Article directory
- Intelligent Reflecting Surface (IRS)-Enabled Covert Communications in Wireless Networks
- Intelligent Reflecting Surface (IRS)-Aided Covert Wireless Communications With Delay Constraint
Intelligent Reflecting Surface (IRS)-Enabled Covert Communications in Wireless Networks
As security threats to wireless systems continue to grow, protecting user privacy is becoming more and more challenging. Even if the transmitted information is encrypted, the potential eavesdropping channels are physically limited, and the raw data itself, such as the location of the transmitter and the mode of transmission, could reveal confidential information. In this context, covert communications emerged as a practical solution aimed at hiding the existence of transmissions from observant adversaries . However, existing covert techniques inevitably consume additional resources, such as bandwidth and energy, and burden the system deployment. To solve this problem, we propose a communication concealment enhancement method based on Intelligent Reflective Surface (IRS) . The core idea is to utilize a subtly controlled metasurface to reshape adverse propagation conditions that may reveal secret messages. To facilitate the understanding of the proposed ideas, we first give an overview of the state-of-the-art covert communication techniques. Then, we introduce the basic principles of IRS and elaborate on how to integrate IRS to improve the concealment of communication . The joint configuration of IRS and legitimate transmitters is also studied in this paper, which is of great significance for the design of IRS-enhanced covert communication systems. Finally, we point out some open research directions.
Providing secure communications has never been more challenging due to the threat of technology integration. In an open wireless medium, the ubiquity of access interfaces and the use of shared spectrum make it easier for massive confidential information (such as financial accounts, identity authentication, and trade secrets) to be exposed to malicious attackers, whose goals are Intercept sensitive and private data. Therefore, ensuring the reliability and security of wireless data is still one of the important tasks in the development of next-generation networks, and it is increasingly concerned by the wireless community [1].
Current wireless security practices rely heavily on application/transport layer encryption. However, using cryptography to secure wireless communications faces the following challenges:
1) The standardized protocol adopted by the public network makes a large number of entities face the same threat;
2) If the eavesdropper has strong computing power, the security level of the encryption protocol may be compromised, because decryption needs to solve mathematical problems
; In a decentralized network without access and mobility, the distribution and management of keys is difficult.
To address these difficulties in encryption, physical layer security (PLS) methods have attracted considerable attention over the past few years. Essentially, PLS approaches secure information by exploiting only the fundamental properties of the wireless medium (i.e., interference, noise, and fading), which avoids the additional signaling and communication overhead incurred by encryption at higher layers . There are two notable trends in the research on PLS, namely Information Theoretic Secrecy (ITS) [2] and covert communication [3] . Its goal is to obtain a positive secrecy rate (ie, the rate difference between the legitimate channel and the eavesdropping channel) , at which rate information can be transmitted securely. However, from a privacy protection perspective, it is not enough to prevent transmissions from being deciphered. In an increasing number of cases, exposing position, movement, and even the presence of communication is disabling and even fatal. For example, exposure of commercial activities may reveal trade secrets. This has given rise to the need for covert communications, also known as low probability of detection (LPD) communications or undetectable communications, the purpose of which is to obscure the presence of legitimate transmissions from vigilant adversaries while maintaining a certain covert rate for intended users .
Overview It is worth noting that covert communication has the following three advantages:
- Stealth technology guarantees a stronger security level than ITS
- In contrast to encryption, the performance of covert communication does not depend on the capabilities of the adversary. Even if the adversary has powerful information processing capabilities, the achievable level of security will not be reduced
- Third, covert technology can serve as an alternative or complementary solution to upper layer security and privacy technologies, such as steganography and encryption.
