Environment introduction
CPU: 8 cores, memory: 16GB, hard disk: 100GB
Operating system version: CentOS-7-x86_64-DVD-2003
Platform version: Honghu 2.7.0
Install components
Installation environment support confirmation
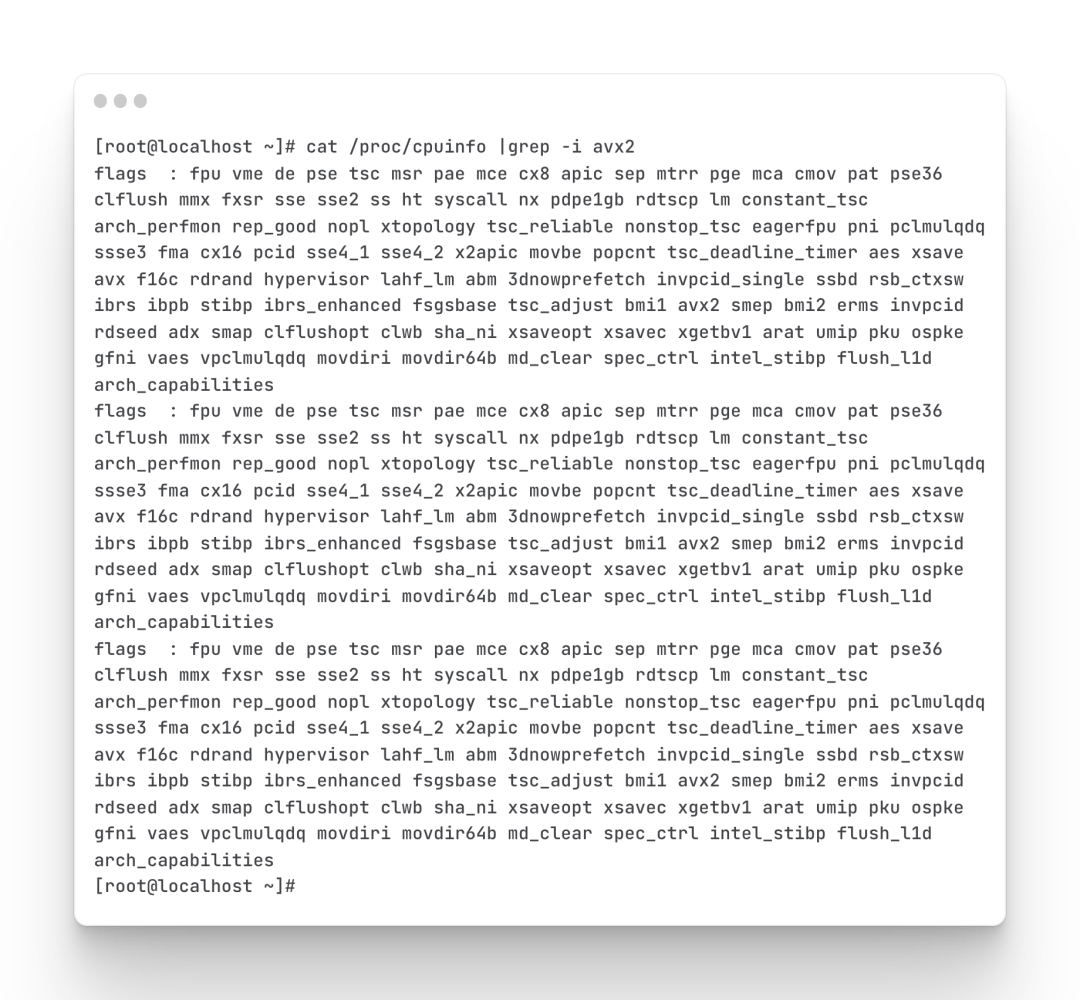
Honghu Computing Engine uses the AVX2 advanced instruction set to accelerate vector calculations. Therefore, Honghu needs to run on a CPU that supports the AVX2 instruction set. Use the following command to check whether the environment CPU to be installed supports AVX2 instruction set.
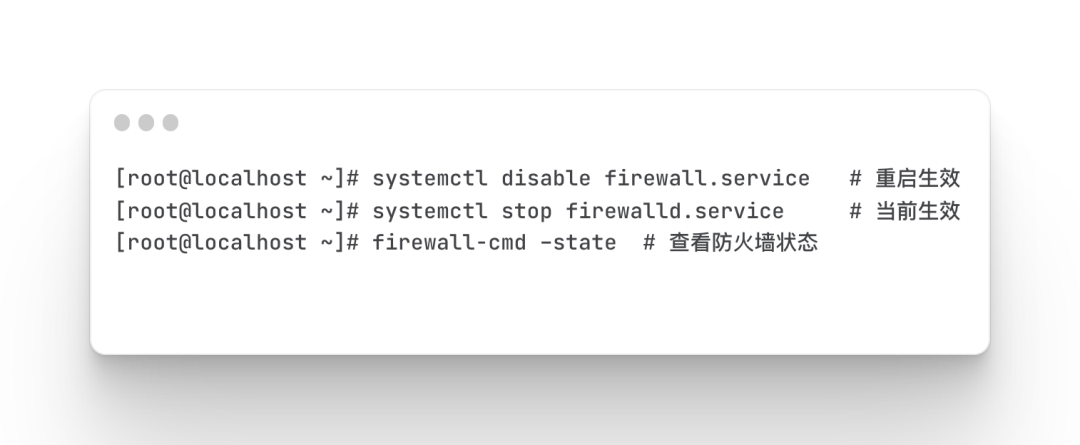
turn off firewall
Enter two commands [systemctl disable firewalld.service] and [systemctl stop firewalld.service] in the console to close the firewall, and use [firewall-cmd --state] to view the running status of the firewall.
