mode,
return to the settings menu, and there will be a development option.
Click in to enable USB debugging
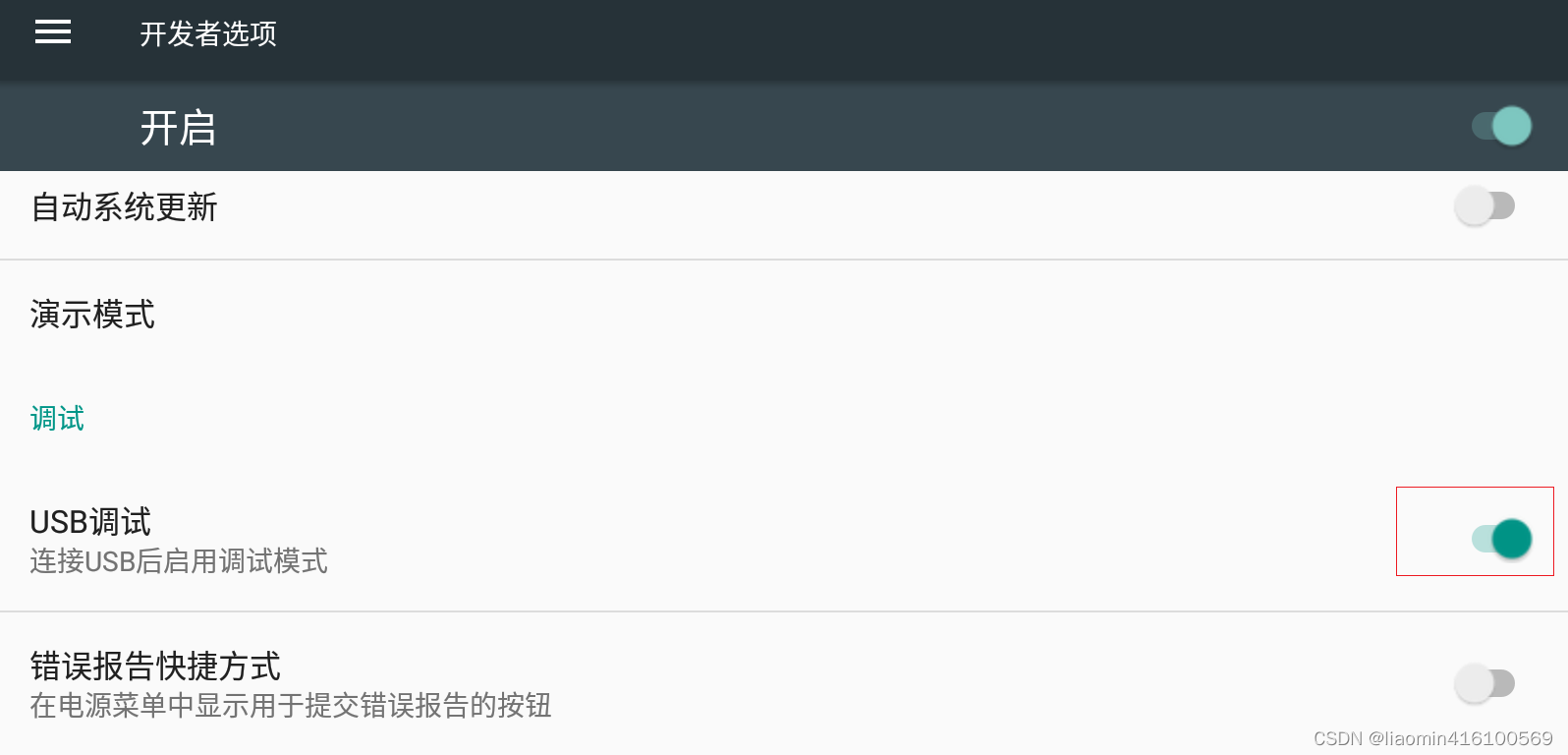
and upload the certificate to the simulator.