Understanding Covert Communication
Consider a general peer-to-peer communication scenario where a legitimate transmitter (Alice) intends to wirelessly deliver a message to an intended receiver (Bob) without being detected by an adversary (Warden Willie). Willy monitors the wireless channel with the goal of detecting whether Alice is transmitting. Therefore, Willie is faced with the null hypothesis H 0 \mathcal{H}_{0} that Alice is silentH0and the alternative hypothesis H 1 \mathcal{H}_{1} that Alice is transmittingH1binary decision-making. For this, Willie can perform statistical hypothesis testing based on the average power received in the slot, denoted as P ˉ W \bar{P}_{W}PˉW. In H 0 \mathcal{H}_{0}H0In the case of P ˉ W \bar{P}_{W}PˉWContains the received interference power IW I_{W}IWand noise power σ W 2 \sigma_{W}^{2}pW2, in H 1 \mathcal{H}_{1}H1In the case of , the received signal power Sw from Alice is also included. Let D0 and D1 denote that Willie supports decisions H0 and H1, respectively. Willie's decision follows a threshold-based rule that asserts d_0 and d_1 when p_w is less than or greater than a predefined threshold τ, respectively. According to this rule, wrong judgment occurs in two cases: 1) Willie supports D1 when H0 is true, that is, false alarm; 2) Willie supports D0 when H1 is true, that is, false detection. The total probability of Willy making a wrong decision (including false alarms and false positives) can be interpreted as the covert probability of the transmission from Alice to Bob. Uncertainties in SW, IW, and σ2W have obvious effects on implicit probabilities.
Figure 1 illustrates the effect of different parameters. The blue and orange lines represent the probability density function (PDF) of IW+σ2W, respectively, with smaller variance and larger variance. For each case, the probability of false detection and probability of false alarm can be represented by the left and right shaded areas, respectively. We can observe that for a given value of τ, reducing SW can increase the false detection probability, and increasing the variance of interference and noise can increase the false detection probability and false alarm probability. As a result, communications can be performed more covertly, with less signal leakage to Willy and/or with greater interference plus noise fluctuations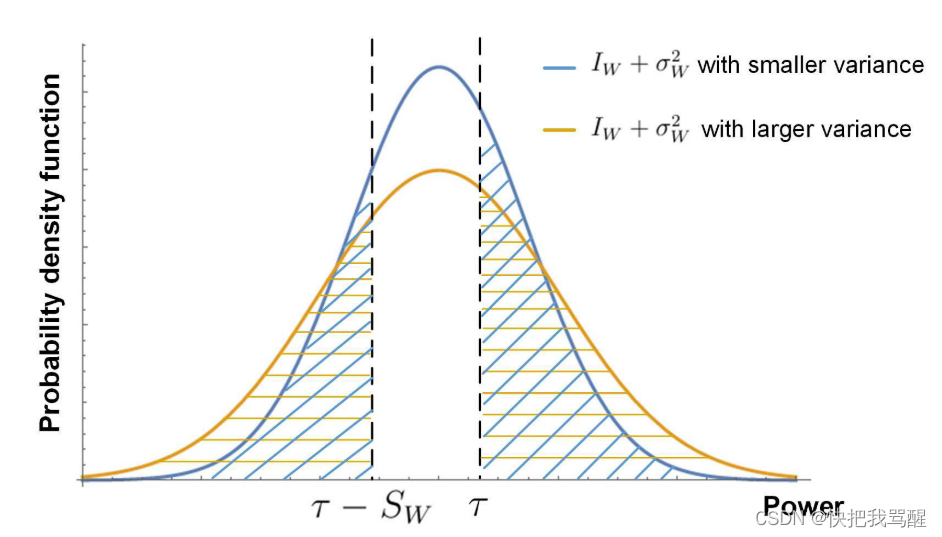
Overview of Covertness Techniques
Using the characteristics of covert communication, different methods have been proposed to improve the performance of covert communication.
1 Multiple Antennas:
Multi-antenna: Taking advantage of the space degree of freedom, multi-antenna technology can improve the concealment of wireless channels through directional transmission [5]. This can be achieved by means of beamforming that produces spatial selectivity. Specifically, the beamformer adjusts the relative phase and amplitude of the signals on each element of the antenna array such that the superimposed radiation pattern is constructive in desired directions and destructive in other directions . Thus, the transmitted signal can be focused towards the intended receiver to increase the achievable rate and at the same time zero the LPD at the adversary. Multi-antenna technology is highly scalable for deployment because it is a transmitter-side implementation. The performance of beamforming depends heavily on the availability of instantaneous channel state information (CSI) . In a multi-antenna transmitter, inaccurate CSI due to estimation errors will lead to a high probability of signal leakage to the enemy, thereby degrading the concealment performance. However, the negative impact of imperfect CSI can be mitigated when the number of transmit antennas becomes huge, eg more than one hundred [6]. Highly correlated channels in the area of massive antennas minimize the CSI estimation error, resulting in high beamforming resolution. The channel hardening effect, which makes the effective channel gain deterministic, is an additional property of massive antennas that can be exploited to provide reliable concealment rates.
