The last article talked about the definition and development history of cryptography, and talked about some basic theories such as diffusion (one bit of plaintext can affect multiple bits of ciphertext) and confusion (complicated correspondence between keys and ciphertext), such as information The three elements of the security system, CIA (confidentiality, integrity, availability), etc., and briefly introduced the classification of cryptography, which can be divided into sequence ciphers and block ciphers according to the plaintext processing method, and can also be classified according to whether the encryption and decryption keys are consistent. For symmetric and asymmetric encryption. Let's talk about symmetric encryption first.
Introduction to Symmetric Encryption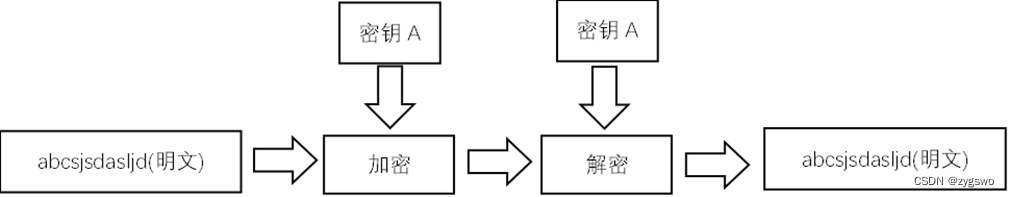
As shown in the figure, the encryption and decryption keys used in symmetric encryption are the same, which also makes it difficult to resist theft and disguise. But with the development of technology, just as the concept of confusion and diffusion proposed by the famous cryptographer Shannon, the relationship between key and ciphertext, plaintext and ciphertext has become more complicated, and the length of the key is getting longer and longer. Symmetric encryption The safety factor is getting higher and higher. After that, algorithms such as DES, 3DES, and AES appeared one after another.
What is DES
Before introducing DES, think about a few questions:
- What are the shortcomings of traditional password dictionaries, shift ciphers and substitution ciphers?
- How does the concept of Shannon confusion and diffusion apply to symmetric encryption and decryption to make it more secure?
- How do you design a scheme that makes it difficult to decipher the ciphertext even if you know the key for the symmetric encryption?
The full name of DES is Data Encryption Standard, which translates to data encryption standard. It is a symmetric encryption algorithm developed by IBM Corporation in the United States, and it is also a block cipher. The plaintext is grouped according to every 64 bits, and the initial key is also 64 bits. The length of the key is 56 bits) A way to form ciphertext after a series of processing, the processing process is shown in the figure below:
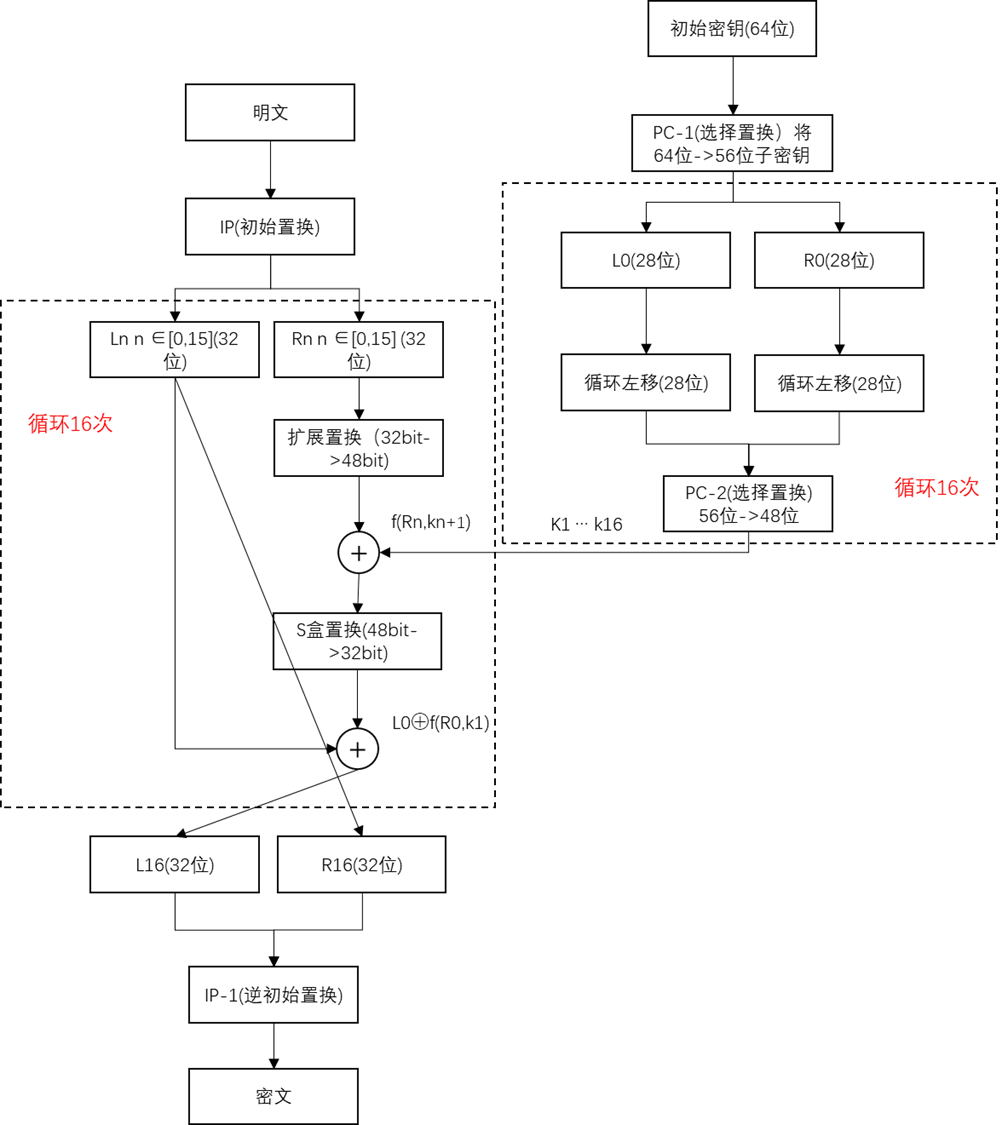
——————————— 2022.12.29 update -------- --------------------------------
DES encryption implementation steps
STEP1 initial replacement
Starting from the initial replacement, what is the initial replacement?
The initial replacement is to replace the characters of the plaintext through an initial replacement table, as shown in the following figure

For example, if the plaintext is 0123456789ABCDEF
, the 64-bit binary plaintext is 0000 0001 0010 0011 0100 0101 0110 0111 1000 1001 1010 1011 1100 1101 1110 1111 and