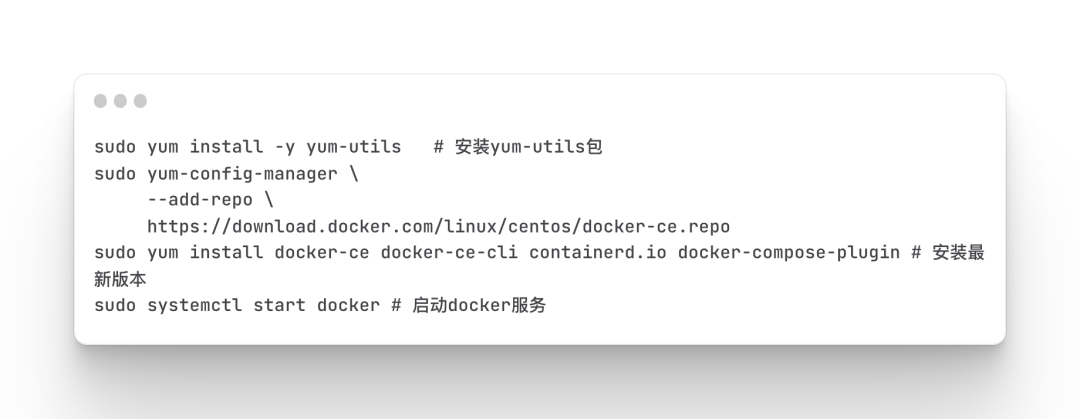
install docker
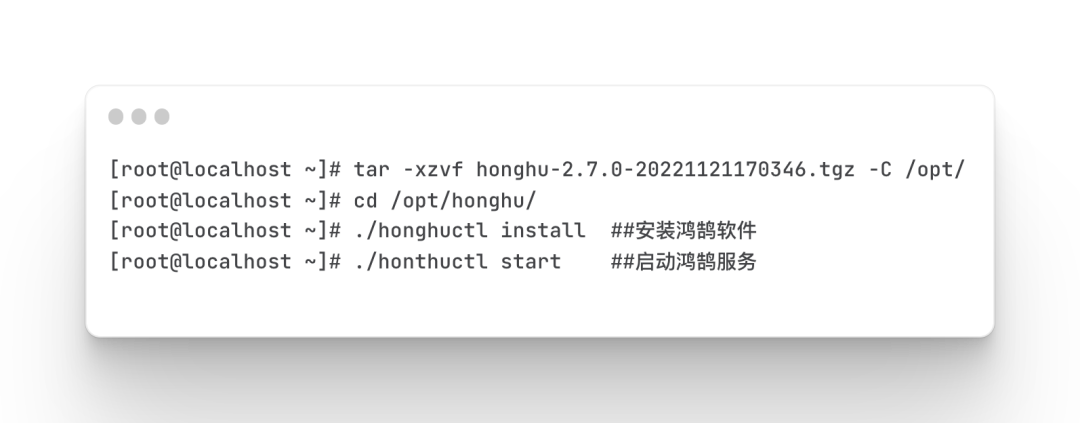
Install Honghu platform
Upload the downloaded honghu-2.7.0*.tgz file and license file to the centos server, and decompress them to the /opt directory.
It can be uploaded by building an ftp site or an http site
Login Honghu platform
https://IP:18080 (default port 18080, default account: admin, password: changeme)
log collection
Data import method
Honghu Data Platform provides a variety of out-of-the-box data import methods, from commonly used uploading files through WEB pages to support for various data collection agents. Users can flexibly choose appropriate data import methods and modules according to different scene conditions.
