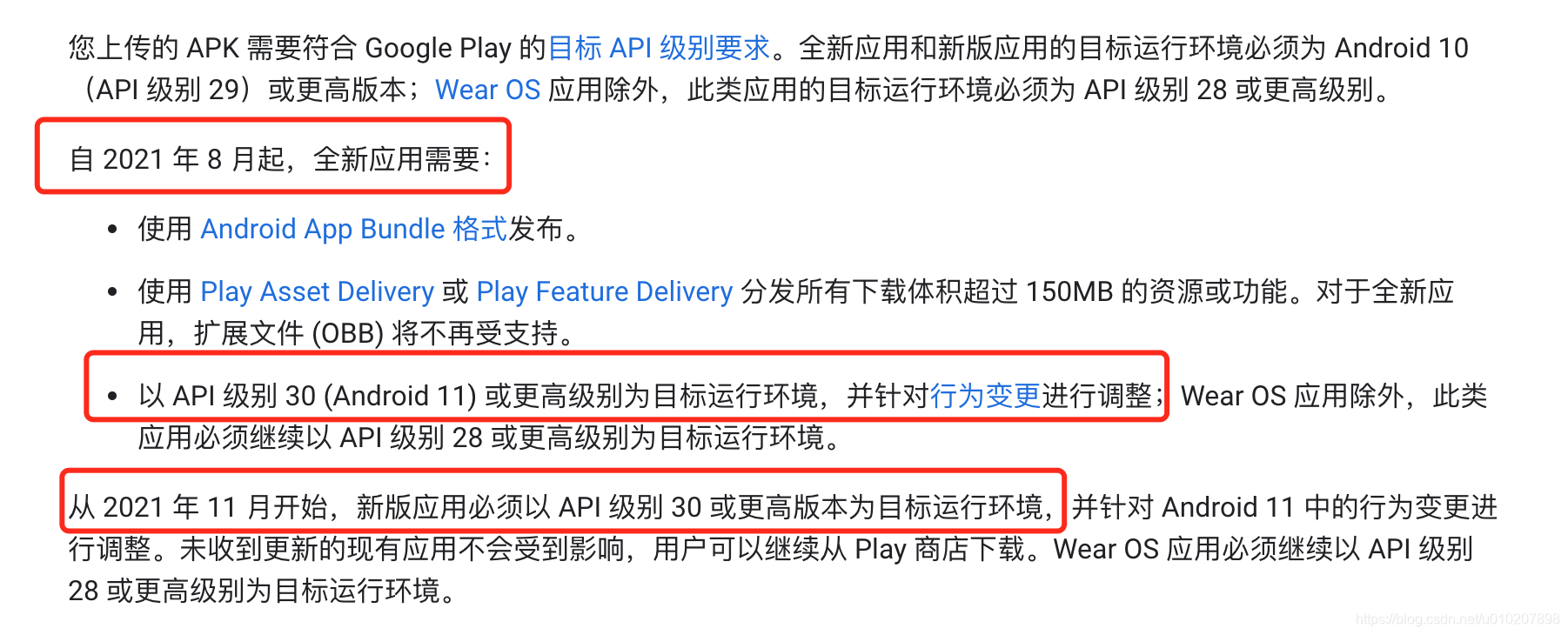
Android 10 migration Android 11
official address: https://developer.android.com/distribute/best-practices/develop/target-sdk?hl=zh-cn#prepie
Mainly 2 parts privacy and security
隐私权
Starting with Android 11, apps that use the partitioned storage model can only access their own application-specific cache files.
Starting with Android 11, apps cannot create their own app-specific directories on external storage. To access the directories provided by the system for your application, call getExternalFilesDirs().
Enforce partitioned storage:
Access to external storage directories is limited to app-specific directories and certain types of media that the app has created.
**什么是应用专属存储空间?**
Store files used only by the application, which can be stored in a dedicated directory in the internal storage volume or in other dedicated directories in the external storage space. Use a directory in internal storage to hold sensitive information that other apps should not have access to. (Only the app itself can access)
Access from the internal storage space, you can use the getFilesDir() or getCacheDir() method; access from the internal storage space does not require any permissions Other applications cannot access the file after the app is uninstalled. Access from the external storage space
, You can use the getExternalFilesDir() or getExternalCacheDir() method. If the app is running on a device running Android 4.4 (API level 19) or higher, access from external storage does not require any permissions. Other apps can access it. Files will not be deleted after the app is uninstalled. remove
The app uses the partitioned storage model to save application-specific files, media files, and other types of files to its own location, and access these files through these locations.
