1 Introduction
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) penetration testing , malware analysis and security assessment framework capable of performing static and dynamic analysis. MobSF supports mobile application binaries (APK, XAPK, IPA, and APPX) as well as compressed source code, and provides a REST API for seamless integration with CI/CD or DevSecOps pipelines. Dynamic analyzers help you perform runtime security assessments and interactive instrumentation tests.
Docker does not support dynamic analysis if deployed using Docker.
GitHub address:
https://github.com/MobSF/Mobile-Security-Framework-MobSF
2. Required environment
This article takes Windows as an example
1. Install Git (example version Git 2.35.1)
2. Install Python 3.8-3.9 (example version Python 3.8.10)
3. Install JDK 8+ (example version JDK 1.8.0_172)
4. Install Microsoft Visual C++ Build Tools
5. Install OpenSSL (non-light)
6. Install wkhtmltopdf, and add the binary file path containing wkhtmltopdf to the environment variable PATH
3. Installation and deployment
1. Download the latest project
git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF.git
2. Jump to the project directory
cd Mobile-Security-Framework-MobSF
3. Execute the installation
setup.bat
Note: Windows users, before running setup.bat, please close all folders opened by MobSF and text editors opened by MobSF, because these will cause permission errors and interrupt the installation.
4. Run
1. Execute startup in the root directory of the MobSF project
run.bat 服务器IP:端口号
例如 run.bat 127.0.0.1:8000
2. Open the browser and visit the address http://localhost:8000/
As shown in the figure: MobSF starts successfully.

5. Operation
5.1. Static analysis
1. Click the upload and analyze button

Select the application to analyze, for example ApiDemos-debug.apk

2. After the file is uploaded, it is being analyzed

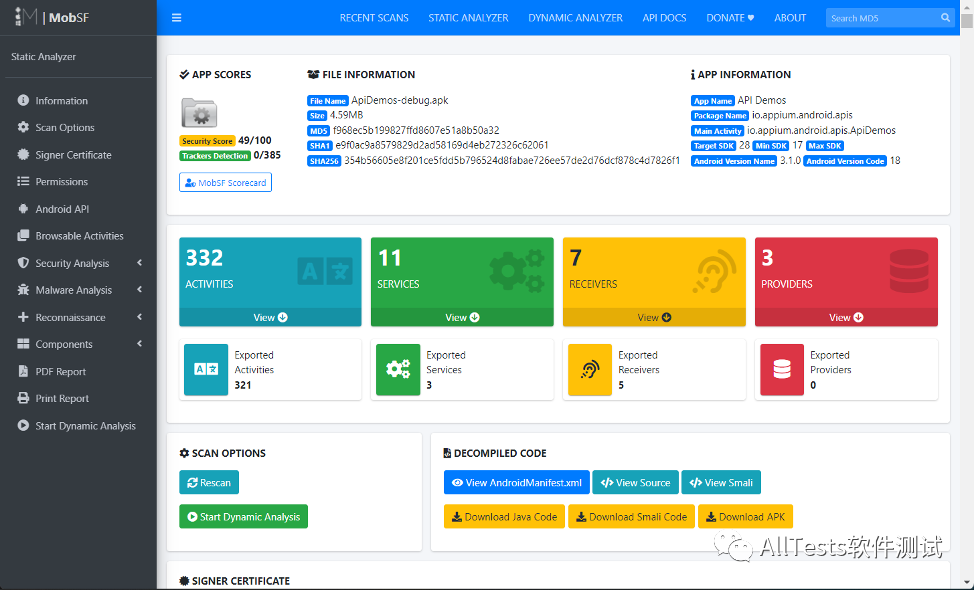
3. Static analysis report after analysis
Reports list information, signer certificates, permissions, security analysis, malware analysis, reconnaissance, PDF reports, print reports, dynamic analysis reports, and more.