Data import is generally divided into two types: push (Push) and pull (Pull):
· The push method means that the external system actively sends data to the platform by calling the API interface of Honghu Data Platform.
· The method of pulling is to use a specific data collection program, set collection tasks in the program, and import the data to be collected into the Yanhuang data platform for storage.
1. For the push data access method, Honghu Data Platform can support
●Upload files
●Import data through API
●Import data through API
●Import data by search statement
●Import data from external data sources
2. For the pull data import method, users can flexibly choose the data collection Agent they are familiar with, and by configuring the collection task of the Agent, the data collection and preprocessing on the target machine will be sent to the Honghu Data Platform.
●Import data through Vector
create dataset
Create Dataset: Name: syslog
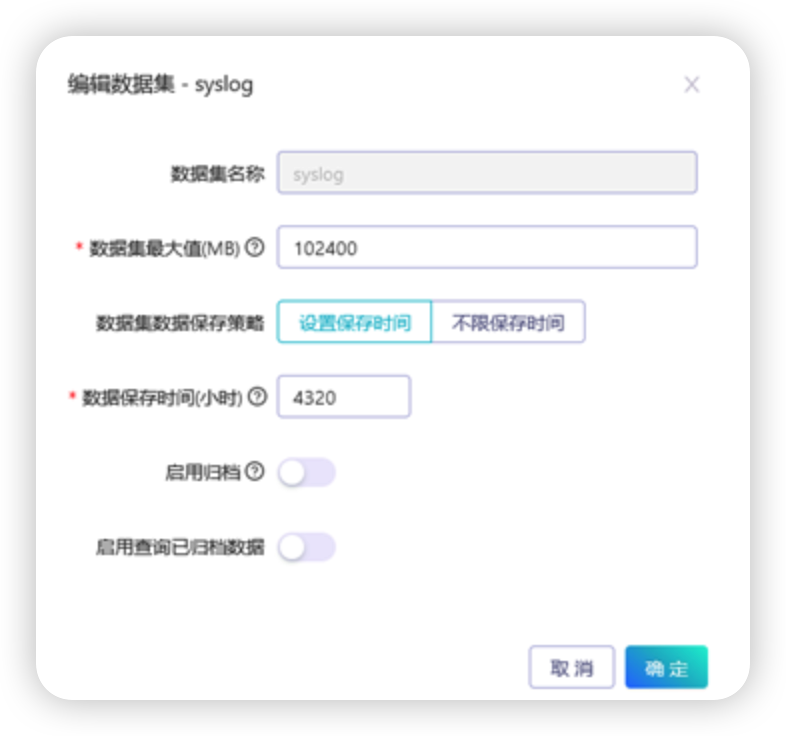
Configure vector, select the data set scope "syslog"
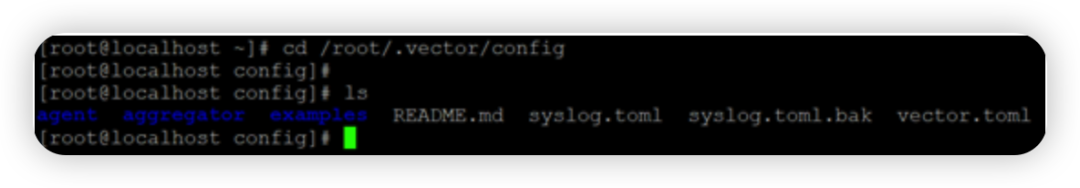
Modify the vector configuration file
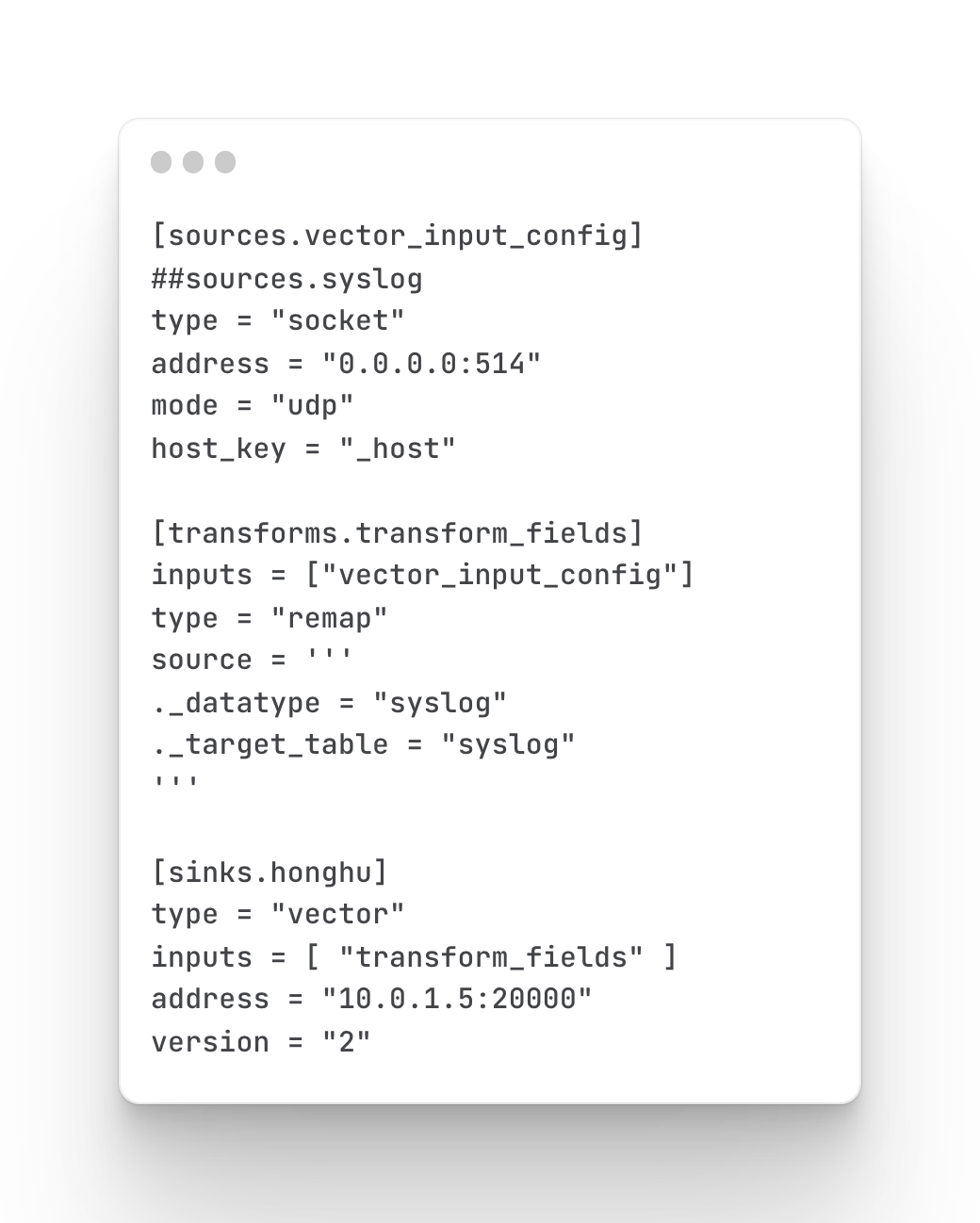
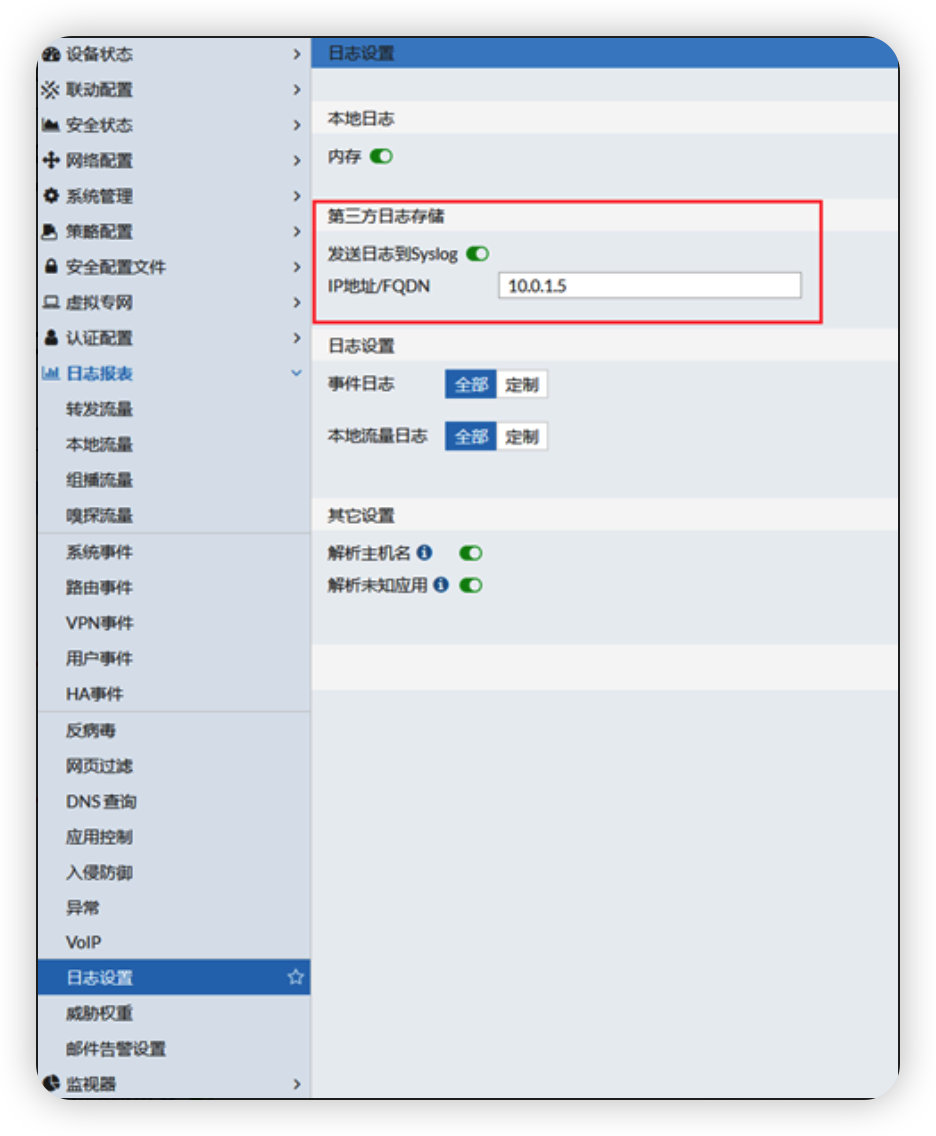
FortiGate firewall log collection
Firewall log setting: select a third-party log storage, and send the log to the remote Honghu platform through syslog
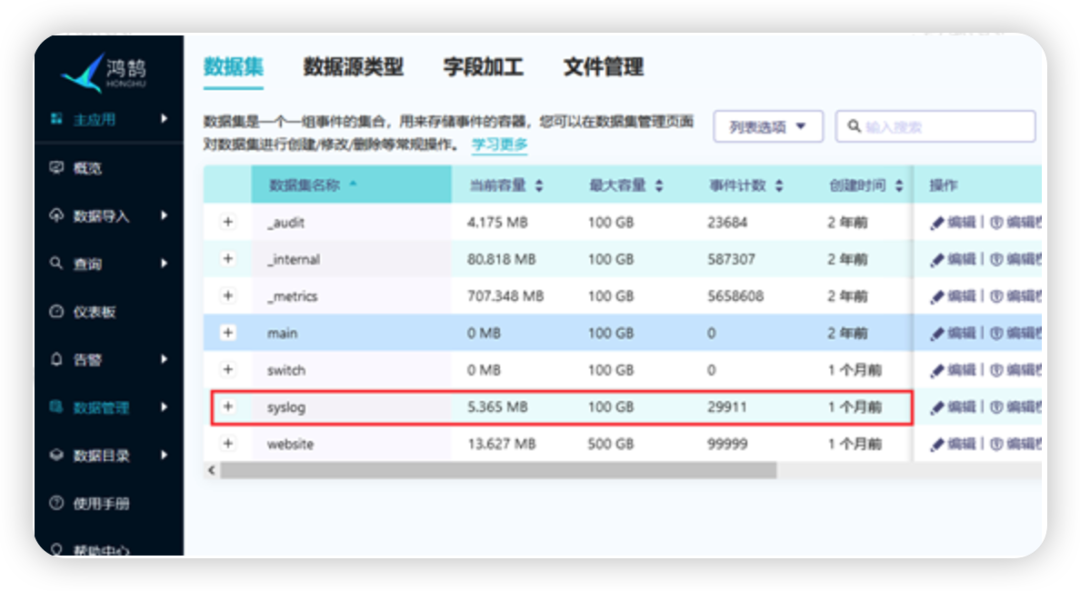
