Introduction to BinaryFormatter BinaryFormatter is located in the namespace: System.Runtime.Serialization.Formatters.Binary, which serializes and deserializes objects in binary format. BinaryFormatter is widely used throughout the .NET ecosystem because of its power and ease of use. However, its powerful capabilities also allow an attacker to influence the control flow within a target application. A successful attack could result in the attacker being able to run code in the context of the target process.
A simpler analogy is to assume that calling BinaryFormatter.Deserialize on a payload is equivalent to interpreting that payload as a standalone executable and launching it. For more information, please see the official website introduction: Deserialization risk when using BinaryFormatter and related types (https://learn.microsoft.com/zh-cn/dotnet/standard/serialization/binaryformatter-security-guide
)
## 01 BinaryFormatter serialization and deserialization
First we define a Person class
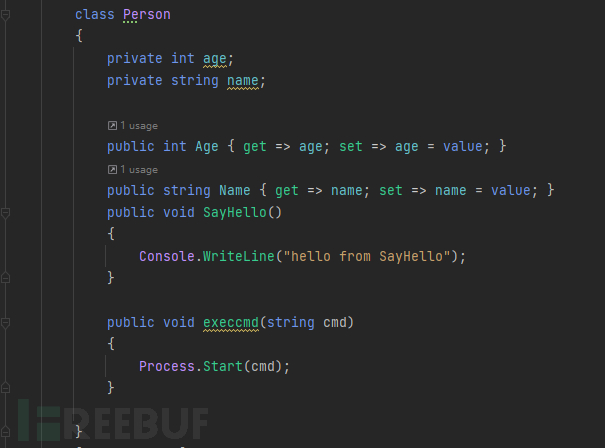
Initialize and serialize output and deserialize
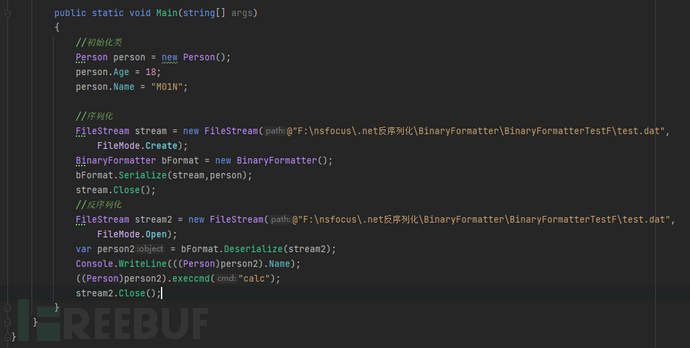
BinaryFormatter deserialization command execution does not need to control the type type, but only needs to be able to control the incoming value. If you have read the source code of ysoserial, you can find that the BinaryFormatter deserialization attack chain is mainly based on two chains, one is TextFormattingRunProperties, and the other is One is TypeConfuseDelegate, and most other attack chains are encapsulated on the basis of these two chains.
##02TextFormattingRunProperties
Let's take a look at how ysoserial generates the payload of TextFormattingRunProperties, the code is in TextFormattingRunPropertiesGenerator.cs. In TextFormattingRunPropertiesGadget() on line 242, you can see that a xaml_payload is generated and passed into TextFormattingRunPropertiesMarshal(xaml_payload) to get the final payload.
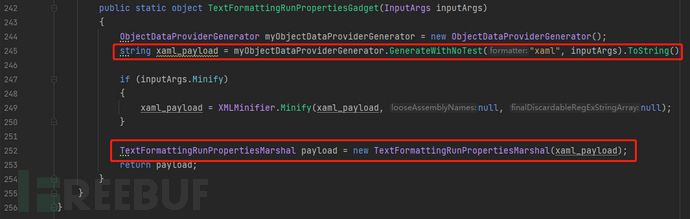
In TextFormattingRunPropertiesMarshal(xaml_payload), xaml_payload is set to ForegroundBrush.
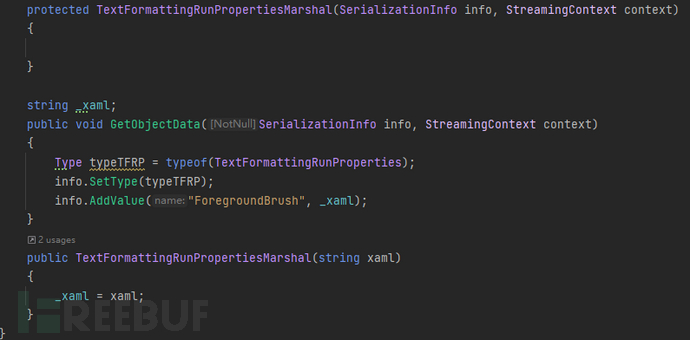
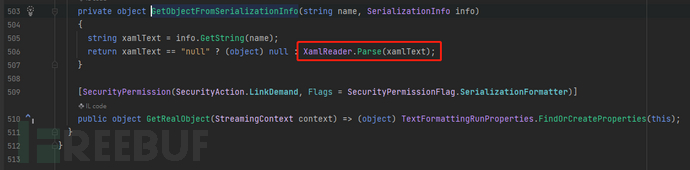
Why ForegroundBrush? We can take a look at TextFormattingRunProperties. In the serialization function, this.GetObjectFromSerializationInfo(nameof
(ForegroundBrush), info) is executed.