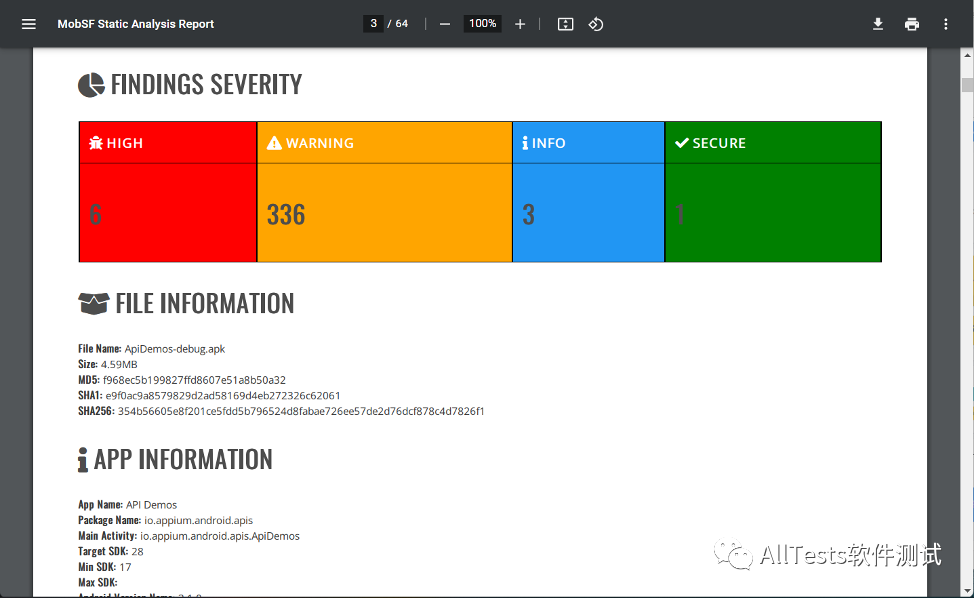
PDF report.
4. Click Security Scorecard
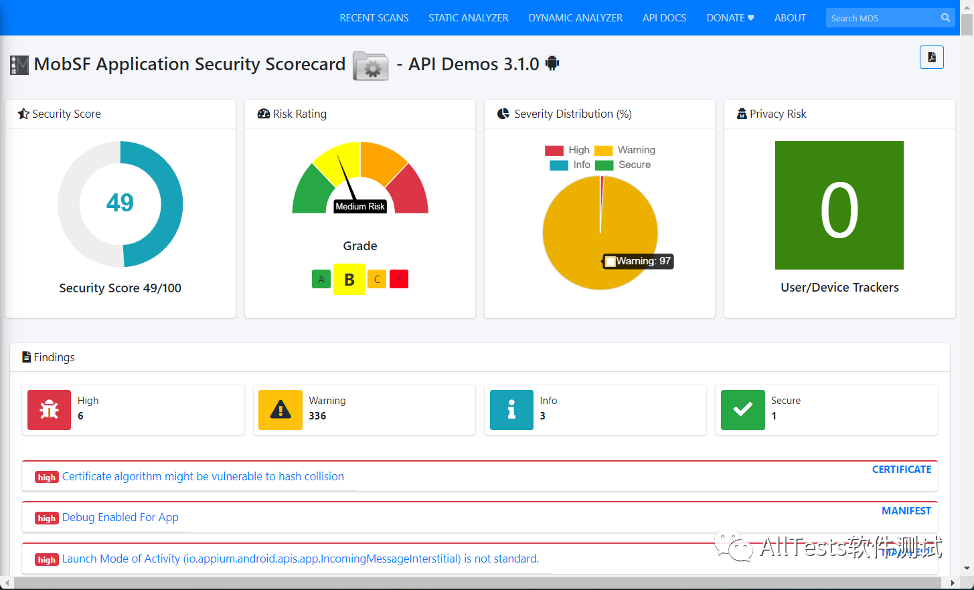
You can see security scores, risk ratings, severity distributions, privacy risks, and more.