View log collection status:
After a period of log collection, you can see that the logs are collected
FortiGate firewall log audit report
Firewall overview diagram display
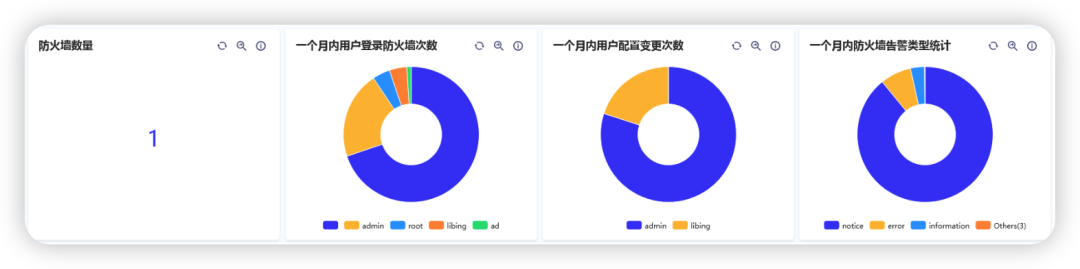
Count and define the number of firewalls
query command
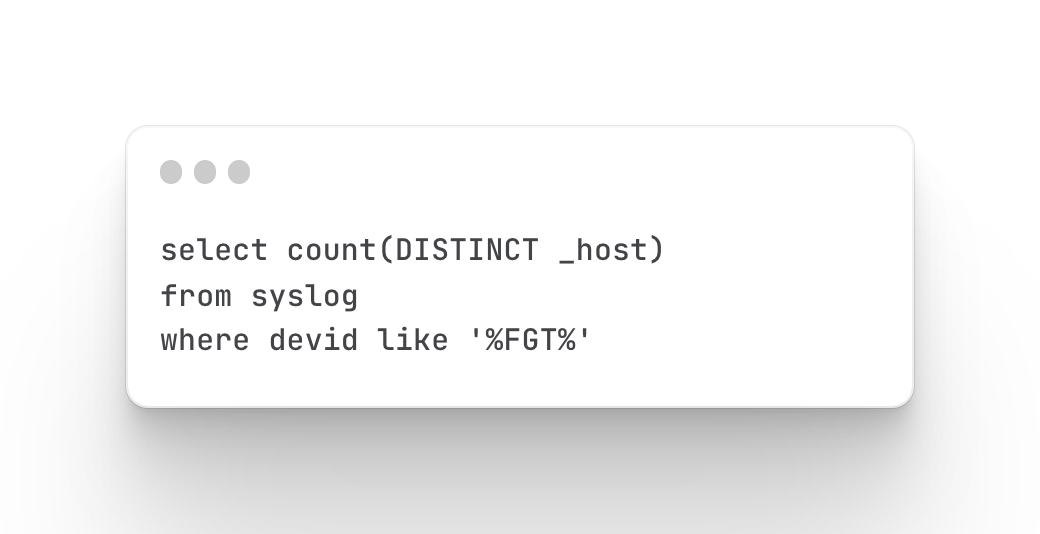
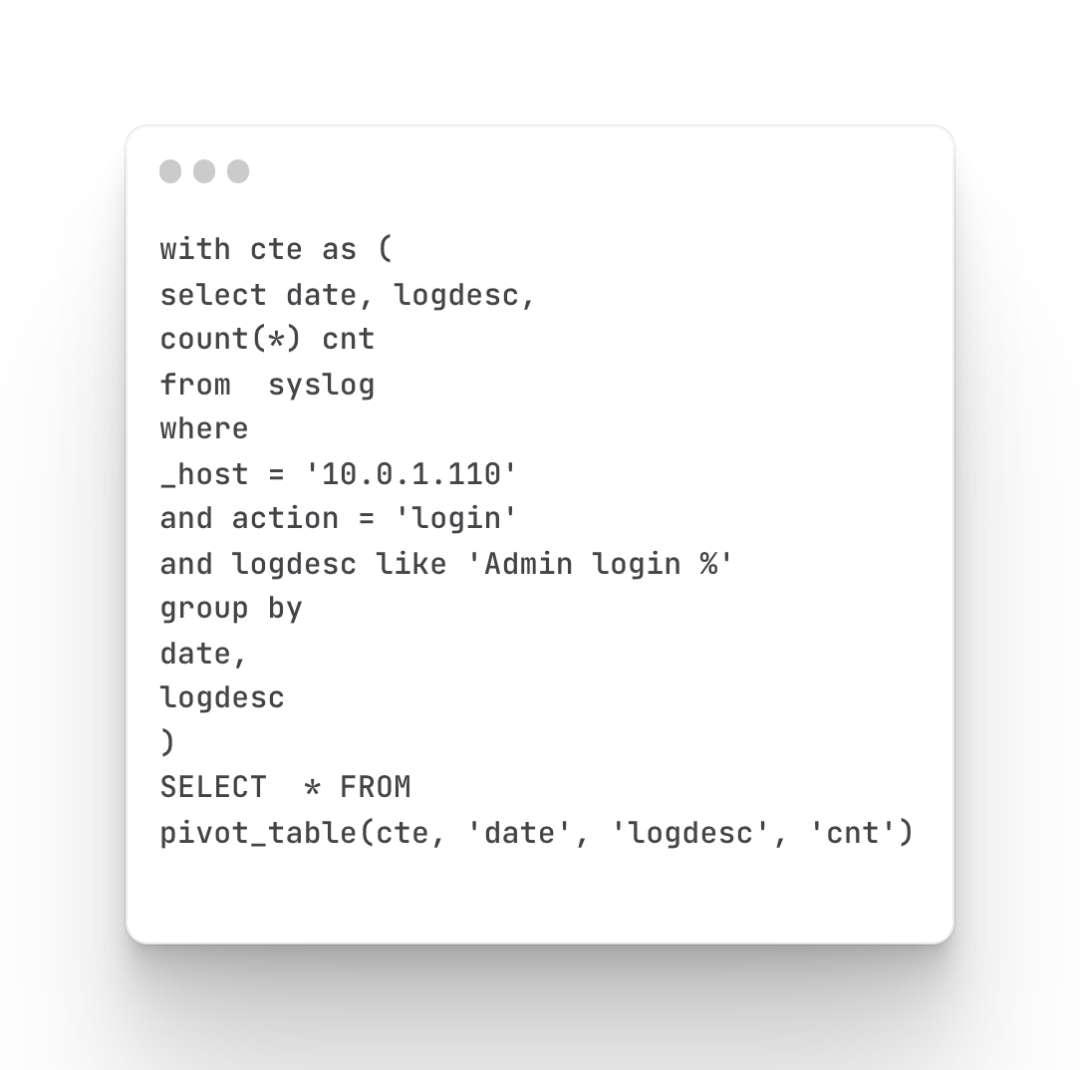
Count and define firewall user login times
Mainly query the login status of the firewall, which users have logged in, and how many times they have logged in
query command
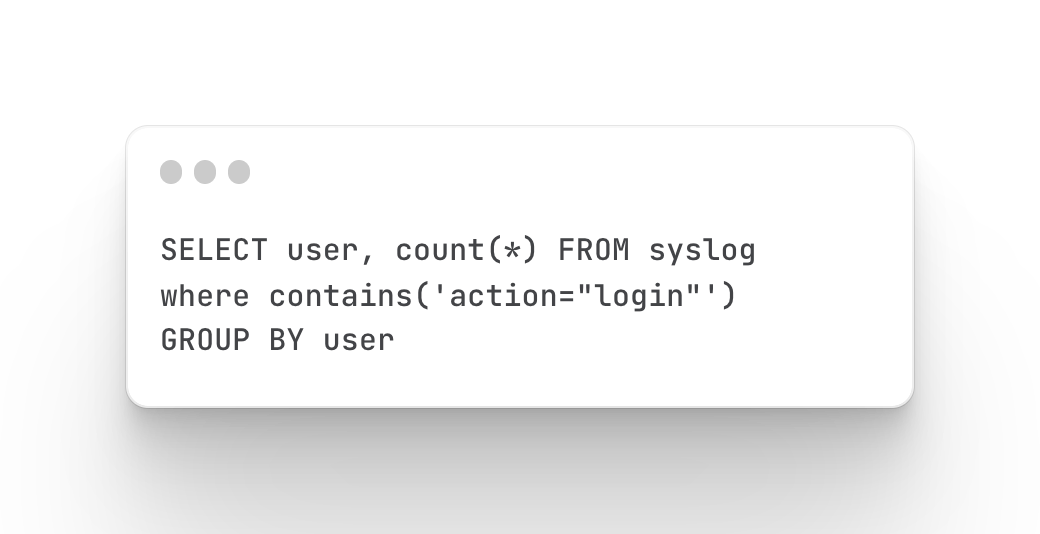
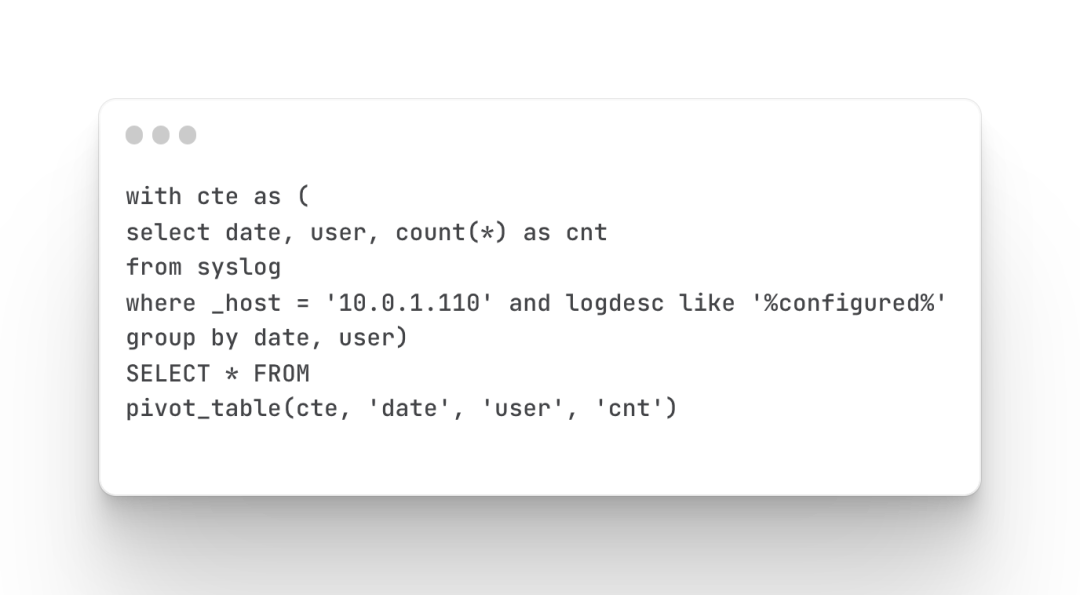
Count and define the number of firewall configuration changes
