Article directory
1. The meaning of the transport layer
The data coming down from the application layer is not directly sent to the network, but is transmitted from the top to the bottom of the network protocol stack, passing through the transport layer, network layer, data link layer, and finally sent to the network through hardware.
The first two chapters talked about two protocols of the application layer: HTTP and HTTPS . The main purpose of the application layer is to ensure data security, while the purpose of the transport layer is to ensure that data can be reliably transmitted to the target address .
2. Port number
2.1 Five-tuple identifies a communication
Port numbers are used to identify different applications on a host for network communication .
Because there are different services on the host, when the data obtained from the network is delivered upwards, the destination port number corresponding to the data will be extracted at the transport layer , and then the data should be delivered to which service process on the current host (application layer). That is, services with different port numbers can be deployed on one host at the same time.
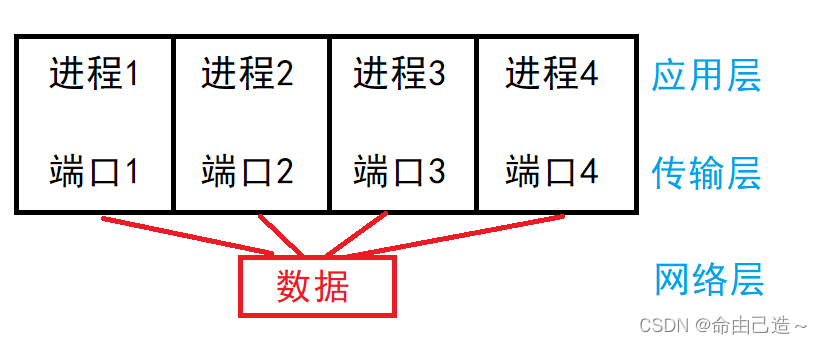
In the TCP/IP protocol, a communication is identified by a five-tuple such as "source IP address", "source port number", "destination IP address", "destination port number", and " protocol number ".
For example, we open a browser and use different pages to access CSDN. Although the source IP address is the same, but the source port number is different, it means two different communications. Through this five-tuple, the server can accurately distinguish where the request comes from .
- communication process
1️⃣ First extract the destination IP address and destination port number from the data , and make sure that the data is sent to the current service process.
2️⃣ Then extract the protocol number from the data and provide the corresponding type of service for the data.
3️⃣ Finally, extract the source IP address and source port number from the data , use them as the destination IP address and destination port number of the response data, and send the response result to the corresponding client process.
2.2 Port number range division
The length of the port number is 16 bits, so the range of the port number is 0 ~ 65535:
0 ~ 1023: well-known port number. For example, widely used application layer protocols such as HTTP, FTP, and SSH have fixed port numbers . (Compared to 120 or 110)
1024 ~ 65535: The port number dynamically assigned by the operating system. The port number of the client program is assigned from this range by the operating system.
2.3 Well-known port numbers
Some servers are very commonly used, and the port numbers of these servers are generally fixed:
ssh server - port 22.
ftp server - port 21.
telnet server - port 23.
http server - port 80.
https server - port 443.
- Check the port number
It can be vim /etc/servicesa file, which records network service names and their corresponding port numbers and protocols.
2.4 The number of bound port numbers
- Can a port number be bound by multiple processes?
no! Because the role of the port number is to identify a unique process . If multiple processes are bound, how to find the corresponding process? So if you bind a port number that has already been bound, there will be a problem of binding failure.
- Can a process bind multiple port numbers?
Can! For example, two port numbers A and B are bound, and these two port numbers identify the same process, which does not conflict with the uniqueness of the port number used to identify the process.