then refer to this initial permutation table, such as the initial permutation table [0,0] A value of 58 on the , means to replace The position of the last first bit is the 58th position of the binary plaintext. Similarly, the value on the initial permutation table [0,1] is 50, and the value of the 50th bit of the plaintext is replaced, and so on.
Finally, the binary plaintext after the initial permutation is
1100 1100 0000 0000 1100 1100 1111 1111 1111 0000 1010 1010 1111 0000 1010 1010
Why the initial permutation first? What are the benefits of initial permutation?
The purpose of initial permutation is to increase the difficulty of cracking. Only users who have the initial permutation table can correctly encrypt DES plaintext and decrypt ciphertext. Putting it in the first link is to reduce the risk of cracking and increase the difficulty of cracking. Embodies Shannon's concept of confusion.
STEP2 divides 64-bit plaintext into left 32-bit and right 32-bit plaintext
It is convenient for the subsequent 16 rounds of iterative operations, and it is convenient for left and right plaintext XOR operations. It can integrate high-order information into low-order information, which is a bit like the hash operation of hashmap.
STEP3 16 groups of key generation
Subkey generation process:
- Convert key text input into binary text (total 64-bit initial key)
- The 64-bit initial key is converted into a 56-bit subkey by selecting the permutation PC-1. The purpose of selecting permutation is to increase the diffusion and replace the extra digits to facilitate the subsequent 48-bit XOR operation)
- Divided into left and right groups, each with 28 bits
- The left and right groups are shifted to the left at the same time, (note that the 1st, 2nd, 9th, and 16th rounds are shifted to the left by 1 bit each time, and the other rounds are shifted to the left by 2 bits each time, and a total of 28 bits are shifted to the left, that is The length of the left half group) ps: Circular left shift Example: the original value of 10000001 becomes 00000011 after circular left shift.
- Then select and replace PC-2 again, and convert the 56-bit subkey into a 48-bit output.
- Repeat steps 3-5 15 times to generate 16 sets of key outputs.
STEP4 16 encryption operations
—————————————————— Note: After 4.1-4.4, it is collectively referred to as F function operation —————————————————————
4.1 Extended permutation, the The 32-bit plaintext on the right half is expanded into 48 bits in this way
It is convenient for subsequent encryption operations with the key. (The subkey is 56 bits, and the one involved in the operation is 48 bits)
There is also a table for extended permutation, as shown in the figure
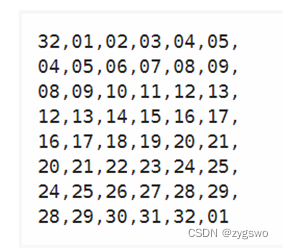
It is not difficult to find from the figure that the second to fifth columns are original plaintext bits, and the first and sixth columns are extended columns.