Mainly query the status of firewall configuration changes, which users have made changes, and the number of changes
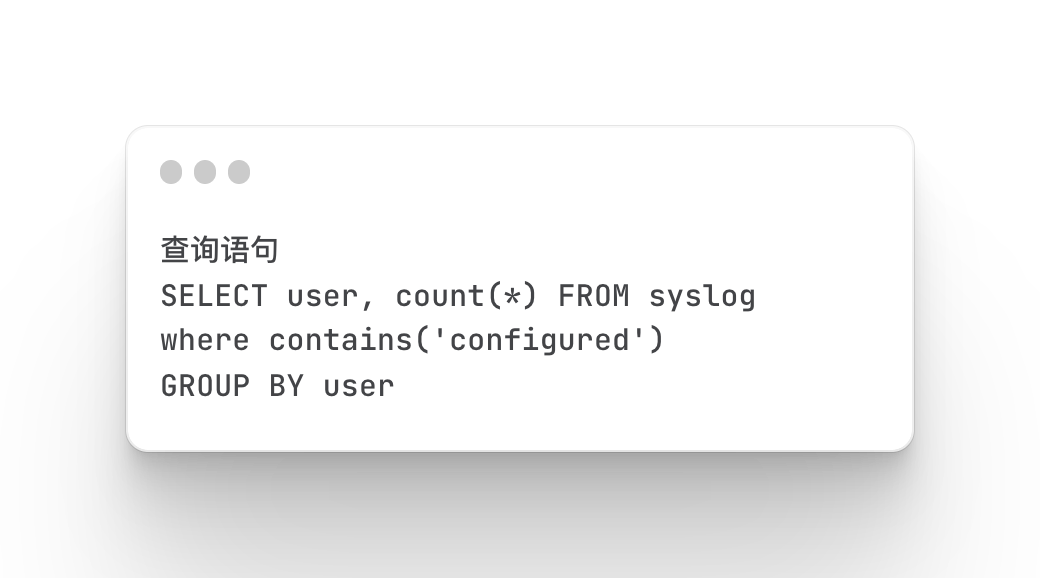
Collect statistics and define firewall alarm types
Mainly query the status of firewall alarms, which type of alarms, and the number of statistics
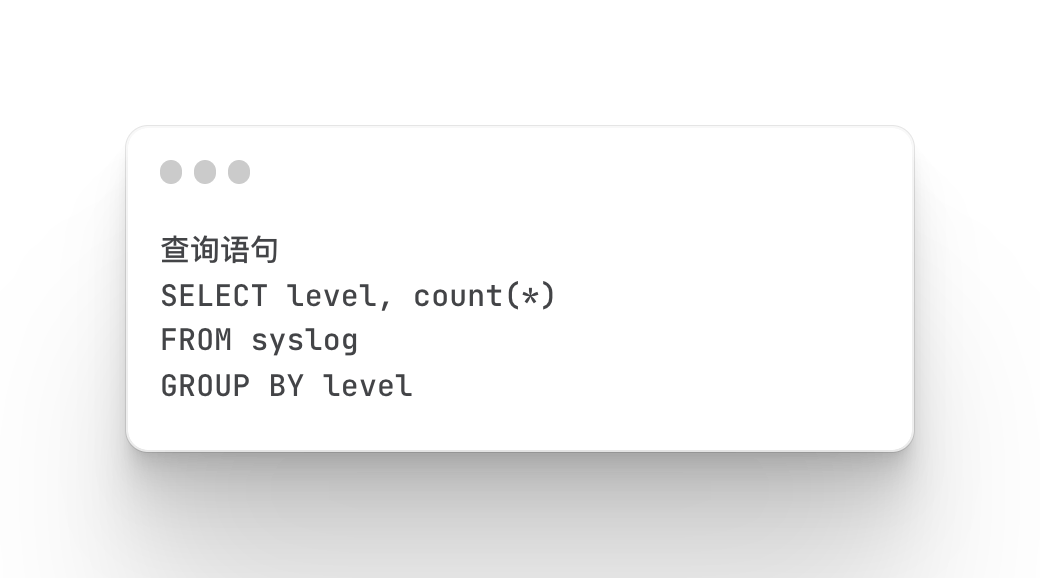
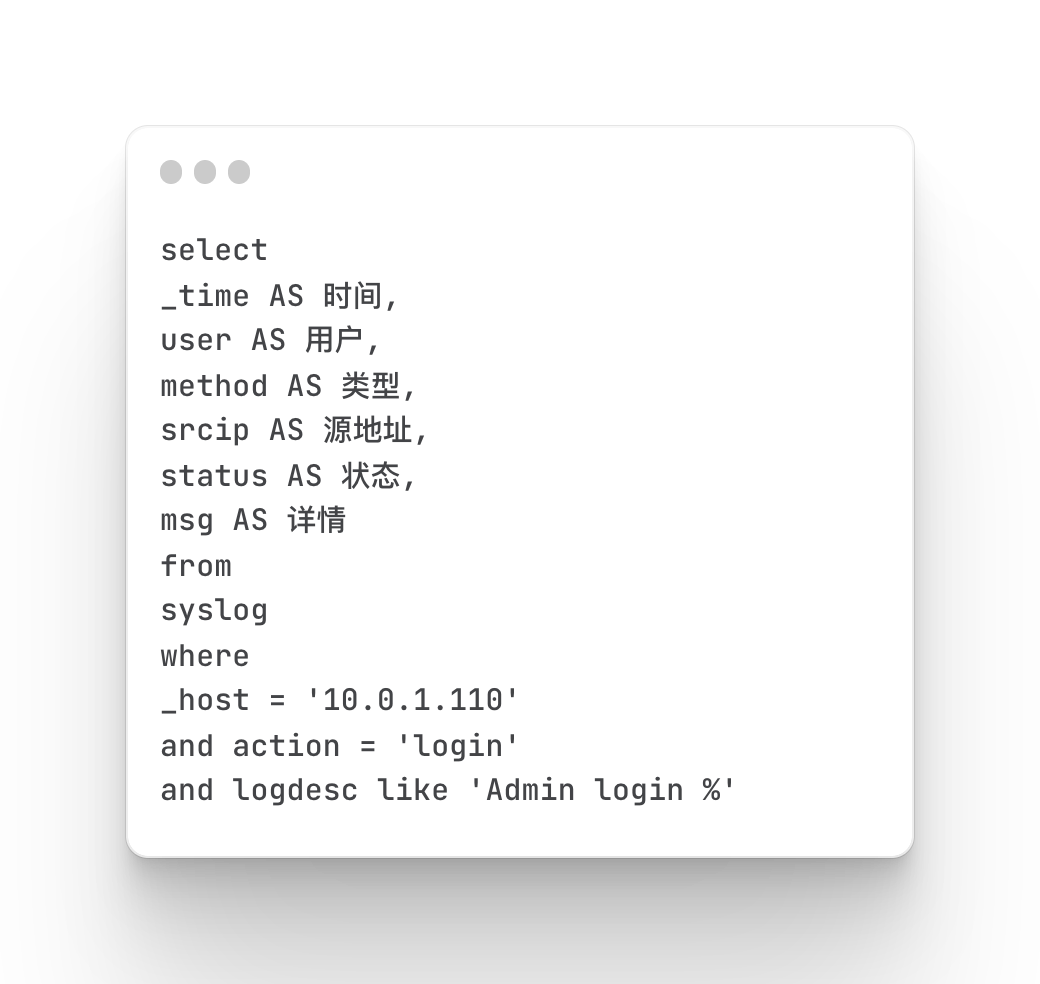
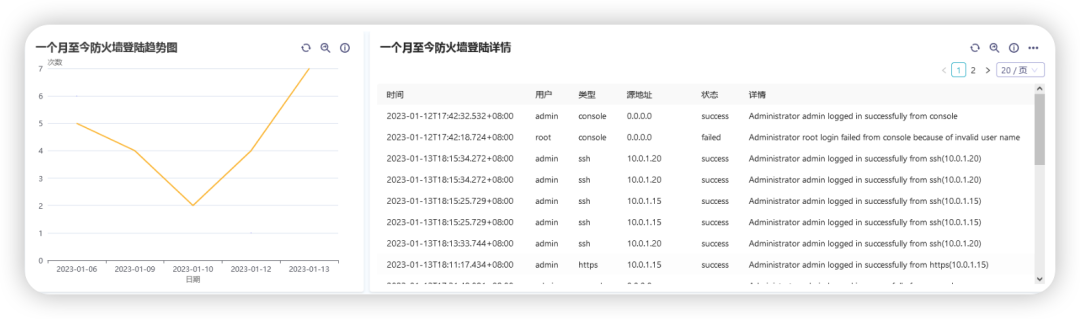
Firewall Logging Trends and Details
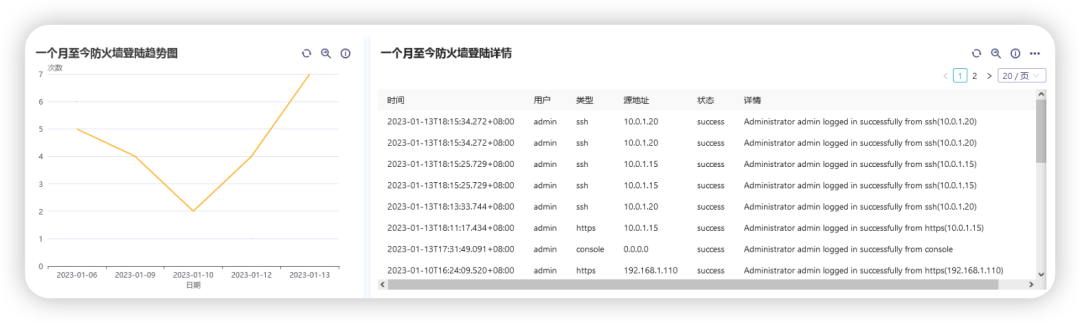
Statistical Firewall Logon Trends
Mainly query the situation and trend of firewall login
Firewall login details
Mainly query the login status of the firewall, which users log in, and how to log in, including the time of login, source address, etc.