Open the file explorer, enter the installation directory of the Yeshen simulator, find the nox_adb.exe or adb.exe program, add its path to the environment variable Path, or cmd directly to Execute the command in the Yeshen directory
to view the simulator device
D:\Program Files\Nox\bin>adb devices
List of devices attached
127.0.0.1:62001 device
Enter nox_adb.exe connect 127.0.0.1:62001 to connect to adb, or adb connect 127.0.0.1:62001
Then execute the following commands in sequence. After checking the system certificate, you will find that the installation is successful.
adb root // 提升到root权限
adb remount // 重新挂载system分区
adb push D:\test\cert\9a5ba575.0 /system/etc/security/cacerts/ //将证书放到系统证书目录
Test packet capture
Open bp, open proxy - Http History
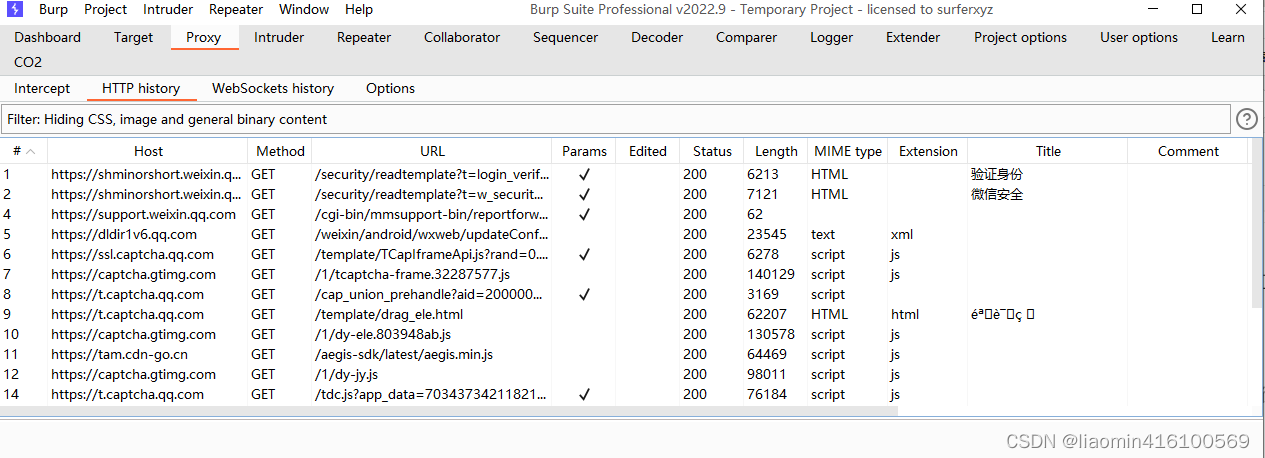
Open WeChat of the Yeshen simulator, and you can capture some interfaces for WeChat login authentication.
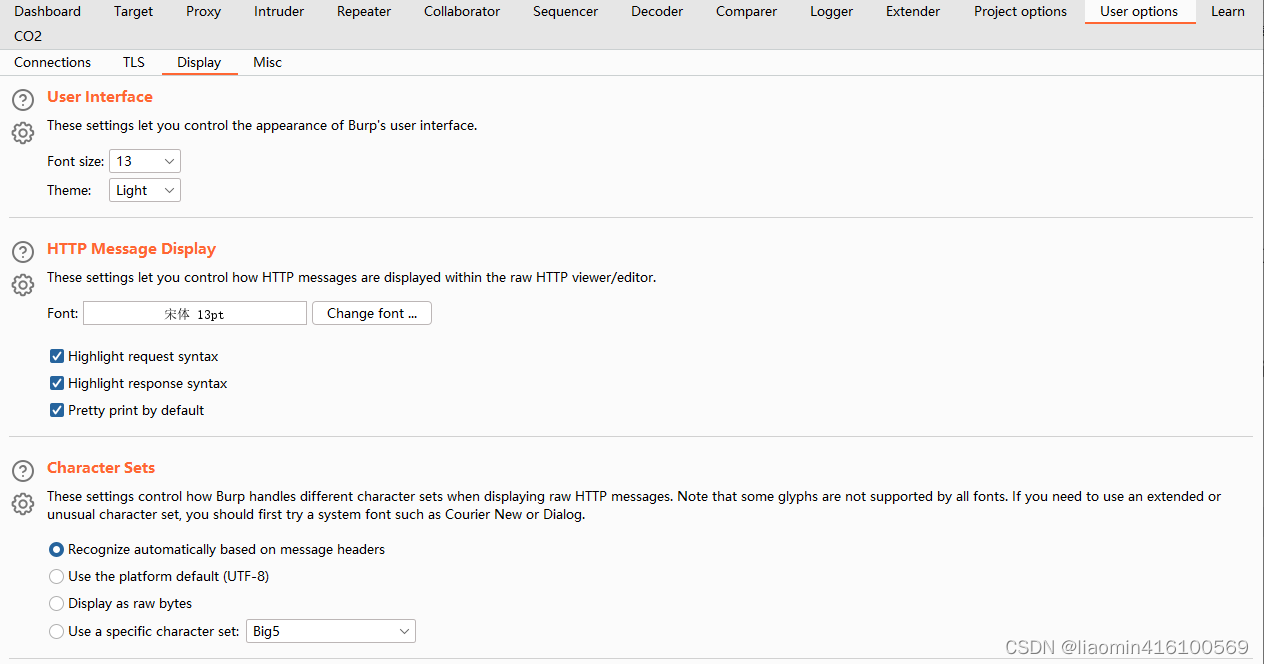
If the Chinese response from burpsuite is garbled, use User Options-Display-Http Message Dispaly and change the font to Song Dynasty to
open the mini program, and you can still capture it. Go and analyze the interface, such as handheld bus, select Shenzhen and select No. 75 bus to capture packets. All sites can be captured.