Android 10 apps can still request the requestLegacyExternalStorage attribute. The requestLegacyExternalStorage flag is ignored when the app is updated to target Android 11)
Automatically reset permissions
The system automatically resets an app's sensitive permissions if the user has not interacted with the app for several months. This setting doesn't affect most apps. If your app runs primarily in the background without user interaction, you may consider asking the user to disable automatic resets
**什么是自动重置?**
≥ The system of android11 has not been used for several months, the system will automatically reset the runtime sensitive permissions that the user has granted to the application to protect user data. This has the same effect as a user viewing permissions in system settings and changing the app's access level to deny. It is thoughtful and applies every time when I use it.
Access to background location information
≥30API (≥Android11)
The application must request separately for the foreground location information acquisition permission and the background location information acquisition permission. Background location permission can only be granted in the app settings, not through the runtime permissions dialog.
Package Visibility
When an app queries the list of apps and services installed on the device, the system filters the returned list. If you use text-to-speech or speech recognition services, you need to add
elements for these services in the manifest file
. In other words, in Android 11, if you want to get information about other apps, such as package name, name, etc., you cannot get it directly Yes, you must add elements to the manifest file to tell the system which application information or type of application you want to obtain
安全性
Compressed resource.arsc files are no longer supported
Apps targeting Android 11 (API level 30) or higher
will fail to install if they contain a compressed resources.arsc file or if this file is not aligned on 4-byte boundaries.
https://developer.android.com/about/versions/11/behavior-changes-11?hl=zh-cn#change-details_3
Now requires APK Signature Scheme v2
Android 11 (API level 30) must be signed with APK Signature Scheme v2 or higher. Users cannot install or update apps signed only with APK Signature Scheme v1 on devices running Android 11 Note: To support devices running older versions of Android, in addition to signing your APK with APK Signature Scheme v2 or higher, you It should also continue to be signed using APK Signature Scheme v1.
Firebase
≥Android11 (API level 30), Firebase JobDispatcher and GcmNetworkManager API calls are disabled on devices running Android 6.0 (API level 23) or higher . For more information about migration, please refer to the official documentation, the following is the address
Firebase JobDispatcher Migrating to WorkManager
(https://developer.android.com/topic/libraries/architecture/workmanager/migrating-fb?hl=zh-cn)
from GCMNetworkManager Migrating to WorkManager
(https://developer.android.com/topic/libraries/architecture/workmanager/migrating-gcm?hl=zh-cn)
These two APIs are not used in China, and are mainly used for background tasks. The official alternative is WorkManager, which is available in China and belongs to the jetpack component. It is mainly used for scheduling and executing deferred background work.
Device-to-device file transfer
If your app is ≥ Android 11 (API level 30), you cannot
disable device-to-device migration of app files using the allowBackup attribute. This feature is automatically enabled.
However, even if your app ≥ Android11 (API level 30), you can disable cloud backup and restore of app files by setting the allowBackup property to false ## OnSharedPreferenceChangeListener's callback changes
if your app ≥ Android11 (API level 30 ), now every time Editor.clear is called, the OnSharedPreferenceChangeListener.onSharedPreferenceChanged callback is called back with a null key.
Restrict non-SDK interfaces.
For apps targeting API level 30, non-SDK interfaces are not recommended as some of them are now blocked. For a complete list of blocked non-SDK
interfaces, see Non-SDK interfaces currently blocked in Android 11.
Non-SDK Interface Restrictions
Android 11 includes an updated list of restricted non-SDK interfaces (based on collaboration with Android developers and the latest internal testing). Before restricting the use of non-
SDK interfaces, we do our best to ensure that there are public alternatives available.
If you are not sure whether your application uses a non-SDK interface, you can test the application to confirm. If your app relies on non-SDK interfaces, you should start planning to migrate to SDK alternatives. However, we know that some apps have
valid use cases for using non-SDK interfaces. If you can't find an alternative to a feature in your app that doesn't require a non-SDK interface, you should request that a new public API be added.