Trends and details of firewall configuration changes
Mainly query the trend and details of firewall configuration changes, including which users have made configuration changes, the content of the changes, etc.
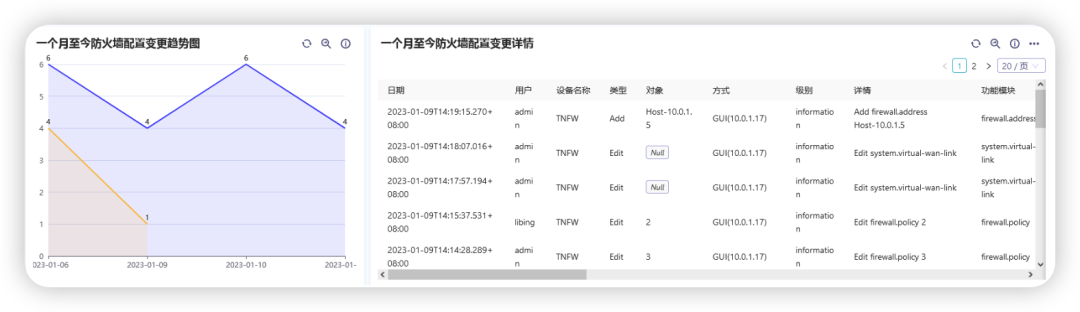
Trends in Firewall Configuration Changes
Firewall Configuration Change Details
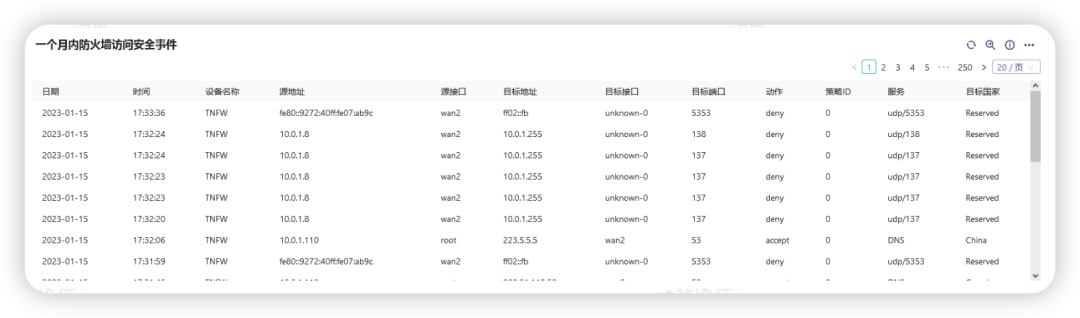
Firewall Security Access Events
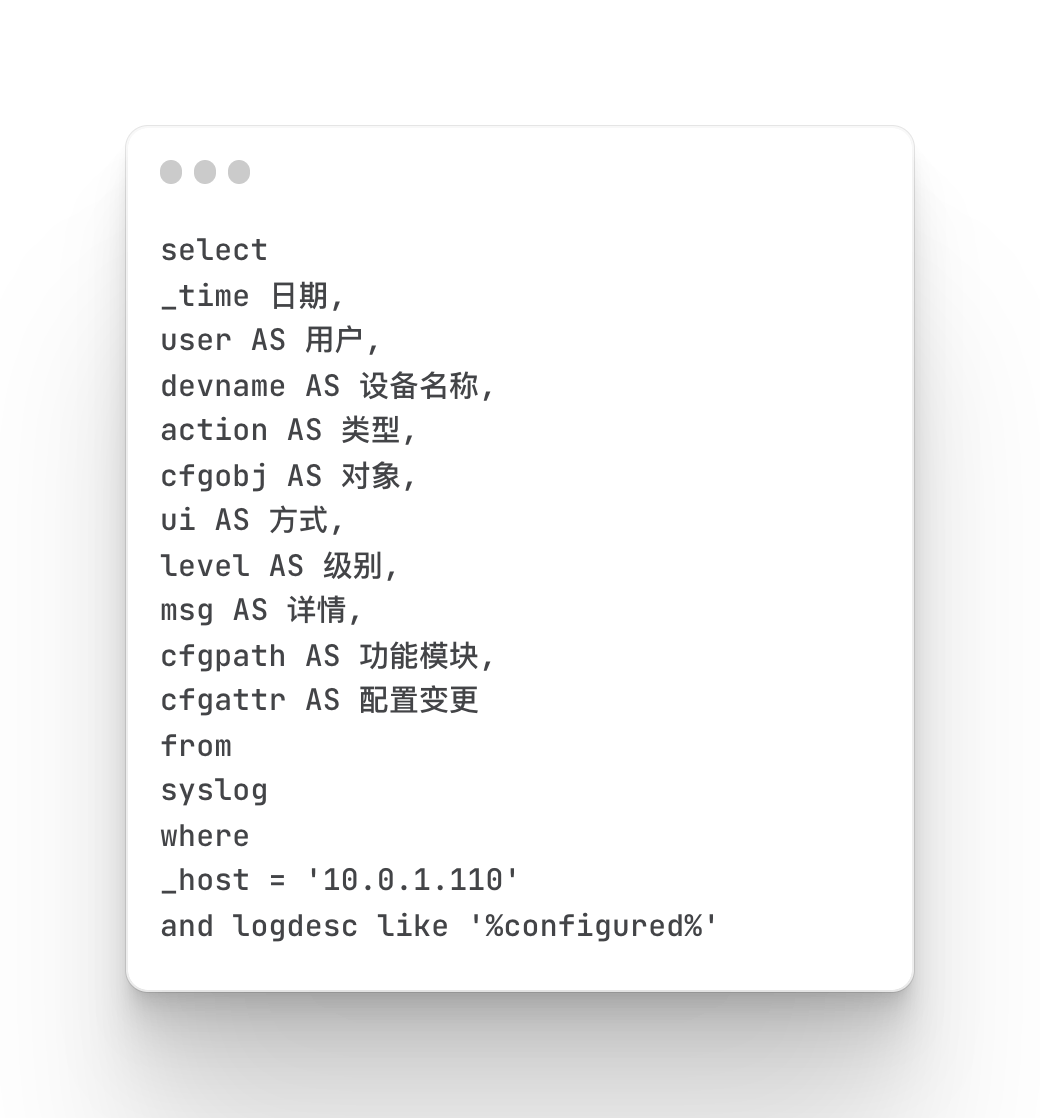
Mainly query firewall security access events, including source address, destination address, access protocol, port number and other information
Check for phrases:

Firewall failure trends and details
Mainly query firewall fault trends and details, including type statistics, alarm levels, types, modules, etc.