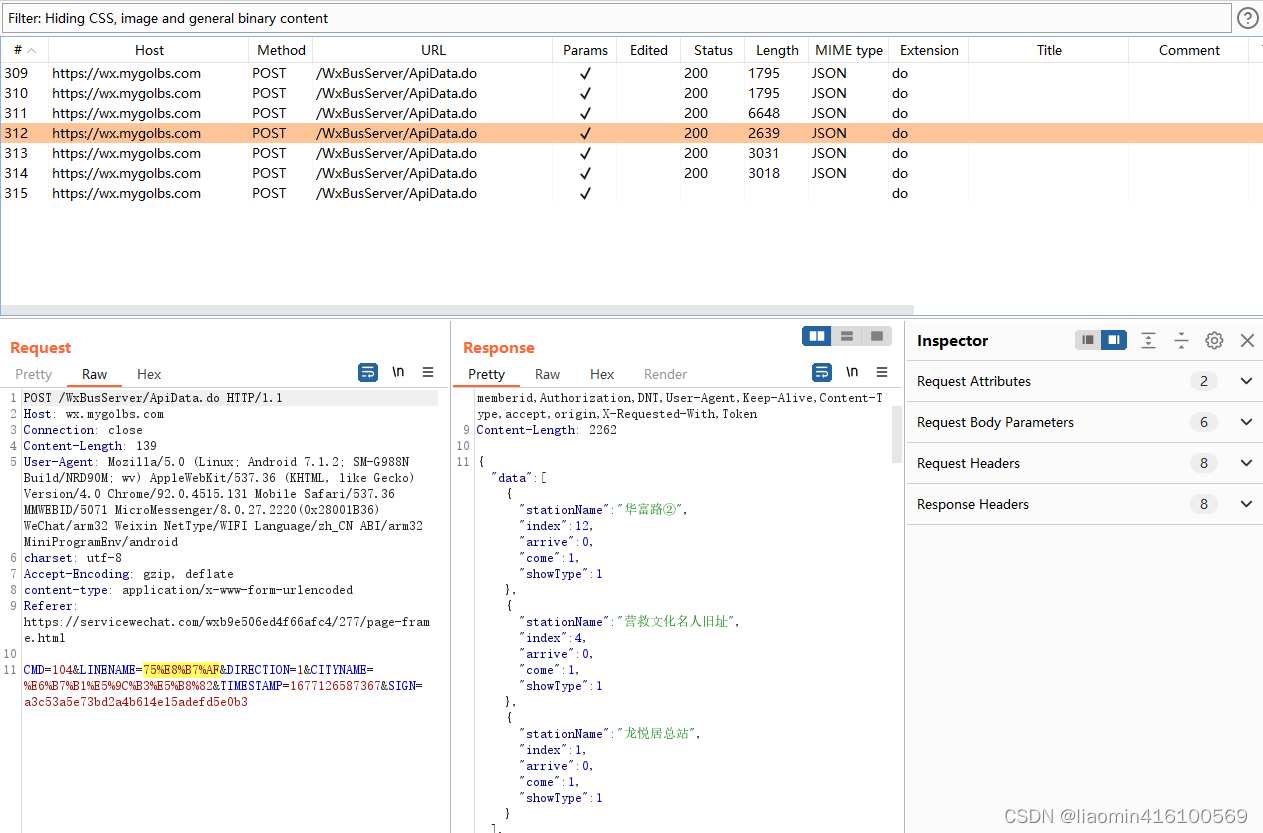
Since this interface has a SIGN signature mechanism, we have other parameters and do not know the logic of his signature. If you need to crawl Other bus routes can only view the signature algorithm by decompiling the applet.