5.2. Dynamic Analysis
1. Click to enter DYNAMIC ANALYZER
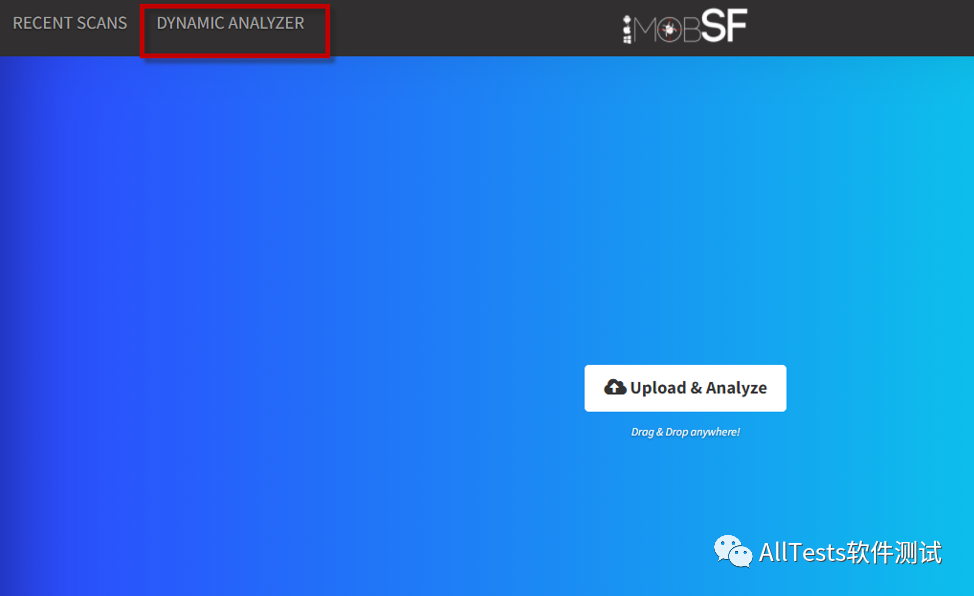
If an error is reported: Android Runtime not found!
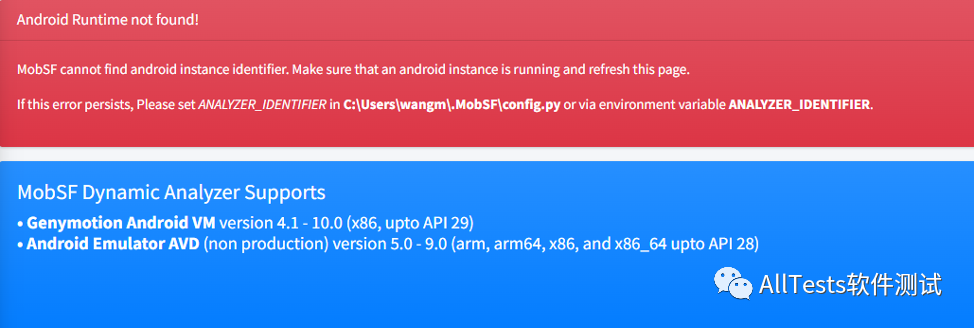
Solution: Open and run the emulator (such as Genymotion).
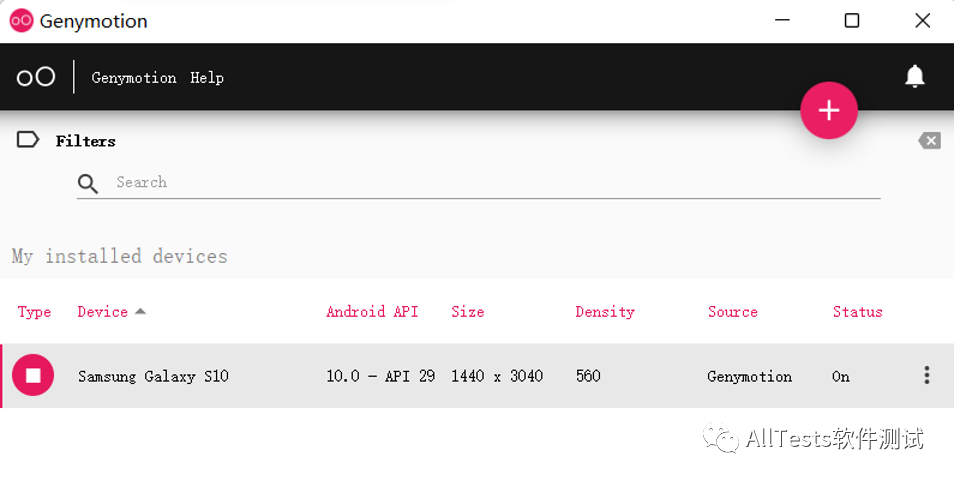

Just refresh the page again.