Taking advantage of spatial degrees of freedom, multiple-antenna tech- niques
can be utilized to improve the stealthiness of wireless channels through directional
transmission [5]. This can be realized by means of beamforming to produce spatial selectivity. In
particular, a beamformer adjusts the relative phase and amplitude of the signals on each element
of an antenna array such that the superposed radiation pattern is constructive in the desired
direction and destructive in the other directions. As a consequence, the transmitted signals can
be concentrated towards the desired recipient to enhance the achievable rate and concurrently
nulled at the adversary for LPD. Multiple-antenna techniques have high deployment scalability
as it is a transmitter-side implementation. Beamforming performance is largely dependent on the
availability of instantaneous channel state information (CSI). The inaccuracy of CSI at a multi-
antenna transmitter due to estimation error could result in a high probability of signal leakage
to the adversary and thus degrade the covertness performance. However, the negative impact of
imperfect CSI can be mitigated as the number of transmit antennas becomes massive, e.g. more
than one hundred [6]. The highly correlated channels in massive antenna region render minimal
CSI estimation errors and hence high beamforming resolution. Channel hardening effect that
makes effective channel gains deterministic is an additional attribute of massive antennas that
can be exploited to provide reliable covert rate.
2 AN Generation
Random ANs can be generated to increase the jamming dynamics, deliberately misleading the adversary's decision about the existence of any covert transmissions . The key to a successful design is to avoid the negative impact of interfering signals on legitimate channels [7]. To this end, multiple antenna techniques can be used to generate nulls in the direction of legitimate users. In the case of knowing the location of the opponent, stronger concealment can be obtained, so as to destroy the detection ability of the opponent to the greatest extent through directional jamming .
A prominent feature of AN generative methods is their flexible realizability. In practice, can be generated by different entities. Some common ways to achieve generation are described below. :
- ** Coordinated Jamming: Use third-party devices such as power beacons and drone radio transmitters as aides in jamming an opponent's channel**. One or more friendly jammers could coordinate with Alice to jam Willie's channel while causing minimal impact to legitimate transmissions. Cooperative interference incurs synchronization and communication overhead to control transmit power. Furthermore, the use of cooperative jammers sacrifices scalability of deployment and may not work effectively in the presence of mobility.
- Full-duplex interference: Concurrent message reception and in-band AN generation can be supported by full-duplex receivers . This approach overcomes the control overhead and mobility issues of cooperative interference at the expense of loopback self-interference from the transmit to receive RF link . Due to the recent development of full-duplex techniques in several areas such as antenna interfaces, analog baseband, and digital processing, self-interference can be suppressed to tolerable levels at a feasible cost.
- AN injection is a sender-side technique capable of simultaneously sending information signals and AN . Ideally, the AN is constructed to be orthogonal to the legal channel such that only the Willy channel is affected. The key to injection is to balance the trade-off between concealment and information rate by optimizing the transmit power of the interference signal and the information signal.
Cooperative Relaying
Cooperative relay relies on cooperation from intermediate nodes to facilitate undetectable communication. For legitimate communications, access distance has a profound effect on concealment. For long-distance transmission, higher transmit power is required to achieve the target rate, which inevitably compromises concealment . Cooperative relay solves this problem through multi-hop forwarding. The rationale is to shorten the access distance at each hop to keep the required transmit power low, resulting in a low probability of Willy detection . Since covert communication based on cooperative relay involves using third-party devices as relays, its deployment scalability is relatively low.
Spread Spectrum
Spread spectrum methods facilitate concealment by suppressing the average power spectral density (PSD) of the transmitted signal below the noise floor level . Specifically, this information is modulated onto sequential noise-like waves, or pseudonoise sequences, that greatly expand the transmission bandwidth compared to that required for normal narrowband signals. Therefore, it is difficult for an attacker to distinguish the information-carrying signal from the noise, which greatly reduces the detectability of the signal. Typical modulation techniques used for bandwidth extension include direct sequence technology and frequency hopping technology. The direct sequence technology spreads the transmission signal to multiple frequency channels , and the frequency hopping technology randomly and quickly switches the transmission channel within a fairly wide frequency range . In general, direct sequences are more immune to malicious detection when the PSD of the sending signal is consistently low. Frequency hopping is more exposed because it utilizes narrowband signals with high PSD to hop at any frequency. In addition to LPD, the frequency diversity conferred by spread spectrum signals also provides robustness against fading for covert communications. The spread spectrum method is highly deployable because it is a sender operation.
