I. Introduction
When connecting to third-party systems, it is often necessary to consider the security of the interface. This article mainly shares the authentication schemes for several common systems when connecting to interfaces.
2. Certification scheme
For example, "asynchronous" scenarios such as connecting to the "logistics system" through "delayed tasks" after placing an order are all interactions between systems, and there is no user operation; therefore, what is required for authentication is not user credentials but It is the system credential, usually including "app_id" and "app_secrect".
2.1. Baic certification
This is a relatively simple authentication method. The client transmits the username and password in plain text (Base64 encoding format) to the server for authentication.
By Header adding the key as Authorization and the value as Basic username: base64 encoding of the password, for example, app_id is and app_secrect are both zlt, and then zlt:zlt the characters are base64 encoded, and the final value is:
Authorization: Basic emx0OnpsdA==
2.1.1. Advantages
Simple and widely supported.
2.1.2. Disadvantages
The security is low and HTTPS needs to be used to ensure the security of information transmission.
-
Although the username and password are Base64 encoded, they can be easily decoded.
-
"Replay attacks" and "man-in-the-middle attacks" cannot be prevented .
2.2. Token authentication
Token authentication is Oauth2.0 in use . The process is as shown in the figure below:客户端模式
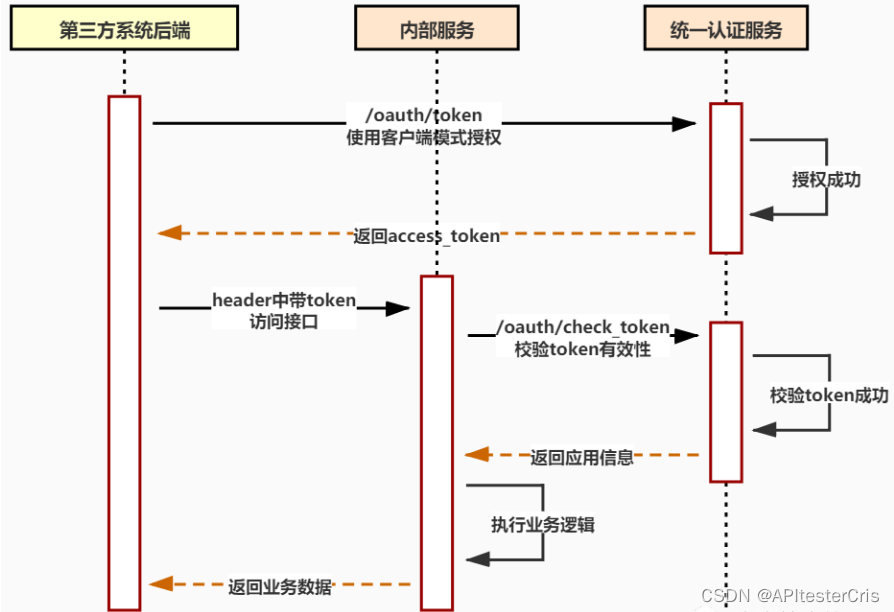
After obtaining the access_token using Basic authentication, use the token to request the business interface.
2.2.1. Advantages
Security has been relatively Baic认证 improved. Temporarily issued ones are used every time the interface is called access_token to 用户名和密码 reduce the chance of credential leakage.
2.2.2. Disadvantages
Baic认证 Security issues remain .
2.3. Dynamic signature
The following parameters need to be transmitted during each interface call:
-
"app_id" application id
-
"time" current timestamp
-
"nonce" random number
-
"sign" signature
The sign signature is generated as follows: use the app_id + time + nonce in the parameters to append app_secrect the string at the end for md5 encryption, and convert all to uppercase.
If you need to implement anti-tampering of parameters, you only need to use all the request parameters of the interface as signature generation parameters.
2.3.1. Advantages
Highest security
-
The server uses the same method to generate signatures for comparison and authentication without transmitting them over the network
app_secrect. -
It can prevent "man-in-the-middle attack" .
-
timeDetermining whether the request time difference is within a reasonable range through parameters can prevent "replay attacks" . -
nonceThe idempotency judgment is performed through parameters.
2.3.2. Disadvantages
Not suitable for front-end applications, the js source code will expose the signature method and app_secrect