Article directory

0. Preface
Background: The project was found to be a Spring Boot vulnerability. Strictly speaking, it should be a vulnerability in the Spring Security component. The security department requested a quick fix. After consulting some information, I sorted it out as follows.
CVE-2021-22096 is a security vulnerability targeting Spring Security. Spring Security is a framework for providing security services in Java applications. It provides a complete set of security functions, including authentication and authorization.
According to the description of the CVE (Common Vulnerabilities and Exposures) database, CVE-2021-22096 mainly affects Spring Security versions 5.5.0 to 5.5.1, and Spring Security versions 5.4.0 to 5.4.7. This vulnerability mainly exists in the way Spring Security handles OAuth 2.0 client registration. If an attacker is able to authenticate as a registered OAuth 2.0 client, they may gain higher privileges.
The development team of Spring Security has fixed this problem in versions 5.5.2 and 5.4.8. It is recommended that all users of affected versions upgrade to new versions as soon as possible to avoid being affected by this vulnerability.
For developers, security is a very important issue, and any small vulnerability may be exploited by attackers. Therefore, developers should always pay attention to relevant security updates and take measures to repair and upgrade as soon as possible. At the same time, developers should also pay attention to security during the development process and try to avoid such vulnerabilities.
1. Reference documents
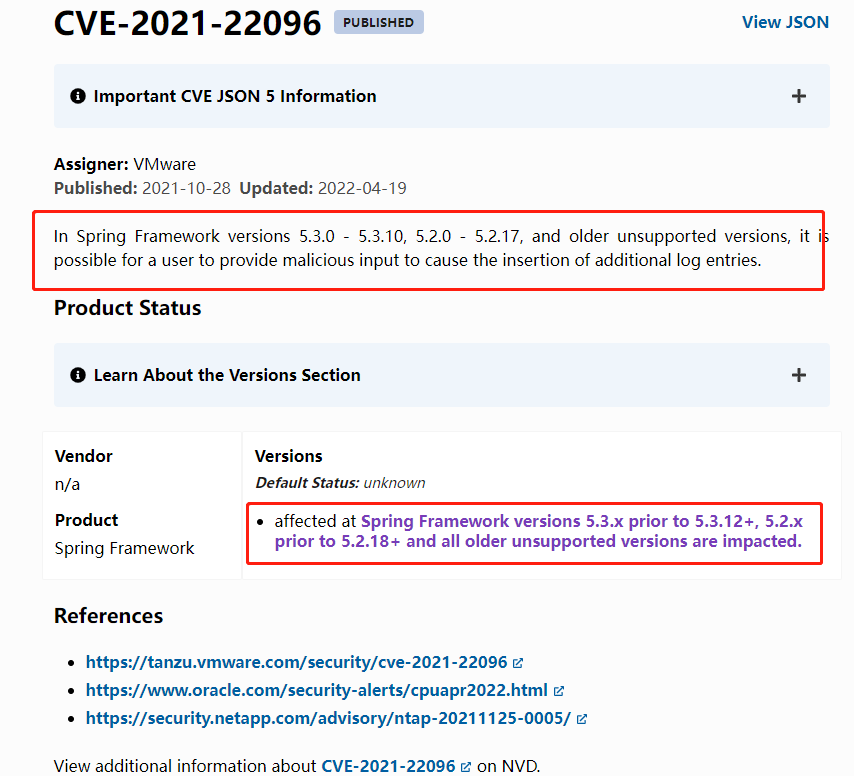
CVE (Common Vulnerabilities and Exposures, public vulnerabilities and exposures) records https://www.cve.org/CVERecord?id=CVE-2021-22096
CVE is a public global vulnerability database, whenever a new security vulnerability is discovered , CVE will assign a unique ID to it for easy tracking and reference. CVEs are usually in the format "CVE-Year-Number".
According to the description of CVE-2021-22096, this is a vulnerability affecting VMware vCenter Server. Submitted by VMware.
The vulnerability is a Server-Side Request Forgery (SSRF) vulnerability that would allow an attacker to send a forged HTTP or HTTPS request to an internal network accessible to the victim's server. This could lead to unauthorized information disclosure or the victim's server being used to attack the internal network.
The CVSS (Common Vulnerability Scoring System) base score for this vulnerability is 8.6/10, indicating that this is a fairly serious vulnerability. CVSS is a system developed to quantify (measure, score) the severity and urgency of vulnerabilities.
2. Basic introduction
CVE-2021-22096 is a security vulnerability affecting Spring Security. Spring Security is a widely used Java security framework that provides many powerful security features such as authentication and authorization.
Vulnerability scope:
This vulnerability primarily affects Spring Security 5.5.0versions 5.5.1, as well Spring Security 5.4.0到5.4.7版本.
Official description:
The vulnerability exists in the way Spring Security handles OAuth 2.0 client registration. If an attacker is able to authenticate as a registered OAuth 2.0 client, they may gain higher privileges.
Fix version:
The Spring Security development team has fixed this issue in versions 5.5.2 and 5.4.8.
Exploitation steps:
The specific exploit steps may involve technical details. In general, attackers need to first find a registered OAuth 2.0 client and then authenticate as that client to elevate their privileges.
Repair method:
Users of Spring Security should upgrade to the latest version as soon as possible. For users using versions 5.5.0 to 5.5.1, they should upgrade to version 5.5.2. For users using versions 5.4.0 to 5.4.7, they should upgrade to version 5.4.8.
Generally speaking, the best way to fix this type of vulnerability is to upgrade to the latest version. If an upgrade is not possible for some reason, users can also try to mitigate the vulnerability by disabling or restricting the affected functionality. In this case, users may consider restricting or increasing OAuth 2.0 client registration security measures.
CVE-2021-22096 is a security vulnerability affecting Spring Security. The existence of this vulnerability allows an attacker to authenticate as a registered OAuth 2.0 client, which may obtain higher privileges. This is mainly due to Spring Security not properly validating permissions when handling OAuth 2.0 client registration.
Such vulnerabilities are usually due to insufficient understanding or negligence of security requirements during the design and implementation stages, resulting in insufficient security checks when processing client registration.
3. Solutions
CVE-2021-22096 is a security vulnerability affecting Spring Security. In response to this problem, the official has released a solution:
- Upgrade Fix: Users of Spring Security should upgrade to the latest version as soon as possible. For users using versions 5.5.0 to 5.5.1, they should upgrade to version 5.5.2. For users using versions 5.4.0 to 5.4.7, they should upgrade to version 5.4.8.
2.temporary solutionRestrict OAuth 2.0 client registration: 如果由于某些原因无法立即升级,用户可以考虑限制或增加OAuth 2.0客户端注册的安全措施,以此来减轻漏洞的影响.
- Only allow trusted apps to register as OAuth 2.0 clients.
- Add a human review step to the client registration process to ensure that only legitimate and company policy-compliant apps are registered.
- Limit the number of OAuth 2.0 clients that each user or IP address can register within a certain period of time.
- Add a blacklist or whitelist system, only allow applications in the whitelist to register, or prohibit applications in the blacklist from registering.This is the most efficient solution
- Audit logs: For systems that may have been affected by this vulnerability, administrators can review their audit logs to determine if any unauthorized users attempted to exploit this vulnerability.
Upgrading to the latest version is the most convenient and most effective solution to avoid the impact of vulnerabilities. If an immediate upgrade is not possible, other necessary security measures should also be taken to reduce the possible impact of this vulnerability.