HKDF is called HMAC-based KDF (key derivation function), which is based on the key derivation function of HMAC, so we first understand the HMAC algorithm.
1. HMAC
The mechanism that provides message integrity confirmation between two peers based on a common key is called "message authentication codes (MAC), message authentication code". In fact, it is to hash the message, and the obtained hash value is appended to the message, and sent together with the message. After the peer receives it, the hash is also performed to verify whether the message has been tampered with. The key point is that the hash value obtained by different data must be different— —The obtained hash value is MAC (also called message digest in other contexts). In addition, in order to avoid using the same hash function to operate on the same data to always get the same digest, an additional key is added so that different keys can be used to get different MACs. Of course, this key is two pairs Everyone knows. In this way, we get the algorithm of message integrity authentication based on encrypted hash - Hash-based MAC.
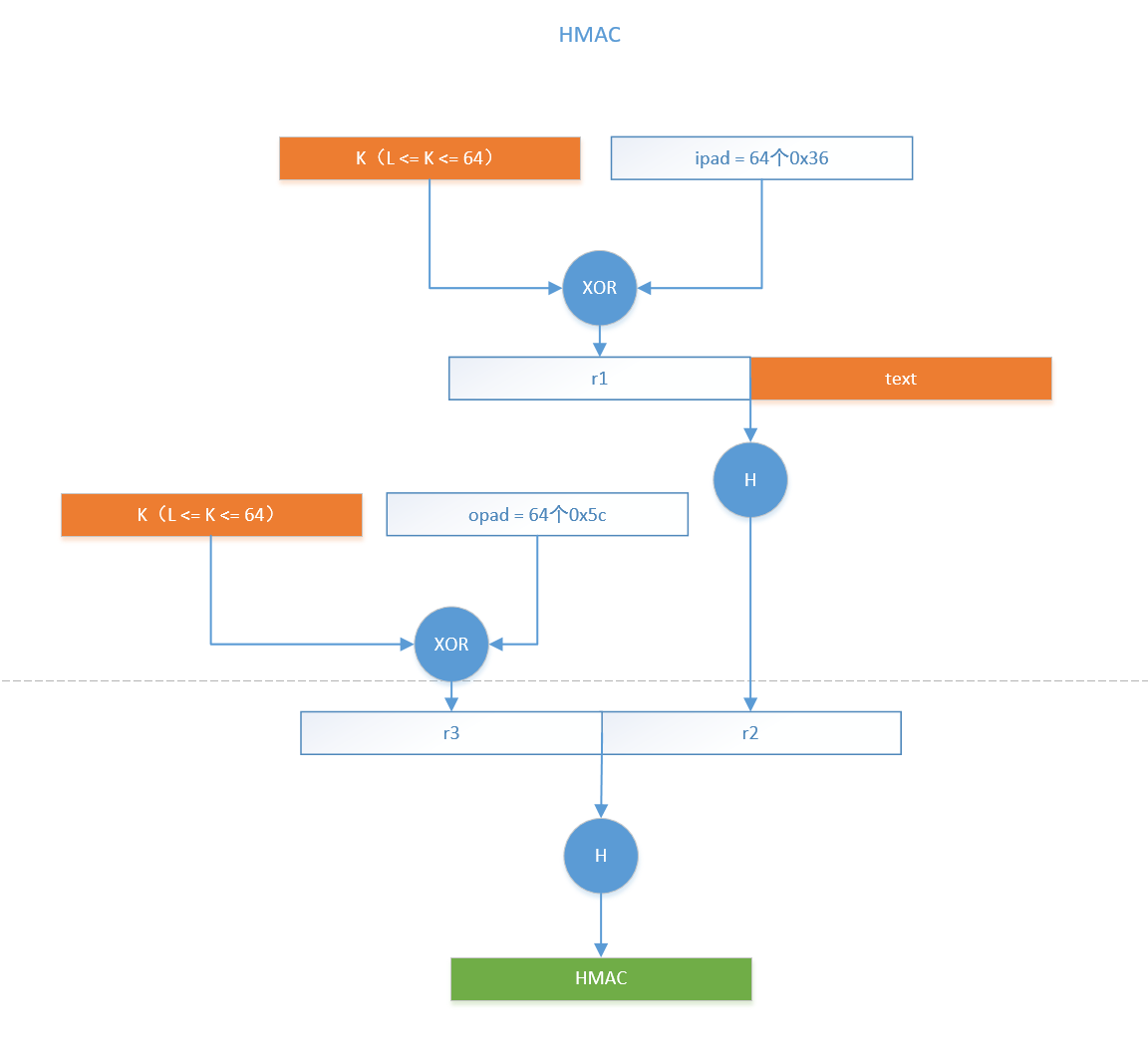
HMAC is defined as follows:
enter:
- The encrypted hash function H used, the output length is hashLen
- The key K used, the length hashLen <= Klen <= 64, if the length of K exceeds 64, first perform a hash with the hash function, and use the obtained value as K
- The data text that needs to be authenticated
output:
- Message Integrity Authentication Code HMAC
process:
- Define ipad = 64 0x36, opad = 64 0x5c
- HMAC = HMAC-Hash(H, K, text) = H(K XOR opad, H(K XOR ipad, text))
Purpose:
- Generate an HMAC message integrity authentication code for text, and the output length is the output length of the hash function
2. HKDF
The main purpose of HKDF is to use the original key material to derive one or more keys that can achieve cryptographic strength (mainly to ensure randomness)—that is, to expand shorter key materials into longer keys Materials and processes need to ensure randomness.
HKDF contains two basic modules, or two basic usage steps: 1. Extract Extract, 2. Expand Expand.
- Extraction: Use the original key material to derive a cryptographically strong pseudo-random key
- Expansion: Use the pseudo-random key extracted in the first step to expand a key of a specified length (while ensuring randomness).
HKDF-Extract
enter:
- The hash function H used by HMAC, the output length of H is hashLen
- Original key material IKM (input keying material)
- Another random source salt, if not, the default is a string of 0 with the length of hashLen
output:
- Pseudorandom key prk (pseudorandom key) of hashLen length
process:
- prk = HKDF-Extract(H, salt, IKM) = HMAC-Hash(H, salt, IKM)
- In fact, it is equivalent to using salt as the K of HMAC-Hash to perform message integrity authentication on IKM
Purpose:
Use a salt to increase the randomness of IKM

HKDF-Expand
enter:
- The hash function H used by HMAC, the output length of H is hashLen
- The PRK generated in the first step
- Another random element info, can be empty
- Expected key length L
output:
- L-length OKM (output keying material)
process:
N = ceil(L/hashLen)
T = T(1) || T(2) || T(3) || ... || T(N)
OKM = first L bytes of T
T(0) = empty
T (1) = HMAC-Hash(PRK, T(0) || info || 0x01)
T(2) = HMAC-Hash(PRK, T(1) || info || 0x02)
T(3) = HMAC- Hash(PRK, T(2) || info || 0x03)
…
Purpose:
- Extend the PRK to a specified length L while maintaining cryptographic strength (randomness)

3. Summary
- HKDF is a key derivation algorithm, which derives a key of a specified length based on an original key material;
- HKDF is based on HMAC;
- HMAC is a message integrity authentication algorithm based on an encrypted hash function, and its main purpose is to authenticate message integrity. is used here to increase the randomness of the raw key material;
- HKDF consists of two steps: (1) Extract Extract, (2) Expand Expand;
- HKDF-Extract is HMAC, taking the authentication code of IKM is equivalent to increasing the randomness of IKM (text) with an additional random source salt (Key);
- HKDf-Expand is to make the short key longer while ensuring randomness.