1. Misunderstandings and pitfalls of self-study network security learning
1. Don't try to become a programmer first (programming-based learning) and then start learning
Behavior: start to master from programming, learn everything from front-end and back-end, communication protocols, and everything.
Disadvantages: It takes too long, and there is not much critical knowledge available after the actual transition to security.
A lot of security function knowledge and even nouns do not understand unserialize outfile
2. Don’t take in-depth learning as the first lesson for getting started.
Many people are aiming to learn network security well and solidly, so it is easy to use too much force and fall into a misunderstanding: that is, to learn all the content in depth. But it's not a good idea to use deep learning as a first lesson in cybersecurity. The reasons are as follows:
[1] The black-box nature of deep learning is more obvious, and it is easy to learn and swallow
【2】Deep learning has high requirements on itself, it is not suitable for self-study, and it is easy to enter a dead end
3. Misunderstandings of self-study in the direction of hacking skills and interests:
Behavior: frantically searching for security tutorials, joining various small circles, downloading every resource, watching every video, as long as it is related to hacking.
Disadvantages: Even after considering the quality of resources, the knowledge points that can be learned are very scattered and highly repetitive.
The code can't be understood, the explanation can't be understood, and the situation of half-knowledge happens from time to time.
After spending a lot of time understanding it, I realized that the content of this video is actually the same as other knowledge points I watched.
4. Don't collect too much information.
There are a lot of learning materials about network security on the Internet, and there are several gigabytes of materials that can be downloaded or viewed at every turn. And many friends have "collection addiction", buying more than a dozen books at once, or collecting dozens of videos
Many online learning materials are extremely repetitive and most of the content has not been updated a few years ago. During the introductory period, it is recommended to choose "small but refined" materials. Below I will recommend some learning resources that I think are good for Xiaobai. Read on patiently.
2. Some preliminary preparations for learning network security
1. Hardware selection
often asks me "Do I need a computer with a high configuration to learn network security?" The answer is no, the computer used by hackers does not need high configuration, as long as it is stable. Because some programs used by hackers, Low-end CPU can also run very well, and it does not take up much memory. There is another one, the hacker is done under the DOS command, so the computer can be used in the best condition! So, don’t re-purchase the machine in the name of learning ...
2. Software selection
Many people will be entangled in learning hackers whether to use Linux, Windows or Mac system. Although Linux looks cool, it is not friendly to newbies. The Windows system can also use the virtual machine to install the target machine for learning
As for the programming language, Python is the most recommended because of its good expansion support. Of course, many websites on the market are developed by PHP, so it is also possible to choose PHP. Other languages include C++, Java...
Many friends will ask if they want to learn all languages? the answer is negative! To quote my sentence above: Learning programming is just a tool, not an end, our goal is not to become a programmer
(An extra thing to mention here is that although learning programming cannot get you started, it can determine how far you can go on the road of network security, so I recommend you to learn some basic programming knowledge by yourself)
3. Language skills
We know that computers were first invented in the West, many nouns or codes are in English, and even some existing tutorials were originally translated from English, and a bug is found to be translated into Chinese. In the time of the week, the bugs may have been patched at this time difference. And if you don’t understand some professional terms, you will have obstacles when communicating technology or experience with other hackers, so you need a certain amount of English and hacker professional terms (you don’t need to be particularly proficient, but you must be able to understand the basics)
For example: broiler, hanging horse, shell, WebShell, etc.