Follow up GetObjectFromSerializationInfo(), what do you see? XamlReader.Parse()! So far , the xaml_payload of ObjectDataProvider has been connected. This part has been introduced in the front.
As for why ForegroundBrush is used, other parameters are not used, because the lack of ForegroundBrush will report an error.

So far, the following attack chain can be constructed:
Implement the ISerializable interface –> assign the ForegroundBrush field to the xaml payload when GetObjectData is serialized, and assign the object type to the TextFormattingRunProperties class –> trigger the deserialization constructor GetObjectFromSerializationInfo –> the deserialization constructor triggers the XamlReader .Parse(payload)
RCE
Note that the TextFormattingRunProperties
class is located in the namespace: Microsoft.VisualStudio.Text.Formatting. It is implemented in Microsoft.VisualStudio.Text.UI.Wpf.dll and Microsoft.PowerShell.Editor.dll assemblies. The former needs to install Visual
Studio, while the latter comes with PowerShell. So the target environment can use this class without VS installed.
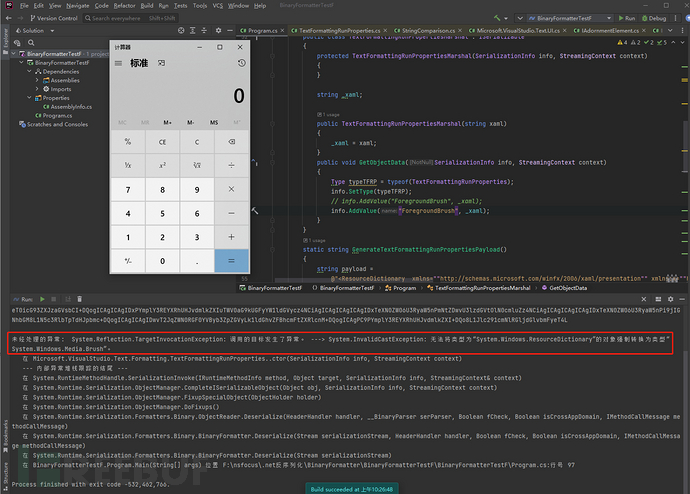
In the end, although the deserialization is executed successfully, an error will still be reported. So why do we report an error? Because XamlReader.Parse()
parses an instance of ResourceDictionary type, we assign it to a variable of type Media.Brush, so an error will be reported.
## 03 Summary
BinaryFormatter deserialization has many attack chains, but most of them are encapsulated on the basis of TextFormattingRunProperties chain. And TextFormattingRunProperties is the encapsulated XamlReader.Parse()
, which
can realize code execution with the Xaml payload of ObjectDataProvider. In other words, when we use BinaryFormatter to deserialize the data encapsulated by TextFormattingRunProperties, it will eventually fall to XamlReader for deserialization.
reference
https://xz.aliyun.com/t/9593
https://zhuanlan.zhihu.com/p/333316520
https://zhuanlan.zhihu.com/p/333701103
http://www.hackdig.com/05/hack-356873.htm
https://mp.weixin.qq.com/s/2s457-XCm4XSCjK5NsMv6g#at
ck-356873.htm
https://mp.weixin.qq.com/s/2s457-XCm4XSCjK5NsMv6g#at
at last
For students who have never been exposed to network security, we have prepared a detailed learning and growth roadmap for you. It can be said that it is the most scientific and systematic learning route, and it is no problem for everyone to follow this general direction.

At the same time, there are supporting videos for each section corresponding to the growth route:
Of course, in addition to supporting videos, various documents, books, materials & tools have been sorted out for you, and they have been classified into categories for you.
Due to the limited space, only part of the information is displayed. Friends in need can [click the card below] to get it for free: