Data reference: CISP official
Table of contents
- The importance of smart mobile terminals
- Smart Mobile Terminal Security Threats
- Safe use of mobile smart terminals
1. The importance of smart mobile terminals
1. Development of smart mobile terminals
complete ultra-small computer system
- powerful processing capability
- Complete hardware and software system
Can complete more complex processing tasks
- Taking pictures, listening to music, playing games, surfing the Internet, video conferencing, storing documents and business processing

2. Comprehensive information processing platform
Mobile Internet is fully popularized
- Smart mobile terminals penetrate into every aspect of life
Become a comprehensive information processing platform
- Tools for personal affairs and entertainment
- Tools for Mobile Law Enforcement, Mobile Office and Mobile Commerce

3. The importance of mobile terminals - data storage
-
Hardware information : the mobile terminal stores various hardware information, such as processor model, memory capacity, storage space, etc. This information is very important for the proper functioning and performance optimization of the device.
-
Operating system data : The operating system (such as iOS, Android, etc.) on the mobile terminal stores system files, drivers, and configuration information. These operating system data are responsible for managing various functions of the device and ensuring the proper functioning of the operating system.
-
Application software : Various application software installed on the mobile terminal store relevant data, settings and configuration information, etc. These apps include social media apps, email clients, games, etc., which store users' personal preferences, login credentials, and other related data.
-
User data : User data is one of the most important mobile terminal data, including photos, videos, documents, contacts, calendar events, etc. This data has high personal value and privacy, so it must be properly protected and backed up.

4. The importance of mobile terminals - identification basis
The popularity of mobile smart terminals provides support for identity authentication
- Maturity of technology and reduction of hardware cost
Multiple authentication methods are supported
- Entity owned: mobile phone number (short message)
- Entity features: fingerprints, facial recognition, irises, etc.

2. Mobile Smart Terminal Security Threats
1. Security Threats and Countermeasures
Service carrying platform
- A large amount of storage of personal information and important data, the key target of attackers
- There are security holes in the operating system and a large number of third-party software, which become the attack targets of viruses, worms and Trojan horses, etc.
Typical Security Threats
-
Pseudo base station : A pseudo base station is a device that simulates a real mobile network base station, which can trick mobile terminals into connecting to it and steal communication data. Attackers can use fake base stations to monitor, hijack communications, and conduct phishing attacks.
-
Lost and damaged devices : Loss or damage to mobile terminals can lead to sensitive data disclosure and unauthorized access. Third parties may be able to access personal information stored on the device if the data is not properly secured (such as with a screen lock password or encryption).
-
System Vulnerabilities : Vulnerabilities in mobile operating systems and applications may be exploited by hackers to enter mobile terminals through malware or attack means. These vulnerabilities can lead to data leakage, remote control, denial of service and other issues.
-
Malicious applications (APP ): Malicious APPs can be spread by fraud or hidden in legitimate APPs, and perform malicious activities on mobile terminals and user data. These malicious apps may steal sensitive information, monitor user activity, or install other malware.
- .....
2. Fake base station attack
Working mechanism of mobile signal mechanism (principle)
- Cellular networking : The mobile communication system adopts cellular network networking, which divides the communication area into multiple cells (cells), and each cell is covered by a base station. The overlapping area between base stations forms the boundary for seamless handover.

- GSM one-way authentication : GSM is a mobile communication standard, which uses a one-way authentication mechanism. Before communication is established, the terminal needs to authenticate itself by sending an authentication request to the network. The network will authenticate the terminal and respond to the authentication result, and only the authenticated terminal can successfully establish a communication connection.
- The terminal automatically searches for the base station with the strongest signal : the mobile terminal determines the best communication base station by monitoring the signal strength of the surrounding base stations. The terminal will automatically select the base station with the strongest signal strength for communication, and conduct signal detection regularly to ensure that it is always connected to the best base station.