Millimeter-Wave Communications:
Millimeter wave (MMWave) communication works in the frequency band of 30-300 gigahertz (GHz), and has the characteristics of steerable narrow beam, that is, accurate angular resolution can be achieved through a moderately small antenna size . The directivity of the narrow beam is naturally beneficial for obscuration since signal leakage due to imperfect beam patterns towards off-axis directions can be suppressed . To intercept MMWave communications, an adversary can only detect a misaligned beam that exhibits a behavior of switching on and off when burst beams arrive intermittently [8]. This distinguishable beam pattern effectively undermines adversary detectability. In addition, MMWave's ultra-wideband allows a high degree of flexibility in the frequency range of legal transmissions compared to microwaves. Sweeping signals across a wide spectrum can impose significant overhead on adversary signal detection. The disadvantage of short wavelengths is that the scattering and diffraction capabilities are weakened, so that millimeter waves are severely attenuated and easily affected by obstacles. Also, MMWave's Doppler shift is strong even at walking speeds. Therefore, the deployment stability of MMWave-based covert communication is low, because the covert rate of MMWave communication is largely affected by line-of-sight channel availability and mobility.
Table 1 summarizes and compares the physical layer techniques for covert communication reviewed above. In general, existing concealment techniques can be divided into two categories based on their impact on adversaries. One is to mitigate information signal leakage, and the other is to expand the interference dynamics to cover signal leakage. These methods inevitably consume additional system resources, such as bandwidth and energy, and sacrifice communication performance at legitimate users.

IRS-ENHANCED COVERT COMMUNICATION
In order to solve the resource consumption problem of existing covert technology, a covert communication solution based on Intelligent Reflective Surface (IRS) is proposed. The core technology of IRS is to use programmable metamaterials to fully control the electromagnetic behavior of shock waves. With the support of IRS, the proposed method has the potential to protect the transmission from malicious detection by changing the propagation environment. This approach is fundamentally different from existing approaches, since recycling environmental resources (i.e., transmitted signals not received by the intended recipient) has not previously been considered for covert communication. An outstanding advantage of IRS is its compatibility with existing systems, which can be illustrated in Figure 2. In particular, IRS can work in conjunction with existing concealment techniques without redesigning the corresponding protocols and hardware, because The IRS is intended only as an aid for ambient signal manipulation. At the same time, IRS can be configured jointly with existing systems for performance optimization, a case study in this paper will show an example. This paper first expounds the basic concept of IRS, including the principle, characteristics of IRS and the difference with other related concepts, and then introduces the covert communication system enhanced by IRS.
Fundamentals of IRS
The IRS is a software-controlled artificial surface that can be programmed to alter its electromagnetic response. The hardware implementation of the IRS is based on tunable metasurfaces, which are thin, planar electromagnetic materials composed of discrete scattering particles dispersed on a structure, whose electromagnetic properties (such as capacitance and resonance) can be changed without the need for refabricated digital reengineering. This can be achieved by exploiting electronically tunable meta-atoms, such as liquid crystals, varactor/PIN diodes, doped semiconductors, microelectromechanical systems (MEMS) switches, and flexible plasmas. Generally, there are three methods to change the electromagnetic properties of meta-atoms, namely tunable resonant cavity technology, guided wave technology and rotation technology.
The collective configuration of the constituent meta-atoms enables the synthesis of a wide variety of radiation modes not feasible in natural materials across the meta-surface. The meta-atoms can be tuned both uniformly and individually. The former enables simple electromagnetic manipulations, such as absolute absorption and passive reflection, while the latter supports more complex manipulations, such as wave polarization, imaging, and holograms. Electromagnetic reconfiguration enables a remarkable function of the IRS to recycle existing environmental signals. Specifically, IRS can reshape the phase, amplitude, and reflection angle of environmental signals to serve its own goals, such as jamming and signal cancellation. With the rapid development of metamaterial fabrication technology, modern IRSS can completely reshape the phase, amplitude, frequency and reflection angle of the impact signal in a full-duplex manner. For example, the authors in [10] implemented a biphasic IRS and demonstrated that for point-to-point transmission in an indoor environment, IRS can increase the signal strength at the receiver by an order of magnitude or cancel it outright. More detailed knowledge about the hardware fabrication and network implementation of IRS can be found in [9], [11].
