#01 Basic concept of VPC
(1) VPC: Private network, a user-defined private network on the cloud.
(2) vSwitch: Switch, the basic network device that forms the VPC. The switch can connect to different cloud resources. When creating a cloud resource in the VPC, you must specify the switch where the cloud resource is connected.
(3) vRouter: router, as the hub of the private network, can connect to each switch of the vpc, and is also a gateway device connecting the private network and other networks; the router forwards network traffic according to the routing entries.
(4) RouterTable: Routing table, a list of routing entries managed on the router.
(5) RouterEntry: Routing entry, which defines the next-hop address of the network traffic leading to the specified target network segment. Routing entries include system routing and custom routing.
## #02 VPC configuration process
Create VPC-"Create Subnet-"Configure Routing-"Security Configuration-"Connectivity Test
## #03 Create a VPC
(1) Create a VPC: region, name, ipv4/6 network segment, resource group.
(2) Create a switch: name, availability zone, ipv4/6 network segment.

## #04 Traditional Network
The traditional network is a distributed network from the beginning without a central control node. Each device in the network learns the reachability information of the network through word of mouth, and each device decides how to forward it. This directly leads to the lack of an overall concept and the inability to regulate traffic from the perspective of the entire network. .
Because it is word of mouth, it is necessary to use the language that everyone knows, which is the network protocol. Each equipment supplier cannot develop the protocol casually by itself, otherwise different manufacturers will have their own opinions, and the network will still be unreachable. With this in mind, global organizations such as the IETF were born. The RFC is the law of network protocols, which is equivalent to international law. All equipment suppliers can basically guarantee the normal operation of the entire network world by acting in accordance with international law.
## #05 Network Virtualization
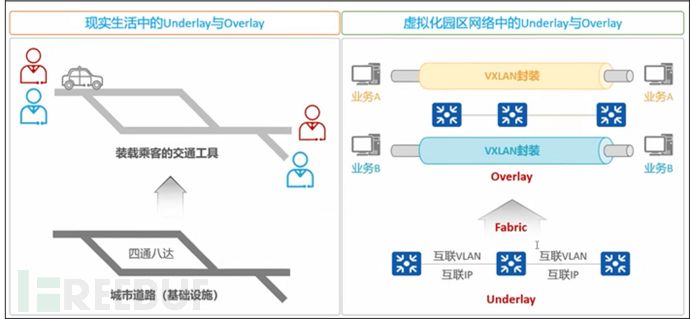
Network virtualization is the transformation of previously hardware-based networks into software-based networks. As with all forms of IT virtualization, the basic goal of network virtualization is to introduce a layer of abstraction between physical hardware and the activities that utilize that hardware. That is, network virtualization allows the delivery of network functions, hardware resources, and software resources independently of the hardware, ie a virtual network.
To realize network virtualization, the most basic technology is layering. There are two main levels of network:
-
Underlay: physical network, the underlying network, responsible for interconnection;
-
Overlay: Virtual network, based on tunnel implementation, traffic needs to run on the Underlay.
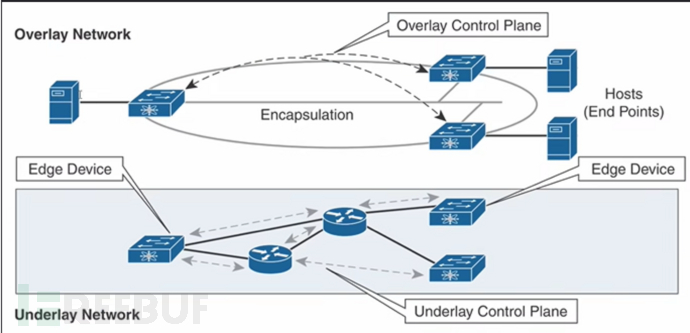 After building the Underrelay, you only need to care about the Overlay, and build a tunnel in the Overlay.
After building the Underrelay, you only need to care about the Overlay, and build a tunnel in the Overlay.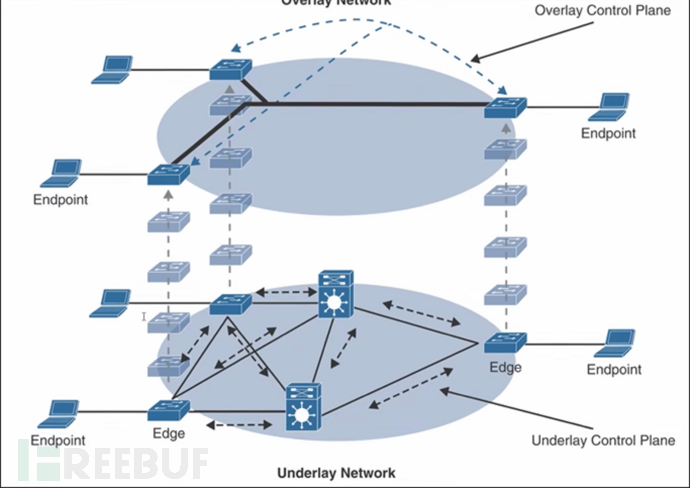
In Overlay, services are isolated by building different tunnels.