2.5 pidof & netstat command
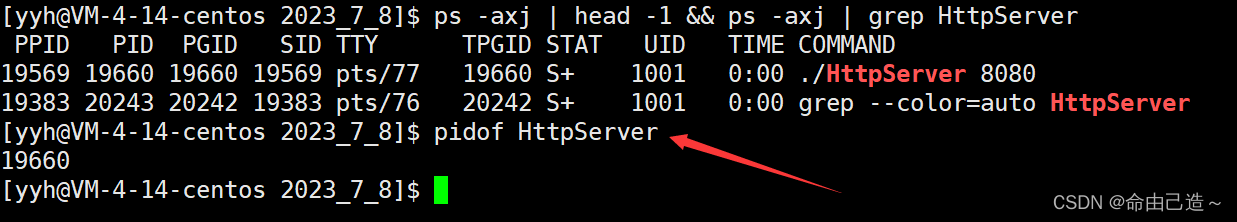
- pidof command
View the pid of the process
Kill a process with kill:
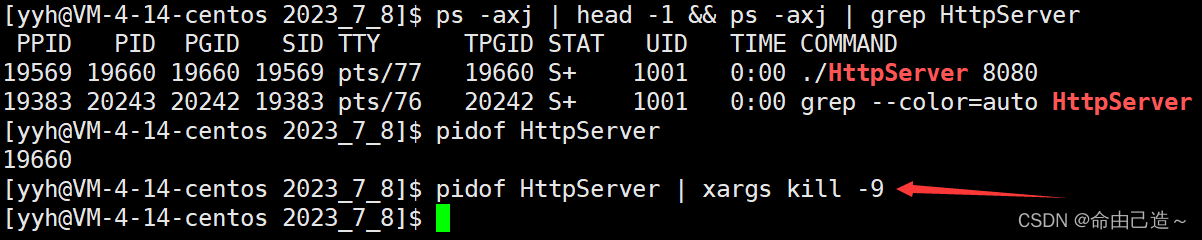
Here xargsit is used to splice the data read from the pipeline to the end of kill -9.
- netstat command
Used to check network status
options:
n: Refuse to display aliases, and convert all numbers that can be displayed into numbers.
l: Only list services in the LISTEN state.
p: Displays the name of the program that established the related link.
t(tcp): Only display tcp related options.
u(udp): Only display udp-related options.
a(all): Display all options, and LISTEN is not displayed by default.
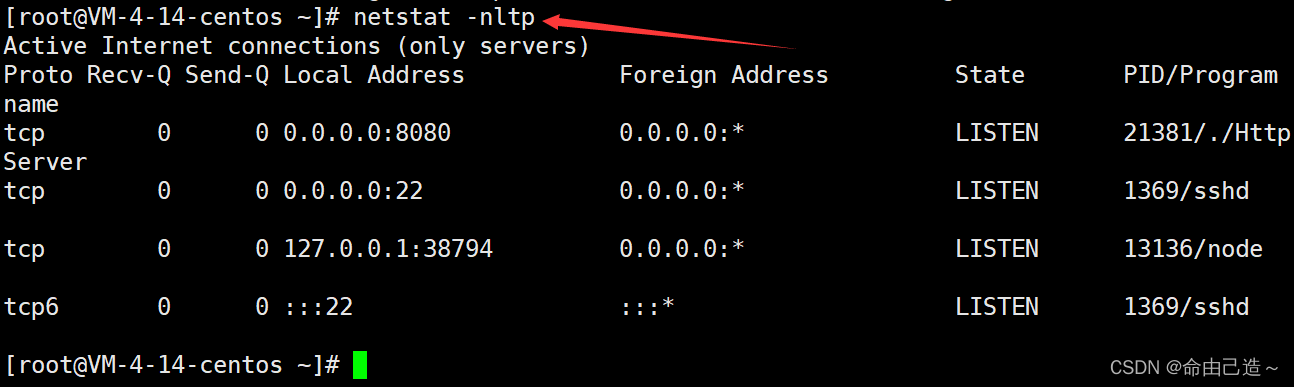
When viewing TCP-related network information, generally choose to use nltpthe combination option.
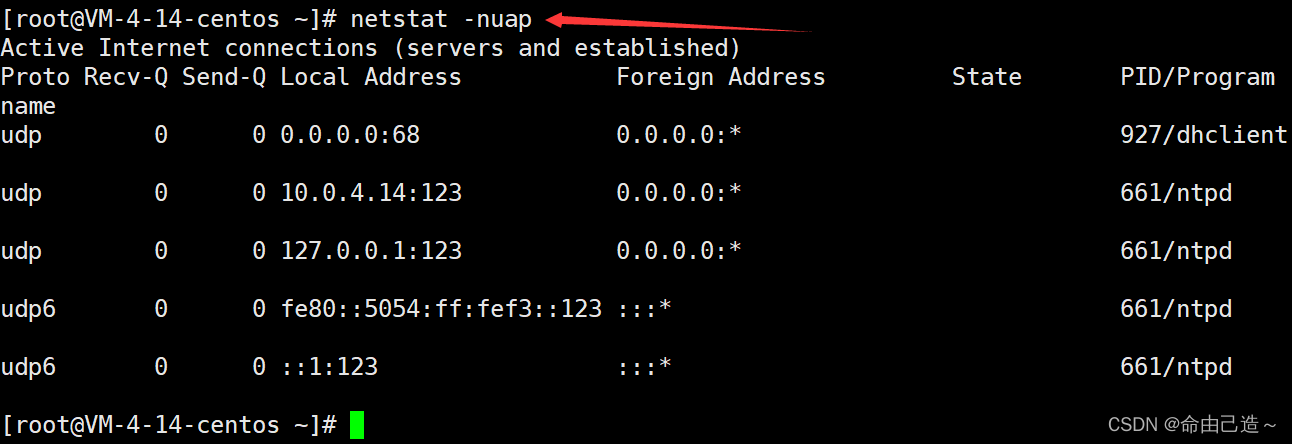
When viewing UDP-related network information, generally choose to use nlupthe combination option.