To avoid confusion with some related technologies that can also be used to facilitate covert communications, we discuss their key differences and highlight the comparative advantages of IRS as follows.
- A phased array utilizes an array of radiators with variable phase shifts to produce different beam patterns. Since each radiator is associated with a dedicated active RF chain, phased arrays have high hardware costs and a large form factor. Additionally, the performance of phased arrays degrades at high frequencies (e.g. GHz), a consequence of the reduced efficiency of the feed lines. In contrast, IRSs are characterized by low-cost manufacturing with almost passive components. Metamaterials such as ferroelectric thin films and graphene maintain good control of electromagnetic waves over a wide frequency range covering the terahertz and visible regions [9]. Another desirable feature of the IRS is that the adjacent surfaces enable finer spatial resolution of electromagnetic control compared to radiator-separated spaced antenna arrays.
- Active metasurfaces [ 12] utilize active materials (e.g. ε-near-zero materials [13]) to generate electromagnetic fields across the surface. Although active metasurfaces offer exceptional signal controllability, manipulation is energy-intensive, and configuration often results in high computational complexity, for example due to signal processing. In contrast, IRS has greatly reduced computational complexity and lower energy distribution due to its passive electromagnetic manipulation. The IRS consumes virtually zero power during reflections and only incurs power dissipation when reconfiguring the electromagnetic properties of the IRS unit.
- Full-duplex relays are similar to IRSs in terms of full-duplex transmission and multipath diversity gain. Full-duplex relays can be active or passive.
Active relays relay data using signals generated by their active components, such as power amplifiers. Self-interference and this signal processing delay are unavoidable for active relays due to full-duplex operation. In contrast, the IRS is immune to self-interference due to its passive electromagnetic operation .
A passive repeater reflects an existing source signal for data forwarding. The electromagnetic response (i.e. reflection coefficient) of a passive relay is usually pre-designed and fixed. In contrast, IRSs have greater flexibility in tuning their electromagnetic responses.
In addition, IRS is far more versatile than information forwarding relay, as it can perform concurrent functions (such as beam steering and interference cancellation) to meet heterogeneous quality of service (QoS) requirements.
In addition to its unique physical characteristics, IRSS is deployment friendly. First, metasurfaces can be fabricated with nearly passive components, such as analog phase shifters, that do not rely on active components for transmission. As a result, circuits on metasurfaces typically consume low power and can be powered by microwave energy harvesting. For example, the experimental results in [10] show that the energy consumption of the implemented IRS is generally equal to or lower than the microwave energy it can recover. Second, due to the lightweight and ultrathin footprint of the metamaterial, it can be easily coated on the fronts of environmental objects, such as walls, vehicles, and smart clothing, to construct a rich scattering environment. Therefore, IRS-coated objects have the potential to provide a more deterministic wireless propagation environment in a self-sustaining manner. This opens up opportunities to meet the heterogeneous QoS requirements (e.g., more stable connections, higher data rates, higher spectral efficiency) of next-generation networks by simply recycling existing environmental resources.
IRS-Aided Covert Communication Systems、
By taking advantage of MetaSurface's powerful electromagnetic control, IRS can be carefully designed to improve undesired propagation conditions to facilitate covert communications. In general, two functions of the IRS can be utilized to enhance the concealment of transmissions. On the one hand , IRS can reflect a desired signal (such as information transmission) in phase with the signal at the intended receiver, thereby strengthening the signal, known as signal enhancement . On the other hand, IRS can reflect unwanted signals (such as information leakage and interference) with the opposite phase of the signal at the unwanted receiver, which is called signal cancellation . Generally, there is a trade-off when configuring the electromagnetic response of an IRS element in order to simultaneously achieve the above two goals.