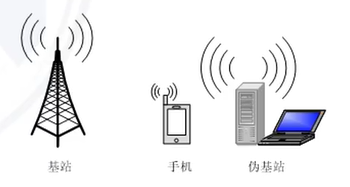
Countermeasures against fake base station attacks
- Pay attention to the situation of the mobile phone signal falling back to 2G, the fake base station can only disguise the 2G signal
- SMS is unsafe information, please be careful to access all links in SMS, even if it is identified as sent by the operator
- "Safety accounts, remittances, arrears, money laundering" involving funds need to be paid attention to
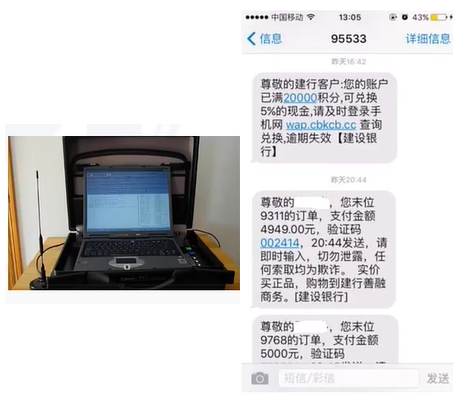
3. Spam
source of spam
- Mobile phone text messages: corporate greetings, advertising text messages, fraudulent text messages
- App message: imessage message, App push
Responses
- Mobile spam filtering
- imessage off or set to filter unknown senders
- third-party filtering software

4. Equipment lost or stolen
Security Risk
- Insufficient access control measures, illegal operations (transfer, loan, etc.)
- data loss risk
- Risk of SIM card being used illegally
security measures
- Mobile Access Control Mechanism
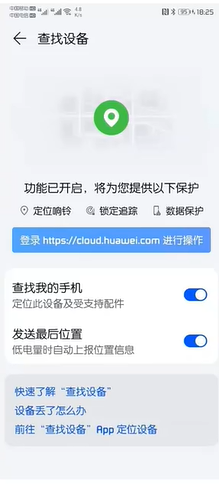
- Turn on the positioning and "find device" functions to clear data
- Set SIM card lock
5. Equipment maintenance and old mobile phones
Security Risk:
- The data deleted in the mobile terminal can be restored
Case: the famous Yanzhaomen and Apple Yanzhaomen

Security measures:
- Official channels, maintenance mode, data shredding
6. System loopholes and excessive permissions
System Vulnerabilities
- Mobile terminal operating systems and APP applications are all software, and there will be loopholes
Excessive permissions
- The application has applied for permissions that should not be needed, such as: positioning, taking pictures, microphones, reading contacts...
7. Malicious apps
Security Risk
- Piracy, Illegal Information Gathering
- Repackage and encapsulate malicious code
security measures
- Regular app store download
- App Security ID

3. Safe use of mobile smart terminals
1. Visit unknown websites with caution
There are pitfalls on the web page
- fishing
- hanging horse
- collect message
If you can't confirm the safety, don't visit at will
- Do not click on links from untrustworthy or unknown sources. These links may lead you to malicious sites where phishing attacks or malware can be planted.

2. After the QR code is risk
- QR codes are not intuitive to users, please confirm before scanning

3. Do not connect to unknown network
One-way authentication of wireless networks is risky
- Risk of man-in-the-middle spoofing attacks
- information leakage

4. Do not click on unknown links
- The link target address may be risky

5. Lock screen access control needs to be set
- Protect data and reduce security risks from device loss

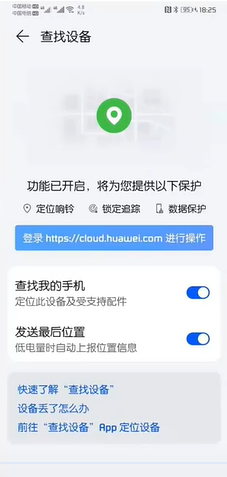
6. Turn on the device search function
- Device lost search, data erasure
- Enable SIM card PIN code
7. Data should be backed up regularly
- Avoid loss of important data