3. UDP protocol
3.1 UDP protocol format
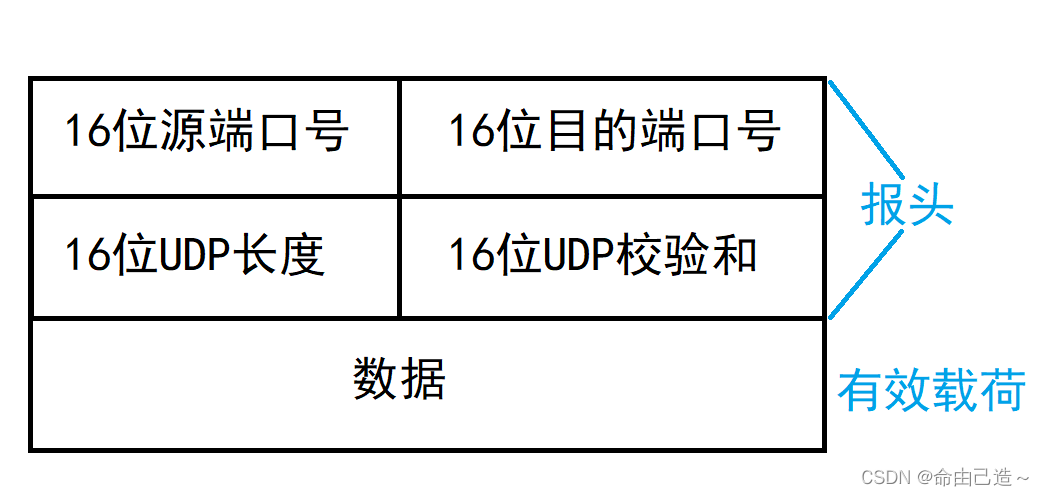
16-bit source port number: indicates where the data comes from.
16-bit destination port number: Indicates where the data is going.
16-bit UDP length: Indicates the length of the entire datagram (UDP header + UDP data).
16-bit UDP checksum: If the checksum of the UDP packet is wrong, the packet will be discarded directly.
We have always used ports in the user layer uint16_t, and the fundamental reason is that the port number in the transport layer protocol is 16 bits. Our send data is not sent directly to the network, but to the transport layer.
- How to separate header and payload?
UDP uses a fixed header . The UDP header only contains four fields, and the length of each field is 16 bits, totaling 8 bytes. So directly extracting the first eight bytes is the header, and the rest is the payload.
- How to use UDP? (Which protocol is the payload delivered to the upper layer?)
Each process of the application layer is bound with a port number, and UDP finds the corresponding application layer process through the destination port number in the header , and hands over the payload.
3.2 How to understand the header?
In fact, the header here is a structured data object:
struct udp_hdr
{
uint16_t src_port;// 源端口
uint16_t dsc_port;// 目的端口
uint16_t length;// UDP长度
uint16_t check;// 校验和
};
- UDP data encapsulation process:
First of all, it is necessary to know that the sendto data of the application layer is sent to the transport layer.