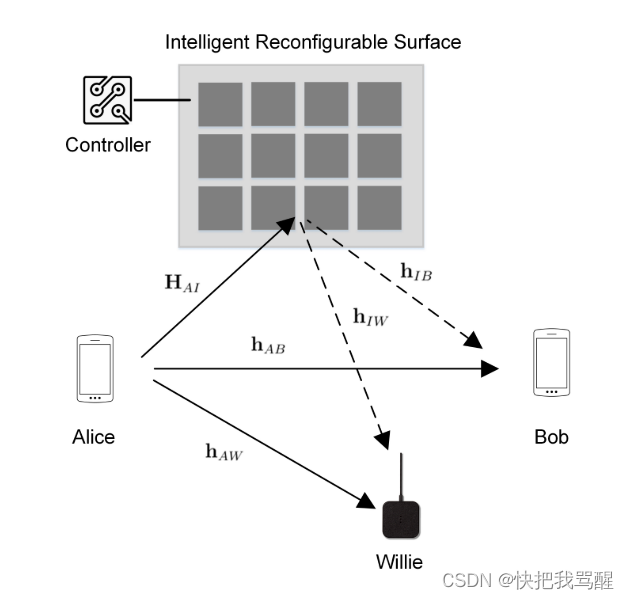
Next, we illustrate how IRS can be exploited to enhance covert communication in various system contexts (Fig. 2).
Figure 2(a) illustrates a baseline system model in which Alice transmits data to Bob intermittently in the presence of Willy. In this case, IRS can be used to perform signal enhancement at Bob and signal cancellation at Willie. Therefore, an increased transmission rate at Bob and a decreased detection probability at Willie can be achieved simultaneously .
In addition, in the wireless power covert communication system in which Bob has the RF energy harvesting capability, Alice can also perform wireless power transmission or wireless information and power transmission simultaneously to provide energy for Bob. In addition to enabling covert communications, IRS can also be used to facilitate wireless power transfer. Figure 2(b) considers the case where Alice uses MMWave for covert transmission, which is extremely vulnerable to blockage due to severe penetration loss and poor diffraction of non-line-of-sight links. As shown in the figure, when there is congestion between Alice and Bob, deploying an IRS with LOS link to Alice and Bob can be used to solve the negative impact of congestion on MMWave covert communication.
Figure 2© depicts the case where the baseline system is affected by co-channel interference, eg from environmental interference or malicious interference. In this case, the IRS can additionally be configured to perform interference cancellation at Bob and interference enhancement at Willie to hide the signal from Alice.
In addition to the negative impact of co-channel interference, legitimate users may face eavesdropping attacks, as shown in Figure 2(d). Signal cancellation at the eavesdropper and Wiley is required to deal with concurrent attacks.
Research on Optimal Configuration of IRS Enhanced Covert Communication under Uncertainty of Noise
We present a case study of designing an IRS-enhanced covert communication system. We use noise as the only masking medium in order to demonstrate the impact of IRS on masking performance.
We present a case study of designing an IRS-enhanced covert communication system. We use noise as the only masking medium in order to demonstrate the impact of IRS on masking performance. We consider an IRS-enhanced covert communication system in which Alice intends to send to Bob via LPD via Warden Will. An IRS was deployed to facilitate Alice's covert transmission. We think that Alice, Bob, and Willy all have an antenna. Alice has PA ˉ \bar{P_A}PAˉIndicates the maximum transmit power budget. IRS by NNIt consists of N passive reflection units, and each passive reflection unit can independently generate any phase shift of the incident signal wave. All channels in the system experience exponentα \alphaPower-law path loss and block Rayleigh fading for α . Similar to [4], we assume that the CSI of all channels is available on both Alice and IRS for joint optimization, resulting in the best system performance benchmark. It is worth noting that Wiley's CSI can be reasonably estimated when Wiley is an active transmitter [14].
We considered Willie σ W 2 \sigma_{W}^{2}pW2A bounded uncertainty model of the observed noise whose PDF is given by [15, Equation 3]: f σ W 2 ( x ) = 1 / ( 2 ln ( ρ ) x ) f_{\sigma_{W }^{2}}(x)=1 /(2 \ln (\rho) x)fpW2(x)=1/(2ln ( ρ ) x ) , ifσ n 2 / ρ ≤ σ W 2 ≤ σ n 2 ρ \sigma_{n}^{2} / \rho \leq \sigma_{W}^{2} \leq \sigma_{ n}^{2} \rhopn2/ p≤pW2≤pn2ρ, f σ W 2 ( x ) = 0 f_{\sigma_{W}^{2}}(x)=0 fpW2(x)=0 , otherwise. Here,σ n 2 \sigma_{n}^{2}pn2is the nominal noise power, ρ ∈ [ 1 , ∞ ) \rho \in[1, \infty)r∈[1,∞ ) is to determineσ W 2 \sigma_{W}^{2}pW2Uncertainty parameter for range. Note that the larger the value of ρ1, the greater the uncertainty of σ2w. Similar to [15], the noise uncertainty at Bob is not considered since it does not affect the concealment performance. Specifically, the noise power at Willie is considered to have mean 0 and variance σ B 2 \sigma_{B}^{2}pB2Gaussian white noise. Furthermore, Wiley is considered to know a priori σ W 2 \sigma_{W}^{2}pW2distribution and received signals from Alice, without knowing the existence and operation of the IRS. Therefore, Willie can only set its detection threshold based on existing prior knowledge.