For more information about the changes in this Android release, see Updates Restricting Non-SDK Interfaces in Android 11. See Restrictions on Non-SDK Interfaces for comprehensive details on non-SDK interfaces.
heap pointer mark
The heap pointer has a non-zero mark in the most significant byte (MSB). Apps that use pointers incorrectly, including
those that modify the MSB, will now crash or experience other issues. This is
a required change to support future ARM Memory Tag Extensions (MTE) enabled hardware. For more information, see the marked pointer
(https://source.android.com/devices/tech/debug/tagged-pointers?hl=zh-cn)
To disable this feature, see allowNativeHeapPointerTagging (https://developer.android.com/guide/ topics/manifest/application-element?hl=zh-cn#allowNativeHeapPointerTagging) manifest document
Updates to message boxes
Custom message boxes from the background are blocked. For security reasons and to maintain a good user experience, if the message box containing the custom view is sent from the background by an app targeting Android 11 or
later , these message boxes are blocked.
Note : Custom Toasts cannot pop up in the background (note the restrictions: background, custom).
If it is in the background, only native Toasts can pop up. If it is not in the background, a custom Toast can pop up. Toast.getView() Toast.setView() method is deprecated and now returns null
//The following is a custom Toast display text + picture Toast, has been tested
public static void showImageToas(Context context,String message){
View toastview= LayoutInflater.from(context).inflate(R.layout.toast_image_layout,null);
TextView text = (TextView) toastview.findViewById(R.id.tv_message);
text.setText(message); //要提示的文本
Toast toast=new Toast(context); //上下文
toast.setGravity(Gravity.CENTER,0,0); //位置居中
toast.setDuration(Toast.LENGTH_SHORT); //设置短暂提示
toast.setView(toastview); //把定义好的View布局设置到Toast里面
toast.show();
}
Message Box Callback
If you want to be notified when a message box (text message box or custom message box) appears or disappears, use the addCallback() method added in Android 11.
Toast message box API changes
Apps that target Android 11 or higher will see the following side effects for toast boxes:
The getView() method returns null.
The return values of the following methods do not reflect actual values, so you should not rely on them in your application:
getHorizontalMargin()
getVerticalMargin()
getGravity()
getXOffset()
getYOffset()
The following methods are no-ops and should not be used by your application They:
setMargin()
setGravity()
connect
Apps targeting Android 11 must now have the Manifest.permission.WRITE_APN_SETTINGS privilege to read or access the telephony provider APN database. Attempting to access the APN database without this permission will generate a security exception.
So the question is, what is APN?
Refers to a network access technology, which is a parameter that must be configured when surfing the Internet through mobile phones. APN configuration parameters include name, operator number, APN access point, etc.
Accessibility Services
**在清单文件中声明与 TTS 引擎的交互**
Due to changes to package visibility, apps targeting Android 11 that interact with the text-to-speech (TTS) engine need to add the following
elements to their manifest files:<queries> <intent> <action android:name="android.intent.action.TTS_SERVICE" /> </intent> </queries>
**在元数据文件中声明“无障碍”按钮使用情况 **
Starting in Android 11, your accessibility service cannot declare at runtime that it is associated with the system's Accessibility button. If you attach AccessibilityServiceInfo.FLAG_REQUEST_ACCESSIBILITY_BUTTON to
the flags property of the AccessibilityServiceInfo object, the framework will not pass the Accessibility button callback event to your service.
To receive accessibility callback events in an accessibility service, declare your service's association to the Accessibility button using an accessibility service metadata file. Add the flagRequestAccessibilityButton value in the definition of the accessibilityFlags property. A common location for an accessibility service metadata file is res/raw/accessibilityservice.xml.
camera
The media intent operation requires the system default camera
Starting with Android 11, only the pre-installed system camera app can respond to the following intent:
android.media.action.VIDEO_CAPTURE
android.media.action.IMAGE_CAPTURE
android.media.action.IMAGE_CAPTURE_SECURE
if more than one pre-installed system camera app is available , a dialog is displayed allowing the user to select an app. If you want your app to use a specific third-party camera app to capture pictures or video on its behalf, you can
make those intents explicit by setting the package name or component for the intent