## #06 SDN network
Software-defined network (SDN) is an innovative network architecture, which separates the two layers through a centralized control layer and a distributed data layer. The control layer uses the control-data interface to centralize routers on the data layer. Control, convenient software to control the network.
The main task of the network layer is forwarding and routing selection, and the network layer can be abstractly divided into a data plane (also called a forwarding plane) and a control plane. Forwarding is a function implemented on the data plane, while routing is a function implemented on the control plane.
In the traditional Internet, each router has both a forwarding table and routing software, that is to say, it has both a data plane and a control plane. The current SDN network generally has the following form: there is a controller (or cluster), which is responsible for collecting the topology and traffic information of the entire network, calculating the traffic forwarding path, and sending the forwarding table items to the router through the OpenFlow protocol. Table entries perform forwarding actions. As for the router corresponding to the controller and performing the forwarding action, it is generally called a forwarder. The control plane is separated from a single device in the traditional network and concentrated on the controller, and the forwarding plane is composed of transponders. 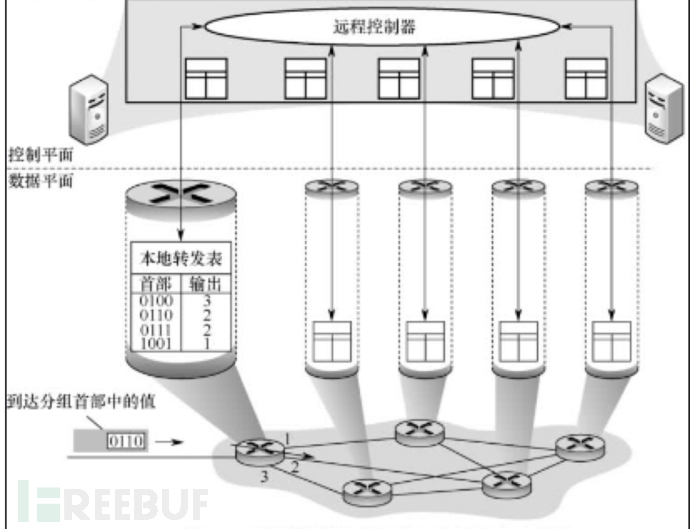 ****
****
## #07 Two forms of network deployment
(1)
One is an underlay network. In this network, all forwarding behaviors are determined by the controller. The controller sends the forwarding table entries to the forwarder through the OpenFlow protocol or a customized BGP protocol, and the forwarder only performs actions. , without a separate control surface.
(2) The other is an overlay network. The transponders of this network are generally traditional devices that do not support OpenFlow, or private custom protocols cannot be deployed. At this time, tunneling technology is used. The basic network is still in the form of a traditional network, and each node is connected through a routing protocol. However, at the server access point, tunneling technology is used to encapsulate or decapsulate data packets.
For traditional networks, what you see is ordinary data packets, which can be forwarded. Tunneling technology is actually a vest for packets, which confuses network devices and makes them think they are their own. But in fact, the heart of the packet is the heart of virtualization. Currently, tunneling technologies such as VxLan, GRE, and NVGRE are generally used. These are also newly added protocols, which also need to be upgraded to support existing network equipment. Although wearing a vest can add new functions without major transformation, it will undoubtedly reduce network performance. The underlay method must be the ultimate form of SDN network.
In this way, the network becomes centralized control again, and the Internet is originally distributed. SDN does not mean to transform the entire Internet into a centralized control mode as shown in the figure, which is unrealistic. However, under some specific conditions, especially the wide area network between some large data centers, using the SDN model to build can make the network run more efficiently.