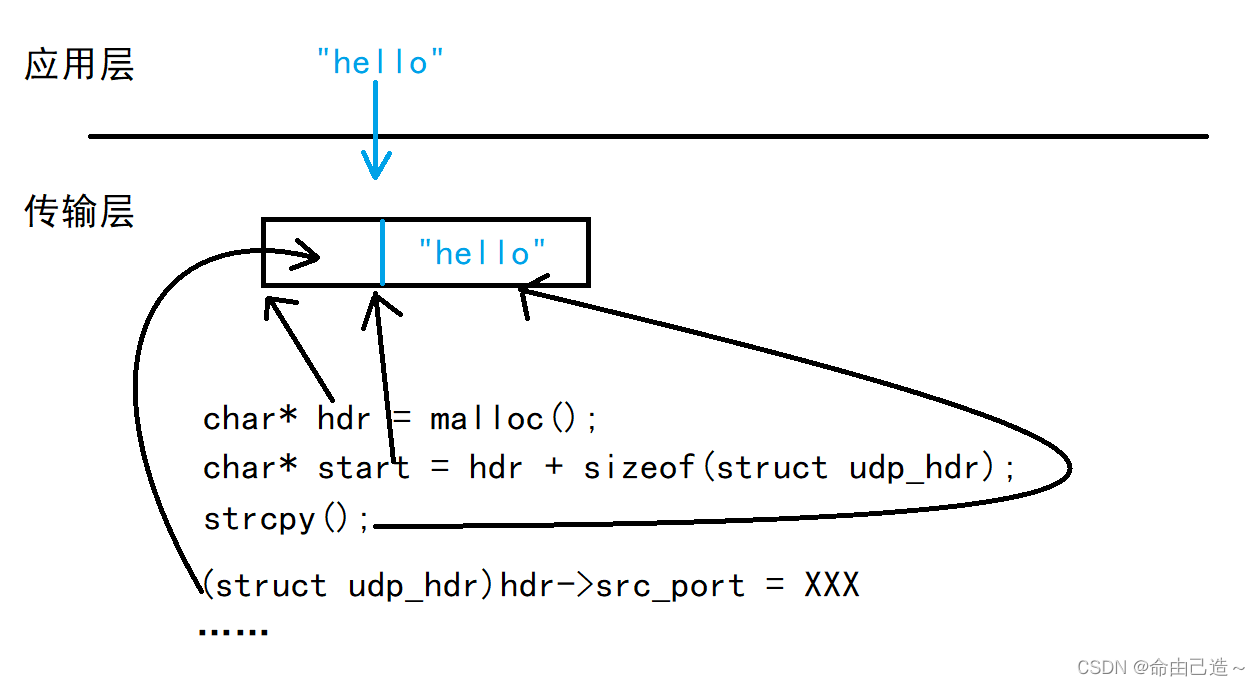
Create a block of memory, calculate the starting address of the payload, copy the payload, and fill in the header part by force. Finally, a UDP message is formed.
- UDP data sharing process:
Because it is a fixed-length header, the destination port number is directly taken out, and the payload is delivered upward to the specified protocol (process).
3.3 Features of UDP protocol
No connection : know the IP and port number of the peer, and then directly transmit data without establishing a connection.
Unreliable : There is no confirmation mechanism and no retransmission mechanism; if the segment cannot be sent to the other party due to network failure, the UDP protocol layer will not return any error information to the application layer.
Datagram-oriented : Guaranteed to read the complete message.
- Datagram Oriented
It's like a courier here, if someone sends three couriers, then we must receive three, not one, one and a half. If there is only one package, we can't just take half of it.
After sending a message, either do not read it, or recvfrom waits until the entire message is read and returns.
If the sending end calls sendto once to send 100 bytes, then the receiving end must also call the corresponding recvfrom once to receive 100 bytes; instead of calling recvfrom 10 times in a loop, receiving 10 bytes each time.
3.4 UDP buffer
1️⃣ UDP has no real sending buffer , because it has no reliable mechanism and does not need to temporarily store data. It directly copies the data to the kernel, and the kernel passes the data to the network layer protocol for subsequent transmission actions.
2️⃣ UDP has a receiving buffer, but there is no guarantee that the order received is the order sent. And if the buffer is full, the incoming UDP data will be discarded .
UDP can also write during the reading process, so it is full-duplex .
- Why does UDP have a buffer?
If UDP does not have a receiving buffer, then the upper layer is required to read the message obtained by UDP in time. If a message is not read in UDP, then the message data obtained by UDP from the bottom layer will be forced to throw away.
3.5 UDP transmission maximum length
The UDP maximum length in the UDP protocol header is 16 bits, so the maximum length of a UDP packet is 64K (including the size of the UDP header).
If you want to transmit data larger than 64k, you need to manually subpackage at the application layer, send it multiple times, and manually assemble it at the receiving end.