And also found that the value of each row is not repeated, each column is also.
The extended permutation operation is similar to the initial permutation, but with additions.
Put the original left 32-bit plaintext 1100 1100 0000 0000 1100 1100 1111 1111
into the extended operation table to get: 1110 0101 1000 0000 0000 0000 0110 0101 1001 0111 1111 1111 After
formatting, it is:
111001
011000 000000
000000
011001
011001
011111 111111 (convenient Subsequent S-box operation understanding)
4.2 Perform encrypted XOR operation on the subkey and the 48 bits on the right half that have been extended and replaced in sequence
4.3 S box replacement
In cryptography, S-box (Substitution-box) is the basic structure of symmetric key algorithm [1] to perform substitution calculation. The S-box is used in the block cipher algorithm, which is the only non-linear structure, and the quality of the index of the S-box directly determines the quality of the cipher algorithm. The purpose of S-box permutation is to be able to convert an input with a length of 48 bits into a 32-bit output to facilitate subsequent operations
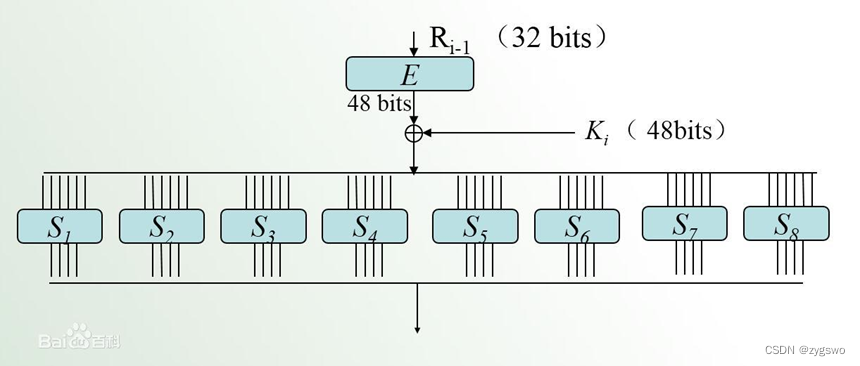
There are 8 S-boxes in total, and each s-box has 6 input bits, but then only 4 output bits.
The S-box sample is as shown in the figure (there are 8 different S-boxes in total). The behavior of the default s-box is the value after the combination of extended bits, and the column is the value of the original bit (four columns in the middle).
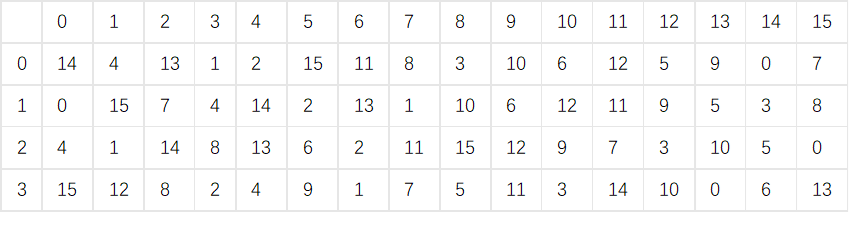
Assume that the input after encrypted XOR operation is 011001, then since the first column and the last column are extension bits, the value of the first and last bit is extracted, which is 01, as the number of rows, which is the second row . The four digits in the middle are the number of columns, 1100 (12), and the value obtained by searching the s box is 9 (1001), and the output is 1001, which means the transformation is realized. The design of the s-box becomes the key to the quality of the algorithm.
4.4 P box replacement
The purpose of p-box replacement is to increase diffusion. Similar to other permutations, there is also a table of P-box permutations.
————————————————————F function ends here———————————————————
4.5 The result of the F function operation XOR with the left half and use it as the right half of the input for the next round.
The purpose of this is to increase confusion
4.6 Use the binary value of the right half of the current round of encryption operation as the left half of the next round of input
4.7 Carry out the next round of encryption until repeated to 16 rounds
STEP5 reverse the initial permutation of the encryption result
The inverse initial permutation is the inverse of the initial permutation. The data block can be restored to its original position after initial permutation and inverse initial permutation.
STEP6 Get the final encryption result
DES decryption implementation steps
The des decryption steps are basically similar to the previous encryption steps, but the 16 sets of keys need to be reversed.
Note: You should also pay attention to the grouping efficiency and the uniformity of the group size when writing the formal code. In addition, you should also pay attention to the length of the encrypted ciphertext, so it is best to use it together with the hash (hash) function. There are certain flaws in the security of this algorithm. After all, the key is only 64 bits, which is not long enough.
————————————————————————————————————— La la la, the end of this article is scattered —————————————————