The programmability of SDN is to provide developers with a powerful programming interface, so that the network has good programmability. For developers of upper-layer applications, the programming interface provided by SDN is called the northbound interface. The northbound interface provides a series of rich APIs, on which developers can design their own applications without caring about the underlying hardware details. The interface through which the SDN controller and the forwarding device establish a two-way session is called the southbound interface. Through different southbound interface protocols, the SDN controller can be compatible with different hardware devices, and can implement the logic of upper-layer applications in the device. The communication interface between the internal controllers of the SDN controller cluster is called an east-west interface, which is used to enhance the reliability and scalability of the entire control plane.
## #08 Advantages of SDN
(1) Global centralized control and distributed high-speed forwarding, on the one hand, are conducive to global optimization at the control level, and on the other hand, are conducive to high-performance network forwarding;
(2) The balance between flexible programmability and performance, after the control and forwarding functions are separated, the network can be configured programmatically by proprietary automation tools;
(3) Reduce costs. After the control and data planes are separated, especially after using an open interface protocol, the manufacturing of network equipment is separated from the development of functional software, thereby effectively reducing costs.
## #09 There is a problem with SDN
(1) Security risks. Centralized management is vulnerable to attacks. If it crashes, the entire network will be affected;
(2) Bottleneck problem. After the original distributed control layer is centralized, as the network scale expands, the controller may become the bottleneck of network performance.
## #010 Introduction to VPC
VPC (Virtual Private
Cloud) is an isolated network environment built on Alibaba Cloud, and the VPCs are logically completely isolated. Hosted in the VPC are our service resources on the private cloud, such as cloud hosts, load balancing, cloud databases, etc.
1. VPC mainly provides two capabilities:
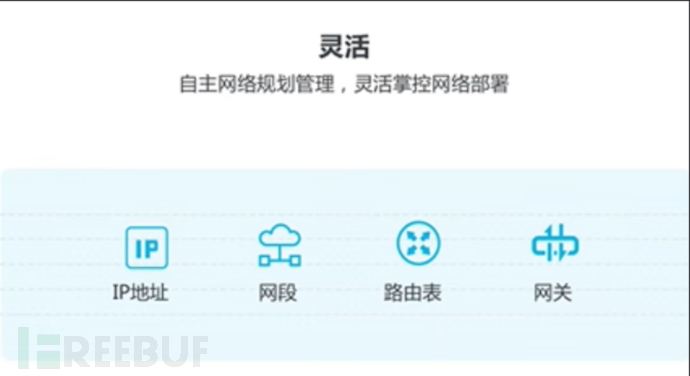
*Users can customize the network topology, including selecting their own IP address range, dividing network segments, configuring routing tables and gateways, etc.
- Connect to the original data center through a dedicated line or VPN, and the resources on the cloud and off the cloud use the same network address plan to realize the smooth migration of applications to the cloud.
 2. Advantages:
2. Advantages:
(1) Safety isolation
 (2) Flexible
(2) Flexible
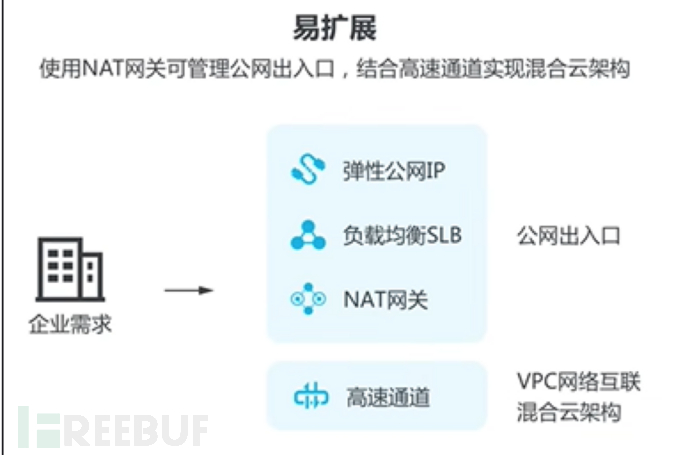
 (3) Easy to expand
(3) Easy to expand
 (4) Free
(4) Free
3. Application scenarios
(1) Secure network
A network with strict security access control is built through the VPC
network, while taking into account the security isolation of core data and effective access from public network access. Users can deploy the core server or database system that processes core data and services in a subnet that cannot be accessed by the public network, and deploy the web server for public network access in another subnet environment, and set the subnet settings with the Internet connection. In
the VPC network, users can implement access control to core data and business servers through access control between subnets, ensuring the security and controllability of core data while meeting the access requirements of the public network.