3. Network security learning route
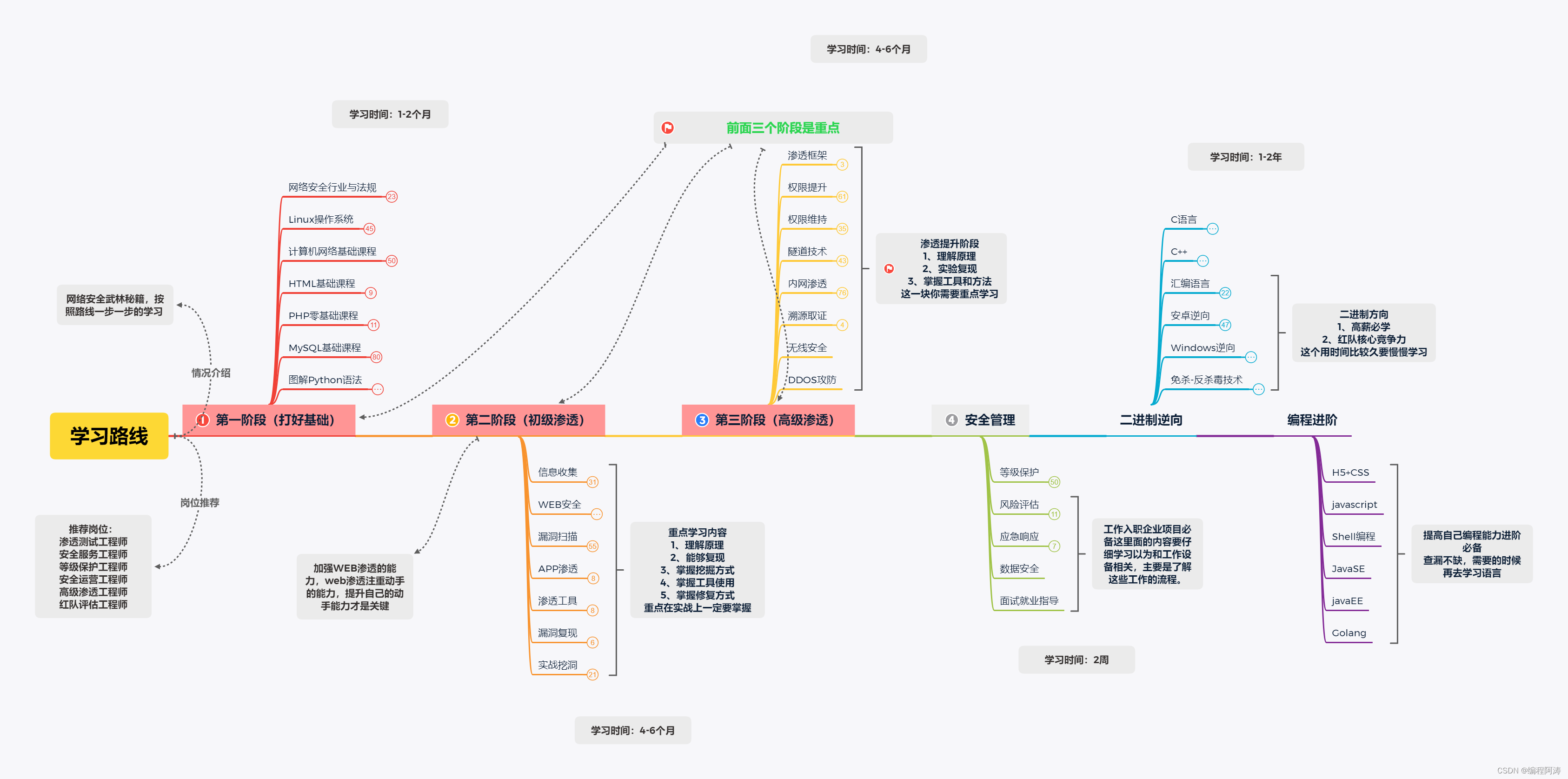
The first stage: getting started with basic operations and learning basic knowledge
The first step to getting started is to learn some current mainstream security tool courses and supporting books on basic principles. Generally speaking, this process takes about 1 month.
At this stage, you already have a basic understanding of cybersecurity. If you have finished the first step, I believe you have theoretically understood the above is sql injection, what is xss attack, and you have also mastered the basic operations of security tools such as burp, msf, and cs. The most important thing at this time is to start laying the foundation!
The so-called "foundation" is actually a systematic study of basic computer knowledge. If you want to learn network security well, you must first have 5 basic knowledge modules:
1. Operating system
2. Protocol/network
3. Database
4. Development language
5. Principles of common vulnerabilities
What is the use of learning these basic knowledge?
The level of knowledge in various fields of computer determines the upper limit of your penetration level.
[1] For example: if you have a high level of programming, you will be better than others in code auditing, and the exploit tools you write will be easier to use than others;
[2] For example: if you have a high level of database knowledge, then when you are conducting SQL injection attacks, you can write more and better SQL injection statements, which can bypass WAF that others cannot bypass;
【3】For example: if your network level is high, then you can understand the network structure of the target more easily than others when you infiltrate the internal network. You can get a network topology to know where you are, and get the configuration of a router. file, you will know what routes they have made;
【4】For another example, if your operating system is good, your privilege will be enhanced, your information collection efficiency will be higher, and you can efficiently filter out the information you want.