2. Perform dynamic analysis in available applications, or perform dynamic analysis in applications on the device
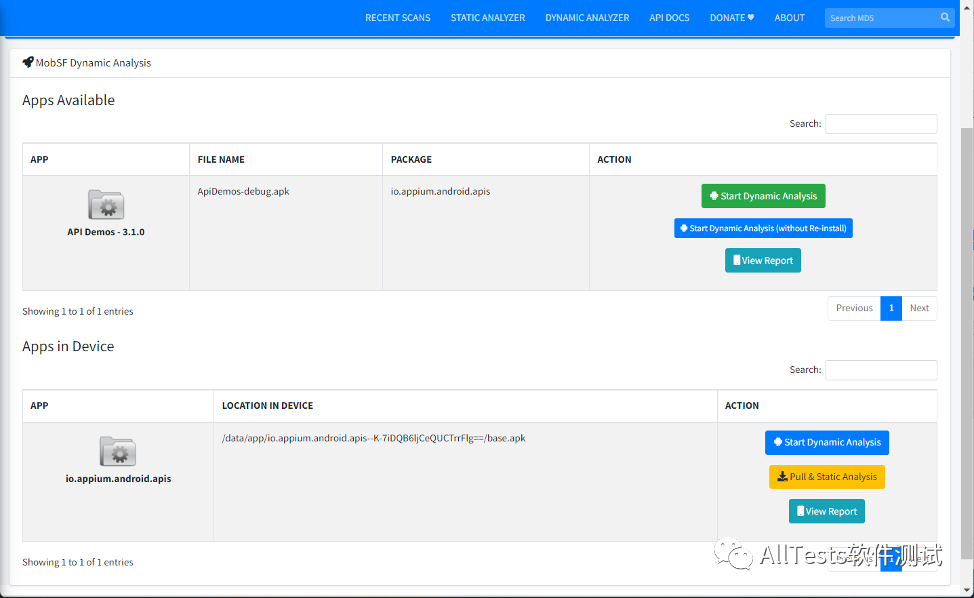
3. For example, in the available application, start dynamic analysis
Tap to display the screen, then tap Start Detection.
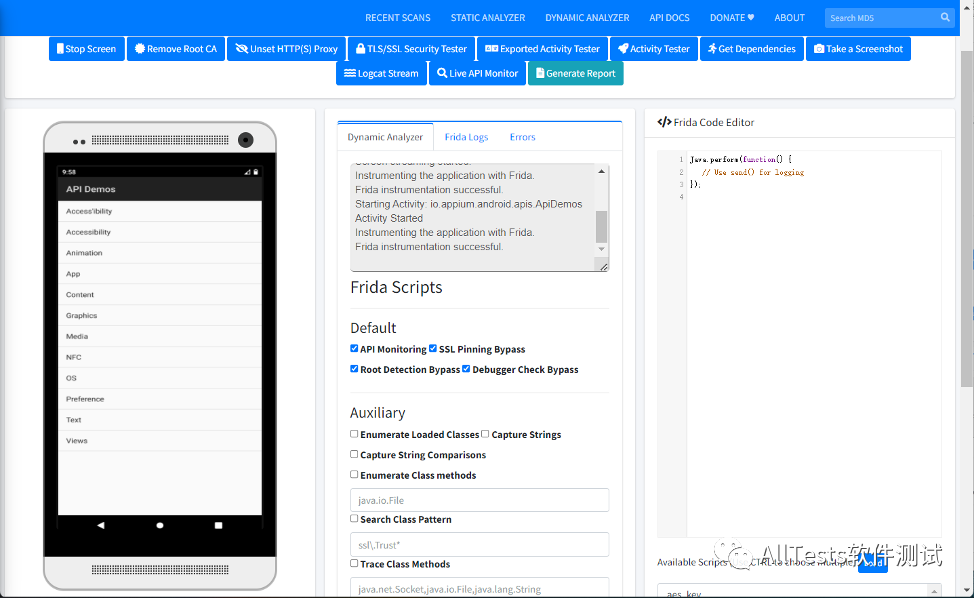
Conduct TLS/SSL security testing, exported activity testing, activity testing, and more.


Click Logcat Stream to view log information in real time.
