Scenes
It is often encountered that there is always some sensitive information in the configuration file of the project, such as the url of the data source, the user name,
Password... Once this information is exposed, the entire database will be leaked, so how to hide these configurations.
In addition to manually writing the encrypted configuration into the configuration file and manually decrypting it when extracting, you can also use the following
Way.
jasypt-spring-boot
GitHub - ulisesbocchio/jasypt-spring-boot: Jasypt integration for Spring boot
Note:
Blog:
Overbearing rogue temperament blog_CSDN Blog-C#, Architecture Road, Blogger in SpringBoot
accomplish
1. Add project dependencies to SpringBoot
<dependency>
<groupId>com.github.ulisesbocchio</groupId>
<artifactId>jasypt-spring-boot-starter</artifactId>
<version>3.0.3</version>
</dependency>2. Add a secret key for encryption in the configuration file yml, which can be specified arbitrarily
jasypt:
encryptor:
password: badaodechengxvyuanIt is not safe to directly put the secret key in the configuration file, you can configure the secret key when the project starts
java -jar xxx.jar -Djasypt.encryptor.password=badaodechengxvyuan3. Write unit tests to generate encrypted data
In order to encrypt the configured plaintext data, the data needs to be encrypted
import org.jasypt.encryption.StringEncryptor;
import org.junit.jupiter.api.Test;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.boot.test.context.SpringBootTest;
import org.springframework.util.Assert;
@SpringBootTest
class JasyptTest {
/**
* inject encryption method
*/
@Autowired
private StringEncryptor encryptor;
/**
* encrypt data
*/
@Test
void encrypt() {
String name = encryptor.encrypt("root");
String password = encryptor.encrypt("123456");
System.out.println("name:"+name);
System.out.println("password:"+password);
Assert.isTrue(name.length()>0,"name encrypt success");
Assert.isTrue(password.length()>0,"password encrypt success");
}
}Here, only the user name and password are encrypted for demonstration purposes. Of course, url or other plaintext data that needs to be encrypted is fine.
Running unit tests will output encrypted string data
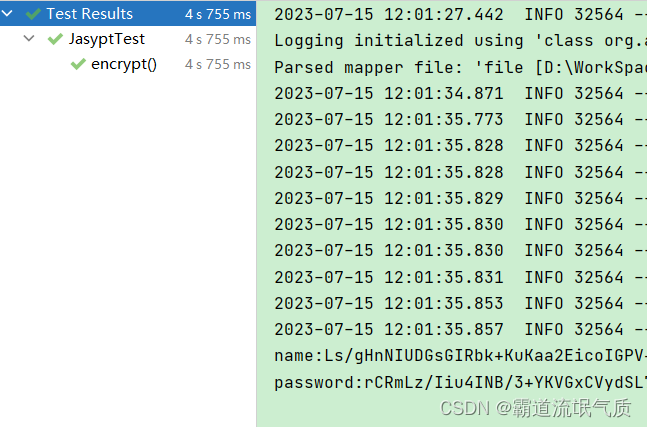

4. Copy the encrypted data to the corresponding location in the configuration file yml, and wrap it with ENC().
# 数据源
spring:
application:
name: badao-tcp-demo
datasource:
url:jdbc:mysql://localhost:3306/test?useUnicode=true&characterEncoding=utf8&zeroDateTimeBehavior=convertToNull&useSSL=true&serverTimezone=GMT%2B8
username: ENC(Ls/gHnNIUDGsGIRbk+KuKaa2E...)
password: ENC(rCRmLz/Iiu4INB/3+YKVGxC...)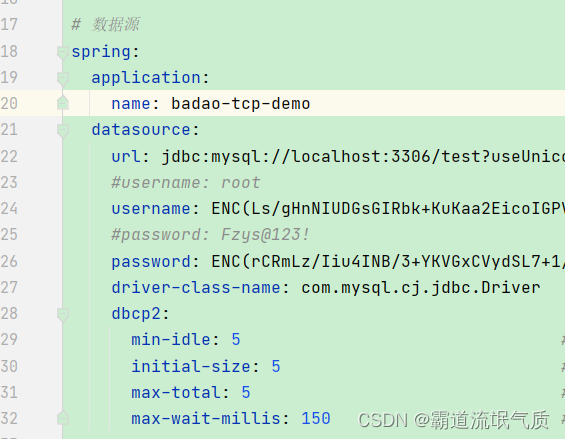

The prefix and suffix wrapped above can also be changed through configuration, and more usages such as configuring the encryption algorithm yourself,
Refer to the official documentation.