Foreword:
This tutorial is purely technical sharing! The purpose of this tutorial is in no way to provide and technical support for those with bad motives! Nor does it assume joint and several liability arising from the misuse of technology! The purpose of this tutorial is to maximize everyone's attention to network security and take corresponding security measures to reduce economic losses caused by network security. ! ! !
One: Definition
Hackers refer to those who have professional knowledge of computer technology and can break through system security in creative ways, explore and discover loopholes and weaknesses in computer systems . Hackers have a wide range of skills, and they can be computer security experts, network programmers, or information technology enthusiasts.
Two: Classification
Depending on how they behave and their motives, hackers can be divided into the following categories:
1. White Hat Hacker
White hat hackers are a group of hackers with a high moral concept. They improve network security by discovering system vulnerabilities and reporting them to relevant parties. Their goal is to protect network systems from attacks and help fix vulnerabilities to ensure that users' data is not lost.
2. Black Hat Hacker
Black hat hackers are those who engage in illegal activities, they use their technical ability to cause damage, steal other people's information or seek improper benefits. They are threats to network security and should be punished by law.
3. Gray Hat Hacker
Gray hat hackers fall in between white hat hackers and black hat hackers, they may find system vulnerabilities and report, or exploit these vulnerabilities for personal gain, but usually do not cause serious damage.

4. Hacker Culture
Hacker culture is a special and scattered cultural group, some hackers advocate the spirit of openness, sharing and exploration. They usually pursue technological innovation and breakthroughs, advocate free access and use of information, and also pay high attention to privacy protection.
5. Ethical issues
The ethical issues involved in hacking are highly debated. In their behavior, a contradiction exists between legality and morality. It's worth noting that hacker culture is not necessarily associated with crime, although hacking is sometimes viewed as a crime.
6. The role of hackers
Hackers play an important role in the field of information security . By discovering and disclosing system vulnerabilities, they advance the development of software and network security, helping to protect personal privacy and corporate secrets from unauthorized access. In addition, some hackers have made outstanding contributions to technical communities, open source software, and Internet services.
Three: Hacking (Network Security) Self-study Advice
Suggestion 1: Seven Levels of Hackers
Hackers are full of temptation for many people. Many people can find that this field is like any other field. The deeper you go, the more you will be in awe. Knowledge is like an ocean, and hackers also have some levels. Please refer to the sharing of Zhichuangyu CEO ic (a member of the world's top hacker team 0x557) as follows:
Level 1 Lengtouqing [millions of people]: know how to use security tools, can only scan and decipher passwords easily
Level 2 system administrators [tens of thousands of people]: make good use of security tools, especially familiar with
the development of systems and networks Level 3 large companies Personnel or core security company Da Niu [thousands of people]: very familiar with the operating system, started to develop codes, wrote their own scanner Level
4 can find and exploit vulnerabilities [hundreds of people]: can find loopholes by themselves, find 0DAY by themselves and Write Exp to exploit loopholes, do protocol testing on the system to find loopholes
Level 5 high level [less than a hundred people]: people who defend and build systems
Level 6 elite level [dozens to a dozen people]: have a good understanding of the operating system In-depth
Level 7 Big Niu Niu [Few]: Mark Zuckerberg, Albert Einstein and other people who changed the world
You can see, what level are you at now? You may be wondering which level I am at, my level is not high, and I am on the way to seek a breakthrough. However, I have also practiced the other two skills, which may allow me to make a more interesting breakthrough. As for what it is, I am sorry, how dare I be presumptuous before I succeed.
Suggestion 2: learn to observe
I often say that the Internet is full of treasures, and observation is the first necessary skill. If you are good at observing and summarizing, you will discover some ways faster, which will make your life easier than others.
Suggestion 3: circle
In the above process, you will definitely become familiar with some IDs. Do you want to make some friends? Show your strengths, sharing is important, no one likes to reach out or troll.
It is especially recommended to understand the classic attributes of all groups in the next circle, and recommend the books "The Selfish Gene" and "The Crowd".
Tip Four: Creativity
I mentioned before that to be creative enough, there are two key points, one is "vision" and the other is "focus". Vision is horizontal, and concentration is vertical. The two need to be balanced, because human energy is limited (the law of energy conservation). As long as either one is out of balance, neither will exist.
For most people, focusing is the most difficult. After all, this is an immediate process of entropy reduction, a process of self-organization of information. Seriously, you accelerated the end of the universe because of your focus. As for why, it will not be expanded here. In short, it is really difficult to focus, and you have to force yourself a lot of times.
Because of selfish genes, human beings are always bursting out their creativity consciously or unconsciously. Some creativity can change the world, some creativity can change the family, and some creativity can change yourself. These are all creativity. How much creativity you need depends on your genes, on who you want to be.
After all, there are "very few" people who can change the world...
Suggestion 5: Some good resources
Open your browser and search for:
i Chunqiu, Wuyun, Zhichuangyu R&D skill table v3.0, FreeBuf, enough!
If these few clues don't open up your hacker world view and make you creative enough, then it's useless to ask more. I suggest that you really savor some of the knowledge they give, follow the vines, and gradually extend your tentacles to the world. As I said earlier, learn to observe
This part of super hacking
is still relatively far away for students with zero foundation, so I won’t go into details, and attach a learning route.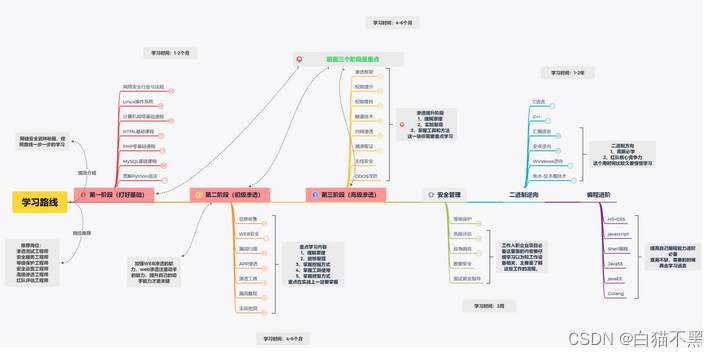
If the picture is too large and compressed by the platform, it is difficult to see clearly, friends who need it can pay attention to it. After paying attention, the background will automatically send it to everyone!
I have also compiled some network security information for you below. If you don’t want to look for them one by one, you can refer to these information. If you need to pay attention, the background will automatically send it to everyone~ You can just get the notice by yourself when the time comes~
Video supporting materials & domestic and foreign network security books, documents & tools

Of course, in addition to supporting videos, various documents, books, materials & tools have been sorted out for you, and they have been classified into categories for you.
Some video tutorials that the author bought by himself, but which are not available on other platforms for free.

SRC&Hacking Technical Documentation

SRC&Hacking Technical Documentation 
If you want to get involved in hacking & network security, the author has prepared a copy for everyone: 282G the most complete network security data package on the entire network for free! After following me, it will be automatically sent to everyone! After everyone pays attention, just pay attention to the background news~
epilogue
Cybersecurity is a critical issue in today's society. With the rapid development of science and technology, the network has penetrated into every aspect of our lives, bringing us great convenience and opportunities. However, there are also various risks and threats in the network, such as hacker attacks, data leakage, etc. Therefore, learning network security knowledge has become a problem that everyone should pay attention to and pay attention to.