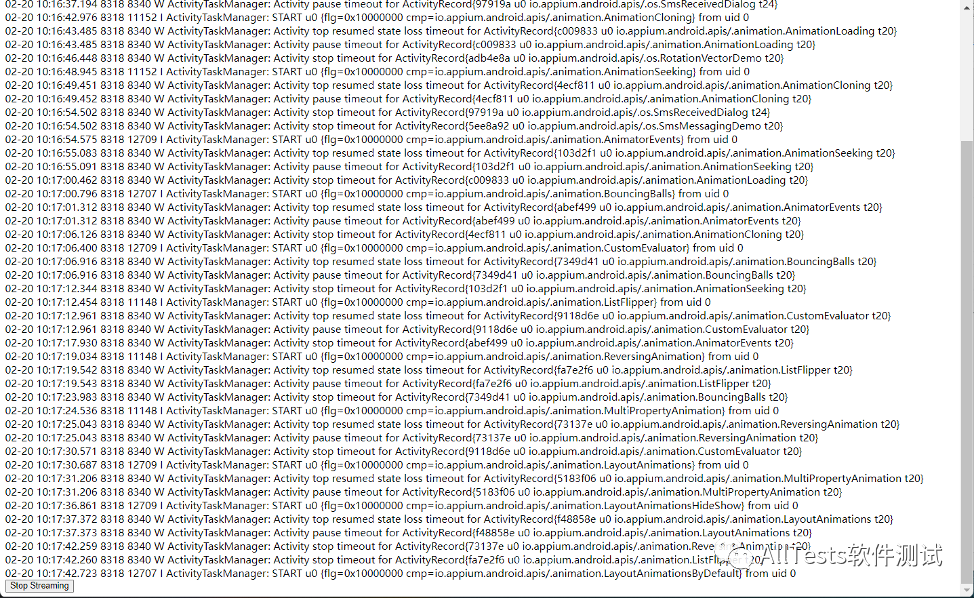
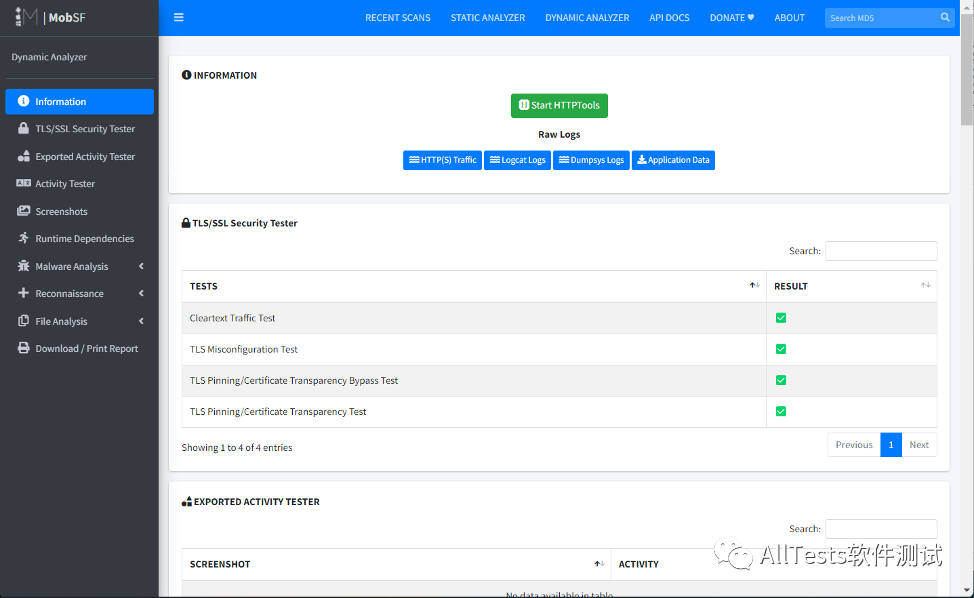
4. Click Generate Report
Dynamic analysis reports list information, TLS/SSL security tests, exported activity tests, activity tests, screenshots, runtime dependencies, malware analysis, reconnaissance, file analysis, download/print reports, and more.