By jointly optimizing the IRS unit phase and Alice’s transmit power, the optimization problem of maximizing the concealment rate between Alice and Bob measured by Shannon’s capacity is considered, and the conditions are: (1) Concealment constraints: Willie’s false alarm probability and false detection probability The sum is greater than the target threshold ζ; 2) Phase operation constraints, that is, the phase shift of the IRS unit is within [0,2π); 3) Transmit power constraints, that is, Alice should transmit at a power level lower than P.
Next, we perform Monte Carlo simulations to investigate the formulation of the optimization problem. In the simulation, Alice, Bob, IRS and Willie are located at (0, 0), (d, 0), (d/2, 0) and (0, 15) in the two-dimensional area, respectively. Alice is considered to have a 50% chance of spreading. For each simulated implementation, we generate independent and identically distributed noise power at Wiley σ2W and exponentially distributed fading gains with unit mean for all channels.
Figure 4 will implicit rate RAB R_{AB}RABDescribed as the maximum transmit power PA ˉ \bar{P_A}PAˉThe function. For comparison purposes, we also give the RAB R_{AB} without using the IRSRABresult. It can be found that with the help of IRS, RAB R_{AB} can be significantly improvedRAB. Furthermore, in the case with the IRS, compared to the case without the IRS, RAB R_{AB}RABA stable value is reached at a larger PA. RAB R_{AB}RABThe reason for stopping the increase at a stable value is that, given a certain noise level, if Alice's transmit power is above a certain level, then with the help of the IRS, the coverability constraint can no longer hold.
Another observation is that at Willy's larger noise uncertainty (with a larger ρ \rhoρ ) helps to improveRAB R_{AB}RAB。 ρ = 5 \rho=5 r=5 andρ = 2 \rho=2r=The performance gap in case 2 increases with PA ˉ \bar{P_A}PAˉbecomes more apparent with the increase. \
conclusion and future directions
Integrating IRS into the covert communication system can recycle previously unused environmental resources and improve the covertness of communication . This paper reviews the existing covert technology and looks forward to the prospect of using IRS technology to revolutionize covert communication system in every aspect. Through an example, through the joint configuration of IRS and covert communication system, the covert performance of the system can be greatly improved. We strongly believe that emerging IRS technologies will open up vast opportunities in the design and development of future wireless security beyond just covert technology.
The scope of research on IRS enhanced covert communications is extensive. Some open questions and research directions are as follows:
- Channel Estimation: Since waveform manipulation of IRS relies on CSI to enhance covert communication, system performance is heavily dependent on the availability and accuracy of CSI. However, since the IRS works almost passively, it is difficult to obtain the instantaneous CSI of the reflection channel. In this context, machine learning-based approaches that allow channel estimation without explicit feedback/detection are worth exploring to design feasible solutions.
- IRS-based information/communication theoretical model: Utilizing the signal enhancement and cancellation capabilities of IRS, the IRS-enhanced covert channel is expected to transmit a larger capacity of information bits. Therefore, the traditional covert channel capacity needs to reconsider the programmability of the channel. Furthermore, scaling laws for IRS-enhanced covert channel capacity need to be derived to fundamentally understand the achievable performance limit.
- Impact of multiple IRSSs: IRSSs are expected to be deployed on the surface of environmental objects with complex spatial patterns. Thus, it is a common scenario that the communication environment is co-shaped by multiple IRSs. The combined effect of ambient IRSS operation on IRS-enhanced covert communications deserves consideration of their spatial distribution.