Firewall Failure Trends

Firewall Fault Details
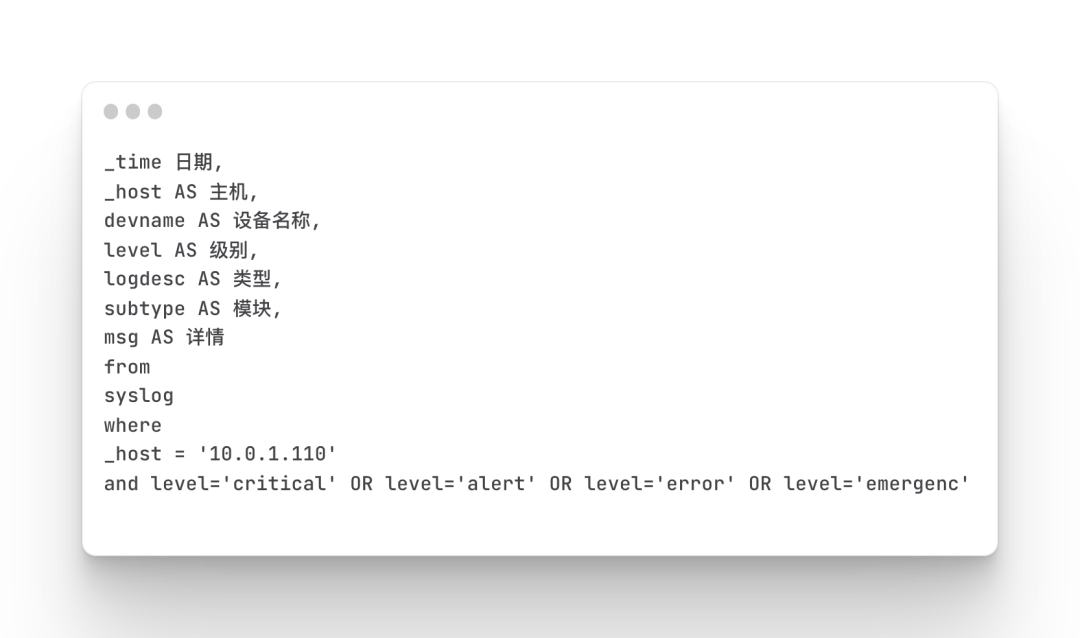
Firewall IPS Events
Mainly query the details of firewall IPS events, including level, source address and destination address, policy action, service type, access domain name and other information
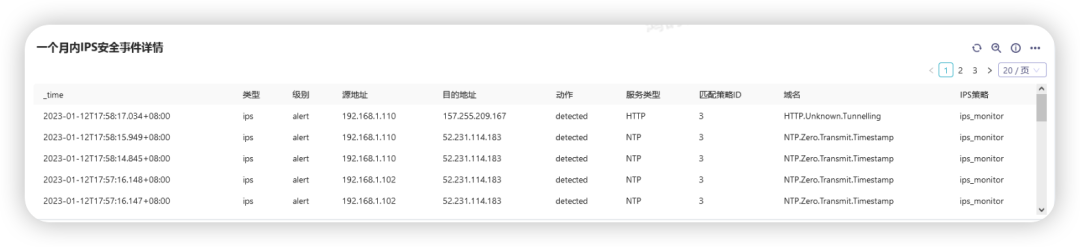
query command
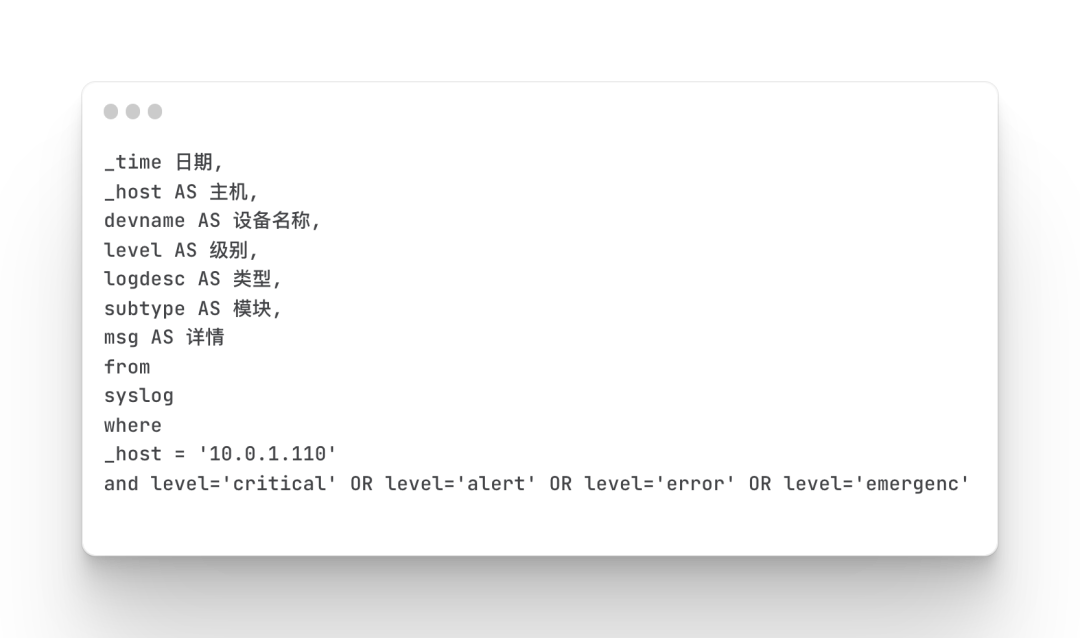
Firewall web protection events
Mainly query the details of firewall web protection events, including level, source address and destination address, action, policy ID, policy name, service type, access domain name and other information
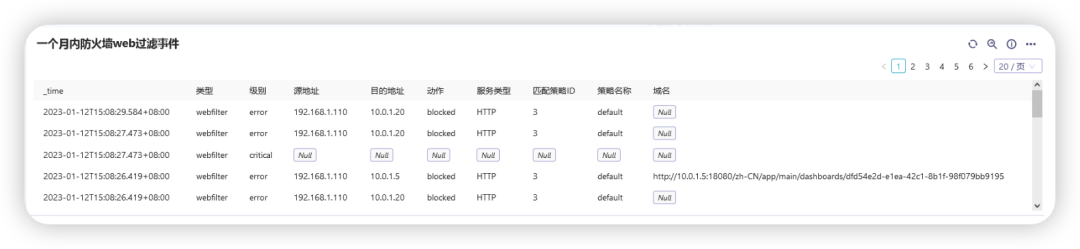
query command