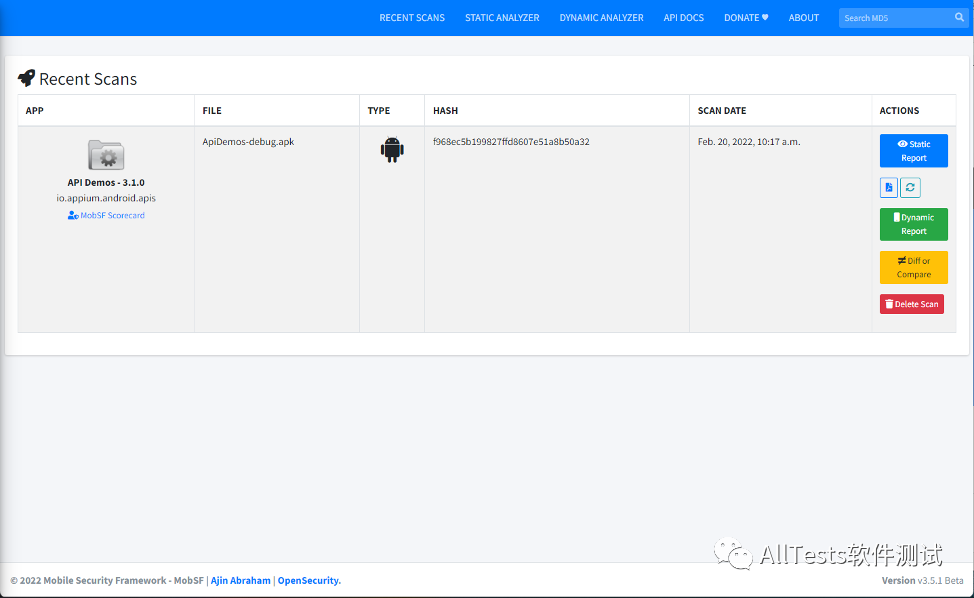
5.3, recent scan
1. Click to enter RECENT SCANS
2. View the application information of historical scans, and you can perform operations such as viewing static reports, viewing dynamic reports, differences or comparisons, deleting scans, and viewing PDFs
5.4、REST API
1. Click to enter API DOCS
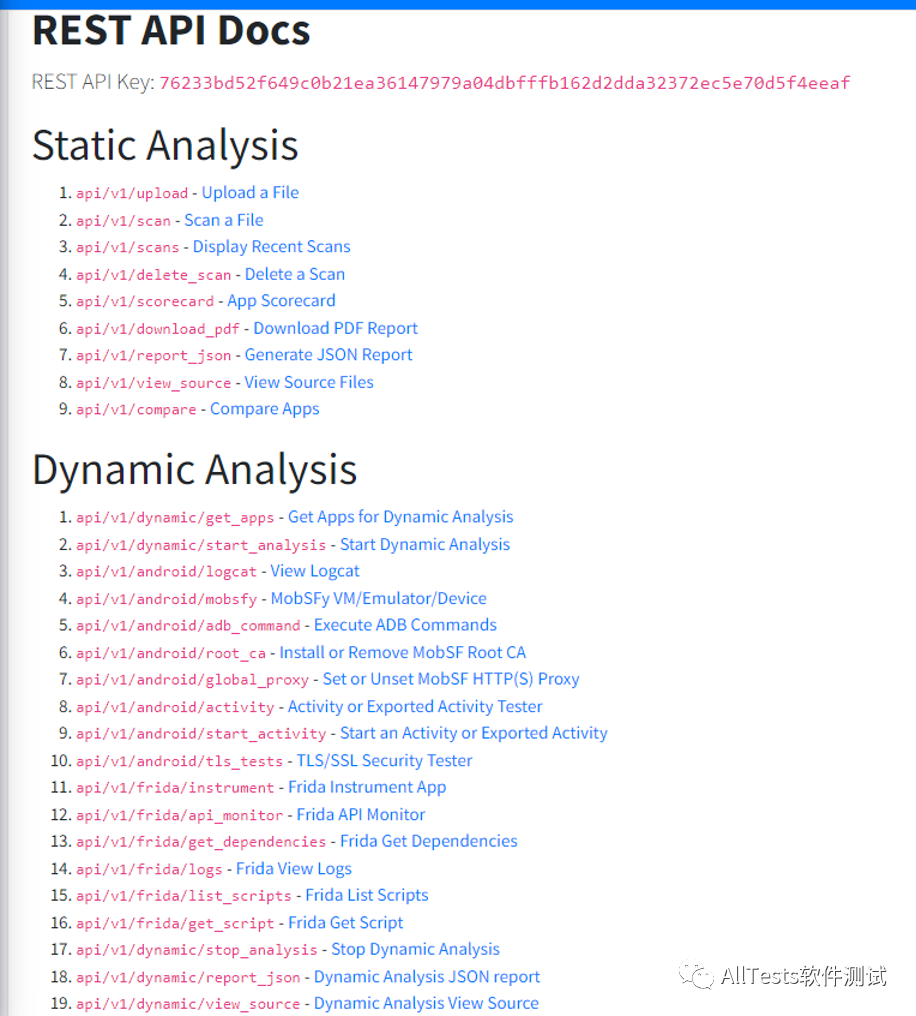
2. You can view the provided REST API documents to facilitate seamless integration with CI/CD or DevSecOps pipelines
API methods are provided for static analysis and dynamic analysis.