Intelligent Reflecting Surface (IRS)-Aided Covert Wireless Communications With Delay Constraint
This paper investigates the performance gains obtained by using intelligent reflective surfaces (IRS) in covert communications. To this end, we propose a joint design of transmit power and IRS reflection coefficient considering the concealment of communication under the condition of global channel state information (CSI) and warden-free instantaneous CSI. For the case of global CSI, we demonstrate that perfect concealment can be achieved even for single-antenna transmitters with the help of IRS, which is impossible without IRS. Then, we develop a penalized successive convex approximation (PSCA) algorithm to solve this design problem. Aiming at the high complexity of the PSCA algorithm, a low-complexity two-stage algorithm is further proposed, and the analytical expressions of the transmit power and the IRS echo coefficient are derived. For the case where Warden's instantaneous CSI does not exist, we analytically derive the masking constraints, which facilitate the design of optimal phase shifts. We then consider three hardware-related constraints and determine their optimal design and optimal transmit power. Our tests show that deploying IRS in covert communications can achieve significant performance gains.
In order to meet the growing demand for high-speed data applications and large-scale connections in wireless networks, a variety of advanced technologies such as massive multiple-input multiple-output (MIMO), millimeter wave (MMWave), and ultra-dense network (UDN) have been proposed [1], [2]. However, these technologies generally suffer from high energy consumption or high hardware complexity due to the use of power-hungry RF links. As a remedial measure, intelligent reflective surfaces (IRS) are emerging as a promising solution to effectively improve spectral efficiency and energy efficiency [3]. Specifically, the IRS is a plane composed of a large number of controllable, low-cost passive reflective elements, each of which reflects an incoming signal with a controllable amplitude and phase shift. Therefore, IRS can customize the propagation environment from transmitter to receiver to achieve various design goals (eg, signal enhancement, interference suppression). Due to the above advantages, IRS has been studied in various application scenarios, such as single-user systems [4], [5], multi-user systems [6]-[11] and wireless information and power transfer systems [12], [13 ], and is considered as a promising technology to realize the sixth generation (6G) wireless network [14], [15].
In recent years, considering the increasing concern about security issues in wireless communication, some recent works discuss IRS-assisted communication security in wireless networks from the perspective of physical layer security, such as [16]–[23]. Usually, by rationally designing the IRS reflection coefficient, the received signal strength of the target user can be enhanced, and the received signal strength of the eavesdropper can be weakened, thereby improving the confidentiality performance of the IRS auxiliary network. For example, as shown in [16], by jointly optimizing the transmit beamforming and the reconstruction beamforming, the security of the physical layer can be guaranteed in the IRS-assisted network even if the quality of the eavesdropping channel is higher than that of the legitimate channel. Along this direction, an alternative optimization algorithm based on the semi-programmatic relaxation technique (SDP) is proposed in [17] to determine safe transmit beamforming and reconstruction phase shifts. Furthermore, the authors of [18] also discuss the question of whether and when artificial noise (AN) is beneficial for IRS-aided physical layer security of wireless communication systems. At the same time, [19]-[21] considered the optimization of the MIMO eavesdropping channel on the transmit covariance matrix and the IRS phase shift, and [22] and [23] considered the multi-user multiple-input single-output (MISO) and MIMO wireless Channel incompleteness in secure communication.
The aforementioned physical layer security techniques focus on protecting the content of transmitted messages from eavesdropping. However, these techniques do not alleviate the privacy concerns that arise from discovering the presence of transmitters or transmissions. Fortunately, emerging cutting-edge covert communication techniques, designed to hide the existence of wireless transmissions, are able to maintain such a high level of security and privacy [24]. In general, a positive covert transmission rate can be obtained when Willie (Willie) has various uncertainties, such as noise uncertainty [25] and channel uncertainty [26]. In particular, a fundamental limit for covert communication in additive white Gaussian noise (AWGN) channels is established in [27], where the authors prove that in N channels, at most O(√N) bits of information can be covertly and reliably from the transmitter (Alice) to the desired receiver (Bob). Furthermore, covert communication with the help of a full-duplex (FD) receiver is studied in [30]–[32], where the FD receiver generates a signal with random transmit power to intentionally confuse Wiley's detection. Inspired by this, the authors of [29] introduce an uninformed jammer to impose artificial uncertainty on Wiley. The results show that the optimal transmit power strategy is a form of truncated channel inversion under the average shadowing constraint. Meanwhile, [34]–[36] studied covert communication in relay network and unmanned aerial vehicle (UAV) network. Furthermore, the conditions for guaranteeing the optimality of Gaussian signaling in covert communication are discussed in [33]. Recent literatures [34], [35] and [36] study covert communication in random wireless networks and covert communication under delay constraints, respectively.