1 Introduction
HTTPS uses a hybrid encryption method of symmetric encryption and asymmetric encryption.
Cryptography knowledge can view my blog
2. HTTPS encryption process
HTTPS uses asymmetric encryption when establishing a link, and symmetric encryption after establishing a link.
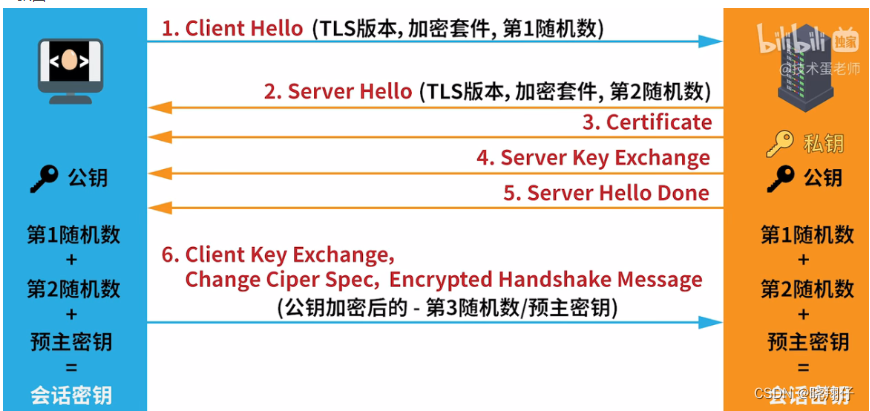
step 1
The client first sends an encrypted communication (https) request to the server. This request includes:
- SSL/TSL version number
- Cipher suite, which is the list of encryption algorithms supported by the client
- Generate a random number, we call him the first random number
- There is a Client Hello string
- step 2
step 2
After receiving the request, the server sends a response to the client:
- Confirm the SSL/TSL version number, if the client does not support it, then close the communication
- List of confirmed encryption algorithms
- Generate a random number, we call the second random number
step 3
The server then sends a digital certificate to the client, and the server registers its public key to the CA (third-party certification authority), and then the CA processes the server's public key with its own private key and issues a digital certificate.
step 4
Server sends public key to client
step 5
The server sends Hello Done, indicating that the sending is complete
step 6
After receiving a series of responses from the server, the client confirms the digital certificate and public key, and sends it to the server after there is no problem:
- Generate a random number, which we call the third random number or pre-master key, which will be encrypted with the public key
- Client handshake end notification, indicating that the client's handshake is over
step 7
After the server receives the client data, it uses the private key to decrypt the encrypted pre-master key. No one else knows the pre-master key because it is encrypted unless the server private key is leaked. Then the server calculates the session key through the first, second, and pre-master keys. The client also computes the session key.
Step 8
The server sends to the client:
- Encrypted communication algorithm change notification, later communicated by session key
- The server handshake ends
So far, the SSL/TSL handshake is over, and after that, the session key will be used to encrypt and decrypt, that is, symmetric encryption.
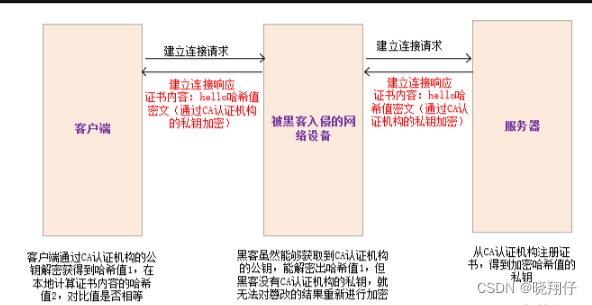
3. About certificate tampering
Assuming that our certificate is just a simple string hello,
the result of calculating the hash value for this string is:
BC4B2A76B9719D91
If any character in hello is tampered with, for example, it becomes hella, then the calculated hash value will change greatly.
The result is:
BDBD6F9CF51F2FD8But if the hacker tampers with hello and recalculates the hash value at the same time, the client will not be able to tell the difference.
Therefore, the transmitted hash value cannot be transmitted in plaintext, and needs to be transmitted in ciphertext;
(1) This hash value is encrypted by another private key on the server side (this private key is given to the server by the certificate issuing authority when applying for a certificate, not The client and the server transmit the private key of the symmetric key);
(2) Then the client decrypts through the public key of the certificate issuing agency already stored in the operating system, restores the original hash value, and then performs verification;
The above content can be visually represented by the following figure
4 last
In my opinion, the biggest advantage of HTTPS is that it can effectively ensure the authenticity of the server and the confidentiality of transmitted data.
References
Hardcore! 30 Graphical HTTP Common Interview Questions
Detailed HTTPS encryption process - Xing Tao's Blog - CSDN Blog