3. For example, view the latest scanning method api/v1/scans for static analysis
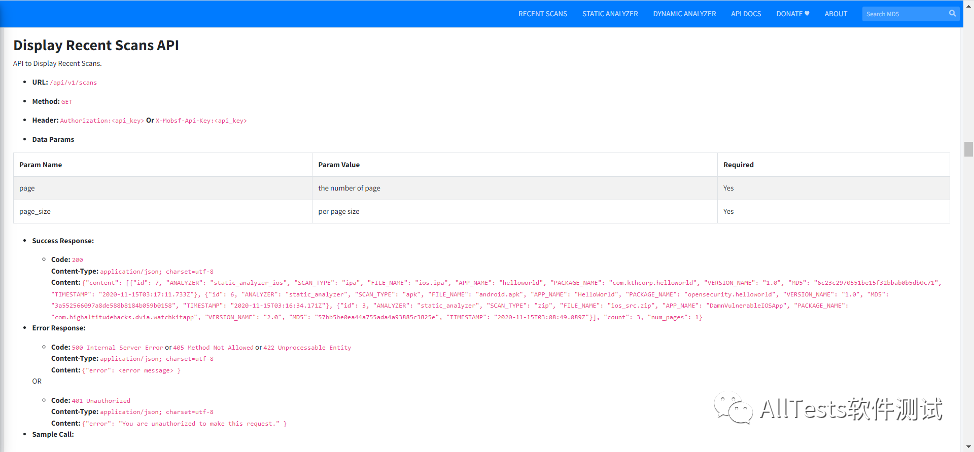

According to the provided example, make a request on Postman, pay attention to adding key information in the request header, as shown in the figure, the request is successful.
Other API methods can be requested according to the provided examples.


1 Introduction
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) penetration testing , malware analysis and security assessment framework capable of performing static and dynamic analysis. MobSF supports mobile application binaries (APK, XAPK, IPA, and APPX) as well as compressed source code, and provides a REST API for seamless integration with CI/CD or DevSecOps pipelines. Dynamic analyzers help you perform runtime security assessments and interactive instrumentation tests.
Docker does not support dynamic analysis if deployed using Docker.
GitHub address:
https://github.com/MobSF/Mobile-Security-Framework-MobSF
2. Required environment
This article takes Windows as an example
1. Install Git (example version Git 2.35.1)
2. Install Python 3.8-3.9 (example version Python 3.8.10)
3. Install JDK 8+ (example version JDK 1.8.0_172)
4. Install Microsoft Visual C++ Build Tools
5. Install OpenSSL (non-light)
6. Install wkhtmltopdf, and add the binary file path containing wkhtmltopdf to the environment variable PATH
3. Installation and deployment
1. Download the latest project
git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF.git
2. Jump to the project directory
cd Mobile-Security-Framework-MobSF
3. Execute the installation
setup.bat
Note: Windows users, before running setup.bat, please close all folders opened by MobSF and text editors opened by MobSF, because these will cause permission errors and interrupt the installation.
4. Run
1. Execute startup in the root directory of the MobSF project