The second stage: actual operation
1. Mining SRC
The purpose of digging SRC is mainly to put the skills into practice. The biggest illusion of learning network security is to feel that you know everything, but when it comes to digging holes, you can’t do anything. SRC is a very good opportunity to apply skills.
2. Learn from technical sharing posts (vulnerability mining type)
Watch and study all the 0day mining posts in the past ten years, and then build an environment to reproduce the loopholes, think and learn the author's digging thinking, and cultivate your own penetrating thinking
3. Range practice
Build a shooting range by yourself or go to a free shooting range website to practice. If you have the conditions, you can buy it or apply to a reliable training institution. Generally, there are supporting shooting range exercises.
The third stage: Participate in CTF competition or HVV action
recommendation: CTF competition
CTF has three points:
【1】A chance close to actual combat. Now the network security law is very strict, unlike before, everyone can mess around
[2] Topics keep up with the frontiers of technology, but many books lag behind
【3】If you are a college student, it will be very helpful for finding a job in the future
If you want to play a CTF competition, go directly to the competition questions. If you don’t understand the competition questions, go to the information according to what you don’t understand.
Recommendation: HVV (network protection)
HVV has four points:
[1] It can also greatly exercise you and improve your own skills. It is best to participate in the HVV action held every year
【2】Be able to meet many bigwigs in the circle and expand your network
【3】The salary of HVV is also very high, so you can earn a lot of money if you participate
[4] Like the CTF competition, if you are a college student, it will also be very helpful for finding a job in the future
Fourth, the recommendation of learning materials
Recommended Book List:
Computer Operating System:
[1] Coding: the language hidden behind computer software and hardware
【2】In-depth understanding of the operating system
【3】In-depth understanding of windows operating system
【4】Linux kernel and implementation
Programming development class:
【1】windows programming
【2】windwos core becomes
【3】Linux programming
【4】Unix environment advanced into
【5】IOS becomes
[6] The first line of code Android
【7】C programming language design
【8】C primer plus
[9] C and pointers
[10] C expert programming
[11] C traps and defects
[12] Assembly language (Wang Shuang)
【13】java core technology
【14】java programming ideas
【15】Python core programming
[16] Linux shell script strategy
[17] Introduction to Algorithms
[18] Compilation principle
[19] Compilation and decompilation technology practice
[20] The way to clean code
[21] Code Encyclopedia
[22] TCP/IP Detailed Explanation
【23】Rootkit: Lurkers in the gray area of the system
【24】Hacking Attack and Defense Technology Collection
【25】Encryption and decryption
【26】C++ Disassembly and Reverse Analysis Technique Revealed
[27] web security testing
【28】White hat talks about web security
【29】Proficient in script hacking
【30】Web front-end hacking technology secret
[31] Programmer's application
【32】English Writing Handbook: Elements of Style
Common Internet Security and Forums
Kanxue Forum
Safety Class
Safety Niu
Safety Internal Reference
Green League
Prophet Community
XCTF Alliance
I have also compiled some network security information for you below. If you don’t want to find them one by one, you can refer to these information! Follow me and send it automatically! Pay attention to the background information after paying attention
video tutorial

SRC&Hacking Technical Documentation

epilogue
The network security industry is like a river and lake, where people of all colors gather. Compared with many decent families with solid foundations in European and American countries (understand encryption, know how to protect, can dig holes, and are good at engineering), our talents are more heretics (many white hats may not be convinced), so in the future Talent training and In terms of construction, it is necessary to adjust the structure and encourage more people to do "positive" "system and construction" that combines "business" and "data" and "automation" in order to quench the thirst for talents and truly serve the society in an all-round way. Internet provides security.
Special statement:
This tutorial is purely technical sharing! The purpose of this tutorial is in no way to provide and technical support for those with bad motives! Nor does it assume joint and several liability arising from the misuse of technology! The purpose of this tutorial is to maximize everyone's attention to network security and take corresponding security measures to reduce economic losses caused by network security.