1. Data security has become the core of protection, and storage security protection cannot be compromised
1. As the core assets of enterprises, data urgently needs to be protected, and data security has become the core of cyberspace protection
2. The state attaches great importance to the data security of key information infrastructure, and storage security has become the focus of audits
2. Storage security is a key part of data security, and a complete security system should be established
▶ Storage security is a key part of data security
1. Protect important data
2. Prevent Data Leakage
3. Prevent data loss
4. Compliance requirements
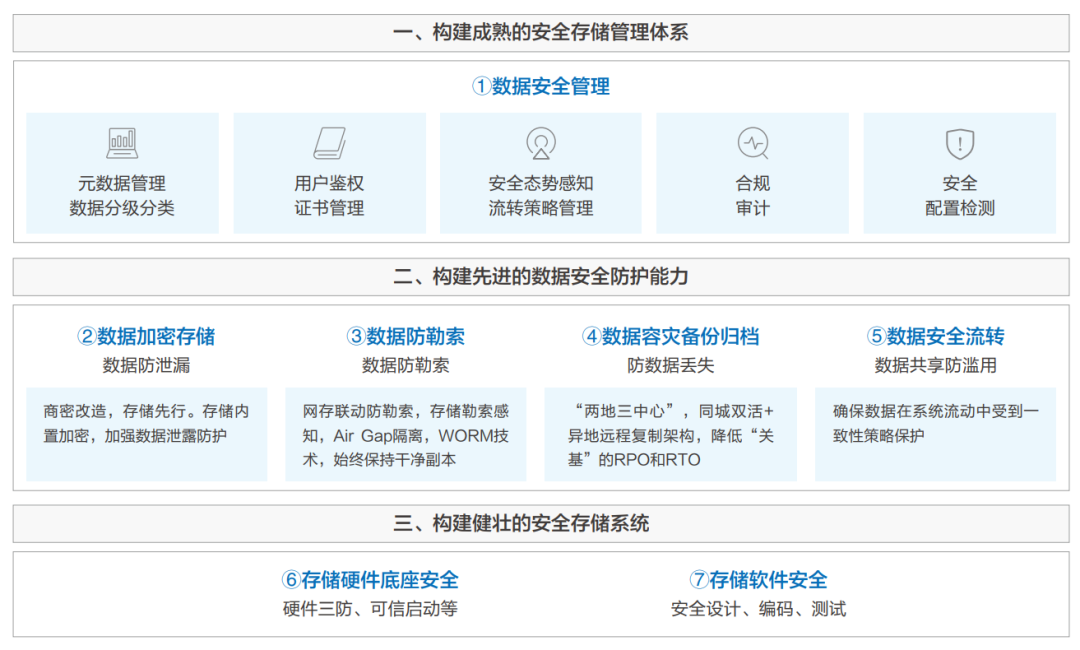
▶ How to establish a complete safe storage system correctly?
Build an effective security storage system from the following three aspects:
- Organizational management system
- Storage protection capabilities
- Storage system security
3. Build a defense system based on endogenous security capabilities to create safe and reliable advanced data storage
▶ Build a defense-in-depth storage security system through endogenous security capabilities
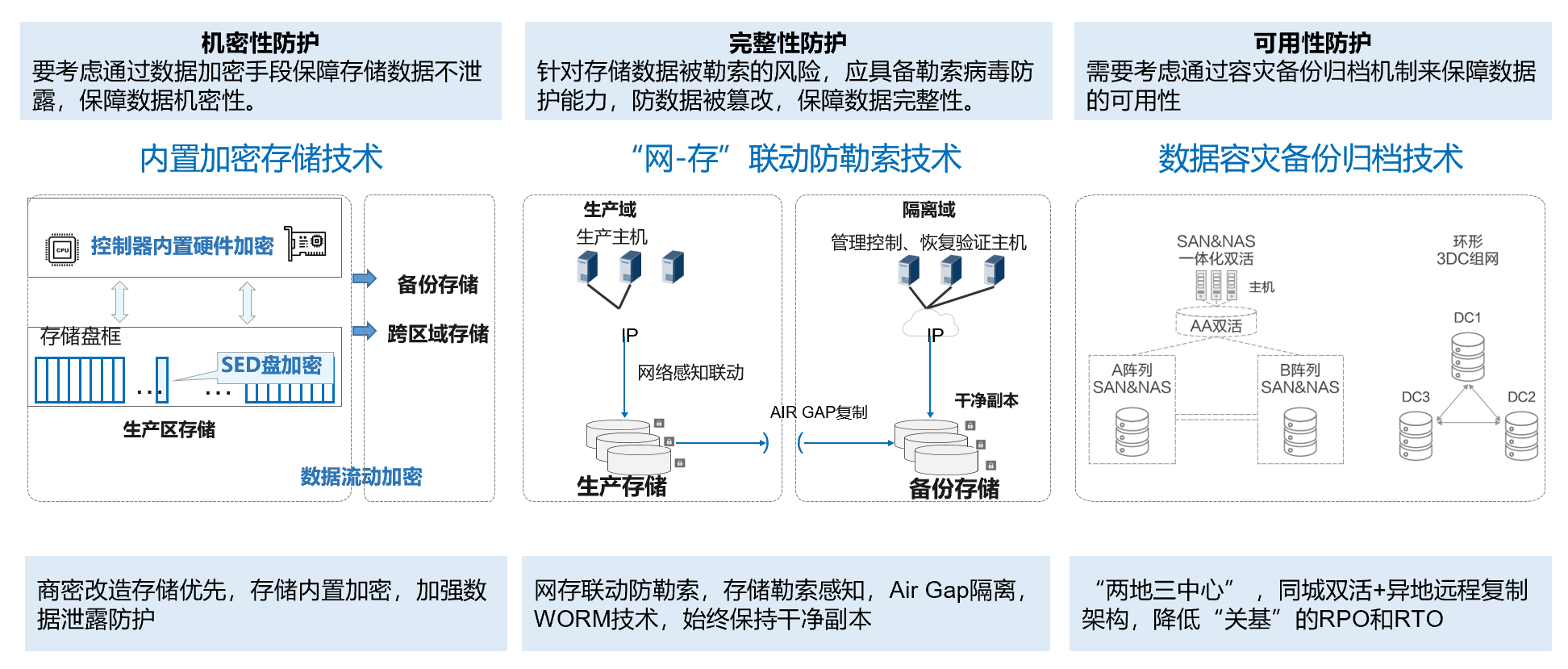
How to use secure storage technology to enhance the data security protection capability of the entire system by an order of magnitude can be viewed from the "three characteristics" of data security, namely confidentiality, integrity, and availability.
First: Large-scale information systems need to use dedicated storage systems to store massive amounts of data. Enterprise-level storage products organize a large number of storage hardware into virtualized storage resource pools to provide high-performance, high-availability, and high-reliability storage services.
