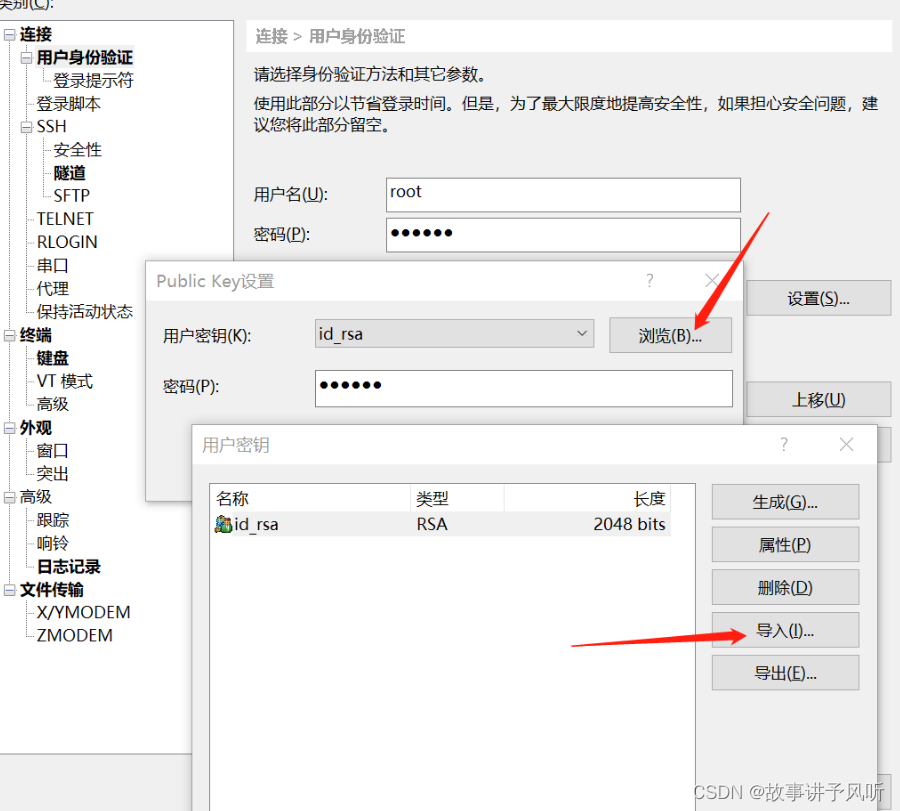
Using a key to log in increases the security of ssh because it prevents malicious users from attempting to guess passwords using brute force techniques. In ssh, logging in with a key is a two-step process:
-
Generate or obtain a pair of public and private keys.
-
Add the public key to
~/.ssh/authorized_keysthe files of the users managed on the server.
Here are more detailed steps:
1. Generate or obtain a pair of public and private keys.
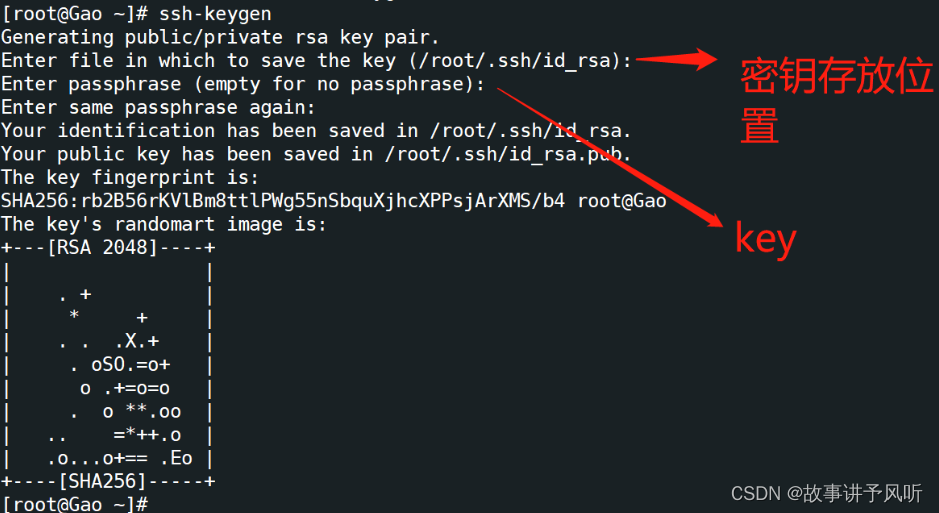
SSH keys can be generated using the following command:
ssh-keygen
After executing the command you will be prompted to enter a filename and password (optional) for the new key. If you do not enter a filename, the default filename is used id_rsaand id_rsa.pubthe private key is stored in ~/.ssha directory and the public key is stored in .puba file in the same directory.
2. Add the public key to the user managed on the server
in ~/.ssh/authorized_keythe file.
The public key can be added to the target user's authorized_keysfile with the following command:
ssh-copy-id username@remote_host
This will copy the local public key to the target user's file on the remote host ~/.ssh/authorized_keys. If ssh-copy-idcommands are not available, you can copy the public key locally to a authorized_keysfile named , and then copy that file to the remote host with the following command:
cat id_rsa.pub >> authorized_keys
Add permissions

3. Edit configuration file
The system will first check whether there is a corresponding matching private key to log in to the target host. If the corresponding private key is found, the login will proceed automatically, otherwise a password verification window will pop up.

4. Connect using private key
download to desktop