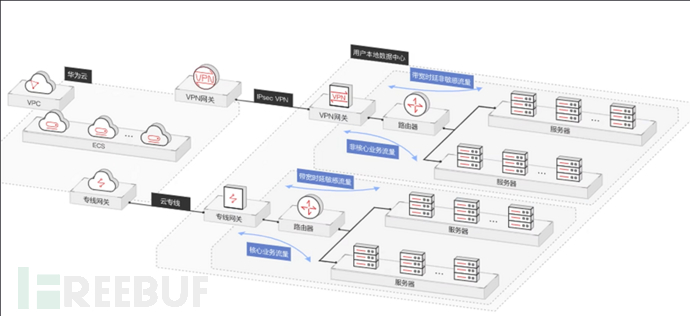
(2) Hybrid cloud network
Through the tunnel or VPN service provided by the VPC network, a secure and efficient network connection is established. Deploy web applications in VPC
, and obtain additional privacy protection and security through distributed firewalls. Users can create firewall rules to make web applications respond to requests such as HTTP/HTTPS while denying access to the
Internet, so as to consolidate the security protection of the website, so as to realize the communication between the applications deployed on the public cloud and the services deployed in the self-owned data center Interconnection to build a hybrid cloud architecture.
(3) hosting website
Through the destination address NAT function provided by the VPC network, secure access to the Internet without EIP is realized.
(4) Solve the network bottleneck
Through the tunnel/VPN/dedicated line services provided by the VPC network, it is convenient to deploy enterprise applications to the cloud.
(5) Disaster recovery
Through the tunnel/VPN/dedicated line services provided by the VPC network, it is convenient to build a disaster recovery environment.
## #011 CGN
1. Technical background
On the one hand, telecom operators are vigorously deploying mobile Internet, expanding broadband users, and actively promoting the integration of three networks, but on the other hand, they have to face the practical problems brought about by the exhaustion of IPv4 addresses.
2. Two main solutions
-
IPv6: It can fundamentally solve the problem of address exhaustion, but because most of the content and applications are still based on IPv4, a rigid full switch to IPv6 may face the risk that existing services cannot be inherited.
-
NAT: Continue to use IPv4 to develop services, and deploy IPv4 private addresses on a large scale to achieve statistical multiplexing of the current public network and lPv4 addresses, so that the IPv4 address problem can be solved for a long time.
Since the NAT solution does not need to replace the home gateway device, the investment cost of the operator is greatly reduced.
CGN: Carrier Grade NAT, carrier-grade NAT, also known as LSN (Large Sca. 000le NAT, large-scale deployment of NAT)
-
Compared with traditional NAT, it has been greatly improved in the number of concurrent users supported, performance, traceability, etc., to adapt to large-scale commercial deployment of operators;
-
Contains a variety of technologies and application scenarios, such as: NAT444, DS-Lite, etc.
NAT444: The deployment position of traditional NAT
(NAT44) is improved, and the operator deploys NAT44 equipment CGN, which is easy to deploy. It only needs to add CGN equipment at the aggregation layer or core layer, and there is no need for large-scale equipment replacement.
 ****
****
## #012 Elastic public IP
Elastic IP
Address (EIP for short), an independent public IP resource, can be bound to Alibaba Cloud private network VPC type ECS, NAT gateway, and private network load balancing SLB, and can be dynamically unbound. Realize the decoupling of public network IP and ECS, NAT gateway, and SLB to meet the requirements of flexible management.
 ****
****
## #013 Expressway
Express Link is a product that provides users with network interconnection capabilities, and realizes high-speed, stable and secure private network intercommunication for users. Express Connect can realize the ability of the IDC under the cloud to connect to Alibaba Cloud, the intercommunication between the IDC and the VPC on the cloud, and the cross-regional intercommunication between VPCs on the cloud.
 ****
****
## #014VPN Network
VPN Gateway (VPN
Gateway) is an Internet-based
service that securely and reliably connects enterprise data centers, enterprise office networks, or Internet terminals with Alibaba Cloud's proprietary network (Virtual Private Cloud) through encrypted channels.

## 014VPN Network
VPN Gateway (VPN
Gateway) is an Internet-based
service that securely and reliably connects enterprise data centers, enterprise office networks, or Internet terminals with Alibaba Cloud's proprietary network (Virtual Private Cloud) through encrypted channels.
[External link image transfer...(img-E9OTXi5B-1689996051596)]
Network security engineer enterprise-level learning route
At this time, of course you need a systematic learning route
If the picture is too large and compressed by the platform, you can download it at the end of the article (free of charge), and you can also learn and communicate together.
Some of my collection of self-study primers on cyber security

Some good video tutorials I got for free:
The above information [click the card below] can be received, free to share