Second: Using secure storage technology to resist the risk of ransomware requires four functions, namely "Air Gap", "Anti-tampering", "Detection Analysis" and "Data Encryption".
Third: The integrated disaster recovery system to be built needs to have the core capabilities of data security and reliability, unified security and compliance, service-oriented operation and maintenance, and green, low-carbon and energy-saving.
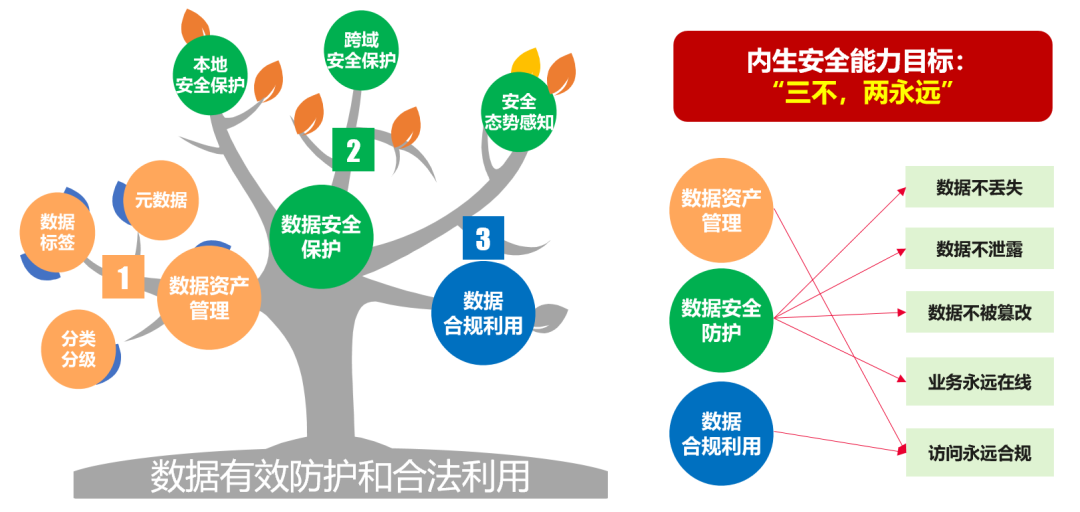
▶ Create safe and reliable advanced data storage based on the whole data life cycle
First, for the security and reliability of data storage, Huawei provides a full-stack, multi-layer linkage data security solution based on the entire data lifecycle, achieving the goal of "three nos and two forever" in data security.
Second, in terms of ensuring data confidentiality, the storage device fully supports the national secret commercial encryption algorithm, and uses the national secret certified Kunpeng chip to enable acceleration and provide an end-to-end encryption solution.
Third, to ensure data integrity, especially for extortion attack scenarios, Huawei provides the industry's first network-storage linkage and end-to-end anti-extortion solution.
Fourth, in terms of data availability, Huawei provides a full set of disaster recovery backup solutions including OceanProtect backup all-in-one machine, OceanProtect dedicated backup storage, and Blu-ray archive storage, and uses OceanCyber data security all-in-one machine to take care of the entire data life cycle from disaster recovery to backup Safe storage ensures data security and availability.
The content is excerpted from: https://mp.weixin.qq.com/s/62cjFdT1hW2JvxZmL7aNGQ